AI for Threat Hunting
As artificial intelligence reshapes cybersecurity, 67% of organizations now use AI to strengthen their defense strategies. Yet, most SOC teams still struggle to keep up with the avalanche of alerts and complex attack chains that evolve faster than legacy systems can respond.
This guide examines AI for Threat Hunting, explaining how machine learning transforms real-time detection and response in modern SOC environments.
DataSunrise’s advanced AI/ML Security platform delivers Zero-Touch Security Orchestration with Autonomous Threat Detection, Context-Aware Protection, and Surgical Precision across 50+ supported platforms.
Understanding AI-Driven Threat Hunting
AI-driven threat hunting leverages machine learning models to identify anomalies and suspicious behavior that traditional SIEM rules might miss. Unlike static signature-based systems, AI models continuously learn from live database activity monitoring data, adapting to new tactics and minimizing false positives.
Traditional tools rely on human-defined thresholds, while DataSunrise’s machine learning tools autonomously correlate patterns across audit trails, role-based access controls, and database firewalls. This delivers real-time context, ensuring threats are detected with maximum accuracy and minimal noise.
Critical AI Threat Vectors in SOC Environments
AI brings precision—but it also introduces new attack surfaces. SOC teams must watch for these critical vectors:
- Model Poisoning: Attackers manipulate training data to corrupt AI decision-making. DataSunrise mitigates this through continuous data protection and audit logs.
- Adversarial Evasion: Subtle input alterations deceive classifiers. By combining filtering with behavior analytics, DataSunrise exposes these anomalies before damage occurs.
- Data Exfiltration via APIs: Unauthorized access paths leak sensitive data. DataSunrise enforces access controls and dynamic data masking to restrict exposure.
- Privilege Escalation Attacks: Compromised accounts gain unauthorized admin rights. With least privilege enforcement and real-time notifications, DataSunrise keeps escalation attempts under control.
Each layer integrates seamlessly with DataSunrise’s security policy framework, delivering “Maximum Security, Minimum Risk.”
Implementing AI for Threat Hunting
Effective AI threat hunting requires models that understand behavioral baselines and can flag deviations autonomously. DataSunrise’s ML-powered analyzers exemplify this with adaptive risk scoring.
Example: AI Threat Detection Engine
class AIThreatEngine:
"""
Template-aligned detector that mirrors DS-style signal fusion.
Inputs are stitched from Audit Trail, Activity Monitoring/History,
RBAC, Firewall, and Data Discovery contexts.
"""
def __init__(self, z_thr: float = 2.5):
# simple per-entity baseline knobs (stand-in for UBA profiles)
self.z_thr = z_thr
def analyze(self, ev: dict) -> dict:
"""
ev example:
{
"user":"svc_app", "role":"report_reader",
"action":"SELECT", "object":"customer.ssn",
"is_sensitive": True, # from Data Discovery tags
"rule_matches": ["high_risk_read"], # Audit Rules hits
"firewall_blocked": False, # Database Firewall event
"qps_z": 3.1, # deviation vs per-user baseline
"err_z": 0.4, # errors vs baseline
"peer_dev": 2.2 # peer-group deviation
}
"""
# Core anomaly score (z-scores + peer deviation)
score = max(ev.get("qps_z", 0), ev.get("err_z", 0), ev.get("peer_dev", 0))
# Contextual boosters (policy correlation)
if ev.get("is_sensitive"):
score += 0.7
if ev.get("rule_matches"):
score += 0.8
if ev.get("firewall_blocked"):
score += 1.0
if ev.get("role") == "report_reader" and ev.get("action") not in ("SELECT",):
score += 0.5 # least-privilege nudge
sev = "LOW"
if score >= self.z_thr + 1.0:
sev = "HIGH"
elif score >= self.z_thr:
sev = "MEDIUM"
return {
"threat_detected": sev != "LOW",
"risk_score": round(score, 2),
"severity": sev,
"explanations": {
"baseline_signals": ["qps_z", "err_z", "peer_dev"],
"policy_context": ["is_sensitive", "rule_matches", "firewall_blocked"]
},
"recommendations": [
"Open audit trail and correlate with matched audit rules.",
"Enable/verify dynamic masking on sensitive objects.",
"Review RBAC/least-privilege and tighten if needed.",
"Subscribe Slack/SIEM notifications for HIGH events; generate report."
],
}
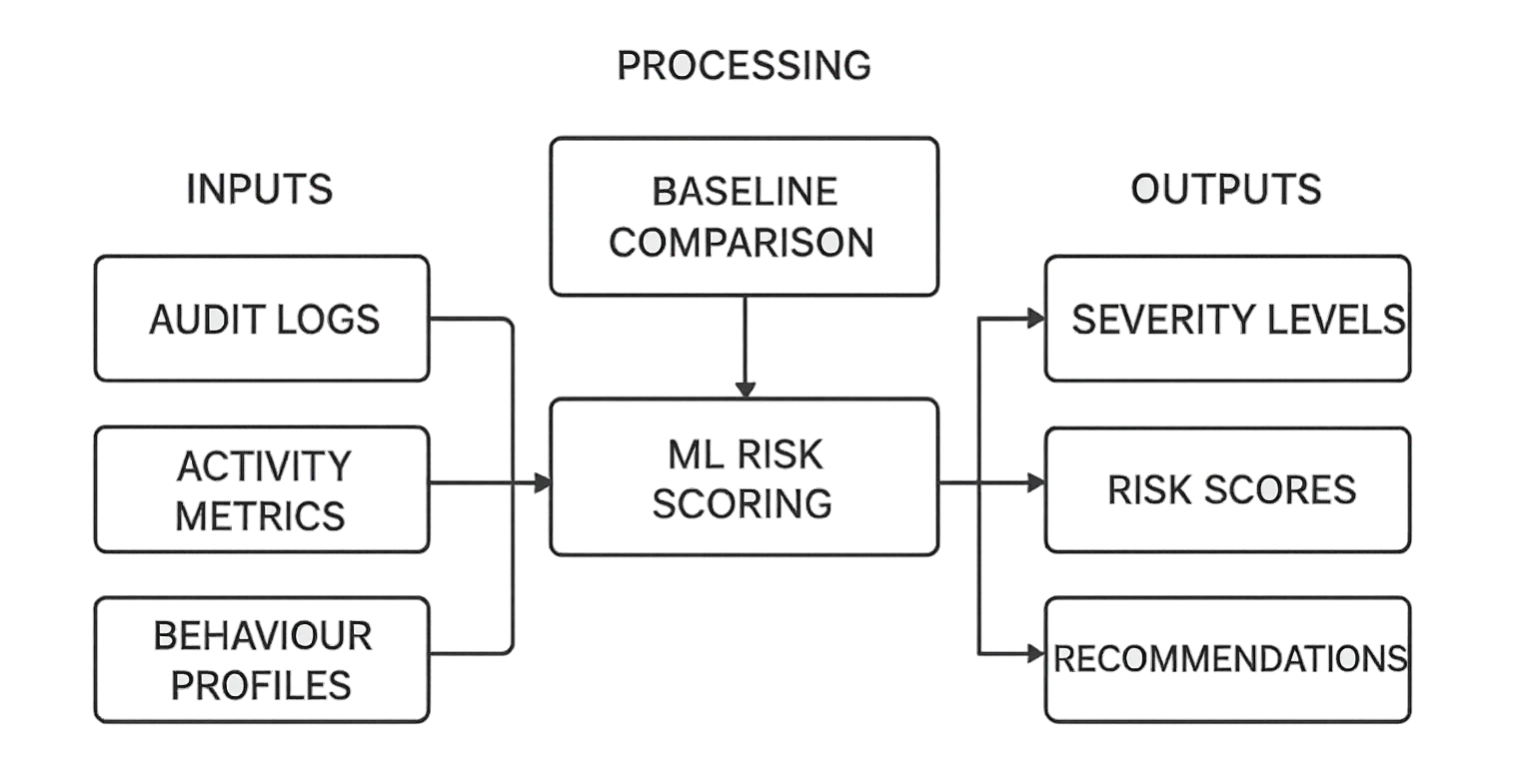
This example illustrates how DataSunrise’s AI Threat Engine fuses anomaly metrics with contextual security data. It combines user behavior baselines, peer-group deviations, and policy signals from audit trails, activity history, role-based access controls, and database firewall events. By weighting each signal, the engine produces adaptive risk scores and prioritizes alerts for sensitive or policy-violating actions—turning AI detection into a unified, actionable defense workflow within DataSunrise.
Adjust the anomaly threshold dynamically based on user behavior trends and database workload patterns. It helps reduce alert fatigue and improve detection accuracy.
Implementation Best Practices
For Organizations:
- Establish AI Governance Frameworks: Define roles, audit cycles, and security policies. DataSunrise simplifies governance through centralized dashboards.
- Adopt Zero-Trust Principles: Combine role-based access controls with database encryption.
- Leverage Continuous Monitoring: Integrate database activity monitoring and user behavior analytics.
- Ensure Compliance Readiness: Use DataSunrise’s Compliance Manager for automated GDPR, HIPAA, and PCI DSS validation.
For Technical Teams:
- Correlate Threat Data: Feed SOC telemetry into DataSunrise’s audit trails and data discovery modules for unified analysis.
- Automate Response Workflows: Configure real-time notifications and report generation.
- Harden ML Pipelines: Enforce reverse proxy and database firewall rules against adversarial data streams.
- Integrate Threat Intelligence: Use vulnerability assessment tools for proactive risk scoring.
When integrating DataSunrise with external SIEM platforms, ensure event normalization aligns with your SOC’s existing schema to maintain correlation accuracy.
DataSunrise: Comprehensive AI/ML Scenario Security Solution
DataSunrise’s AI/ML Security Platform is engineered for “AI Compliance by Default,” combining ML-Powered Analytics and Autonomous Threat Correlation for end-to-end protection across hybrid infrastructures.
Key Features:
- ML-Powered Threat Correlation: Real-time pattern detection across database activity monitoring.
- Context-Aware Access Controls: Dynamic policy enforcement using role-based access control (RBAC).
- Autonomous Data Masking: Adaptive dynamic data masking for sensitive datasets.
- Cross-Platform Orchestration: Support for over 40 data storage platforms.
- Real-Time Compliance Auditing: Continuous validation with audit logs and compliance regulations.
DataSunrise integrates seamlessly with enterprise SIEM and SOAR systems, giving SOC teams visibility, control, and automation from one unified pane.
Conclusion: Elevate Your SOC with AI-Driven Precision
AI-based threat hunting marks the next frontier in security operations. By merging autonomous machine learning with context-aware analytics, organizations can shift from reactive to predictive defense.
DataSunrise’s Zero-Touch Security Orchestration empowers SOCs to detect, correlate, and neutralize threats with Surgical Precision and AI-Compliance by Default.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now