
DataSunrise Deployment Modes: Features and Key Considerations
DataSunrise is a leading data security platform known for its robust protection capabilities and flexible deployment options. DataSunrise is a versatile data security platform that can be deployed in various configurations to suit different organizational needs. Understanding the advantages and disadvantages of each deployment mode is crucial for making an informed decision that aligns with your security requirements and infrastructure. Here’s a professional analysis of the four deployment modes offered by DataSunrise: Proxy mode, Sniffer mode, Agent mode, and Trailing DB Audit Logs.
Proxy Mode
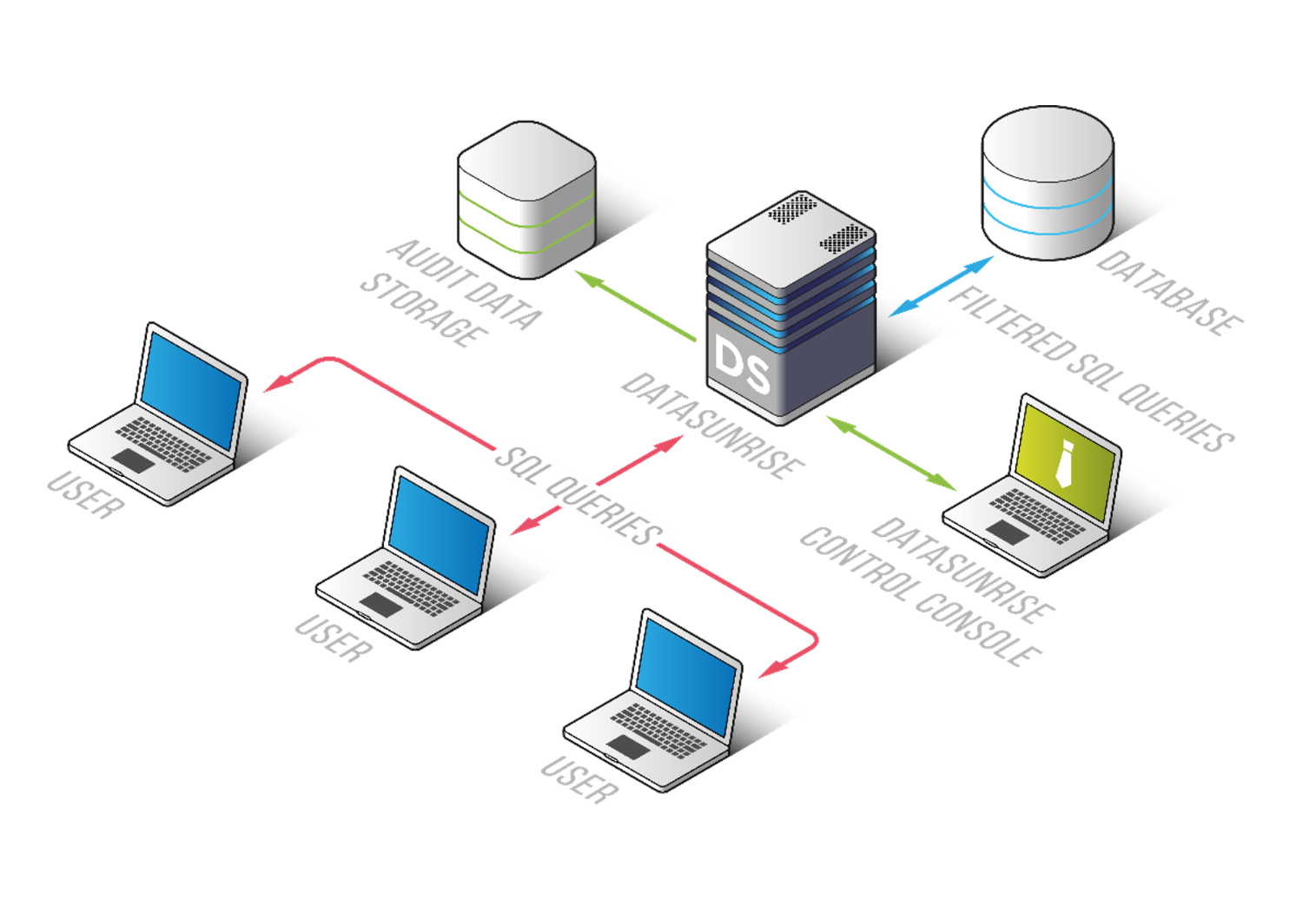
Picture 1. Proxy Mode deployment
Features:
- Full Functionality: Proxy mode enables the complete suite of DataSunrise features, including database activity monitoring, database firewall, and dynamic and static data masking.
- Encrypted Traffic Handling: This mode supports the processing of encrypted traffic, ensuring secure data transmission.
- Performance: There is no direct performance impact on the database server since the proxy operates on a separate host. This is particularly beneficial for databases licensed by the number of CPU cores on the database server, as it incurs no additional licensing costs.
- Latency: The lightweight proxy has a minimal impact on latency, typically around 5-10% for fast-growing queries.
- Independent Monitoring: The monitoring and security features in Proxy mode operate independently of the database vendor’s native functionality and the database administrators (DBAs) managing the system. This independence ensures a clear division of responsibilities and enhances security by reducing reliance on external configurations and controls. It provides an additional layer of protection, ensuring that security measures are robust, consistent, and not subject to internal alterations or oversight.
Key Considerations:
- Additional Network Layer: Introducing an additional layer in the network infrastructure can pose a risk to database availability. This risk can be mitigated by deploying DataSunrise in High Availability (HA) mode.
- Network Access Control: It is essential to ensure that network access to the database is restricted to prevent direct access that bypasses the proxy. Proxy mode cannot handle local connections.
Sniffer Mode
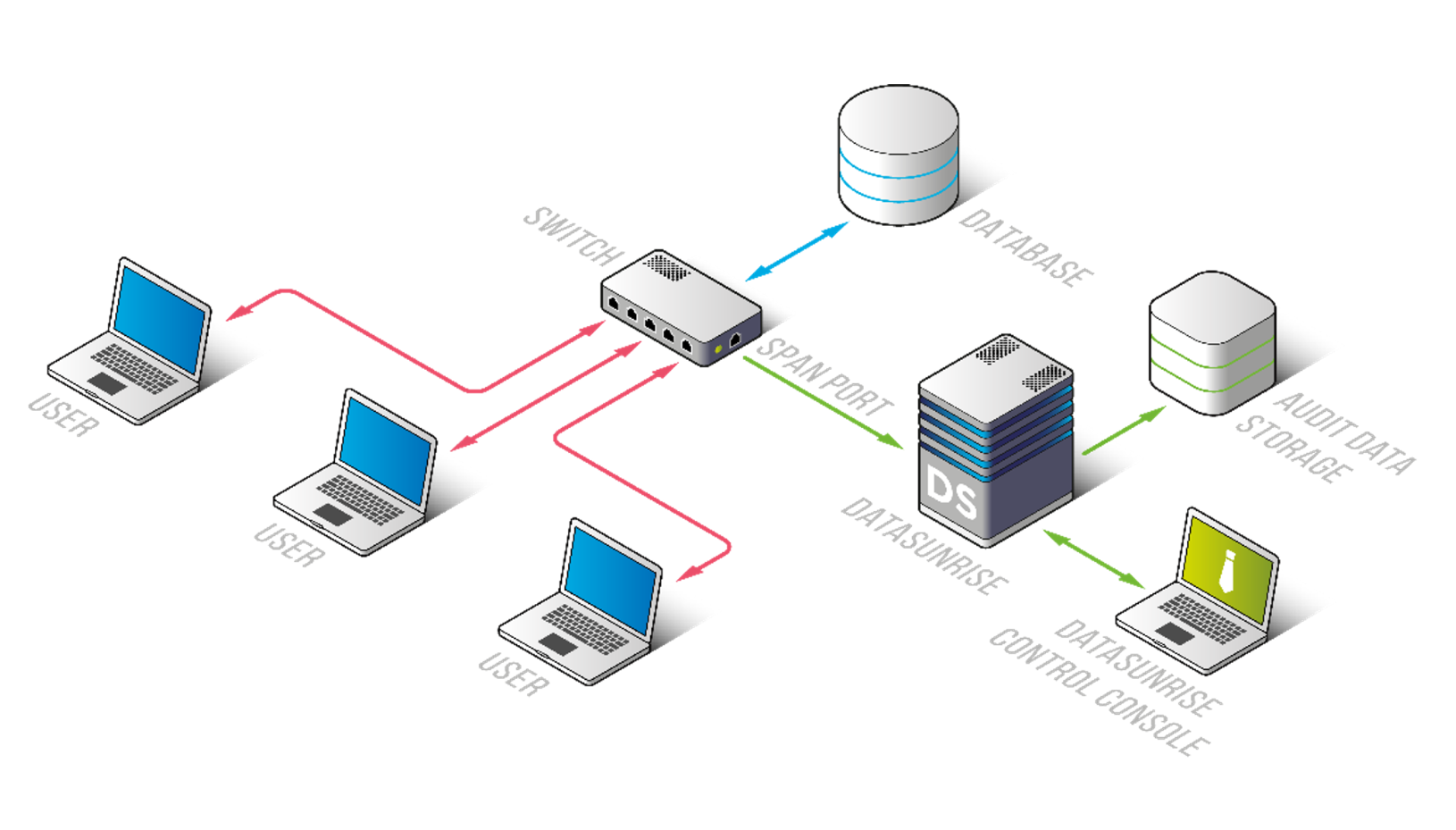
Picture 2. Sniffer Mode deployment
Features:
- Passive Monitoring: Sniffer mode allows DataSunrise to act as a traffic analyzer, capturing database traffic from a mirrored port without impacting database performance.
- Zero Impact on Database Traffic: This mode does not affect database traffic or performance.
- Independent Monitoring: Similar to Proxy mode, Sniffer mode operates independently of the database’s native functionalities and beyond the reach of database administrators (DBAs). This autonomy allows for unbiased monitoring of the database traffic, ensuring that DBAs cannot interfere with or influence the surveillance process. This greatly reduces the risk of access manipulation, bolstering the overall security of the database system.
Key Considerations:
- Limited Functionality: Sniffer mode does not support active security features such as the database firewall or masking. It cannot modify database traffic.
- SSL Encryption Limitation: SSL-encrypted traffic cannot be analyzed in this mode, which is a significant drawback given the widespread use of SSL encryption today. To utilize Sniffer mode, encryption must be disabled or configured to use weaker algorithms (only supported for MS SQL Server).
- Local Connections: Sniffer mode is unable to handle local connections.
- Limitation of virtual environments: Port mirroring capabilities vary across different virtual and cloud environments. Virtual and cloud environments can have limitations for port mirroring which depends on the vendor.
- Complexity of network configuration. Setting up traffic mirroring often requires a good understanding of how traffic flows within the network infrastructure. Only with a well-thought-out strategy for working with network traffic can traffic mirroring be configured correctly to process 100% of all connections. You also need to keep in mind that network addresses of databases can change, which also needs to be clearly monitored.
Trailing DB Audit Logs
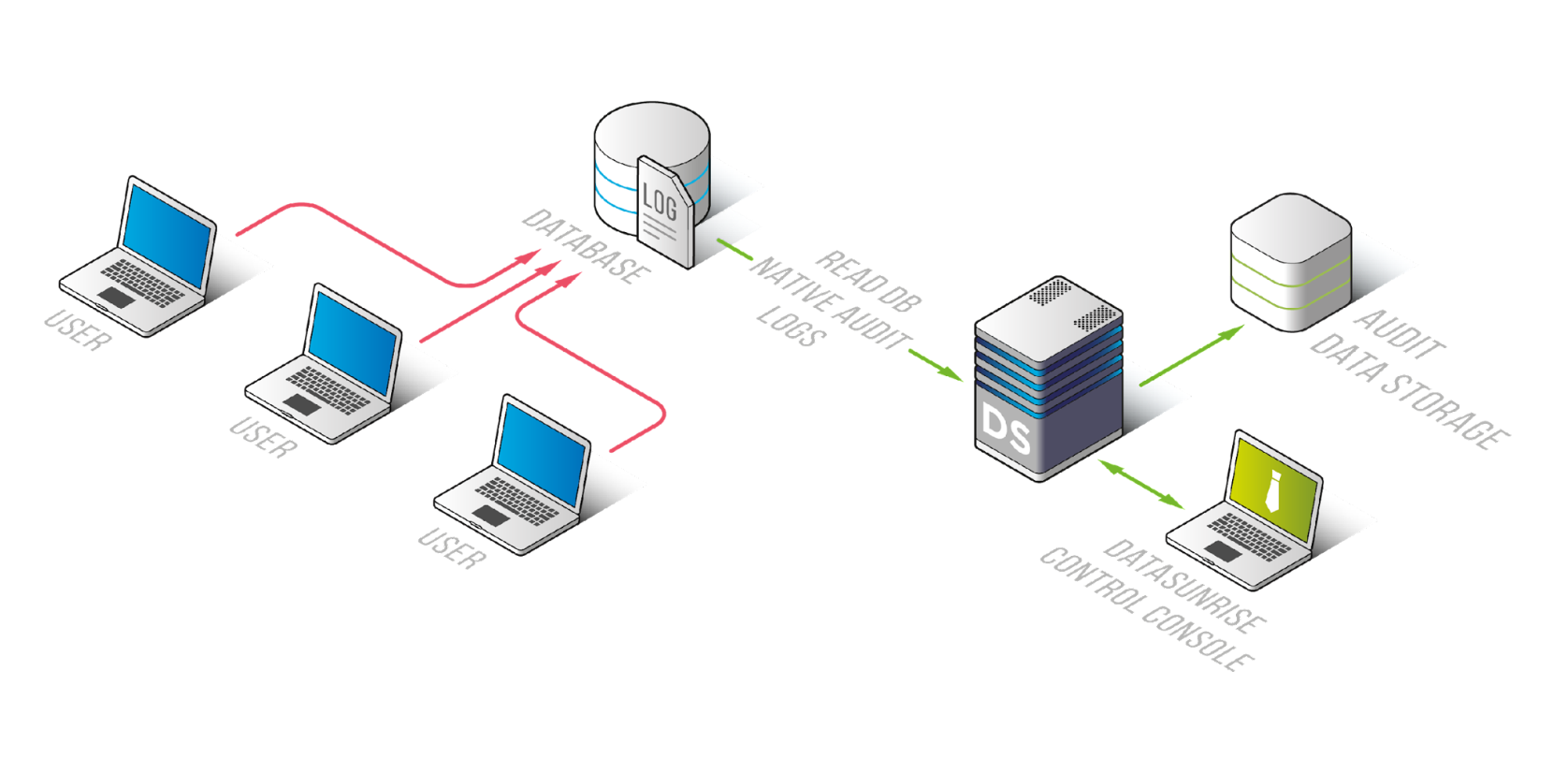
Picture 3. Trailing DB Mode deployment
Features:
- Native Auditing: This mode leverages the native auditing tools of various databases, including Oracle, Snowflake, Neo4J, PostgreSQL-like, AWS S3, MS SQL Server, GCloud BigQuery, MongoDB, and MySQL-like databases.
- No Network Architecture Changes: There is no need to alter the existing network architecture or add an additional layer like a proxy.
- Comprehensive Auditing: Since the database generates native audit logs, both remote and local connections are included.
Key Considerations:
- Performance Impact: The database’s performance can be affected since it is responsible for generating the logs. In active environments, performance degradation can reach 15-30%.
- Audit Log Management: Native audit logs require configuration by the DBA, which can blur the lines of responsibility between security and database administration. There is also the risk of audit logs being disabled accidentally or intentionally by the DBA.
Agent Mode
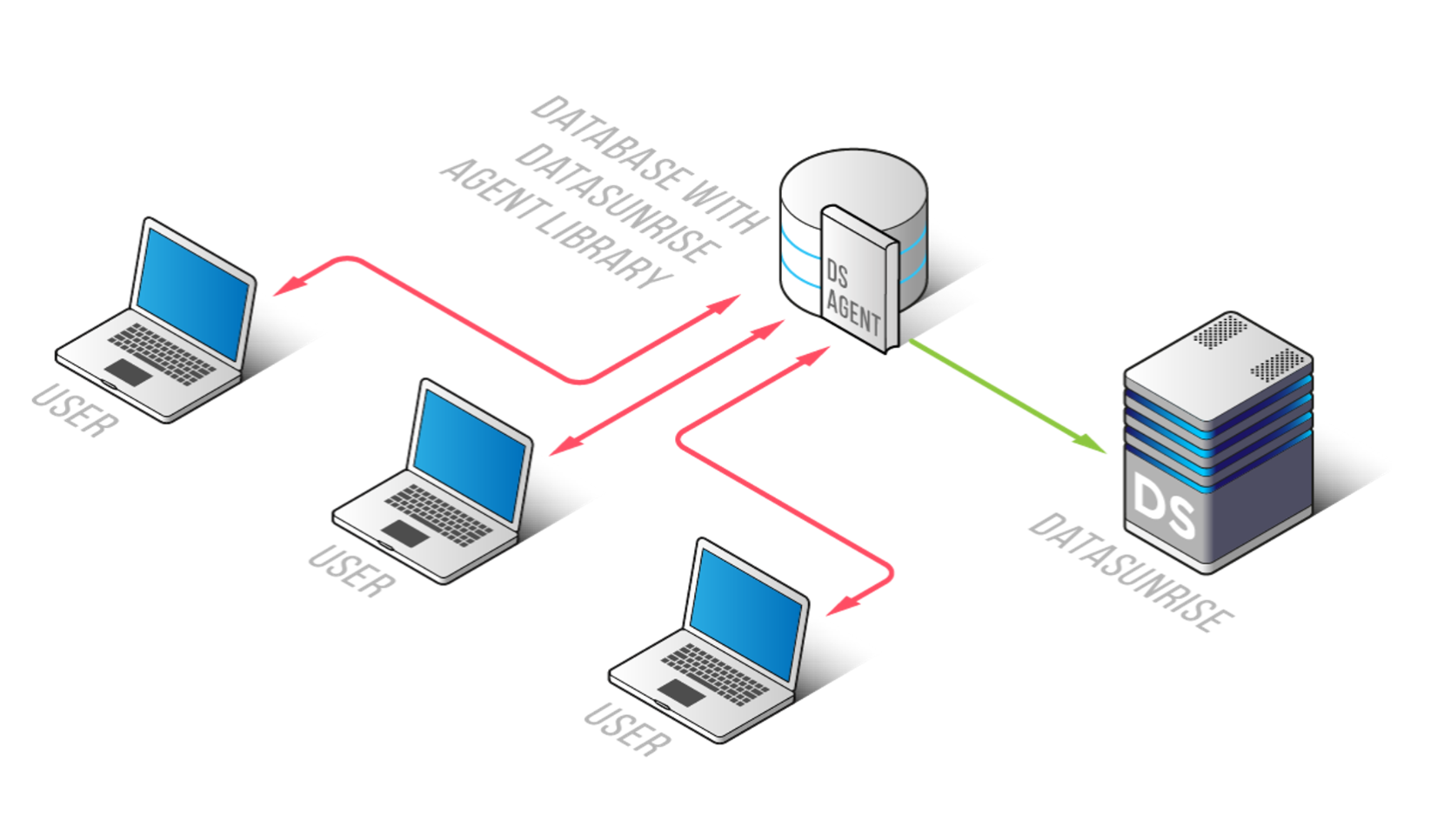
Picture 4. Agent Mode deployment
Features:
- Minimal Network Changes: Agent mode does not require adding an additional network layer, and traffic processing on a separate host can minimize the impact on database performance.
- Local Connection Handling: This mode is capable of handling local connections.
Key Considerations:
- Limited Support: Not all databases are included in our current list of supported databases. To obtain the most up-to-date list of supported databases or to consult our latest guides, please contact our Support Team at [email protected].
- Agents compatibility: Customers should check compatibility with other agents which can be installed to the same environment.
In conclusion, each DataSunrise deployment mode offers unique benefits and comes with its own set of considerations. When choosing the appropriate mode, it is essential to weigh the pros and cons in the context of your specific security needs, infrastructure, and performance requirements. By doing so, you can ensure that your data remains secure while maintaining optimal database performance
