How to Mask Sensitive Data in Percona Server
Sensitive data exposure is rarely caused by external attackers alone. In real-world environments, data leaks often occur through internal access, shared environments, analytics workloads, and non-production copies of databases. For teams running Percona Server for MySQL, the challenge is not only securing the database engine but controlling what data users actually see. This is especially relevant in environments that rely on MySQL-compatible platforms such as Percona Server for MySQL for transactional and analytical workloads.
Data masking addresses this problem directly. Instead of restricting access entirely, masking allows organizations to expose database structures and query results while preventing disclosure of sensitive values such as emails, phone numbers, identifiers, or financial data. This approach fits naturally into broader data security strategies, where visibility and protection must coexist, and complements established database security controls.
This article explains how sensitive data masking can be implemented in Percona Server for MySQL using native SQL techniques, and how centralized platforms such as DataSunrise extend these capabilities with policy-driven, auditable, and scalable masking controls.
What Is Sensitive Data
Sensitive data is information that can cause harm if exposed or misused. In Percona Server for MySQL, it often lives inside regular tables and columns, which makes accidental exposure easy.
Typical examples include personally identifiable information (PII) such as names, email addresses, and phone numbers, as defined in PII data classification, along with financial records, authentication data, and business-critical identifiers.
The main risk comes from overexposure. Sensitive data is frequently accessed by developers, analysts, support teams, and automated processes at the same time. Even when access is legitimate, visibility is often broader than necessary, which creates gaps in database security.
From a protection standpoint, sensitive data is defined not only by its content, but also by context: who accesses it, from where, and for what purpose. Because schemas rarely isolate sensitive fields cleanly, organizations rely on access-layer controls aligned with modern data security practices, including data masking.
Native Data Masking Options in Percona Server for MySQL
Percona Server for MySQL is fully compatible with MySQL and inherits its core behavior. As a result, data masking is implemented at the SQL and schema level. These techniques are typically used in controlled environments where masking requirements are known in advance and enforced through database design.
Masking with Views
Views are commonly used to expose masked representations of sensitive columns while keeping original values stored securely in base tables.
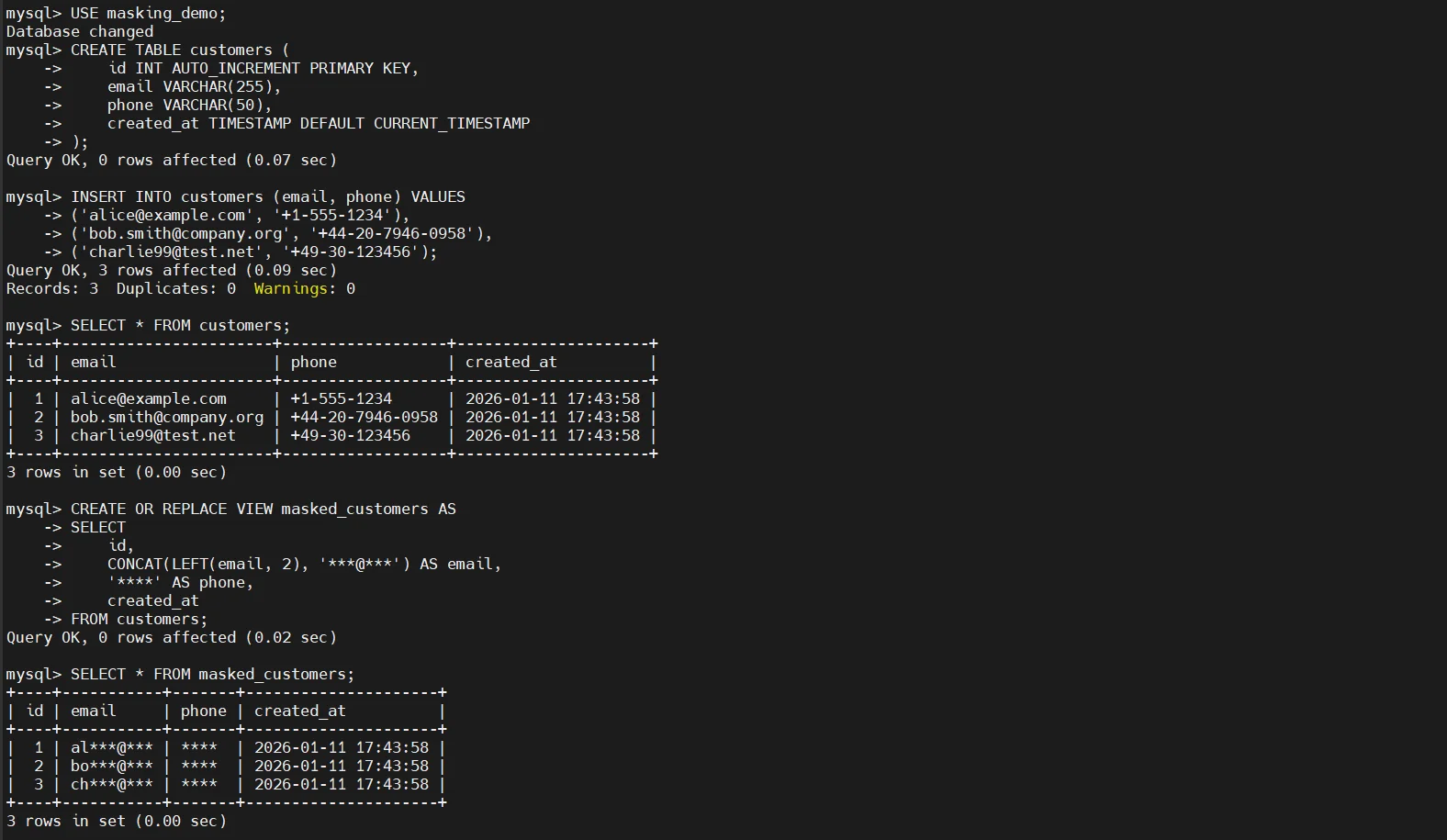
This approach allows applications and analysts to query realistic datasets while preventing direct exposure of sensitive fields.
Masking via SQL Functions
Percona Server supports standard MySQL string and numeric functions that can be used to mask values dynamically within queries.
CREATE TABLE payments (
id INT PRIMARY KEY AUTO_INCREMENT,
user_id INT,
card_number VARCHAR(20),
amount DECIMAL(10,2),
created_at TIMESTAMP DEFAULT CURRENT_TIMESTAMP
);
SELECT
id,
user_id,
CONCAT(
SUBSTRING(card_number, 1, 4),
' **** **** ',
SUBSTRING(card_number, -4)
) AS masked_card_number,
amount,
created_at
FROM payments
WHERE created_at >= DATE_SUB(NOW(), INTERVAL 30 DAY);
This method is commonly used in reports or dashboards where partial visibility of sensitive values is sufficient and full disclosure is not required.
Static Masking Through Data Copy
In non-production environments, static masking is often applied during database cloning, export, or refresh operations.
CREATE TABLE users (
id INT PRIMARY KEY AUTO_INCREMENT,
username VARCHAR(255),
email VARCHAR(255),
registered_at TIMESTAMP DEFAULT CURRENT_TIMESTAMP
);
UPDATE users
SET
email = CONCAT('user', id, '@example.com'),
username = CONCAT('user_', id);
This approach permanently replaces sensitive values with synthetic ones, making the dataset safe for development, testing, or training purposes while preserving table structure and data relationships.
Centralized Data Masking for Percona Server for MySQL with DataSunrise
DataSunrise introduces an external security layer that enforces data masking transparently, without modifying database schemas or application code. Masking rules are applied as queries are processed, which allows the same data to be presented differently depending on access context. This means sensitive values can be protected dynamically without changing how applications interact with the database.
This approach aligns data masking with broader data security and database security strategies while preserving performance and operational simplicity. Because masking is enforced outside the database engine, it remains consistent across environments and does not depend on application-side logic or query discipline.
Dynamic Data Masking
Dynamic data masking is applied in real time, at the moment a query is executed. Sensitive values are transformed on the fly, while the original data remains unchanged in the database. As a result, the same column can be masked or unmasked depending on who is accessing it and under what conditions, without requiring any changes to SQL queries or application logic. This mechanism is commonly referred to as dynamic data masking.
Masking decisions can take into account contextual attributes such as the database user or role, the client IP address, the application source, as well as time-based or session-specific parameters. This enables practical scenarios where applications continue to work with real data, while analysts, support engineers, or external users see masked values appropriate to their access level.
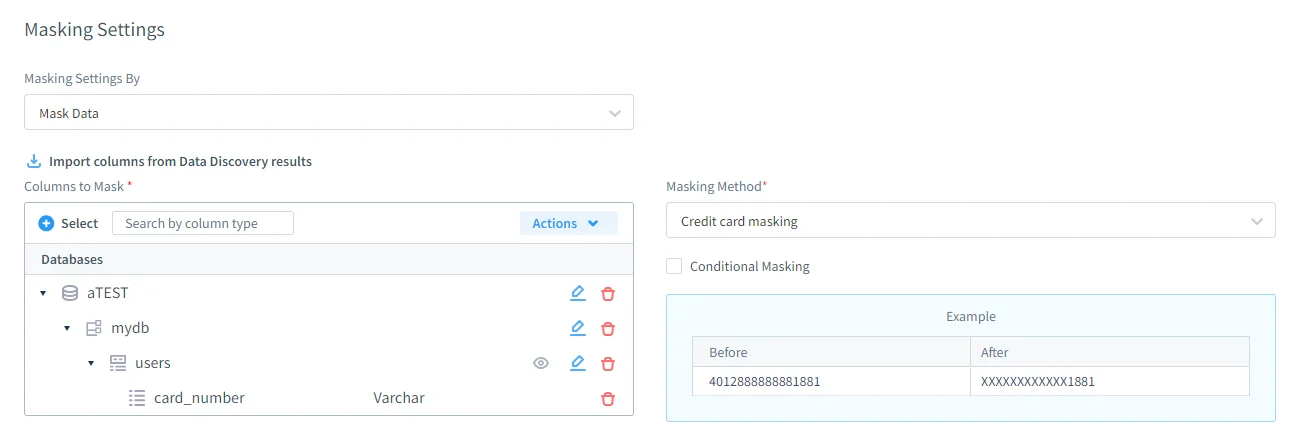
Policy-Based Masking by Data Type
Rather than defining masking rules for individual columns, DataSunrise allows policies to be created at the data category level. Once sensitive data is discovered and classified using data discovery mechanisms, masking rules are automatically applied to all matching fields across databases and schemas.
As schemas evolve, newly created tables and columns that contain sensitive data are protected automatically. Masking follows the data itself instead of being tied to static schema definitions. Common transformations include partial masking of email addresses and phone numbers, tokenization of identifiers, and format-preserving masking for financial values, ensuring usability while reducing exposure of PII.
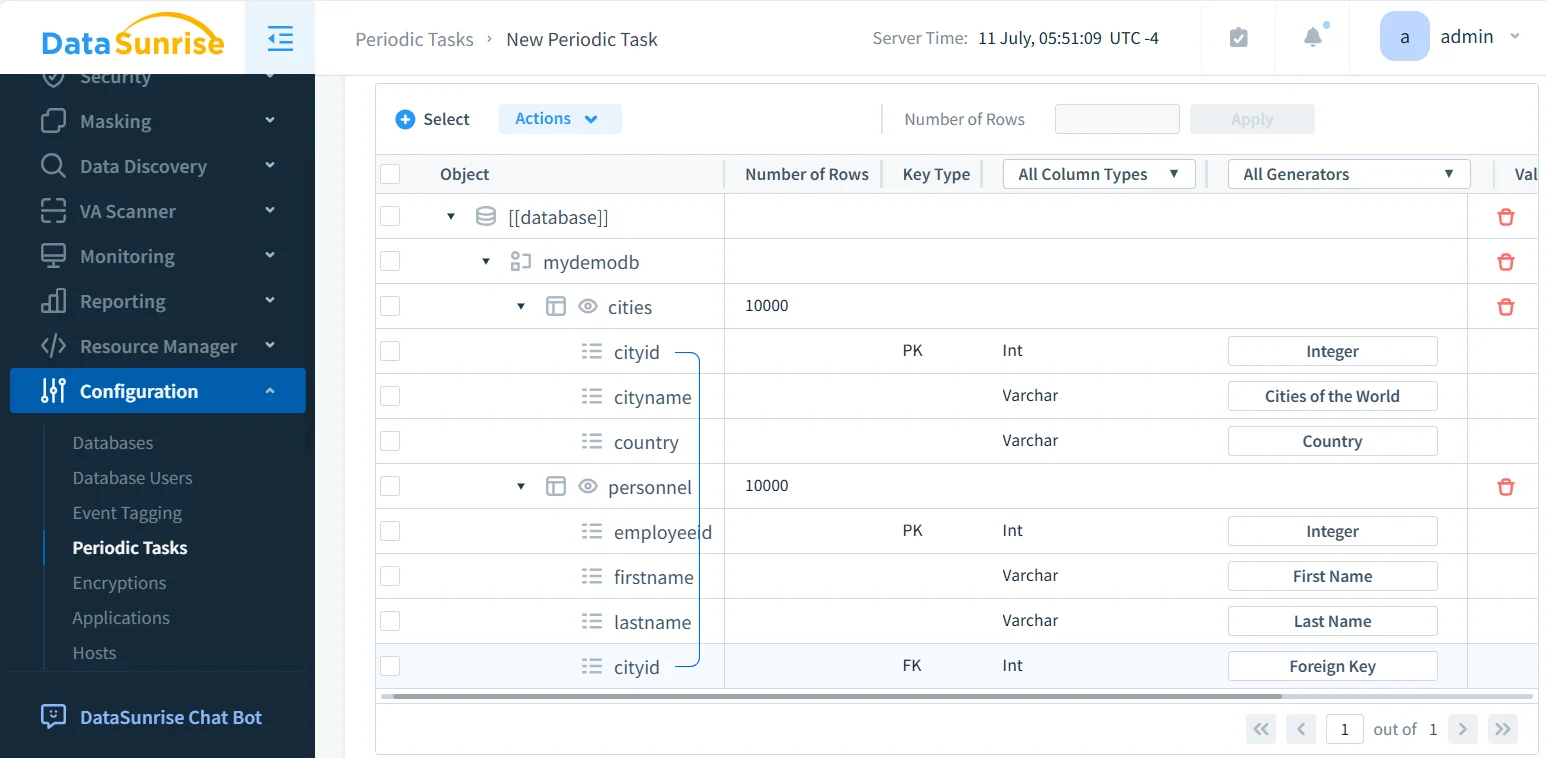
Static and In-Place Masking Workflows
For environments where sensitive data must be permanently transformed, DataSunrise supports controlled static and in-place masking workflows. These workflows are typically used when production data is copied outside tightly controlled environments and align with test data management practices.
Masking can be applied during database cloning, backup restoration, data export, or test data provisioning processes. By enforcing masking before data leaves protected systems, organizations ensure that non-production environments only receive sanitized datasets while preserving structure and referential integrity.
Auditable Masking Operations
All masking activities performed through DataSunrise are logged and fully traceable as part of a unified audit trail. Audit records capture which data was masked, which rules were applied, when masking occurred, and who initiated the operation.
This visibility integrates masking directly into audit and compliance workflows, making it a governed security control rather than a one-time data transformation. As a result, organizations can demonstrate consistent enforcement of data protection policies during internal reviews, security investigations, and regulatory audits.
Native vs Centralized Data Masking in Percona Server for MySQL
| Aspect | Native SQL-Based Masking | Centralized Masking with DataSunrise |
|---|---|---|
| Enforcement model | Implemented through views, queries, or scripts | Enforced externally at query execution |
| Schema impact | Requires schema objects or query changes | No schema or application changes |
| Masking consistency | Depends on manual enforcement | Guaranteed by centralized policies |
| Context awareness | Same masking for all users | Adapts to user, role, IP, or application |
| Schema evolution | Manual updates required | New objects protected automatically |
| Audit visibility | Limited or fragmented | Full audit trail for masking operations |
Centralized masking consolidates sensitive data protection into a governed control layer, reducing operational effort while maintaining consistent and auditable enforcement across Percona Server environments.
Conclusion
Percona Server for MySQL provides the flexibility to implement data masking using native SQL techniques. These approaches can be effective in controlled scenarios, particularly when access patterns are stable and masking logic can be enforced manually at the schema or query level.
At the same time, modern database environments introduce requirements that go beyond basic SQL-based masking:
- multiple user roles accessing the same data simultaneously
- shared production-like datasets used across development, analytics, and support
- growing compliance expectations that require traceability and consistency
In these conditions, centralized platforms such as DataSunrise become a practical extension of Percona Server for MySQL:
- masking is enforced externally and consistently, without modifying schemas or application code
- data visibility adapts to user context, access source, and environment
- masking operations are logged and auditable by design
As a result, sensitive data protection is no longer implemented as a collection of fragile scripts or views. Masking becomes an integral, governed component of secure database operations, supporting both usability and long-term compliance.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now