
Snowflake Security: Enhancements and Measures
Understanding Snowflake
To comprehend the topic of Snowflake security, it’s essential to first delve into what Snowflake is. Imagine you have a website hosted on a dedicated server with specific CPU, memory, and storage capacities. As more people visit your website, you need more computing power to keep up.
Traditionally, this would require stopping the server, upgrading hardware components such as CPU and memory, and expanding storage capacity. Upgrading servers is hard work and takes a long time, which can be a problem for system admins. This is especially true for medium-sized businesses relying on database servers where mistakes can cost a lot.
Transition to Virtual Infrastructure
Cloud services like AWS or Azure have made managing IT much easier. We no longer need to be concerned about physical hardware. With cloud services, users don’t have to deal with the details of setting up and maintaining hardware. Cloud services offer virtual machines with different performance levels to meet user needs.
Software technology has also improved to work well with cloud architecture. Now, we can easily add more computing resources using web interfaces without interrupting services. This eliminates the need for manual setup of virtual machines.
Introduction of Snowflake
Cloud infrastructure charges by the hour, allowing developers to adjust computing resources based on demand. This can lead to significant cost savings.
The need for better integration between cloud tools and data processing solutions has increased as cloud computing has improved. The Snowflake data platform meets these needs.
It provides a scalable and efficient platform for data processing and analytics. It seamlessly integrates with various data sources and tools. This article aims to discuss methods for further improvement and achieving more precise control over data with DataSunrise.
Built-in Snowflake Security Features
Snowflake provides a range of security features designed to protect data both at rest and in transit. These include always-on encryption, role-based access control, and support for multi-factor authentication.
The features of Snowflake enhance security, however, they might not fulfill the requirements of every institution. These features form a strong foundation for security, but they may not cover all security and compliance requirements. Each organization may have different security and compliance needs that these features may not fully address.
Pivotal Security Commands and Features
A few key aspects to understand about Snowflake security. Snowflake has a security system similar to traditional databases like Oracle or MySQL. In Snowflake, you can create users, roles, and grant privileges similar to other databases.
Below are some essential commands and features to be aware of:
Role Management, User Management, Access Control:
CREATE ROLE: Create roles based on the principle of least privilege.
GRANT ROLE: Allocate roles to users or other designated entities.
REVOKE ROLE: Remove roles from users or other roles.
CREATE USER: Create users with appropriate permissions.
ALTER USER: Modify user attributes or permissions.
DROP USER: Eliminate user profiles when access is no longer required.
GRANT: Bestow privileges on databases, schemas, tables, views, and other entities.
REVOKE: Remove privileges from users or roles.
DENY: Explicitly deny access to certain resources.
Snowflake protects data through encryption whether it’s at rest or in transit. Snowflake automatically decrypts data within a table, processes it, and then re-encrypts it after completing the necessary operations.
Audit Logging (see the description below in this article):
CREATE OR REPLACE AUDIT POLICY: Define audit policies to capture relevant activities.
ENABLE DATABASE AUDIT: Enable auditing for specific databases.
DISABLE DATABASE AUDIT: This command deactivates auditing as needed.
GET_AUDIT_LOG_FILES: Retrieve audit logs for compliance.
CREATE NETWORK POLICY: Define network policies to control access from specific IP addresses or ranges. ALTER NETWORK POLICY: Modify existing network policies. DROP NETWORK POLICY: Remove network policies when they are no longer needed.
Data Masking (Data Governance) and Data Tags:
CREATE MASKING POLICY: Define policies to mask sensitive data. ALTER MASKING POLICY: Modify existing masking policies. DROP MASKING POLICY: Remove masking policies when they are no longer needed.
Multi-Factor Authentication (MFA):
Enable MFA for user authentication, which adds an extra layer of security.
Regular Security Audits and Updates:
Regularly review and update security configurations and access controls.
Monitor system logs for suspicious activities and security breaches.
The Role of DataSunrise in Snowflake Security
DataSunrise takes Snowflake security to the next level by offering additional layers of protection. Not a regular database but a security and compliance automation tool that works seamlessly with Snowflake. DataSunrise’s suite of tools includes activity monitoring, database firewall, dynamic data masking, sensitive data discovery, and more. These tools help to detect and prevent unauthorized access, SQL injection attacks, and potential data breaches.
Activity Monitoring and Threat Detection
One of the key features of DataSunrise is its real-time activity monitoring. This capability allows organizations to keep a vigilant eye on all user actions within the Snowflake database. By detecting access rights abuses and potential data breach preparations, DataSunrise enhances Snowflake security by providing an additional layer of surveillance.
The audit rules in DataSunrise and Snowflake are different. They vary in the extent of monitoring, customization options, and ability to enforce security policies.
DataSunrise and Snowflake have different audit rules. DataSunrise offers more monitoring and customization options compared to Snowflake. Snowflake has less ability to enforce security policies than DataSunrise.
Snowflake Built in Monitoring
The Snowflake built-in Web-UI Monitoring looks as follows:
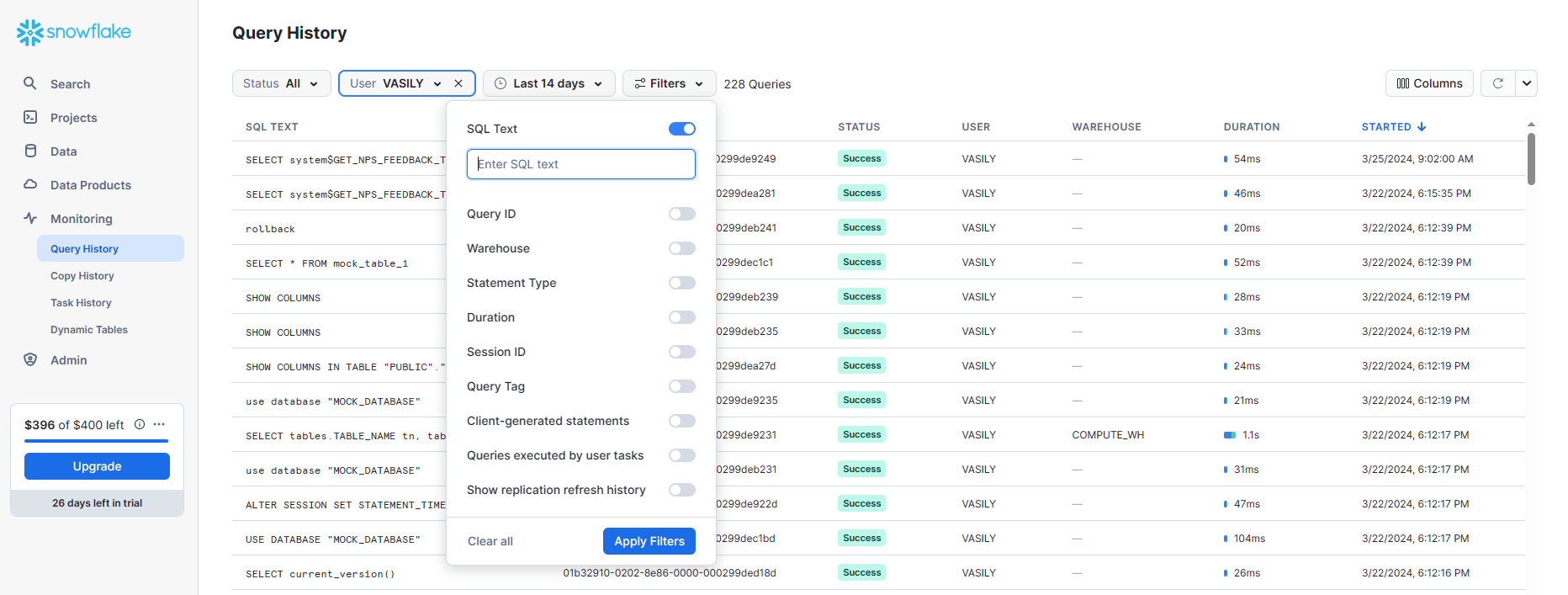
Three options of handling the audit data in Snowflake:
- Query History page
- QUERY_HISTORY View
- QUERY_HISTORY, QUERY_HISTORY_BY_* Table functions
You can find the first method on the Monitoring – Query History page in the Web-UI. You can access the other two methods using SQL syntax. By default, Snowflake does not have an Audit Rules setup.
DataSunrise has a user-friendly interface. This interface allows users to create Audit Rules. Users can also see the results of these rules in Transactional Trails on the Audit Page. The interface is accessible through a web-based UI.
In DataSunrise, you can set up rules for specific Snowflake database object queries. Just go to Audit, Rules, Add Rule, Process Query to Database Objects, and Select. Refer to the image below for details.
The precise rule setup in DataSunrise facilitates analyzing Audit results. Snowflake’s built-in monitoring tools provide all necessary features. However, they may not be as accurate in their configuration. This can result in a large amount of data in the query history table. This occurs when the database program communicates with the database design. This causes the generation of numerous service requests. These requests do not relate to how users actually utilize the program. This happens when the database application interacts with the database schema. This creates many service queries. These queries do not directly relate to usage logic.
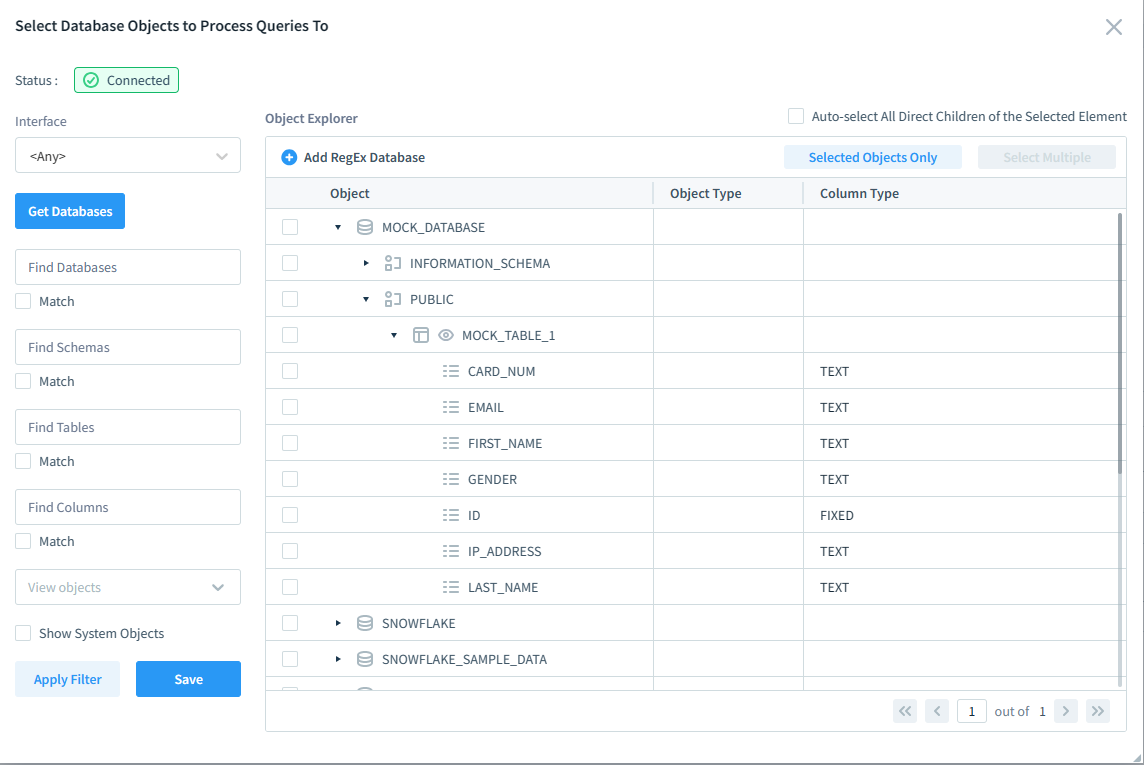
Notice that DataSunrise offers precise setup of the monitored objects, providing better control over the rules.
DataSunrise designed audit rules to offer comprehensive real-time monitoring of all user actions within a database. This includes the capability to detect attempts at abusing access rights and preemptively preventing data breach preparations.
DataSunrise can capture detailed information about database operations. This includes the identities of the users, timing, and attributes of the operations. The auditing capabilities of DataSunrise are extensive. Having detailed information is essential for organizations needing to comply with various national and international data protection regulations.
Also, DataSunrise lets you choose where to save audit logs for later analyzing or investigating. You can store them in either an internal or external database.”
Advanced Database Firewall
DataSunrise’s database firewall is better than Snowflake’s default security measures. It actively detects and stops SQL injections and unauthorized access attempts in real-time. This proactive approach to Snowflake security stops advanced cyber threats before they can cause damage.
The DataSunrise Web Console offers a logical and intuitive graphical user interface (GUI) for managing database security and compliance policies.
Snowflake spreads its security features across the website to keep data safe and analyze it. You can set up security settings on the platform’s interface or by using SQL commands. The Snowflake web interface, often referred to as the Snowflake Console or Snowflake Web UI.
Dynamic Data Masking in DataSunrise
Database administrators can customize DataSunrise’s dynamic data masking to create complex masking rules and policies. Users trigger these rules based on conditions like user roles, access rights, or the content of the data. DataSunrise offers a high level of masking control, allowing for data masking based on its type or internal content. This provides a more personalized approach to data protection.
DataSunrise allows logging masking events into the Dynamic Masking Events log in Figure 03.a. Please note the ‘Log Event in Storage’ checkbox. DataSunrise also has the capability to block queries.
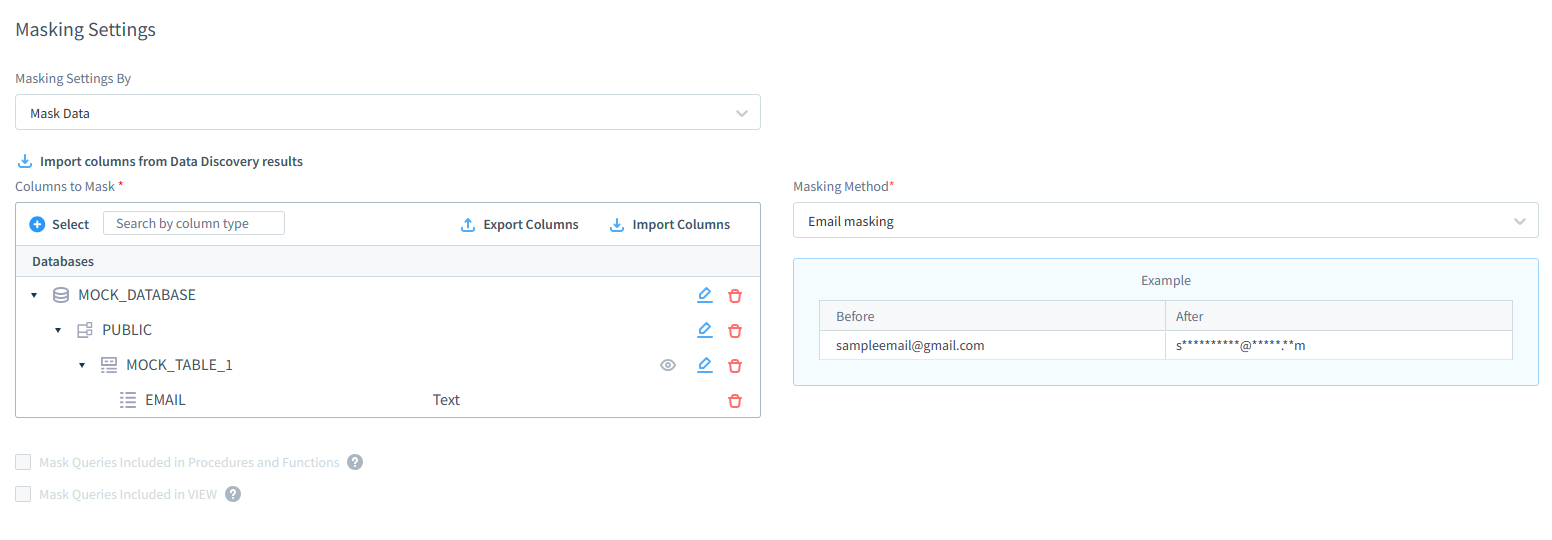
DataSunrise automatically identifies table columns and suggests corresponding masking types as appropriate, enabling you to modify them as needed.
The system can automatically detect the type of data, like the email column in the example. You can adjust this feature to analyze the data in the database rows when masking is Default.
Another significant advantage of using DataSunrise is that its masking solution does not necessitate altering the database itself. DataSunrise masks data in proxy mode as it passes to the user.
Snowflake Data Masking
Snowflake’s data masking capabilities may not offer as much detail like data type or content-based masking. Snowflake has strong security features. However, DataSunrise’s dynamic data masking provides more flexibility. This is especially beneficial for organizations that require a versatile solution.
DataSunrise goes beyond traditional column/row-based approaches. To apply masking by columns, first create a masking policy. Then, apply the policy to the column by changing the table. The SQL code for the example below is as follows:
CREATE OR REPLACE MASKING POLICY email_mask AS (val string) returns string ->
CASE
WHEN current_role() IN ('ACCOUNTADMIN') THEN VAL
ELSE '*********'
END;
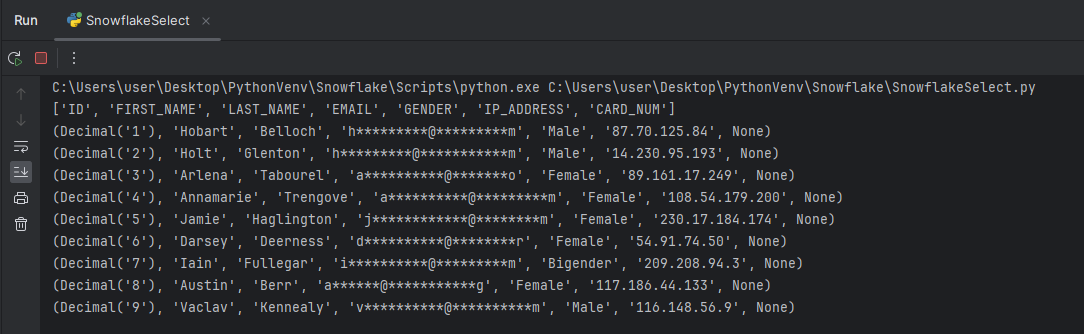
ALTER TABLE mock_table_1
MODIFY COLUMN email
SET MASKING POLICY email_mask;
The Masking results in Snowflake may look as follows.
A much wider range of setup options available in DataSunrise masking. You can select formatted masking and define your own data types along with their masking style.
In Snowflake, dynamic masking is only available in the Enterprise Edition and not in the Standard Edition.” Attempts to implement it in the standard edition will result in an ‘Unsupported feature ‘MASKING POLICY …’ message.
Sensitive Data Discovery
Another aspect where DataSunrise complements Snowflake’s security is through its sensitive Data Discovery tool. This tool searches the Snowflake database for important information. It helps set up security measures and track data usage. This capability is crucial for organizations that must adhere to various regulatory compliance standards.
Snowflake’s Security and Trust Center does not incorporate OCR (Optical Character Recognition) tools to discover sensitive data in images. Snowflake’s main focus is on keeping data safe on its platform. This includes structured and semi-structured data like JSON, Avro, Parquet, and XML.
Snowflake has security features such as data encryption and access control. However, it lacks tools for scanning and identifying sensitive information in image files.
For organizations requiring the identification and protection of sensitive data within images, third-party solutions like DataSunrise’s OCR Data Discovery tool are essential.
For businesses bound by regulatory standards, DataSunrise streamlines compliance for Snowflake security. This self-managing feature reduces the need for manual intervention and ensures compliance without constant oversight.
On the Data Compliance
DataSunrise and Snowflake both help with compliance for regulations like GDPR, SOX, PCI DSS, and HIPAA. DataSunrise offers a wider range of tools for different databases, while Snowflake focuses on compliance within its own environment. DataSunrise’s tools can work with any database to improve security. Snowflake, on the other hand, focuses on managing and protecting data within its platform.
Customizable Traffic Filtering
DataSunrise’s customizable traffic filtering enables the implementation of granular security rules. This empowers organizations to manage queries originating from specific users, applications, hosts, and IP addresses. By doing so, we bolster Snowflake security, ensuring that only legitimate traffic gains access.
Comprehensive Threat Detection
DataSunrise’s comprehensive threat detection capabilities provide real-time access and user suspicious behavior control. This feature is essential for identifying malicious database activity and automatically blocking SQL injections, further strengthening Snowflake security.
Additional Authentication Methods
To enhance Snowflake security, DataSunrise supports additional authentication methods such as Kerberos and LDAP. Major operating systems widely support these protocols, adding another layer of security to the Snowflake database.
Conclusion
Snowflake has many built-in data protection features. We have only discussed a few of them in this article. The main objective is to demonstrate that DataSunrise software enhances database security by providing additional control and options.
By using DataSunrise as a separate layer, users can have more flexibility in achieving their security objectives. This approach allows for a more customized and adaptable security strategy.
By integrating DataSunrise’s security tools with Snowflake’s secure data platform, you can greatly improve protection against various cyber threats. DataSunrise enhances Snowflake’s security measures by providing advanced features like activity monitoring, database firewall, dynamic masking, and sensitive data discovery.
Companies that prioritize Snowflake security can benefit from a comprehensive approach. They can try out a DataSunrise demo session to see how it can enhance their data protection strategy.
This demo session will allow them to understand the capabilities of DataSunrise in strengthening their security measures. By participating in the demo session, companies can assess the effectiveness of DataSunrise in safeguarding their data.
