
MySQL Audit Log

Security teams used to treat the MySQL Audit Log as a slow, bulky after‑thought — something you gzip once a week in case an auditor asks for evidence next quarter. In 2025 the audit trail is the beating heart of the database security pipeline: streamed in real time, masked on the fly, enriched by GenAI, and checked automatically against every relevant compliance clause. This article shows how to raise the humble log to that modern standard, with recipes for native MySQL, a walk‑through for DataSunrise,.
Why the audit log still matters
Every compromise leaves traces in three places: the network, the operating system, and the database. Only the database log captures intent — the actual statement DELETE FROM customers, not just a suspicious port scan. Regulators such as PCI DSS 4.0 and GDPR’s Article 30 now expect those events to be retained, tamper‑evident, and regularly reviewed. That requirement is onerous unless you automate everything downstream of collection.
Streaming first, tailing last
Disk‑based polling makes alerts arrive minutes or hours late. Switch the plugin into asynchronous streaming and write directly to Apache Kafka or Amazon Kinesis:
INSTALL PLUGIN audit_log SONAME 'audit_log.so';
SET GLOBAL audit_log_strategy = 'ASYNCHRONOUS';
SET GLOBAL audit_log_handler = 'FILE';
SET GLOBAL audit_log_file = 'stream://kafka:9092/mysql_audit';
From that moment every login, DDL, and DML statement is available to your SIEM within a second. If your SOC already consumes the Kafka topic used by the network team, you can correlate “odd port 3306 spike” with “failed root login” without writing glue code. Additional audit logging best practices recommend streaming early to avoid bottlenecks.
Dynamic masking & automatic data discovery
Security is not only about who accessed the database but what they saw. Pipe the same real‑time feed through DataSunrise’s dynamic data masking engine. The proxy replaces credit‑card numbers with format‑preserving tokens whenever a session lacks the “PCI-Access” role. Column‑level sensitivity labels come from nightly crawls powered by DataSunrise data discovery; if a developer deploys a table called insurance_claims at 02:00, it is tagged as “PHI” by 03:05 and masked on the next query.
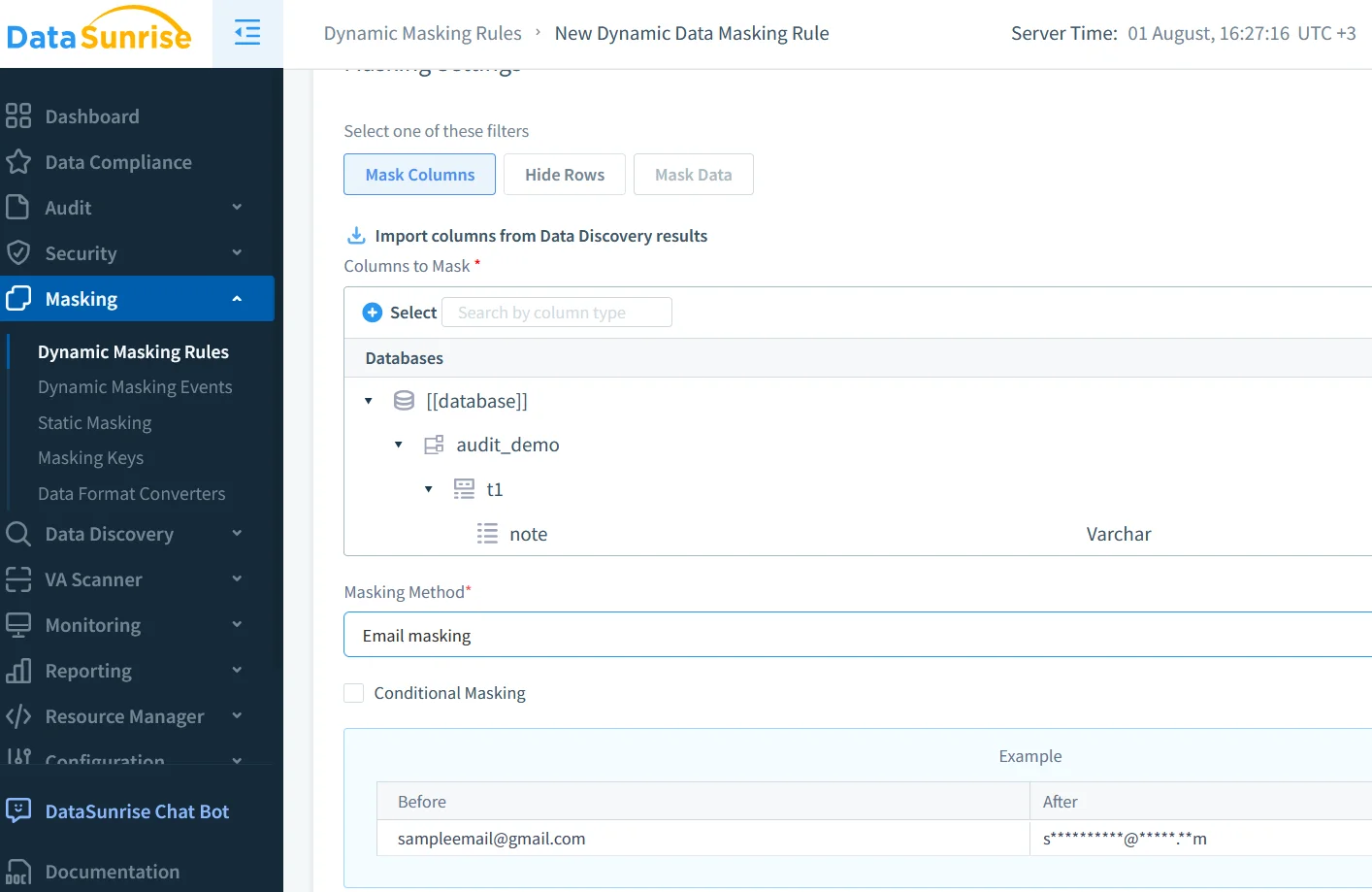
Masked values include checksum watermarks, so your BI dashboard sees “4111‑XXXX‑1111‑1111” – valid Luhn check, bogus number – and your analysts keep working. The masking decision itself is logged and streamed, maintaining full context for forensics and compliance.
GenAI turns noise into narrative
Large language models excel at summarising repetitive JSON. A forty‑line Python worker can turn ten thousand raw events into a Slack‑friendly paragraph:
from openai import OpenAI
client = OpenAI()
prompt = f"You are an infosec assistant. Summarise anomalies:\n{events_json}"
summary = client.chat.completions.create(
model="gpt-4o-mini",
messages=[{"role": "user", "content": prompt}]
).choices[0].message.content
Teams paste that summary straight into Jira, slashing mean‑time‑to‑triage from hours to minutes. Because the LLM sits after masking, no production PII ever reaches the GenAI model.
Native MySQL audit in depth
The official MySQL Audit Log plugin documentation describes the architecture and options in detail. Use filters (see the audit-log filter rules reference) to record everything except SELECT statements executed by reporting:
CALL audit_log_filter_set_filter(
'reporting_app',
'IF user = "reporting" THEN RETURN FALSE; ELSE RETURN TRUE; END IF'
);
CALL audit_log_user_set_filter('reporting','reporting_app');
SET GLOBAL audit_log_format = 'JSON';
SET GLOBAL audit_log_policy = 'ALL';Check the result with:
SELECT *
FROM mysql.audit_log
ORDER BY event_time DESC
LIMIT 5;
Because the configuration lives in SQL you can place it under version control, apply it through CI/CD pipelines, and roll back if needed.
Hardening the log itself
Attackers love to “pave over” their tracks by deleting rows from the log table. Defend the trail by shipping events to an object‑locked S3 bucket in WORM (Write‑Once‑Read‑Many) mode, or by snapshotting the file system every five minutes with immutable flags.
Why add DataSunrise?
A malicious user with the SUPER privilege can unload the plugin; a transparent proxy cannot be disabled from inside the database. Adding DataSunrise gives you a second, independently stored audit trail plus rich runtime controls.
If a query violates policy, DataSunrise pushes an alert through its Slack integration within seconds, complete with before‑and‑after values.
Compliance autopilot
DataSunrise’s GDPR control library and PCI DSS templates map specific audit events to regulatory clauses, while the broader Compliance Manager dashboard attaches ready‑made evidence to each control. Auditors walk away happy and you avoid the death‑spiral of last‑minute evidence gathering.
Example threat hunt: PII access outside office hours
SELECT *
FROM mysql.audit_log
WHERE JSON_EXTRACT(audit_record,'$.user') NOT IN ('svc_backup','replication')
AND HOUR(event_time) NOT BETWEEN 7 AND 19
AND JSON_EXTRACT(audit_record,'$.command_class') = 'select'
AND JSON_EXTRACT(audit_record,'$.object.name') IN ('patients','credit_cards');
Schedule the query as a nightly job or feed the Kafka stream into a Grafana Loki rule that triggers whenever the count exceeds a threshold.
Architecture snapshot
- MySQL emits the MySQL Audit Log through the built‑in plugin.
- Events stream to Kafka; a second path writes immutable objects to S3.
- DataSunrise proxy enforces masking and publishes enrichment events tagged with sensitivity labels.
- A GenAI micro‑service summarises anomalies and opens Jira issues when risk ≥ 0.8.
Disable any single layer and investigators still have breadcrumbs in another.
Final thoughts
Yesterday the audit log was a static artefact. Today it is a live security signal enriched by GenAI and cross‑checked against dozens of compliance frameworks. Start by streaming the MySQL Audit Log, add masking and automation where required, and let the machines do the boring part — your analysts will thank you.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now