
Data Audit in MySQL

Introduction
In today’s data-driven world, ensuring the security and integrity of your MySQL databases is paramount. Data breaches and unauthorized access can lead to severe consequences, including financial losses, reputational damage, and legal ramifications. This is where data auditing comes into play. This article will explain the basics of data audit in MySQL, with a focus on security. It includes examples to help protect your sensitive information.
What is Data Audit in MySQL?
Data audit in MySQL involves monitoring, recording, and analyzing database activities to prevent unauthorized access, data breaches, and security incidents.
A good data audit system helps organizations track who accessed data, when, and where. Being transparent is important for keeping data safe, following rules, and quickly finding and dealing with possible dangers.
The Importance of Data Security
Today, businesses in all industries prioritize protecting sensitive data because it is highly valuable. MySQL, being one of the most widely used relational database management systems, holds vast amounts of critical data.
From customer records and financial transactions to intellectual property and confidential documents, MySQL databases are prime targets for cybercriminals. Implementing a comprehensive data audit strategy is essential to mitigate risks and safeguard your organization’s valuable assets.
Configuring Data Audit in MySQL
To enable data auditing in MySQL, you need to configure the necessary settings and utilize the available tools. One effective approach is to leverage the power of attribute-based access control (ABAC) in MySQL.
ABAC allows you to define fine-grained access policies based on attributes associated with users, resources, and the environment. By using ABAC and data auditing together, you can closely control who accesses certain data and monitor their actions.
Here’s an example of how to configure data audit using ABAC in MySQL:
-- Enable the audit log
SET GLOBAL audit_log_format = 'JSON';
SET GLOBAL audit_log_file = '/var/log/mysql/audit.log';
SET GLOBAL audit_log = 'ON';
-- Create an audit policy
CREATE AUDIT POLICY policy_name
FOR SELECT, UPDATE, DELETE ON mydb.*
TO 'user1'@'localhost'
ATTRIBUTE '{"department":"finance","role":"manager"}'
WHEN ('hour(now())' BETWEEN '09' AND '17');In this example, we enable the audit log, specifying the log format and file location. We made a rule for user1 on localhost to view, change, and delete data in the mydb database. The policy includes an attribute condition that restricts access based on the user’s department and role. Additionally, the policy incorporates a time-based constraint, allowing access only during business hours (9 AM to 5 PM).
Monitoring and Analyzing Audit Logs in MySQL
Once you have configured data auditing, it’s crucial to regularly monitor and analyze the generated audit logs. MySQL provides built-in tools and functions to facilitate this process. For example, you can use the audit_log_read() function to read the audit log and extract relevant information.
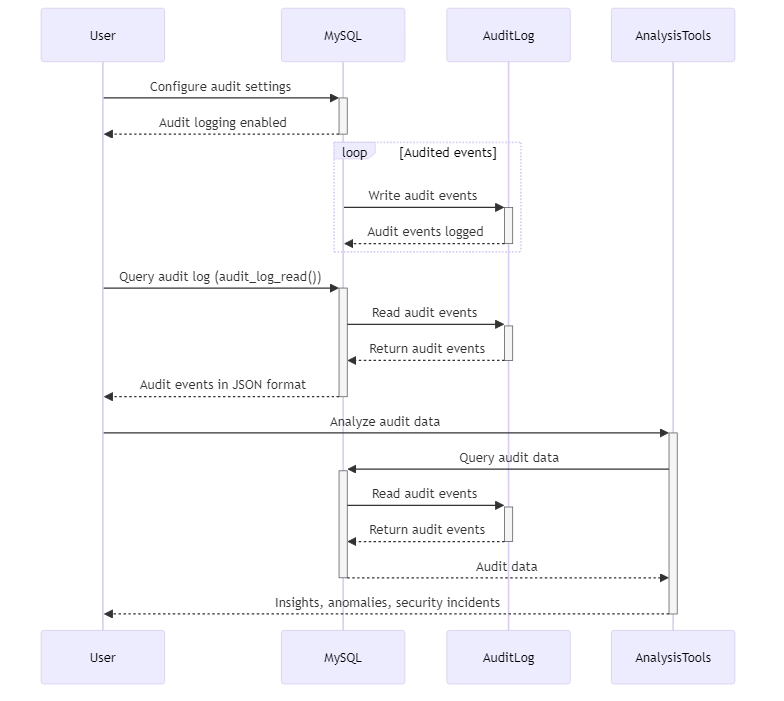
Mysql Audit Log Monitoring Example
Here’s an example of how to query the audit log:
SELECT audit_log_read('audit.log', 'start');This query reads the audit.log file and returns the audit events in JSON format. You can analyze audit data with SQL queries or tools to find suspicious activities, anomalies, and security incidents.
Enhancing Data Audit with DataSunrise
While MySQL provides basic data auditing capabilities, leveraging a dedicated data security solution like DataSunrise can significantly enhance your data audit efforts. DataSunrise offers exceptional and flexible tools for data management, including advanced security features, audit rules, data masking, and compliance support.
With DataSunrise, you can:
- Define granular audit rules to track specific events and user activities
- Implement real-time monitoring and alerting for suspicious behavior
- Apply data masking techniques to protect sensitive information
- Ensure compliance with regulations such as GDPR, HIPAA, and PCI DSS
To experience the power of DataSunrise firsthand, we invite you to schedule an online demo with our team. In the demo, you can see what the platform can do and how it can strengthen your MySQL data audit plan.
Conclusion
Data audit in MySQL is a critical component of maintaining data security and compliance. You can use a strong data audit system to monitor your database. This system helps you detect unauthorized access.
It also allows you to respond promptly to any security threats. Using ABAC and tools like DataSunrise can improve data audits, offering better security and compliance support.
Remember, safeguarding your sensitive data is an ongoing process that requires continuous monitoring, analyzing, and improvement. Regularly checking and acting on your data keeps your organization’s important information safe. It also helps maintain trust with customers and stakeholders.
You can request an online demo today to learn more about data auditing in MySQL and see DataSunrise’s data management solutions in action.
