
Data Compliance Regulations

Introduction
In today’s digital age, data has become a valuable asset for organizations. However, with the increasing use of data comes the responsibility to protect it. This is where data compliance regulations become relevant. This article explains data compliance rules, why they matter, and how they safeguard sensitive information.
What are Data Compliance Regulations?
Data compliance regulations are rules that organizations must follow to handle, store, and protect sensitive data properly. These regulations aim to safeguard personal information, maintain data integrity, and prevent unauthorized access or misuse of data.
Examples of regulations include:
- General Data Protection Regulation (GDPR) in the European Union
- Health Insurance Portability and Accountability Act (HIPAA) in the United States
- Payment Card Industry Data Security Standard (PCI DSS) for credit card data
Sources of Data Subject to Compliance Regulations
Data compliance regulations apply to various sources of data that organizations collect, process, and store. These sources can include:
- Customer data: Personal information collected from customers, such as names, addresses, email addresses, and payment details.
- Employee data: Sensitive information related to employees, including social security numbers, health records, and performance evaluations.
- Financial data: Confidential financial information, such as bank account numbers, credit card details, and transaction records.
- Medical data: Protected health information (PHI) collected by healthcare providers and insurance companies.
Organizations must ensure that they handle and secure these data sources in accordance with the relevant data compliance regulations.
Security Aspects of Data Compliance Regulations
Data security is a critical component of data compliance regulations. These regulations outline specific security measures that organizations must implement to protect sensitive data from unauthorized access, breaches, and misuse. Some key security aspects include:
- Access controls: Implementing strict access controls to ensure that only authorized personnel can access sensitive data.
- Encryption: Encrypting data both at rest and in transit to protect it from interception and unauthorized access.
- Data backup and recovery: Regularly backing up data and having a robust disaster recovery plan in place to ensure business continuity.
- Security audits: Conducting regular security audits to identify vulnerabilities and assess the effectiveness of security measures.
By following these security rules, organizations show they follow data laws and gain trust from customers and stakeholders.
Examples of Data Compliance Regulations in Action
Let’s look at a couple of examples to understand how regulations work in practice:
Example 1: GDPR Consent and Data Deletion
Under GDPR, organizations must obtain explicit consent from individuals before collecting and processing their personal data. Let’s say a company wants to send marketing emails to its customers.
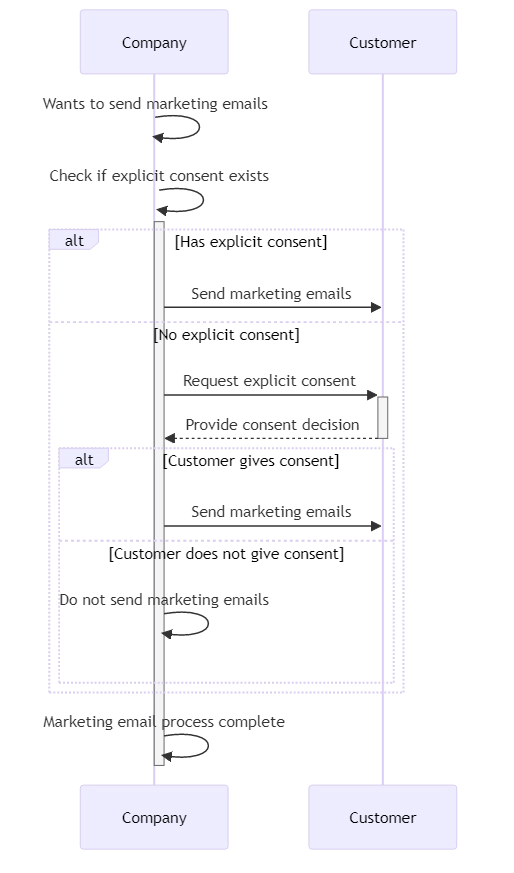
Before doing so, they must:
- Clearly explain the purpose of collecting the email addresses.
- Obtain explicit consent from customers to send them marketing communications.
- Provide an easy way for customers to withdraw their consent and unsubscribe from the emails.
If a customer wants their personal data deleted, the company must do so within a reasonable timeframe.
Example 2: HIPAA and Data Access Logs
HIPAA requires healthcare organizations to maintain detailed access logs for electronic protected health information (ePHI).
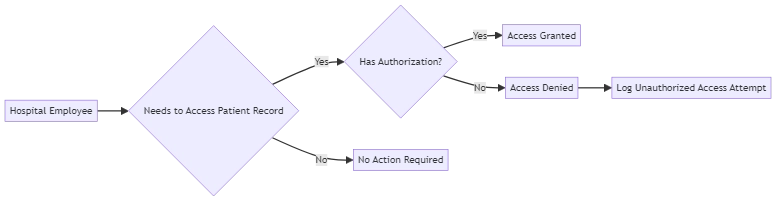
These logs must record:
- Who accessed the ePHI
- When the access occurred
- What actions did someone perform (e.g., viewing, modifying, or deleting data)?
Healthcare organizations must have good logging systems to regularly check for any suspicious activities or unauthorized access attempts.
Conclusion
Data compliance regulations play a crucial role in protecting sensitive information and ensuring the responsible use of data. Organizations can protect their data and maintain trust by following regulations and implementing security measures.
Data compliance is a continuous process. Organizations need to keep current with new rules and best practices to stay compliant. Partnering with a reliable data management solution provider, such as DataSunrise, can greatly simplify the compliance journey.
DataSunrise offers exceptional and flexible tools for data security, audit rules, masking, and compliance. Contact our team for an online demo to see how DataSunrise can help your organization with data compliance regulations.
Investing in data compliance is important to show customers that their information is safe and gain their trust.
