
Database Activity Monitoring
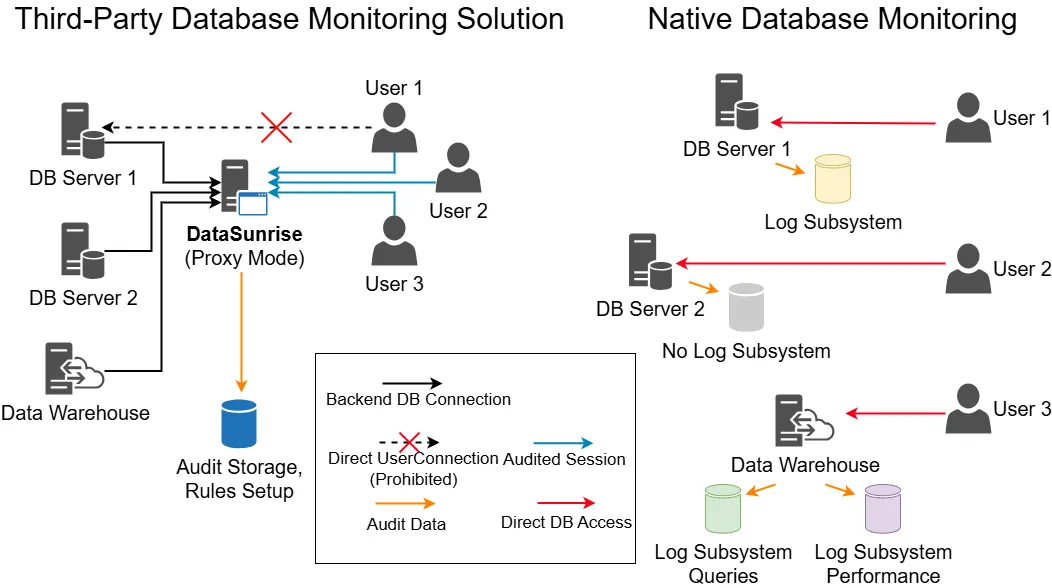
As databases grow in size and complexity, it becomes increasingly important to monitor and secure them effectively. This is where Database Activity Monitoring (DAM) comes into play.
DataSunrise offers comprehensive and advanced Database Activity Monitoring (DAM) solutions. Our state-of-the-art tools provide real-time visibility into database operations, robust security features, and intuitive user interfaces. While this article provides a general overview of DAM practices, DataSunrise’s platform goes above and beyond, offering cutting-edge capabilities that can significantly enhance your database security and compliance efforts.
What is Database Activity Monitoring?
Database Activity Monitoring, often abbreviated as DAM, is a security practice that involves tracking and analyzing all database activities in real-time. It’s like having a vigilant guard watching over your data, ensuring that every interaction is legitimate and secure.
The Importance of DAM
DAM is crucial for several reasons:
- Security: It helps detect and prevent unauthorized access or malicious activities.
- Compliance: Many industries require strict data handling practices, and DAM helps meet these regulations.
- Performance: By monitoring database activities, you can identify bottlenecks and optimize performance.
- User Behavior Analysis: DAM provides insights into how users interact with the database, which can be valuable for improving workflows.
Key Components of Database Activity Monitoring
1. Real-time Monitoring
DAM solutions continuously track all database activities, including:
- SQL queries
- Data modifications and manipulations (inserts, updates, deletes)
- Schema changes
- User logins and logouts
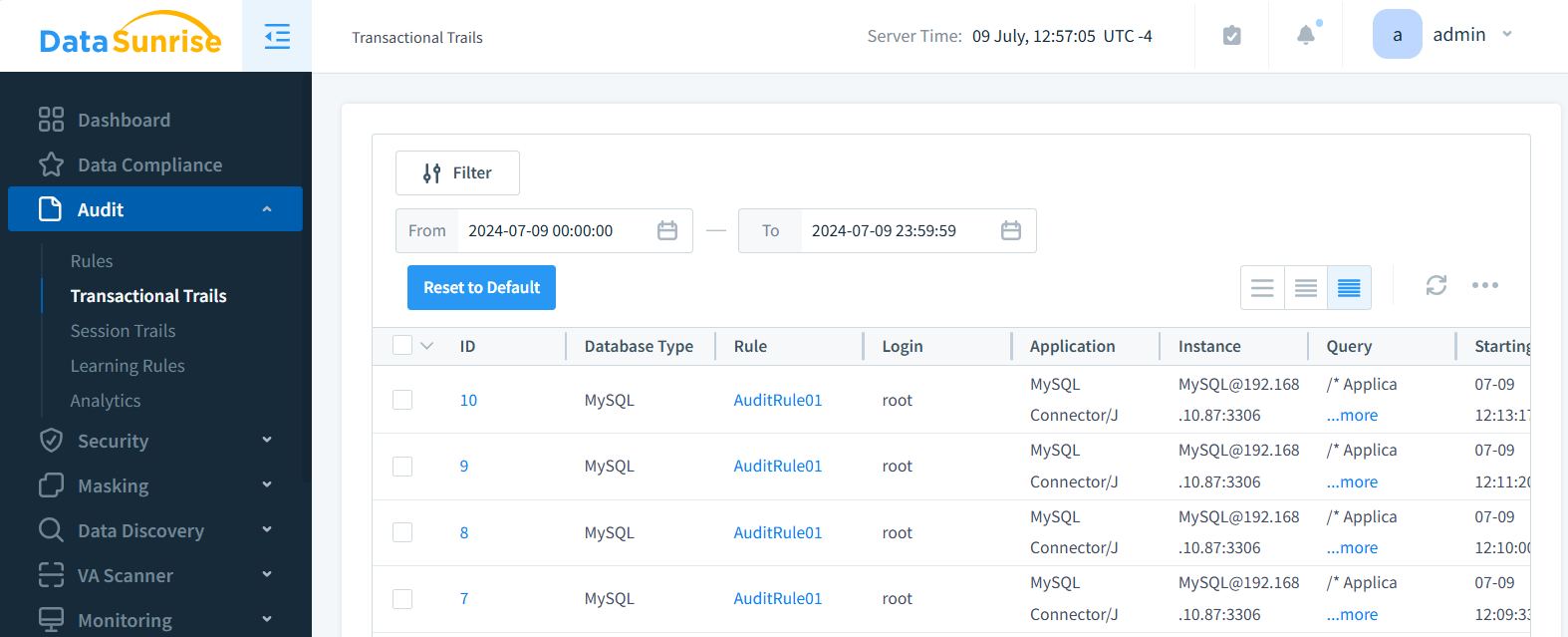
DataSunrise Transactional Trails offer comprehensive insights into all monitored database queries.
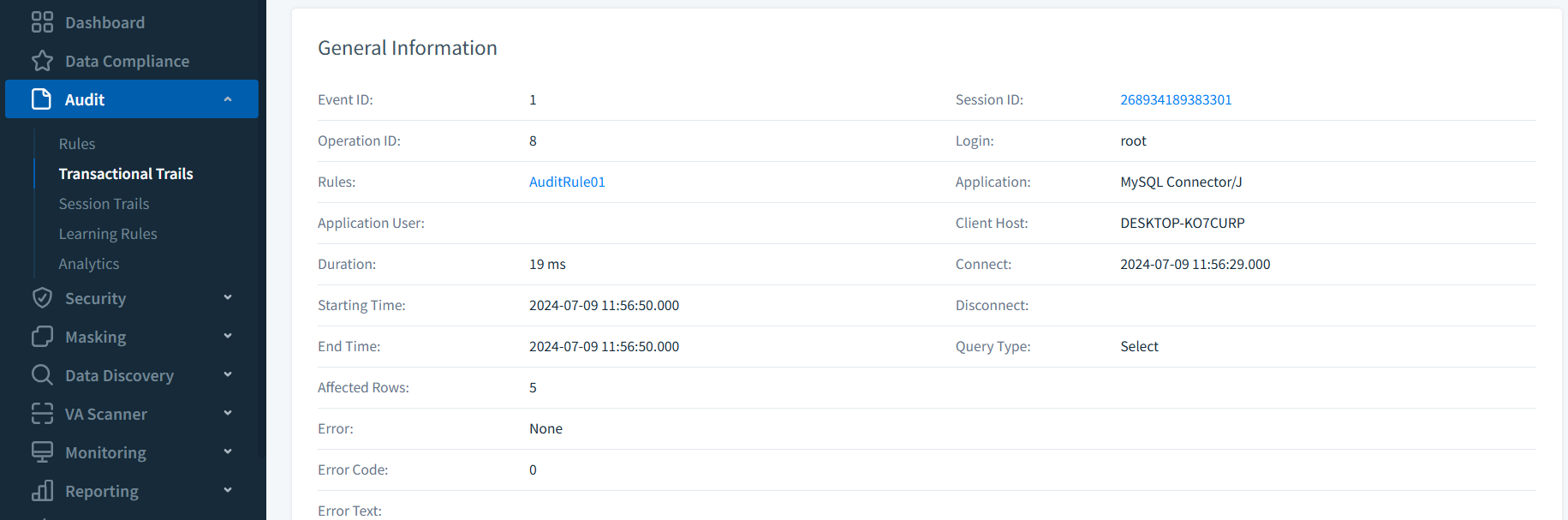
These robust audit logs capture essential information, including the full query text, execution duration, and precise start and end times. Beyond these core metrics, DataSunrise’s flexible logging system allows for the capture of numerous additional parameters, tailoring the audit process to your specific needs.
For in-depth analysis, you can even configure Transactional Trails to store query results, providing a complete picture of database activity and enabling thorough forensic investigations when needed.
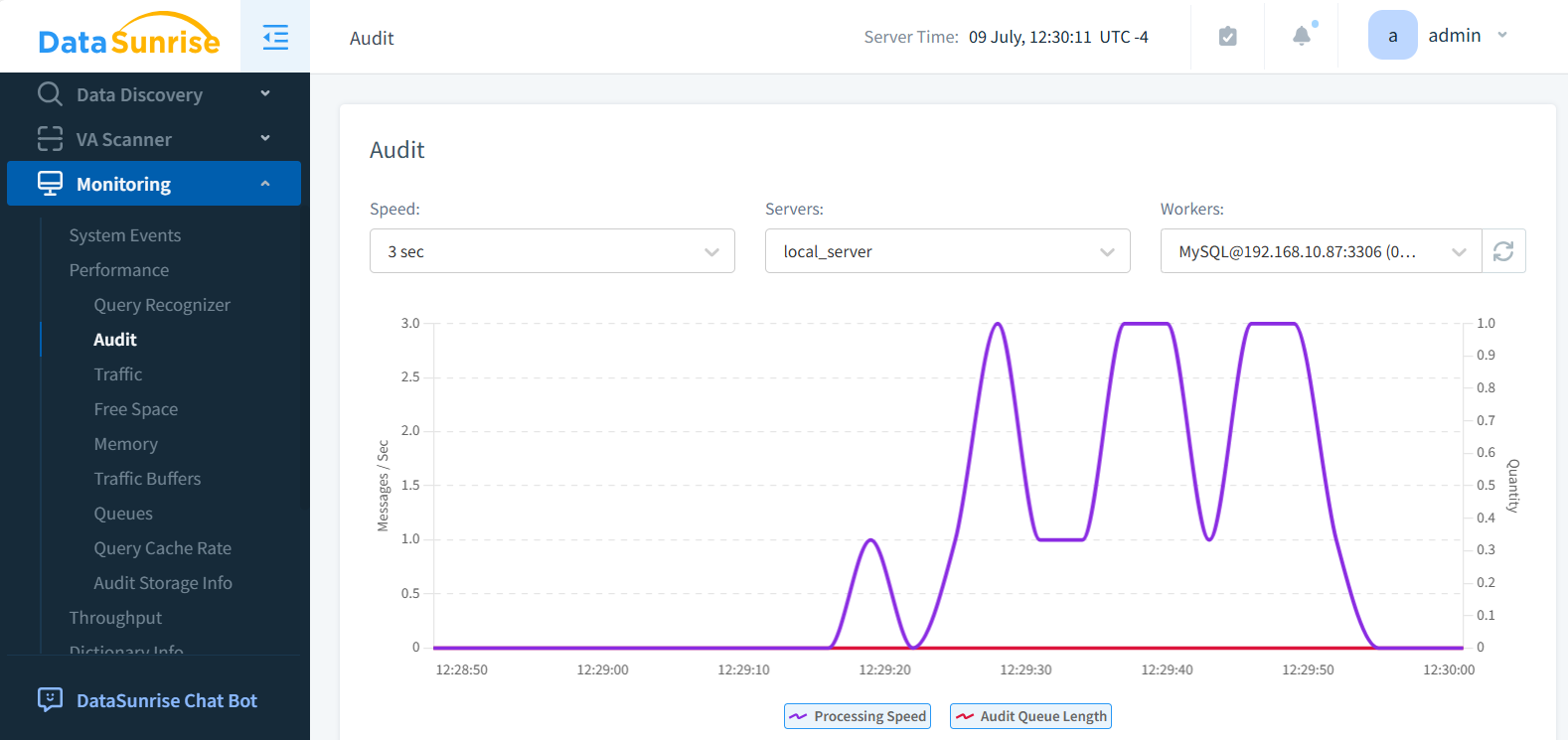
The image below showcases DataSunrise’s powerful Monitoring Tool, a comprehensive solution for database performance oversight. This intuitive interface not only provides a high-level view of database activity but also offers deeper insights through its integrated Traffic and Memory monitoring features.
These sub-elements, visible within the tool’s interface, allow for granular analysis of network traffic patterns and memory utilization, enabling database administrators to quickly identify and address potential performance bottlenecks or security concerns. By presenting multiple monitoring aspects in a single, unified dashboard, DataSunrise empowers users to maintain optimal database performance and security with ease.
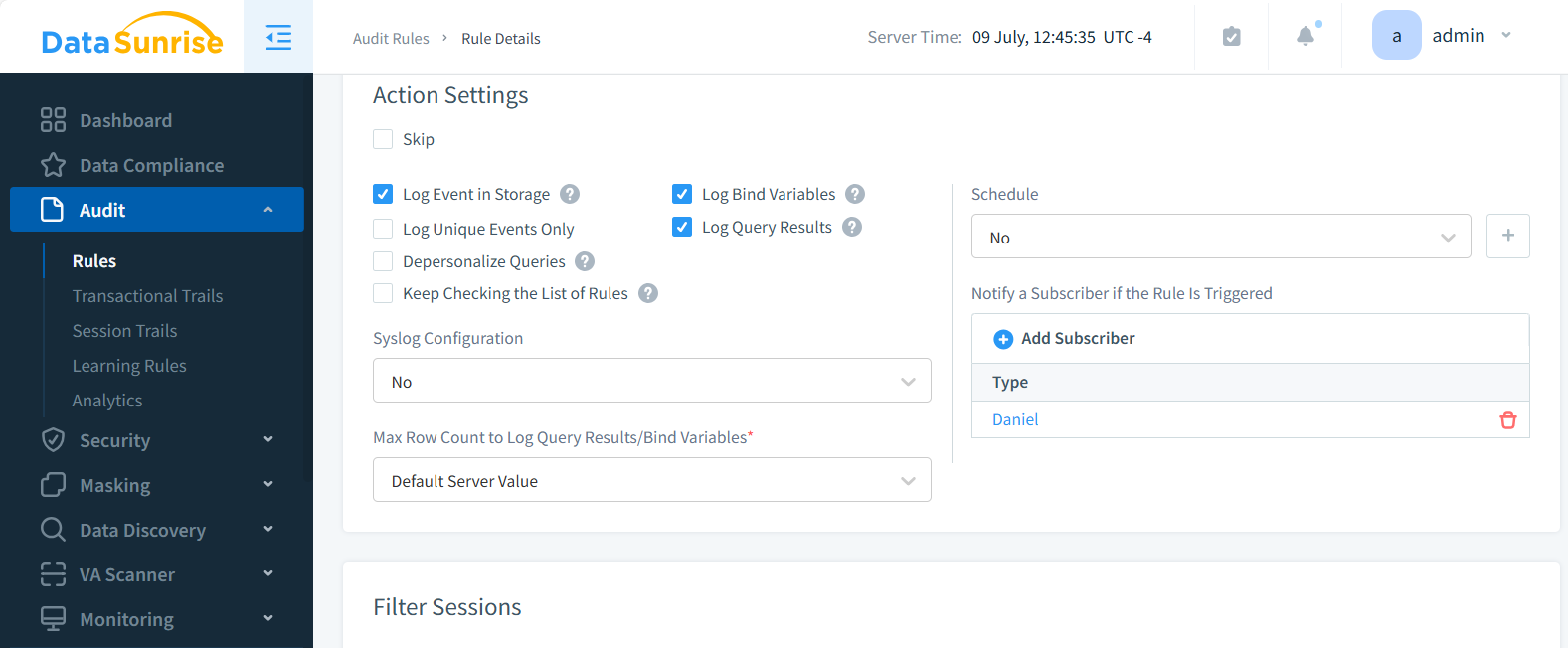
2. Alerting System
When suspicious activities are detected, DAM tools can send instant alerts to administrators. On the picture below you can see the Subscriber added to control the database events like access to some data or query failures. The DataSunrise automatically informs on the failed login attempts in the Dashboard with no prior setup.
3. Audit Trails
DAM creates detailed logs of all database activities, which can be crucial for forensic analysis and compliance reporting.
4. Query Profiling
This feature analyzes SQL queries to identify performance issues and optimization opportunities.
DataSunrise functions as a reverse proxy for database servers, a key feature that significantly enhances its Database Activity Monitoring (DAM) capabilities. This architecture allows DataSunrise to intercept and analyze all database traffic in real-time, providing comprehensive monitoring without impacting database performance. When designing your DAM infrastructure, it’s crucial to understand this reverse proxy functionality to optimize security, ensure seamless integration, and maximize the effectiveness of your monitoring solution.
Practical Implementation of DAM
While implementing Database Activity Monitoring (DAM) in-house might seem appealing, it comes with significant challenges. The process is not only time-consuming but also technically complex, requiring extensive expertise to develop comprehensive monitoring instruments, intuitive visualization tools, and robust alerting systems. Moreover, keeping these custom solutions up-to-date with evolving security threats and compliance requirements can be an ongoing struggle.
To illustrate the intricacies involved, let’s explore the implementation of DAM in two popular database systems: PostgreSQL and MongoDB. By examining these examples, we’ll highlight why many organizations opt for specialized DAM solutions that offer out-of-the-box functionality, regular updates, and expert support.
PostgreSQL Activity Monitoring
PostgreSQL offers several built-in tools for monitoring database activity.
pg_stat_statements
This extension provides a way to track execution statistics of all SQL statements.
To enable it:
- Add pg_stat_statements to shared_preload_libraries in postgresql.conf.
- Restart the PostgreSQL server.
- Run the following SQL:
CREATE EXTENSION pg_stat_statements; Now you can query the pg_stat_statements view: SELECT query, calls, total_time, rows FROM pg_stat_statements ORDER BY total_time DESC LIMIT 10;
This will show you the top 10 time-consuming queries.
PostgreSQL Audit Extension (pgAudit)
pgAudit provides more detailed logging for compliance purposes.
To set it up:
- Install the pgAudit extension.
- Add pgaudit to shared_preload_libraries in postgresql.conf.
- Set pgaudit.log = ‘write, ddl’ to log all data modifications and schema changes.
- Restart PostgreSQL.
You’ll now see detailed audit logs in your PostgreSQL log files.
MongoDB Activity Monitoring
MongoDB provides several tools for monitoring database activity.
Profiler
MongoDB’s built-in profiler can help you identify slow queries.
To enable it:
db.setProfilingLevel(1, { slowms: 100 })This sets the profiler to log operations that take more than 100 milliseconds.
To view profiled operations:
db.system.profile.find().pretty()
MongoDB Compass
MongoDB Compass is a GUI tool that provides real-time server statistics and query profiling.
To use it:
- Download and install MongoDB Compass.
- Connect to your MongoDB instance.
- Navigate to the “Performance” tab to view real-time stats.
Best Practices for Database Activity Monitoring
- Regular Audits: Schedule regular reviews of your DAM logs and alerts.
- Baseline Establishment: Create a baseline of normal database activity to easily spot anomalies.
- Least Privilege Principle: Grant users only the permissions they need to perform their tasks.
- Encryption: Use encryption for sensitive data, both at rest and in transit.
- Continuous Improvement: Regularly update your monitoring tools and strategies based on new threats and technologies.
Summary and Conclusion
Database Activity Monitoring is an essential practice for maintaining the security, performance, and compliance of your databases. By implementing DAM tools and following best practices, you can gain valuable insights into your database operations, detect potential threats, and optimize performance.
Whether you’re using PostgreSQL, MongoDB, or any other database system, there are both built-in and third-party tools available to help you monitor and secure your data effectively. Remember, DAM is not a one-time setup but an ongoing process that requires regular attention and updates.
By prioritizing Database Activity Monitoring, you’re taking a proactive approach to database management, ensuring that your valuable data remains secure and your database operations run smoothly.
For those seeking a comprehensive, user-friendly solution for database security, including advanced DAM capabilities, consider exploring DataSunrise. Our flexible tools offer robust monitoring and protection for various database systems. We invite you to visit our website for an online demo and discover how our solutions can enhance your database security strategy.
