Data Audit with DataSunrise:
All-Day Security Monitoring and Recording
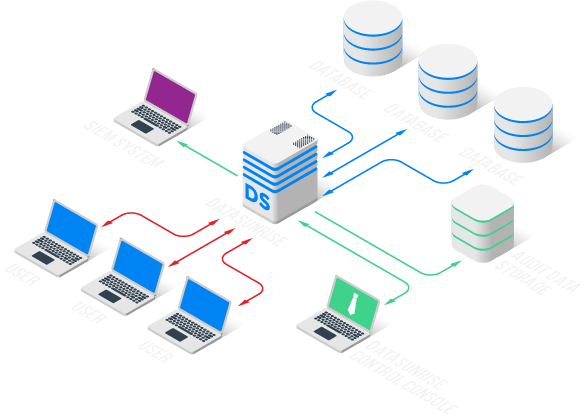
Our flexible and user-friendly database audit subsystem tracks database queries and other activities. DataSunrise Database Audit operates in various deployment modes, each offering different performance levels and feature sets. The proxy mode provides the most comprehensive set of features, including both passive (logging, behavior analysis) and active (blocking security rules) data security components.
Data Audit identifies an organization’s data usage patterns – a crucial first step for security and compliance.
Try our solutions in the Cloud or on-Premises










Increase Visibility into Database Activity

Meet Compliance Regulations
Data Audit with DataSunrise offers strong protection for sensitive data, ensuring compliance with major national and international regulations such as SOX, HIPAA, and PCI DSS. It provides continuous auditing and reporting of activities involving sensitive data. The solution’s self-managing regulatory compliance automation eliminates the need for manual intervention, streamlining your data protection processes.

Security Control
Instant capture of events that triggered security policies. Store audit records in a separate database. You can select to store in an internal built-in database or external database, S3, or send audit results to SIEM.
Notification system of audit events via email, SNMP or instant messengers.

Audit Management
Simplified audit management and segregation of duties from administrative privileges to read-only access to audit settings. Flexible settings to audit queries from certain hosts, IP addresses, client applications, users, and more.
Customizable traffic filters with sufficient granularity up to the column level.
Explore our PostgreSQL Data Audit playlist for comprehensive information on the data audit workflow. This collection includes YouTube videos covering both DataSunrise’s approach and PostgreSQL’s native audit capabilities, allowing you to compare these methods effectively.

Stealth Monitoring
Get proxy functions with the possibility of Sniffer mode. It logs all database events, while the launch does not require any additional configuration of databases or client applications.
The advantage of DataSunrise is that you can make flexible deployment, depending on your security needs, and integrate functions with the Database audit trail.
6 Reasons for Using DataSunrise:
SIEM Integration
Exports audit results to external SIEM systems with Syslog messages, which provides detailed reports
Increased Security
Timely protection against third-party hackers, insider threats, data thefts and data leaks
Profitable Solution
Low cost of maintaining the quick setup of DataSunrise security program and supporting related standards
Learning Mode
An integrated self-learning engine for memorizing activity and simplifying security policy configuration
Real-Time Alerting
Alerts via Email and messengers to send immediate notifications to the administrator about suspicious activity
Selective Audit
Customizable traffic filters with sufficient granularity up to the column level
Discover Opportunities with DataSunrise
Download Free Trial
- Sensitive and PII data auditing, discovery and active protection in on-prem and cloud environments
- Detect access rights abuse attempts and prevent data breach preparations in advance
- DataSunrise analyzes typical user and application behavior and creates an allow list of secure SQL queries to notify of a change in user activity
- Centralized management and continuous monitoring of databases in the cloud or on-prem help to maintain full compliance
Supported Databases and Platforms:
SQL and NoSQL, in the Cloud and on-Premises
Specification
Description
SQL
- All RDS Databases
- AlloyDB
- Amazon Athena
- Amazon Aurora
- Amazon Redshift
- Apache Hive
- Apache Impala
- Azure Synapse Analytics
- Cloudberry Database
- CockroachDB
- GaussDB
- Google BigQuery
- Google Cloud SQL
- Greenplum
- Heroku Postgres
- Hydra
- IBM Db2
- IBM Db2 Big SQL
- IBM Informix
- IBM Netezza
- MS SQL Azure
- MS SQL Server
- MariaDB
- MySQL
- Neo4j
- Oracle
- PostgreSQL
- Percona Server MySQL
- SAP HANA
- Snowflake
- Sybase
- Teradata
- TiDB
- Vertica
- YugabyteDB
NoSQL
Why Take Chances with DataSunrise?
We are number one choice for customers in the fields of healthcare, medicine, insurance, and financial services worldwide.
See for yourself the benefits of our products!
Request a DemoProtect Your Data
DataSunrise security and monitoring settings of are highly scalable and easy-to-use.


