
DataSunrise Database Proxy
Every company works with a huge amount of information, including sensitive data, every day. All information is collected and processed in databases. One of the most important things for people is to know that their information is protected and secured.
Of course, databases have their own security tools such as roles and privileges for users. The facilities of these tools change from one database to another, but the main purpose is the same – to keep safe sensitive information and prevent data leakage. In other words, you should implement such a level of security to protect the main security basics such as Confidentiality, Integrity, and Availability, the CIA triad. Nowadays these aspects are very important because everything depends on the security measures you have. But sometimes built-in security features protecting and ensuring security information are not enough. That is why some companies need to enlarge the protection and use a database firewall. When you use it you see a lot of useful information from traffic between a client application and a database which is analyzed in vendor-independent database software like DataSunrise. This feature can work when DataSunrise runs in a Proxy mode. Below we will tell you about how it works and what advantages you will get thanks to a database proxy.
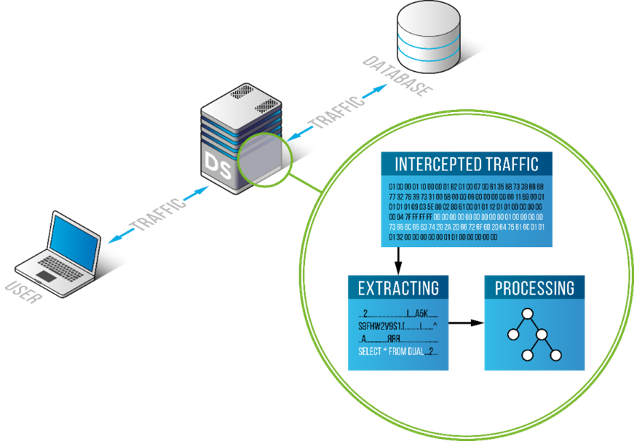
Figure 1: DataSunrise Database Proxy
How Does Database Proxy Work?
In DataSunrise we have 3 modes of analysis traffic: Sniffer, Proxy, and Database Audit Trail.
Sniffer mode is for passive protection. In this mode, DataSunrise can only perform database activity monitoring. Working in this mode DataSunrise is connected to a SPAN port and acts like a traffic analyzer capable of capturing a copy of database traffic.
Trailing is the mode when you also can audit databases by the means of native auditing tools. DataSunrise in this mode performs auditing of Oracle, PostgreSQL, MS SQL Server, and MySQL databases. You should note that this configuration is intended to be used for Amazon RDS databases.
Here we will pay our attention to the second mode. Proxy mode is active protection, where you can use all advantages of our software including firewall and other useful features such as data masking and activity monitoring. But what is DataSunrise Proxy? And how does it work? Database proxy is an intermediary between a user application and a database. In general, when you are sending queries to a database you do it straight to it. If you use a database proxy, your queries go through the proxy, and after that, the database will receive them. The reverse process is the same. The answer from a database goes through the proxy, and after that, you receive it. It means that a database proxy is a secure gateway between a database user and a database.
DataSunrise proxy could work with a lot of databases. DataSunrise maintains the organizational authentication policies of Microsoft Active Directory and Kerberos protocol for cloud-based databases. An additional level of protection as a database proxy will be very helpful.
What Can You Do with DataSunrise Database Proxy?
As we mentioned before, when you use DataSunrise in a Proxy mode all functionality becomes available: database activity monitoring, both dynamic and static masking. But what can you do with these features? Let’s look a little bit closer at what we are ready to offer you when DataSunrise works as an intermediary between a user and a database.
- With Database Activity Monitoring you can see who and when accessed a database, and what modifications were done. It is a very useful feature when you need to comply with different security standards. Moreover, with our continuous activity monitoring, you can detect access rights abuse and prevent data breaches.
- Thanks to Security Rules you can protect your database from different threats including SQL injections and DoS attacks.
- Analyze the queries for Table Relations. This feature is very powerful and increases the effectiveness of sensitive data discovery.
- Using the Data Masking feature you can mask database columns with sensitive information. This feature helps you to prevent data leakage and save private information from third-parties.
Additional Measures with Database Proxy
Previously mentioned features are very important and play the main role in data security and privacy. Besides, we can offer you some more measures to increase database security:
- reduce the risk of unauthorized access to databases with two-factor authentication (2FA);
- using LDAP users to connect to a database;
- scan your databases for vulnerabilities with VA scanner;
- being compliant with different acts and laws, such as SOX, GDPR, HIPAA, etc.
Moreover, with DataSunrise you can do the following things that will make your life easier. For example, with DataSunrise you will be able not only to protect sensitive data in databases but also search for it. Also, you can create custom reports on required events and save them as:
- a PDF file;
- a CSV file.
Working in a Proxy mode DataSunrise serves as an intermediary between a database and a database user. As far as all queries go through the DataSunrise proxy it helps you to monitor everything that is going on in your databases. That is why everything in your databases becomes more transparent and easier. Try our solution right now to understand all possibilities and benefits of the DataSunrise Proxy.
