How to Automate Data Compliance for Vertica
How to Automate Data Compliance for Vertica matters more than ever as organizations scale their analytical environments across BI dashboards, ML pipelines, ETL workflows, and real-time data services. Vertica excels at high-performance analytics, yet this same distributed architecture complicates the ability to enforce consistent compliance rules. Sensitive data often flows through multiple applications, which increases the risk of unintended exposure. Because manual enforcement cannot keep up, automation becomes mandatory for reliable compliance at scale.
Although Vertica provides powerful analytical capabilities, it does not include built-in mechanisms for dynamic masking, contextual SQL policy enforcement, or centralized audit evidence consolidation. Therefore, organizations must integrate an automated compliance layer that evaluates every SQL request, transforms results when necessary, and records activity continuously. DataSunrise delivers this automation by acting as a real-time compliance gateway in front of Vertica. As a result, compliance behavior remains predictable and enforceable, regardless of how many tools or users access Vertica.
For broader governance requirements, organizations can also rely on the DataSunrise Data Compliance framework, which provides uniform policies across multi-database deployments, ensuring Vertica remains aligned with enterprise-wide governance standards.
Why Automating Data Compliance for Vertica Is Essential
Automation becomes critical because Vertica stores data using projections, ROS/WOS containers, and distributed execution paths. Consequently, sensitive values may appear in several physical representations and propagate into multiple transformation processes. Furthermore, separate business units often share Vertica clusters, increasing the complexity of managing access privileges manually.
To solve these challenges, automated compliance systems must:
- apply policy decisions before Vertica executes the query,
- mask sensitive columns consistently across all workloads,
- capture audit records automatically in a unified format,
- adapt to schema drift without manual intervention,
- ensure compliance rules follow the user, not the tool.
By automating these protections, organizations strengthen their regulatory position and eliminate common failure points caused by manual processes or reactive governance models.
Automation Architecture: How to Automate Data Compliance for Vertica
The following diagram presents the core automation workflow. Applications send SQL traffic to the DataSunrise proxy, where requests are evaluated, output is transformed when needed, and sanitized SQL is forwarded to Vertica. This pipeline ensures that masking, auditing, and enforcement occur before data leaves the database boundary.
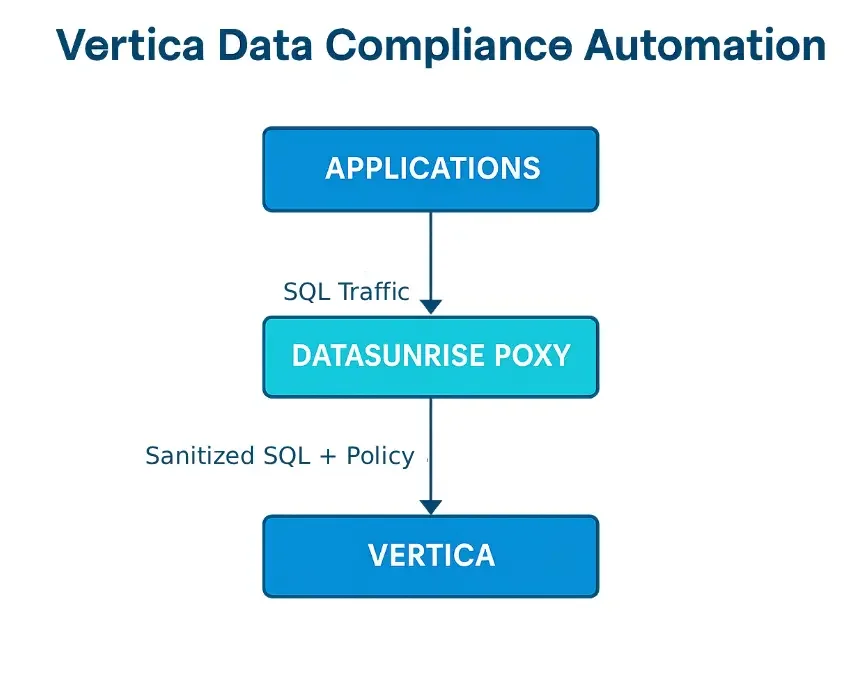
As a result, compliance logic no longer needs to be embedded individually in BI tools or ETL pipelines. Moreover, centralizing enforcement at the SQL gateway ensures uniform behavior across all business units and application environments.
Automating Masking for Vertica Sensitive Data
To automate sensitive-data protection, organizations rely on dynamic masking. This method allows analysts, developers, and service accounts to query Vertica freely while ensuring that sensitive fields remain protected. Because the transformation occurs outside Vertica and in real time, teams avoid maintaining masking views or generating separate masked datasets.
The masking configuration below shows how administrators define and automate masking rules for Vertica columns. Once configured, these rules execute continuously for all queries, guaranteeing that unauthorized users always receive masked or pseudonymized values.
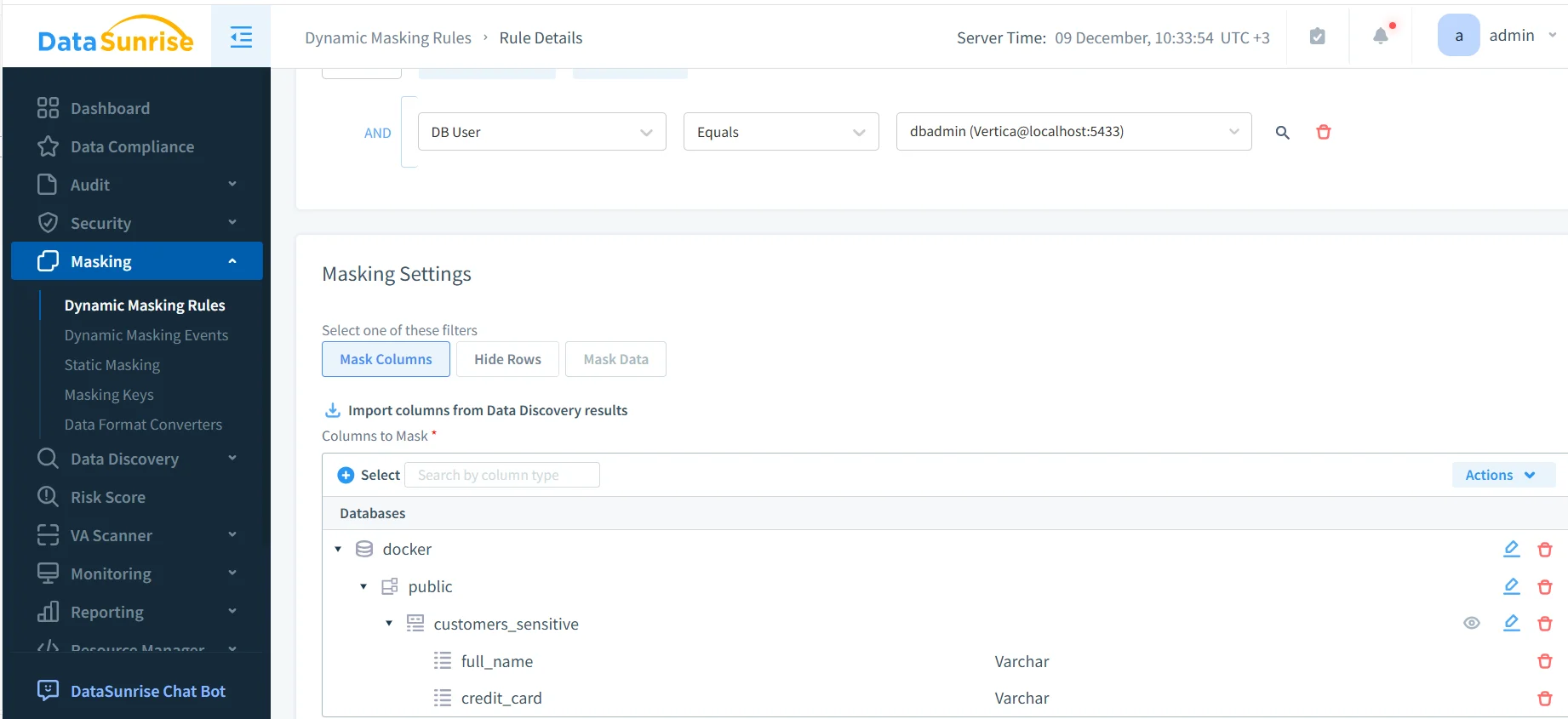
Organizations managing multiple regulated datasets can additionally use the DataSunrise Dynamic Masking module to maintain consistent masking policies across all environments, ensuring Vertica always adheres to enterprise-wide privacy rules.
Regulatory frameworks reinforce the need for this automation. For example, the GDPR pseudonymization rules mandate strict oversight over personal identifiers, while PCI DSS requires masking of PAN fields. With DataSunrise applying masking automatically, protection remains consistent even when schemas evolve or workloads change.
Conditional masking further extends automation by adapting policy behavior to user roles and application contexts. Analysts may see partially redacted data, contractors may receive fully anonymized views, and administrators can view original records only when authorized. This flexibility ensures compliance regardless of workload complexity.
Automating Vertica Audit Capture and Compliance Evidence
Knowing how to automate data compliance for Vertica also requires robust audit automation. Manual log extraction slows investigations, and fragmented node-level logs often fail to present a complete picture. Since Vertica stores audit data across multiple system tables—such as query_requests, query_profiles, and dc_requests—correlating this information by hand becomes impractical.
DataSunrise eliminates this challenge by collecting SQL activity, access attempts, masking events, DDL operations, and rule-trigger outcomes into a centralized audit stream. The screenshot below illustrates this consolidated audit trail.
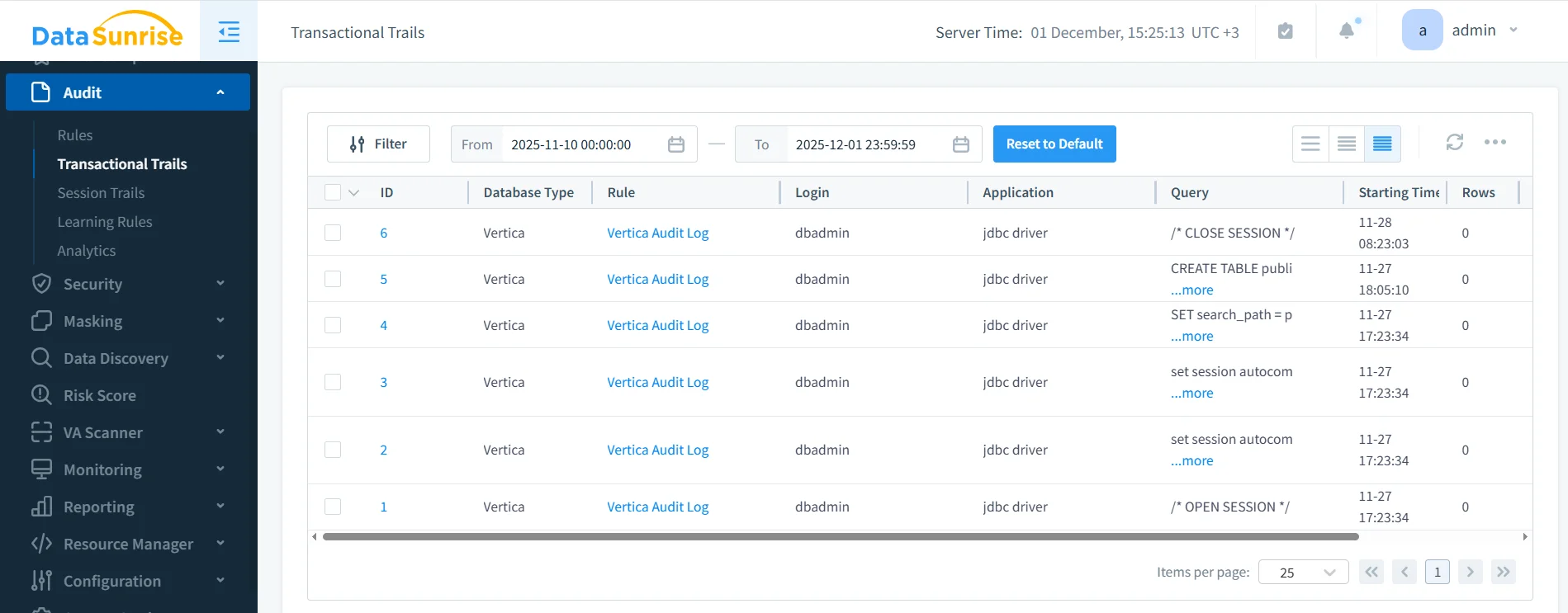
Each audit entry includes full SQL text, user identity, timestamps, session transitions, application metadata, and rule-trigger details. With this information consolidated, compliance teams can quickly analyze behavior and identify anomalies. Additionally, the unified model satisfies logging requirements defined in GDPR Article 30, HIPAA Audit Controls, and NIST 800-53 AU-series controls.
Organizations may extend automation by forwarding logs to SIEM solutions, enabling SOC alerting, and enforcing long-term retention automatically. These integrations strengthen compliance posture without adding engineering overhead.
Benefits of Automating Data Compliance for Vertica
Automation mitigates human error, accelerates compliance operations, and enforces consistent policy behavior across the entire data ecosystem. Manual processes deteriorate quickly as query volume increases, while automated systems remain reliable under any scale.
| Compliance Task | Manual Process | Automated Process |
|---|---|---|
| Masking | Custom SQL, views, ETL rewrites | On-the-fly masking with zero code changes |
| Auditing | Parsing scattered logs manually | Unified, normalized audit stream |
| Policy Enforcement | DBA intervention after violations | Immediate rule-based blocking |
| Evidence Reporting | Manual compilation during audits | Automated compliance reporting |
Conclusion
Understanding how to automate data compliance for Vertica transforms compliance operations from reactive to continuous. Automated masking protects sensitive fields across every workload. Automated auditing delivers complete traceability and regulatory evidence. Automated policy enforcement ensures unauthorized or risky queries never reach Vertica. When combined, these automation layers create a resilient, scalable, and verifiable compliance framework suitable for modern high-volume analytics.
By pairing Vertica’s analytical performance with DataSunrise’s automation platform, enterprises reduce risk, offload operational complexity, and maintain strong regulatory alignment without slowing innovation.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now