
3 Ways to Prevent Connecting Directly to Oracle Database Bypassing DataSunrise
The main principle of any firewall operation is to analyze network traffic in order to accept or reject the connections and the services according to a set of rules. Thus, only authorized traffic defined by the local security policy will be allowed to pass. In the meantime, a firewall cannot protect against the attacks that bypass the firewall.
The DataSunrise platform can be configured to serve as a database firewall. Thus, DataSunrise will be able to analyze database traffic and action based on the predefined rules. But DataSunrise goes beyond the “reject” or “accept” operations and allows to obfuscate sensitive data, to monitor database queries, to track suspicious activities, etc. As in the case of a firewall, DataSunrise is able to protect a database if traffic is going solely though DataSunrise.
This article discusses various approaches to database protection using the DataSunrise solution.
Reject Direct Database Connections
It is important to disallow any direct connections to a database. All the traffic should go through DataSunrise, to avoid any unauthorized actions. This can be easily achieved by filtering all the traffic going through the database port to the traffic coming only from the DataSunrise host box.
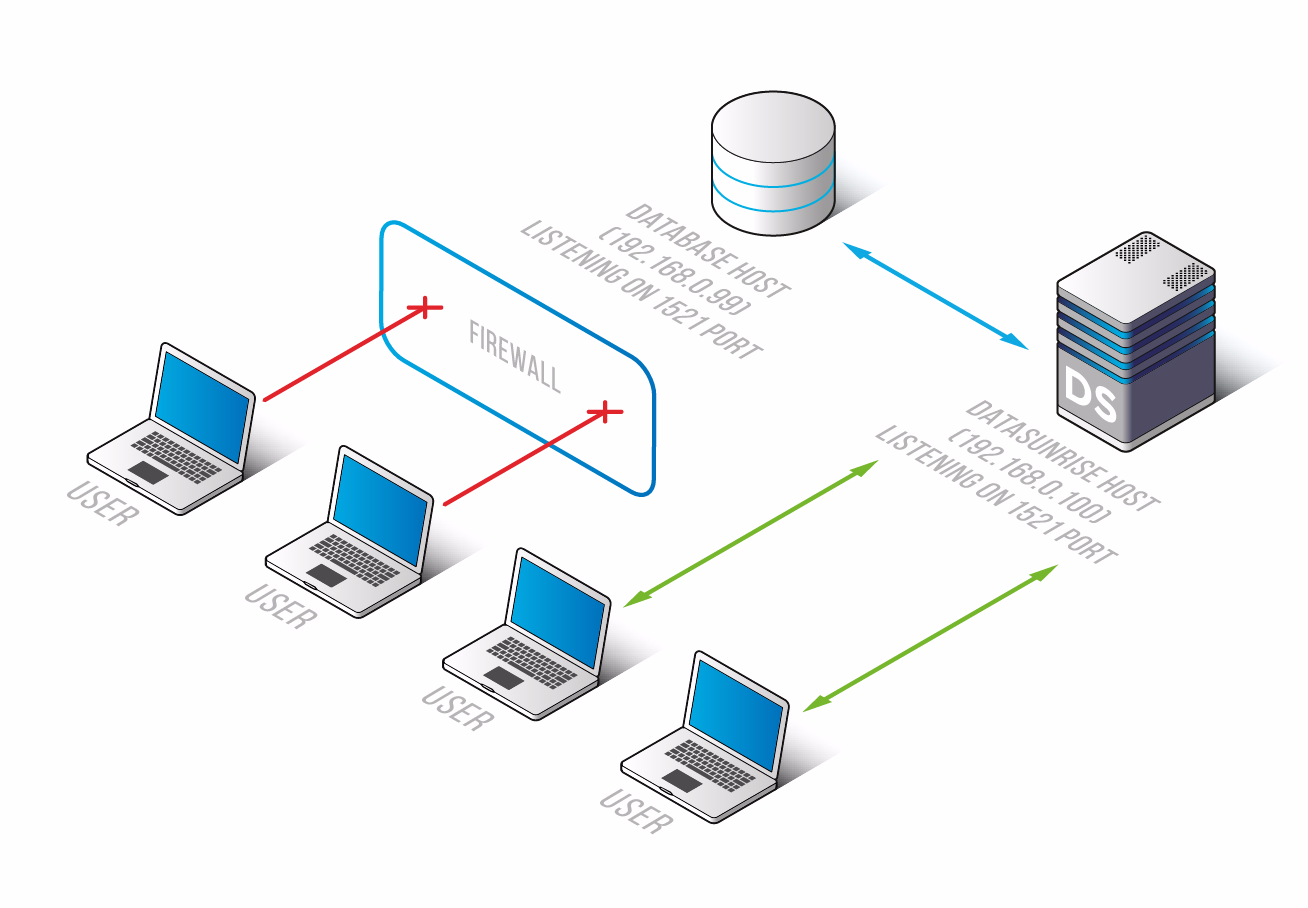
In this environment we’re using a configuration when DS and the database are installed on the separate hosts. The database host machine has the 192.168.0.99 IP address and port 1521 is open to accept any database connections. DataSunrise is installed on the same network and is reachable through the 192.168.0.100 IP address. It is configured as the database firewall for Oracle Database running on the 192.168.0.99 host.
To allow traffic solely from DataSunrise box the following commands need to be executed on the database host:
iptables -I INPUT -p tcp -s 192.168.0.100 --dport 1521 -j ACCEPT
iptables -I INPUT -p tcp -s 0.0.0.0/0 --dport 1521 -j DROPThis allows traffic from the DataSunrise host machine and bans any external clients from connecting to the database directly.
Protect DataSunrise Host and Database Host Boxes
Since we allow direct database traffic solely from DataSunrise, the DataSunrise host needs to be configured to restrict any unauthorized access to the host. Users can still bypass DataSunrise by connecting to the database from the database host so access to the database host has to be restricted as well. In addition, access to any operating system accounts used for configuring and maintaining a database has to be strictly limited.
Restrict Connections Using Database Services
Some databases have a built-in mechanism to restrict connecting to the database. This configuration can be used to prohibit connecting to a database using the built-in services instead of using the firewall configuration. In the meantime, this configuration can coexist with the firewall configuration to provide strongest database protection.
In particular, the Oracle Net “valid node checking” security feature can be used to allow or deny access to the Oracle server processes from the network clients with the specified IP addresses. To activate the “valid node checking” feature the following parameters are to be added into the sqlnet.ora file:
tcp.validnode_checking = yes
tcp.invited_nodes = 192.168.0.100Once the parameters have been applied, the Oracle listener will allow database connections coming solely from the DataSunrise host.
Conclusion
Use this article as a guide to make sure that all the traffic to your database goes solely through DataSunrise and enjoy the total security of your data! The best solution to keep your data intact is Firewall for Oracle.
If you can’t prevent users from connecting your database directly you can use DataSunrise’s Trailing the Database Audit Logs feature. It enables you to get auditing results collected by Oracle native audit tools. First and foremost, this feature can be used on Amazon RDS Oracle databases because DataSunrise doesn’t support sniffing on RDS databases. Data masking and blocking of queries are not possible in this mode.
