Two-factor authentication
Full compliance
Technical support
DataSunrise Web Console at a Glance
Logical web console designed to intuitively set and manage your database security and compliance policies
Download FreeDataSunrise Supported Features for Teradata
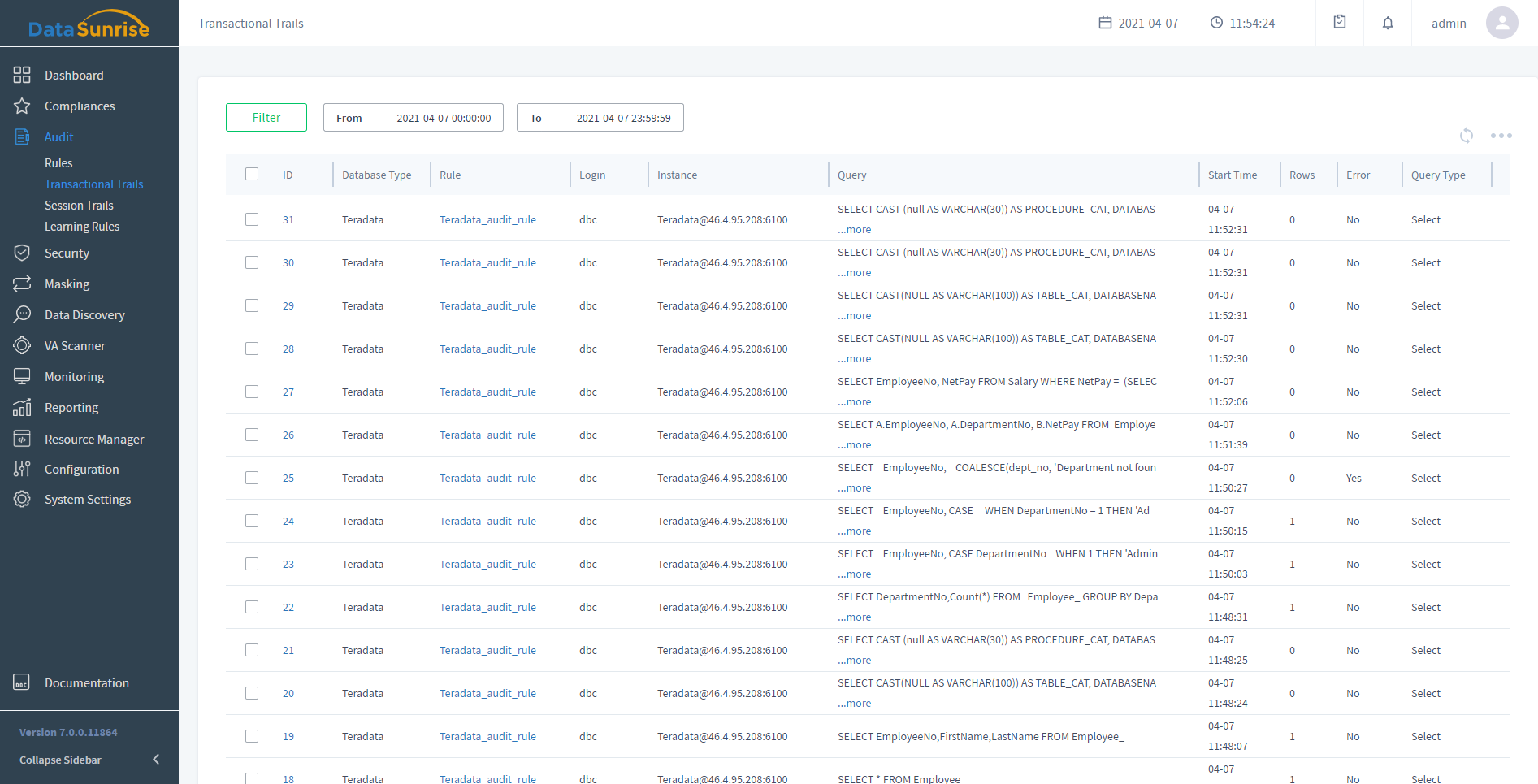
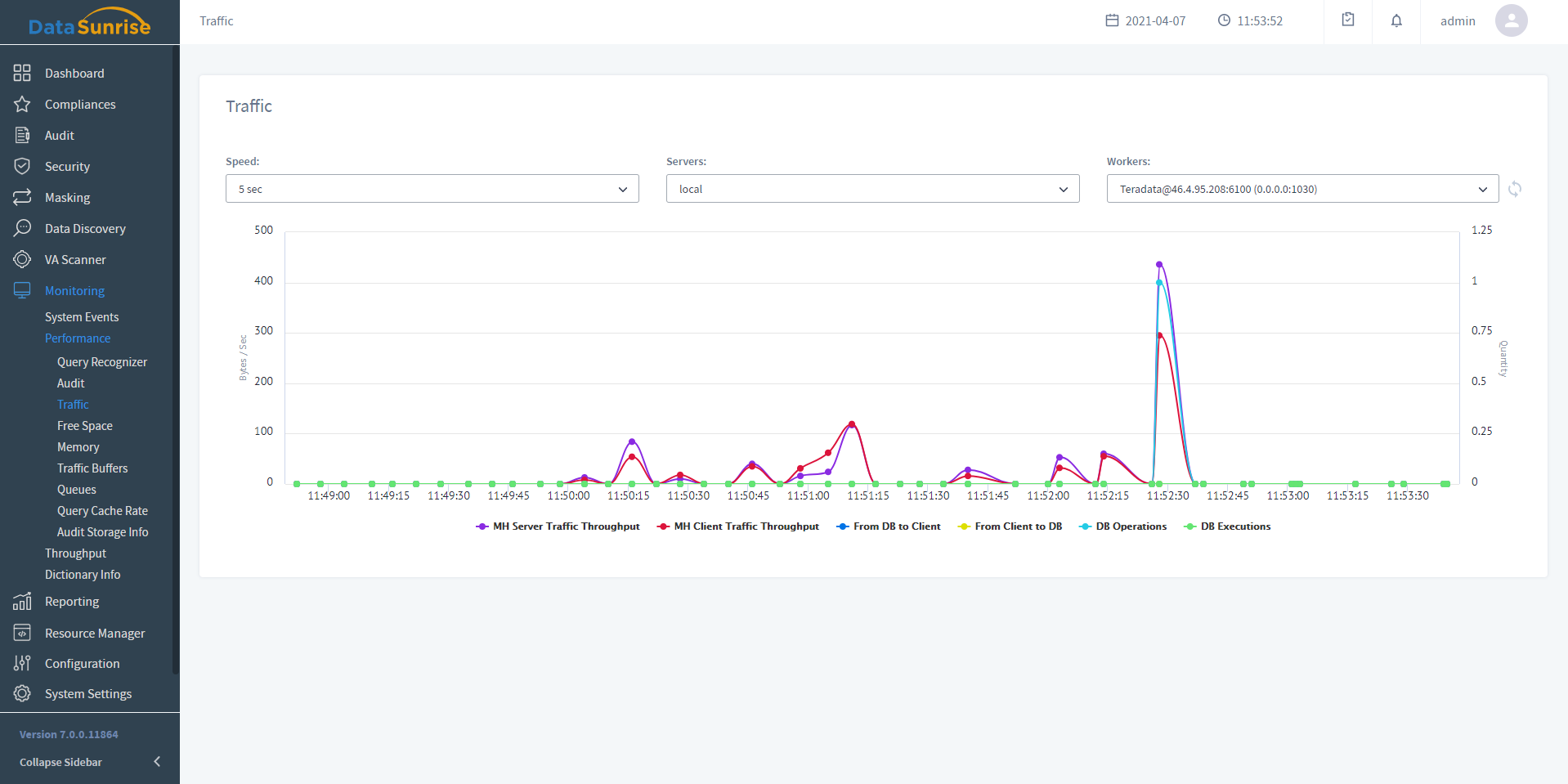
- Activity Monitoring
- Database Firewall
- Data Masking
- Database Regulatory Compliance
- Sensitive Data Discovery
- Activity Monitoring
- Monitors of all user actions made to a database in real time
- Helps to detect access rights abuse attempts
- Prevents data breach preparations in advance
- Learn More
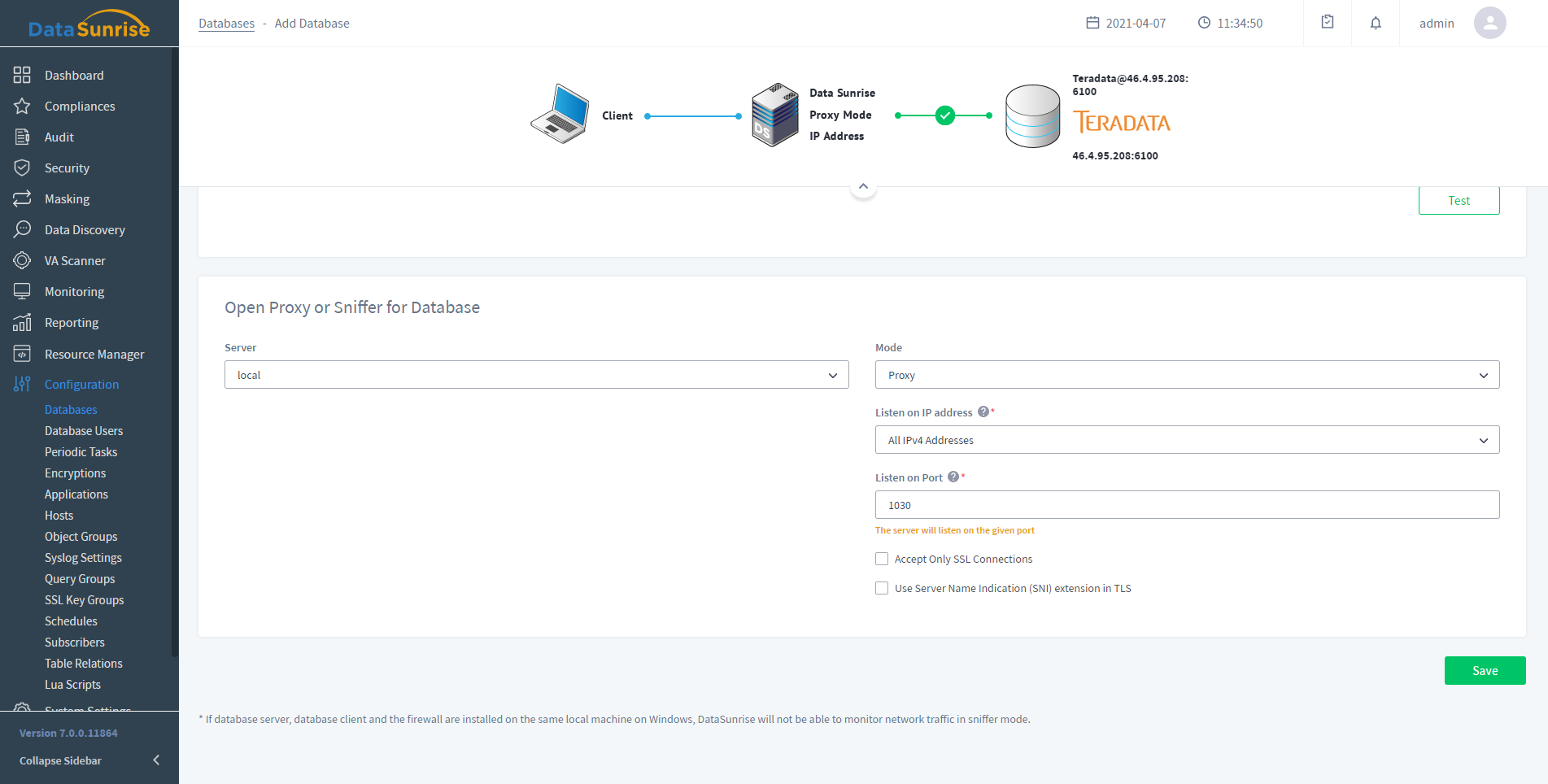
- Database Firewall
- Detects SQL injections and unauthorized access attempts in real time
- Blocks any malicious SQL query immediately
- Blocks DDOS and Brute-Force attempts
- Learn More
- Data Masking
- Avoids a potential data leakage and stay in compliance
- Obfuscates or encrypts the data
- Audits sensitive and PII data, discovery and active protection
- Learn More
- Database Regulatory Compliance
- Helps managing, automating and administrating the government regulations
- Automatic audit and security reports generation
- Prevents internal threats and minimizes data breaches
- Learn More
- Sensitive Data Discovery
- Detects where sensitive data resides in all databases and data warehouses
- Classifies and categorizes sensitive data
- Quickly creates security, audit and masking rules
- Learn More
Customizable Traffic Filtering
Creating granular security, audit, and compliance policies with modifiable traffic filters. Handle queries from certain users, client applications, hosts, and IP addresses as a single object, grouping them together.
Regulatory Compliance Automation
Accurately discover sensitive data to enforce security, masking, and auditing policies to meet certain compliance standards. Self-managing regulatory compliance automation requires no manual intervention.
Comprehensive Threat Detection
Real-time access and activity control to ensure malicious database activity identification, automatic detection and instant blocking of statements containing SQL injections.
Additional Authentication Methods
DataSunrise provides a secure authentication service for computer networks and supports Kerberos and LDAP authentication. All major operating systems, including Microsoft Windows, Linux, Apple OS X and Free BSD, support Kerberos protocol and LDAP.

Keep Your Teradata Database Safe with DataSunrise
Request a DemoFind Your Unique Solution
1. Select Product Type
2. Select Supported Databases
- Activity Monitoring
- Database Firewall
- Data Masking
- Perfomance Monitoring
- Sensitive Data Discovery