Generative AI and Phishing
Phishing—once reliant on crude impersonations and obvious errors—has evolved into a highly sophisticated, AI-powered discipline. Modern attackers now employ Generative AI to craft context-aware emails, cloned websites, and real-time voice simulations that can bypass even well-trained human judgment.
These threats are not hypothetical. In 2025, security researchers observed a surge in LLM-generated phishing kits capable of adapting language tone, structure, and psychological triggers based on target data.
This article explores how Generative AI amplifies phishing campaigns, how organizations can detect these advanced attacks, and how DataSunrise strengthens protection with real-time auditing, anomaly detection, and compliance-aligned masking.
How Generative AI Reinvents Phishing
Traditional phishing relies on fixed templates. Generative models like GPT, LLaMA, and Claude-derived variants allow attackers to dynamically generate text that mirrors legitimate communication—complete with corporate terminology, personalized salutations, and time-sensitive requests.
Key advancements include:
- Adaptive Content Generation: AI tailors messages to user roles and historical behavior.
- Voice and Deepfake Phishing: Generative speech tools mimic real executives.
- Dynamic Landing Pages: Models create HTML templates matching official websites within minutes.
These developments make AI-based phishing almost indistinguishable from genuine correspondence, significantly expanding the potential attack surface
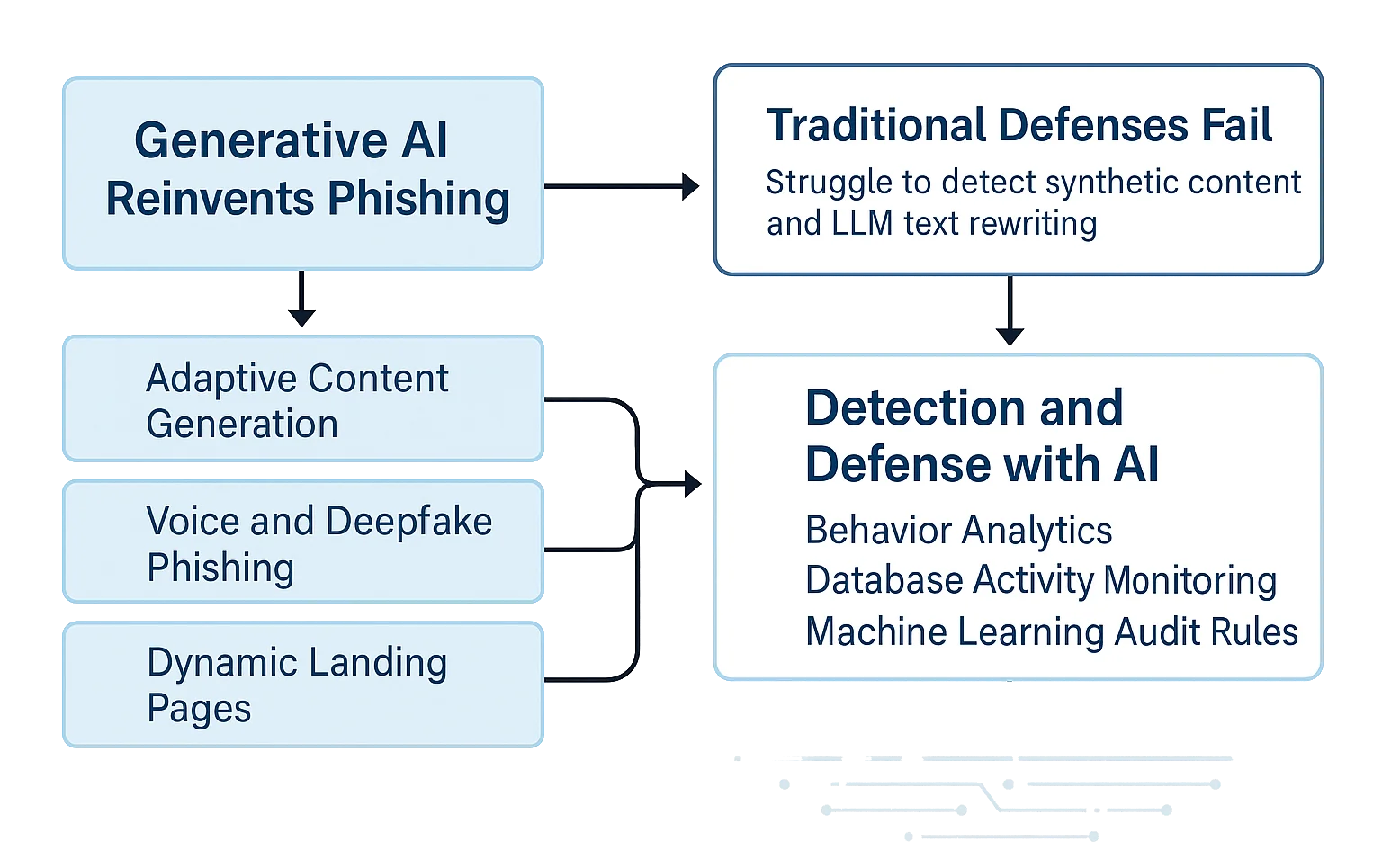
Why Traditional Defenses Fail
Email filters, SPF/DKIM checks, and URL reputation databases were never designed for synthetic content generated on demand. Attackers can slightly alter each phishing instance, bypassing fingerprint-based detection.
Moreover, LLMs can automatically rewrite messages to avoid known security triggers—rendering conventional filtering nearly obsolete.
Example: AI-Generated Bypass
import random
phrases = [
"urgent payroll update",
"action required to confirm credentials",
"secure document access"
]
msg = f"Dear user, please verify your {random.choice(phrases)} using the link below."
print("Generated phishing lure:", msg)
Each message is unique, contextually plausible, and nearly impossible to blacklist. Defense must therefore shift from content analysis to behavioral correlation.
Generative AI in Phishing Detection
While attackers use AI to deceive, defenders can employ it to detect. Generative AI models, when paired with Behavior Analytics and Database Activity Monitoring, can identify anomalies in message flow, access timing, and metadata distribution.
For example, DataSunrise’s Machine Learning Audit Rules can flag suspicious login attempts or bulk credential lookups triggered after phishing mail interactions.
This adaptive intelligence approach helps organizations catch early signs of compromise—even when messages appear legitimate.
DataSunrise as the Defensive Core
Phishing threats don’t stop at the inbox—they extend to databases, applications, and cloud storage once credentials are stolen. DataSunrise protects these assets through:
- Database Firewall that blocks unauthorized access following a phishing-based credential breach.
- Dynamic Data Masking to conceal sensitive data from potentially compromised sessions.
- Audit Trails that trace every post-phishing action for compliance investigation.
- Compliance Autopilot ensuring alignment with GDPR, HIPAA, and PCI DSS in real time.
Unlike traditional security tools, DataSunrise provides Zero-Touch Policy Automation, delivering Context-Aware Protection without requiring manual tuning .
Example: AI-Crafted Credential Harvesting
A multinational firm experiences a breach after receiving hyper-personalized phishing emails mimicking its HR system.
Attackers use generative text models to craft employee-specific content and cloned the login portal using AI web-design tools.
Once credentials are harvested, attackers access internal databases to exfiltrate payroll records.
With DataSunrise deployed, the breach trajectory could be contained early:
- Audit Rules detect irregular login timing.
- Behavior Analytics correlate it with abnormal query volume.
- Masking Policies automatically limit visibility of PII.
- Compliance dashboards produc instant forensics evidence.
This example shows how combining AI detection with autonomous compliance orchestration transforms reactive defense into predictive resilience.
Ethical and Compliance Challenges
AI-generated phishing also raises ethical and regulatory issues. Enterprises must ensure their own use of AI tools doesn’t inadvertently produce misleading content or store synthetic data violating privacy laws.
DataSunrise assists through Data Discovery and Continuous Data Protection — identifying, encrypting, and auditing all sensitive information used in LLM training pipelines.
This capability ensures responsible AI adoption under frameworks like EU AI Act and NIST AI Risk Management Framework.
Business Impact
| Aspect | Without AI-Adaptive Defense | With Generative AI + DataSunrise |
|---|---|---|
| Detection latency | 6–12 hours | Real-time |
| Credential misuse | Often undetected | Automatically blocked |
| Compliance response | Manual reports | One-click evidence |
| Policy updates | Human-driven | No-code automation |
Enterprises adopting AI-enhanced protection gain measurable improvements in response speed, compliance assurance, and breach containment efficiency.
Future of AI-Driven Phishing Defense
Generative AI will continue to blur the line between human and machine communication. To counter it, future security systems must integrate self-learning detection, contextual policy enforcement, and autonomous auditing.
DataSunrise’s roadmap emphasizes:
- ML-based Suspicious Behavior Detection for adaptive phishing response.
- Autonomous Compliance Calibration ensuring AI systems meet evolving global regulations.
- Cross-Platform Integration covering structured, semi-structured, and unstructured data environments.
The convergence of AI and compliance-centric defense marks the next era of enterprise cyber resilience.
Conclusion
Generative AI has made phishing attacks more convincing, scalable, and difficult to trace. Combating this new wave requires combining AI-driven analytics with strong data governance.
By integrating DataSunrise’s intelligent masking, auditing, and compliance automation, organizations can mitigate both the human and technical layers of AI-powered deception.
Explore DataSunrise’s Compliance Manager and AI Security Center to learn how your enterprise can stay ahead of evolving phishing tactics.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now