
LLM and Ml Tools for Database Security
Introduction
With cyberattacks growing more advanced and data exposure incidents becoming increasingly common, organizations are turning to intelligent analytics to strengthen database protection. Today’s large language models (LLMs) and machine learning (ML) engines—augmented by natural language processing (NLP) and optical character recognition (OCR)—serve as the backbone of modern AI-powered auditing and monitoring platforms. These technologies provide automated anomaly detection, continuous analysis of user and application behavior, and precise discovery of sensitive information across both structured systems and unstructured sources such as emails, PDF files, chat logs, scanned documents, and even screenshots. Industry analyses, including the MITRE ATT&CK framework, highlight how AI enhances detection of complex attack techniques across large data environments.
By understanding context rather than just patterns, AI-driven tools can distinguish between normal operational activities and subtle indicators of misuse or compromise. This allows security teams to move from reactive investigation to proactive prevention—enhancing accuracy, reducing false positives, and significantly improving response times. As organizations expand across cloud, hybrid, and distributed architectures, these capabilities become essential for maintaining visibility, compliance, and trust.
Customer Support Automation Using LLMs
One of the key applications of LLM and ML technologies in database security is improving customer support. LLMs drive chatbots capable of understanding natural language, while ML models optimize responses and help prioritize requests. Working together, they create virtual assistants that provide real-time guidance for troubleshooting, configuration, and compliance verification.
For instance, DataSunrise includes an LLM-powered virtual assistant built into the UI and website. When users encounter issues, they can describe problems in plain English and receive accurate responses—instantly.
This not only improves resolution time, but also reduces pressure on human support teams. In fact, according to an IBM case study, LLM-based support resolved over 80% of user queries without escalation.
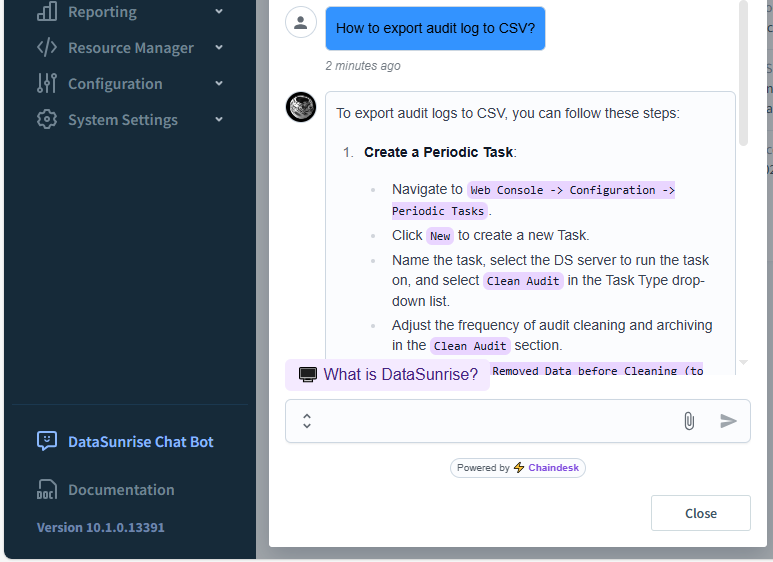
To prevent misleading answers, the assistant uses a zero-temperature setting and restricts access to a controlled internal knowledge base.
User Behavior Monitoring with ML
Another critical application of LLM and ML tools is user behavior monitoring. ML models establish baselines of normal activity, while LLM-driven context analysis interprets unusual behavior and flags potential threats. This hybrid approach detects deviations—like abnormal queries or unauthorized access—more effectively than static rule-based systems.
- Multiple failed login attempts
- Access to restricted or sensitive tables
- Unusual query volume or export frequency
- Logins from new devices or locations
When such anomalies occur, DataSunrise can flag the session, alert administrators, or block access temporarily—depending on the policy configuration.
As a result, even small teams can maintain a high level of monitoring without investing heavily in manual investigation.
Data Discovery Enhanced by NLP
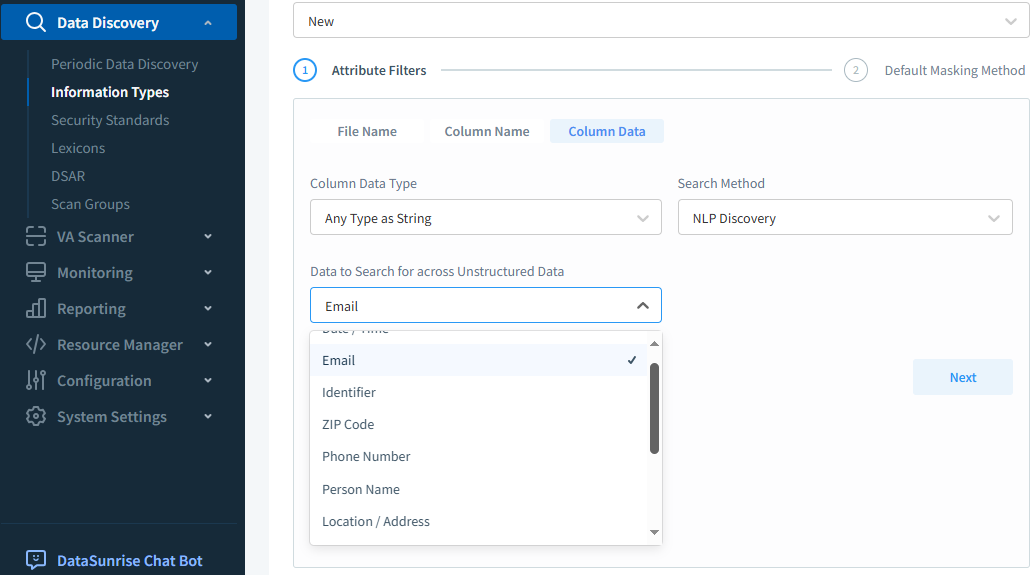
Often, sensitive data isn’t clearly labeled or structured. That’s where NLP helps. Natural language processing scans comments, logs, and text fields to identify personal, medical, or financial information—accurately and at scale.
Unlike basic keyword matching, NLP models use context to identify data types, even if field names are ambiguous. This dramatically improves precision and reduces false positives during discovery.
import spacy
nlp = spacy.load("en_core_web_sm")
text = "Patient John Doe, DOB 05/12/1987, was diagnosed with hypertension. SSN: 123-45-6789."
doc = nlp(text)
for ent in doc.ents:
print(f"{ent.text} - {ent.label_}")
This will produce results like John Doe - PERSON and 05/12/1987 - DATE. Within DataSunrise, this method detects over a dozen types of sensitive fields—even in semi-structured APIs or text-based systems.
OCR Integration for Legacy Documents
Many organizations still store contracts and scanned forms in image formats. OCR (Optical Character Recognition) allows these to be indexed, analyzed, and secured using the same AI tools as modern databases.
After extraction, NLP models process the text to tag SSNs, medical records, or addresses. Because of this layered approach, even archived PDFs or scanned images can be protected and monitored effectively.
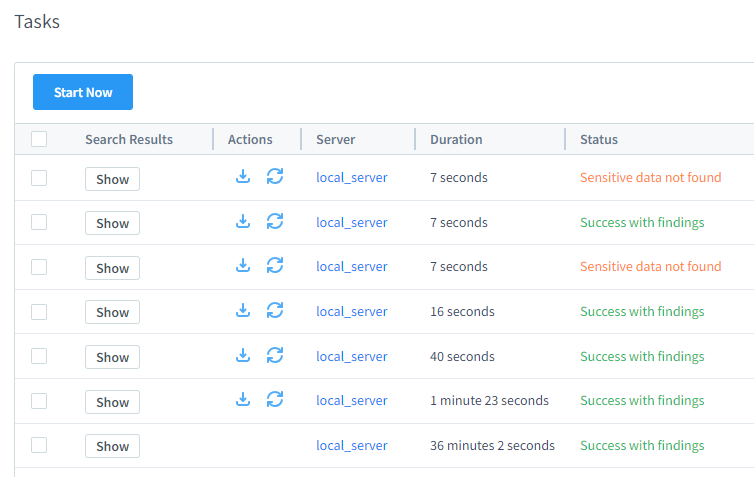
Performance and Accuracy in Real-World Environments
AI-assisted discovery and masking systems often walk a tightrope between speed and precision. That’s why DataSunrise gives you control: OCR and NLP pipelines can be tuned for accuracy or performance depending on the workload.
For instance, low-latency document classification in cloud environments may favor batch processing. Meanwhile, high-security deployments can enable deep analysis for every inbound PDF or API log. The platform adjusts to your infrastructure, not the other way around.
How We Evaluate LLM and ML Tools in Security
| Metric | What It Tells You | Target Trend |
|---|---|---|
| Precision / Recall | Quality of detections vs. misses on real incidents | Increase both; tune per use case |
| False Positive Rate | Noise that burns analyst time | Decrease (especially on noisy datasets) |
| Mean Time to Detect (MTTD) | Speed from signal to alert | Decrease |
| Mean Time to Respond (MTTR) | Speed from alert to action taken | Decrease |
| Cost per Correct Alert | Compute + review cost per validated finding | Decrease over time |
Track outcomes, not just model accuracy—tie alerts to real response and reduction in risk.
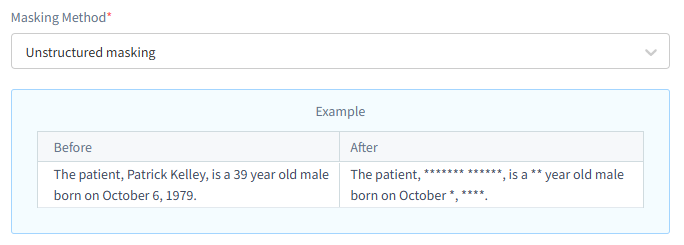
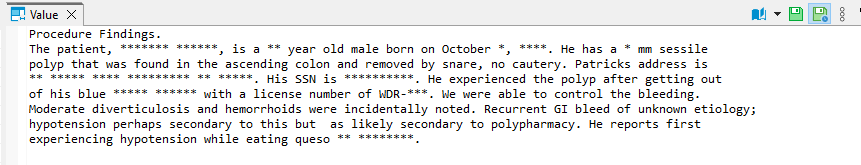
Masking Unstructured Data with NLP
Unstructured data poses a unique challenge. However, DataSunrise uses NLP to detect and mask sensitive values even in documents like Word files, CSV exports, or flat text logs.
Because the masking engine works at the proxy layer, there’s no need to modify source files or change application code. Instead, the redacted version is generated on demand—based on role, content type, or access context.
Common Use Cases Across Roles
DataSunrise’s AI-powered security workflows support different teams—each with its own needs, responsibilities, and access boundaries:
- Security Analysts: Identify unusual patterns, correlate events, and respond to live behavioral threats using ML-driven detection. Automated triage and session replay help analysts understand root causes faster and reduce alert fatigue.
- Compliance Officers: Streamline discovery, classification, and masking audits across databases governed by GDPR, HIPAA, PCI DSS, and other regulations. With NLP and OCR, they can validate sensitive data exposure even in unstructured or semi-structured sources.
- Developers & DBAs: Build and optimize applications using realistic, masked production datasets. This enables accurate testing and debugging while maintaining strict isolation of sensitive information, preventing accidental leakage in dev and staging environments.
- Support Engineers: Leverage LLM-driven assistants to diagnose permission issues, analyze failed queries, and trace access paths—without viewing raw confidential data. Masking and policy controls ensure troubleshooting remains secure by default.
This cross-role design ensures every stakeholder gains meaningful insights and operational benefits—while maintaining strict visibility boundaries, consistent policy enforcement, and high performance across all environments.
How It All Comes Together
DataSunrise orchestrates AI-powered workflows across the entire database security lifecycle. From accelerating support responses to detecting suspicious user behavior and identifying sensitive content, the platform applies automation at every stage—from data intake to enforcement. These technologies work together to streamline compliance, reduce manual effort, and ensure protection across both modern and legacy systems.
| Technology | Function | Data Type |
|---|---|---|
| LLM | Contextual chatbot assistance, support automation | User queries, documentation, logs |
| ML | Behavioral anomaly detection, session scoring | Access patterns, login events |
| NLP | Entity recognition, masking rule application | Text fields, logs, exports |
| OCR | Text extraction for legacy file scanning | PDFs, scanned forms, image files |
Top Benefits of Using LLM and ML Tools in Database Security
Integrating AI technologies like LLMs, ML, NLP, and OCR into database security isn’t just about automation—it’s about delivering smarter, more adaptive defenses that scale with your organization.
- Faster incident response: Anomaly detection and real-time alerts allow teams to react within seconds—not hours—when sensitive data is at risk.
- Continuous compliance assurance: Automated discovery and masking keep pace with changing regulations and environments without manual audits.
- Unified visibility across data types: From relational databases to scanned documents, NLP and OCR ensure no sensitive asset is left unmonitored.
- Reduced reliance on manual workflows: AI tools handle classification, pattern recognition, and user behavior baselining at scale.
- Personalized security policies: LLMs and ML models adapt masking and access rules based on user context, role, and real-time risk scores.
- Streamlined support and onboarding: Conversational agents powered by LLMs reduce ticket volume and accelerate access configuration across departments.
These benefits highlight why leading security platforms are no longer just adopting AI—they’re built around it. DataSunrise unifies these technologies into a single architecture, helping organizations move from reactive patching to proactive protection.
Integrating AI-Powered Security into Existing Workflows
One of the most significant challenges in modern cybersecurity is deploying new technologies without disrupting established business and security operations. DataSunrise addresses this challenge through an AI-powered architecture designed to integrate smoothly into your existing workflows, rather than replace them. Its intelligent suite—featuring LLM-based virtual assistants, machine learning–driven anomaly detection, natural language processing (NLP) for data classification, and OCR-based document scanning—works in tandem with existing monitoring, ticketing, and compliance ecosystems to enhance visibility and automation.
For example, behavioral alerts and anomaly reports generated by DataSunrise can be automatically forwarded to your SIEM or SOAR platform for correlation and response, while NLP-powered discovery modules can enrich your current data catalog with real-time sensitivity tags and ownership metadata. OCR scanning further extends this capability to unstructured data and image-based documents, ensuring that no sensitive element remains hidden or unmonitored.
This seamless integration approach minimizes friction for IT and security teams—allowing new AI-driven insights to amplify, not disrupt, the tools and workflows already in place. By embedding intelligence directly into your existing environment, DataSunrise accelerates deployment, reduces operational overhead, and ensures faster return on investment. The result is a harmonized ecosystem where automation, contextual analysis, and compliance validation work together—empowering organizations to evolve their defenses continuously while maintaining stability, efficiency, and regulatory readiness.
Summary and Conclusion
In the modern cybersecurity landscape, effective data protection requires more than traditional firewalls or static configuration policies. DataSunrise delivers an advanced, intelligent solution that integrates natural language processing, behavioral analytics, and user-focused conversational interfaces to enable proactive threat detection, detailed activity tracking, and automated policy management—all without compromising database stability or performance. This comprehensive approach provides organizations with full visibility and control across on-premises, cloud, and hybrid environments.
By continuously learning and adapting through machine learning, DataSunrise enhances its detection algorithms based on evolving user behavior and query trends, enabling quicker anomaly recognition and faster incident response. It not only reinforces defenses against insider risks and complex external attacks but also ensures seamless integration of compliance, auditing, and data masking processes. In essence, DataSunrise delivers an adaptive and forward-looking security framework that empowers enterprises to maintain resilience, compliance, and operational flexibility in today’s rapidly evolving digital world.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now