
Advanced Solution for Database Audit and Database Activity Monitoring
Almost every large organization has a special department to fight against information security threats. In most cases, its department staff has to perform the following tasks:
- Detection of user passwords cracking and network ports scanning.
- Prevention of computer virus infections.
- Detecting of malicious and illegal software installed on company employees’ PCs.
- Internet fraud prevention.
- Revealing of errors and problems of information systems operation cycle (process).
- Detection of software errors and system malfunctions.
- Revealing of potential vulnerabilities in security and data storage systems, which can be used to perform data breach.
In most cases all the previously mentioned means used for protection against third-party hackers. However, the insider threats could be not less dangerous than hacker attacks. Insider threats called that way because their source is company’s own employees or hired contractors. In most cases of insider-driven incidents, the data thefts or data leaks are done via email, messengers, social networks, cloud storage and the like.
There are a lot of DLP solutions on the market today for data leak channels control. However but in practical life, the violators use not only email and web applications. Various types of databases are widely used to store sensitive data in today’s corporate environment. These DBMSs and associated applications interact with each other through the specific protocols. The problem is that many DLP solutions are not capable of scanning database-specific traffic, so it is necessary to use dedicated software.
Database Activity Monitoring by DataSunrise
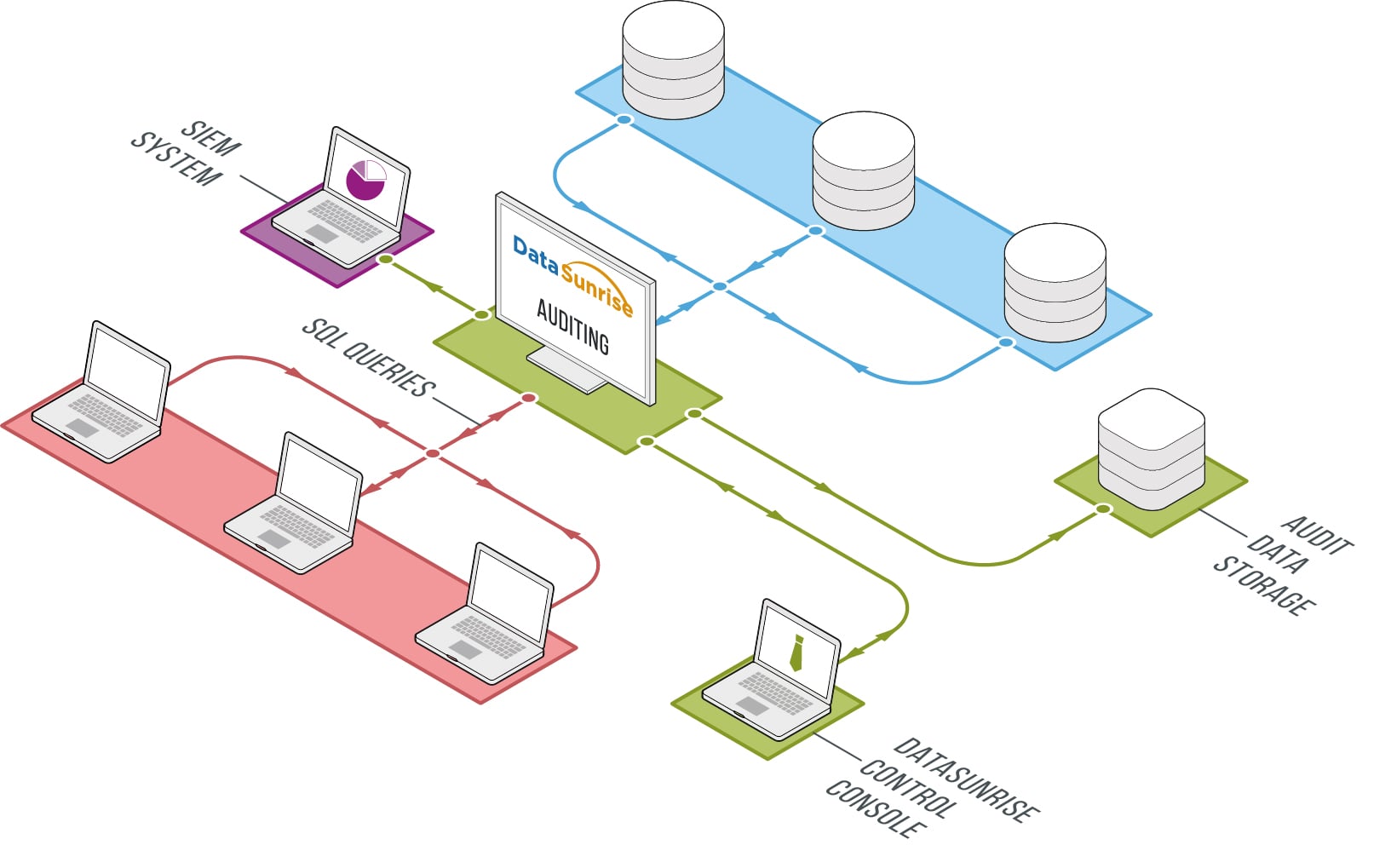
DataSunrise Database Security Suite is purpose-built for database traffic analysis. The database monitoring functionality performs database auditing. Auditing results can be stored in a built-in database or exported to external SIEM-systems for analysis.
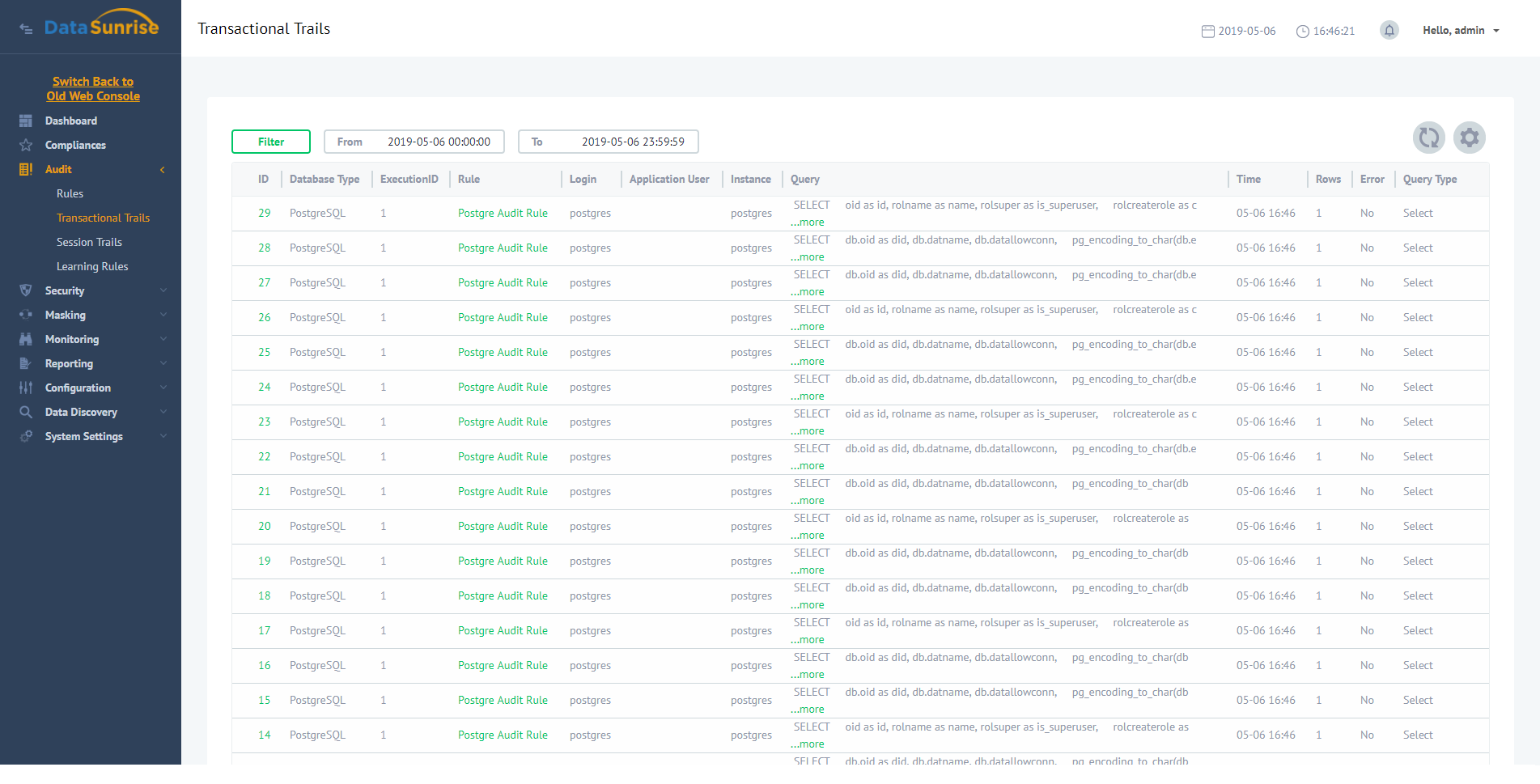
While performing database auditing, DataSunrise collects the following information:
First and foremost, audit results evaluation helps to detect the culprit of data leak and to evaluate its cost. But database auditing also enables you to prevent data theft by revealing suspicious user behavior (for example, queries which are not typical for certain users, attempts to access database elements they are not allowed to view etc.).
DataSunrise Database Audit – Database Activity Monitoring module also features a self-learning algorithms that DataSunrise uses to log SQL queries typical for the given database. Because these queries resemble normal user behavior, they are considered as safe by default, thus all other queries can be considered as suspicious and should be blocked or inspected more thoroughly.
DataSunrise Data Audit and SOX Compliance
Section 404 of SOX establishes the following requirements on database audit:
- 1.1 Monitoring database access by privilege users and “masqueraders”
- 1.2 Monitoring changes in privileges
- 1.3 Monitoring access failures
System Events section of DataSunrise provides comprehensive logs on database connection, authentication attempts, security policy changes, privilege assignment and other system events, which helps to prevent exceeding of authority by insiders and to protect data privacy and governance.
- 1.4 Monitoring schema changes
- 1.5 Monitoring direct data access
DataSunrise continuously monitors changes made to database content and provides comprehensive logs containing the following:
- SQL code of intercepted queries.
- Session information: user names, client applications, session duration time, IP addresses (hostnames) queries came from and so on.
- Target database information: database instance which received user queries, number of database entries that were affected by incoming query.
- Database errors.
DataSunrise Data Audit and PCI DSS
PCI DSS Requirement 10 defines obligations of affected organizations pertaining to monitoring and tracking of cardholder data, which include:
- 10.1 Implement audit trails to link all access to system components to each individual user.
Logs contain data on all actions of the user since opening the session till it’s closing, including the database elements the user accessed.
- 10.2 Implement automated audit trails for all system components to reconstruct the following events: 10.2.1 Verify all individual access to cardholder data is logged. 10.2.2 Verify all actions taken by any individual with root or administrative privileges are logged.
- 10.3.1 Verify user identification is included in log entries. 10.3.2 Verify type of event is included in log entries. 10.3.3 Verify date and time stamp is included in log entries. 10.3.4 Verify success or failure indication is included in log entries. 10.3.5 Verify origination of event is included in log entries. 10.3.6 Verify identity or name of affected data, system component, or resources is included in log entries.
DataSunrise DAM solution tracks logs on all database events including culprit of queries, detailed session data, error logs, SQL codes of the queries, results of their execution, and all required parameters are given above. There is also the Data Discovery feature that helps to detect and organize sensitive data including credit card numbers.
- 10.5 Secure audit trails so they cannot be altered. 10.5.3 Promptly back up audit trail files to a centralized log server or media that is difficult to alter. 10.5.4 Write logs for external-facing technologies onto a secure, centralized, internal log server or media device.
Audit logs are stored in specified PostgreSQL, MySQL database, DataSunrise integrated SQLite database. Storing logs in external databases with separate authentication requirement allows you to conform to the above requirements and prevents attackers from tracking up their traces. DataSunrise generates audit reports in csv and pdf formats. DataSunrise also has a report functionality which views information on target database traffic as tables or diagrams. For real-time analysis of database audit results, DataSunrise can be integrated with almost every existing SIEM-system due to Syslog protocol support.
- 10.6 Review logs and security events for all system components to identify anomalies or suspicious activity. Note: Log harvesting, parsing, and alerting tools may be used to meet this Requirement.
Each audit rule of DataSunrise has an option to add subscribers that will receive a notification whenever the rule is triggered. Properly configured audit rules help to conform to the above requirement and save a lot of time for DBAs.
Note: Some of the sub-clauses of requirements are not mentioned as they require measures on the part of the product acquirer.
Conclusion
Security and audit settings of DataSunrise are highly scalable and easy-to-use. Spend some time to properly configure privacy and audit policies, this will automate main daily routine procedures of monitoring, simplify the required procedures and save time of your employees.
Database audit helps to perform both data leak investigation and prevention. Thus DataSunrise Database Audit functionality is another line of defense of your precious information.
DataSunrise supports all major databases and data warehouses such as Oracle, Exadata, IBM DB2, IBM Netezza, MySQL, MariaDB, Greenplum, Amazon Aurora, Amazon Redshift, Microsoft SQL Server, Azure SQL, Teradata and more. You are welcome to download a free trial if would like to install on your premises. In case you are a cloud user and run your database on Amazon AWS or Microsoft Azure you can get it from AWS market place or Azure market place.
