AI in Network Security
As artificial intelligence reshapes cybersecurity, 81% of organizations now employ AI to enhance network protection. Yet, growing data volumes and evolving threat vectors strain traditional defense mechanisms, demanding adaptive, context-aware protection across hybrid environments.
This guide explores the role of AI in network security, showing how machine learning strengthens monitoring, anomaly detection, and automated response systems. It also demonstrates how DataSunrise’s security framework delivers proactive, cross-platform protection with Zero-Touch Security Orchestration and Context-Aware Defense.
DataSunrise’s ML-powered platform operates with Surgical Precision—correlating behavioral analytics, database activity monitoring, and real-time audit logs to ensure every anomaly becomes an actionable insight.
Understanding AI in Network Security
AI in network security refers to using algorithms that learn from network activity to detect and mitigate threats automatically. Unlike static firewalls or signature-based intrusion systems, ML models adapt dynamically to evolving behavior patterns and contextual anomalies.
Network environments rely on continuous data discovery and access controls to stay secure. Integrating AI adds the ability to correlate massive event streams in real time—helping teams focus on incidents that truly matter instead of drowning in false positives.
Critical Network Threat Vectors
1. Advanced Persistent Threats (APTs)
ML algorithms identify subtle indicators of compromise—unusual connection persistence, exfiltration attempts, or traffic flow irregularities—beyond what traditional SIEM filters capture. User behavior analysis provides additional behavioral context.
2. Insider and Privilege Misuse
Through continuous role-based access control and privilege patterning, AI can flag abnormal resource requests or suspicious privilege escalations before breaches occur.
3. Botnets and Automated Exploits
Database firewall integration and adaptive threat scoring help block malicious automation that operates across distributed endpoints and cloud infrastructure.
4. Phishing and Social Engineering at the Network Edge
AI models analyze communication metadata to detect anomalies in packet behavior, traffic origination, or DNS patterns linked to phishing campaigns.
Implementing AI-Powered Network Security
The example below shows how a lightweight ML-based threat detector might evaluate packet flows for anomalies in real time.
from datetime import datetime
import numpy as np
class NetworkThreatDetector:
"""Machine learning-based threat detector for network traffic."""
def __init__(self, threshold: float = 0.85):
self.threshold = threshold
self.baseline_vector = np.random.rand(5)
def analyze_traffic(self, packet_vector):
similarity = np.dot(packet_vector, self.baseline_vector) / (
np.linalg.norm(packet_vector) * np.linalg.norm(self.baseline_vector)
)
threat_detected = similarity < self.threshold
return {
"timestamp": datetime.utcnow().isoformat(),
"similarity_score": round(similarity, 3),
"threat_detected": threat_detected,
"severity": "HIGH" if threat_detected else "LOW"
}
This simplified detector compares incoming packet metrics against a learned baseline. A drop in similarity indicates a deviation from normal behavior, triggering alerts or automated mitigation workflows.
Implementation Best Practices
Start small—train your AI models on one high-value dataset or system before expanding organization-wide. It’s easier to refine accuracy when you’re not drowning in noise.
For Organizations:
- Centralized Visibility: Consolidate audit trails into unified dashboards for faster anomaly tracing.
- Access Governance: Define security policies that balance detection accuracy with privacy and compliance requirements.
- Adaptive Defense Posture: Integrate vulnerability assessment outputs into your AI models for continuous feedback and model refinement.
- Compliance-Driven Security: Map AI detections to frameworks like GDPR to ensure accountability.
For Technical Teams:
- Behavioral Baselines: Maintain updated baselines using user behavior analysis and continuous telemetry.
- Real-Time Monitoring Integration: Employ database activity monitoring with adaptive filters tuned by AI insights.
- Threat Correlation Pipelines: Use reverse proxy architectures to feed consistent metadata into ML pipelines.
- Automated Response Rules: Combine AI detections with security rules that trigger automatic isolation or throttling actions.
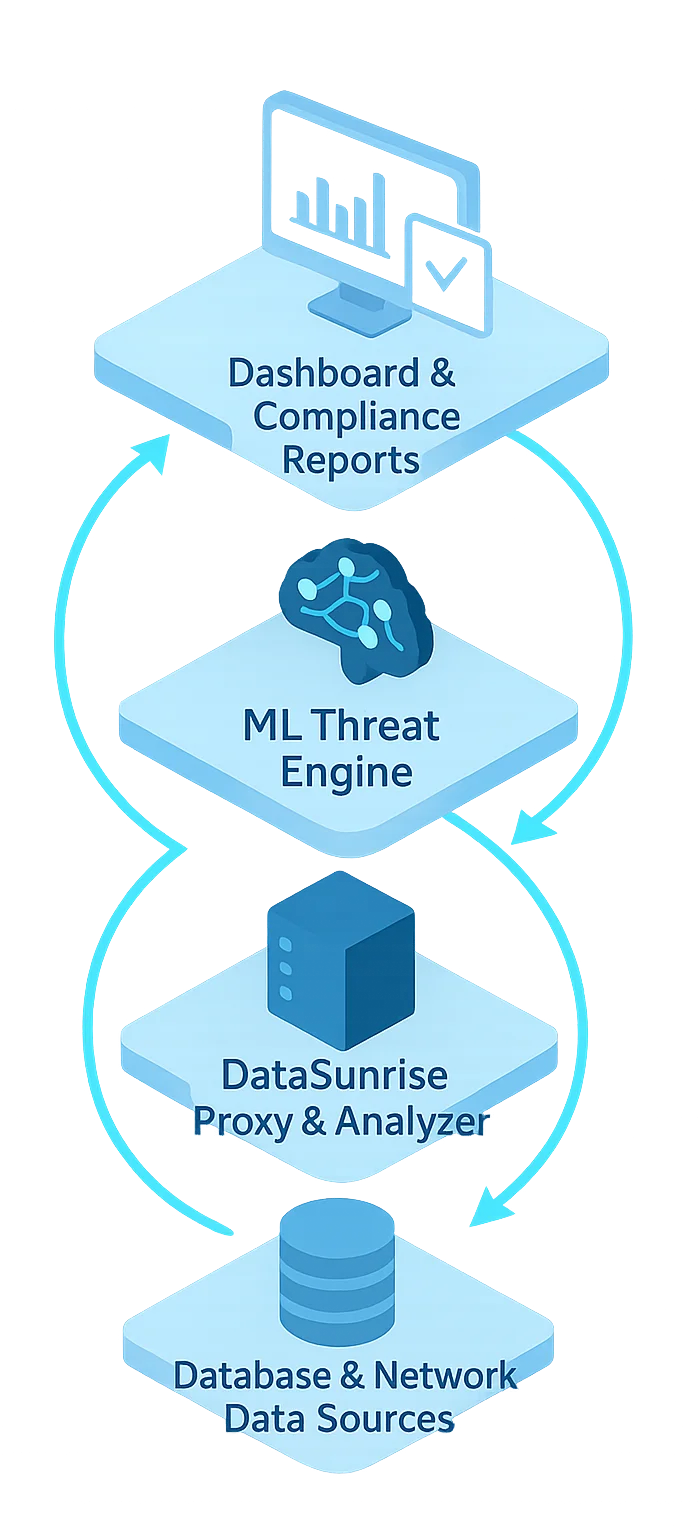
DataSunrise: Comprehensive AI Network Security Solution
DataSunrise provides unified protection across databases, applications, and network layers. Its AI-Driven Security Platform delivers Autonomous Threat Detection, Context-Aware Protection, and AI Compliance by Default across 50+ supported environments.
Conclusion: Building Smarter Defenses with AI
AI in network security transforms reactive defense into predictive resilience. By continuously learning from system patterns and contextual signals, it detects sophisticated threats before they escalate into breaches.
When paired with DataSunrise’s adaptive security tools, organizations achieve a unified defense model that bridges human expertise and machine precision.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now