Teradata Regulatory Compliance
Organizations running critical workloads on Teradata face strict data protection requirements. From finance to healthcare, enterprises must align their Teradata environments with standards such as GDPR, HIPAA, PCI DSS, and SOX .
Data breaches are on the rise, and regulators impose significant fines for non-compliance. For example, the European Data Protection Board frequently publishes enforcement actions under GDPR, while the U.S. Department of Health & Human Services enforces HIPAA standards across healthcare. Similarly, the PCI Security Standards Council outlines strict requirements for handling payment card data.
While Teradata offers security features like access controls, logging, and encryption, regulatory compliance demands continuous monitoring, audit-ready reporting, and sensitive data protection across structured and unstructured assets. This article explores Teradata’s compliance capabilities and demonstrates how DataSunrise extends them with automated discovery, dynamic data masking, and intelligent compliance management.
What is Compliance?
Compliance refers to the processes, controls, and technologies organizations adopt to meet regulatory, legal, and industry-specific standards for data protection. It ensures that sensitive information is collected, stored, and processed according to established rules such as GDPR, HIPAA, and PCI DSS.
In database environments like Teradata, compliance involves:
- Monitoring and auditing database activity to ensure accountability.
- Protecting sensitive data using encryption, masking, and access controls.
- Providing audit-ready evidence to regulators through detailed logs and reports.
- Aligning policies with frameworks like SOX, ISO 27001, or NIST to demonstrate security maturity.
Compliance is not static—it requires continuous monitoring, adjustments, and automation to address evolving regulations and risks. Recent insights from ISO highlight how ISO 27001 remains a global standard for security compliance, while the NIST Cybersecurity Framework provides adaptable guidance for U.S. organizations. Additionally, research from Gartner emphasizes the importance of compliance automation to reduce regulatory risk.
Native Teradata Compliance Capabilities
Teradata includes several built-in features that help organizations meet baseline compliance requirements. These tools provide the foundation for enforcing access restrictions, recording activity, and protecting sensitive information.
1. Access Control Policies
Access control is central to compliance. Teradata implements role-based privileges, allowing administrators to grant or revoke permissions at the database, schema, or table level.
-- Example: Restricting access in Teradata
CREATE ROLE compliance_officer;
GRANT SELECT, INSERT, UPDATE ON Finance.Records TO compliance_officer;
CREATE ROLE developer_readonly;
GRANT SELECT ON Finance.Records TO developer_readonly;
GRANT compliance_officer TO USER JohnDoe;
GRANT developer_readonly TO USER DevUser1;
By leveraging fine-grained access policies, organizations can enforce compliance with frameworks like SOX or HIPAA.
2. Logging and Monitoring
Teradata’s system logs capture events such as login attempts, executed queries, schema changes, and administrative actions.
-- Enable logging for query activity
BEGIN LOGGING WITH TEXT ON Finance.Records;
-- Log failed login attempts
BEGIN LOGGING LIMIT SQLTEXT=0 ON ALL;
Logs can be exported into SIEM systems to centralize monitoring. This supports accountability requirements under GDPR.
3. Encryption
Teradata supports Transparent Data Encryption (TDE) for protecting data at rest and in transit.
-- Example: Creating a table with encryption
CREATE TABLE SecureCustomers (
CustID INT,
Name VARCHAR(100),
CreditCard VARCHAR(50) ENCRYPT USING AES256
);
-- Encrypt an existing column
ALTER TABLE Finance.Records
MODIFY CreditCardNo VARCHAR(50) ENCRYPT USING AES256;
-- Check encryption status of a table
HELP COLUMN Finance.Records.CreditCardNo;
This ensures compliance with PCI DSS, which mandates strong encryption for payment data. Encryption can be applied to new and existing objects, and administrators can verify protection using built-in catalog queries.
4. User and Session Management
Authentication is integrated with LDAP or Kerberos, ensuring centralized identity control.
-- Strong password policy
CREATE PROFILE SecureProfile
AS PASSWORD = EXPIRE (30)
MINCHAR (12)
NUMERIC (1)
SPECIAL (1);
-- Assign profile to user
MODIFY USER Alice AS PROFILE = SecureProfile;
-- Lock a user account after repeated failed login attempts
MODIFY USER Bob AS MAXLOGONATTEMPTS = 5;
-- View active sessions
HELP SESSION;
-- End a suspicious session manually
ABORT SESSION 123456;
Session management provides accountability, with options to enforce strong password rules, lock accounts after failed attempts, and terminate risky sessions. These measures align with ISO 27001 and NIST Cybersecurity Framework requirements.
Compliance Challenges in Teradata Environments
- Complex Regulations: Mapping Teradata data operations to compliance frameworks like GDPR, HIPAA, and SOX can overwhelm internal teams.
- Limited Automation: Native logging lacks intelligent audit rule orchestration, forcing reliance on manual reviews.
- Sensitive Data Sprawl: Identifying and classifying personal or financial data across Teradata tables remains difficult without advanced discovery tools.
- Audit Readiness: Generating evidence for auditors requires correlating multiple logs and access records, slowing compliance cycles.
Enhanced Teradata Compliance with DataSunrise
DataSunrise extends Teradata’s built-in capabilities, providing automation, intelligence, and continuous alignment with regulations.
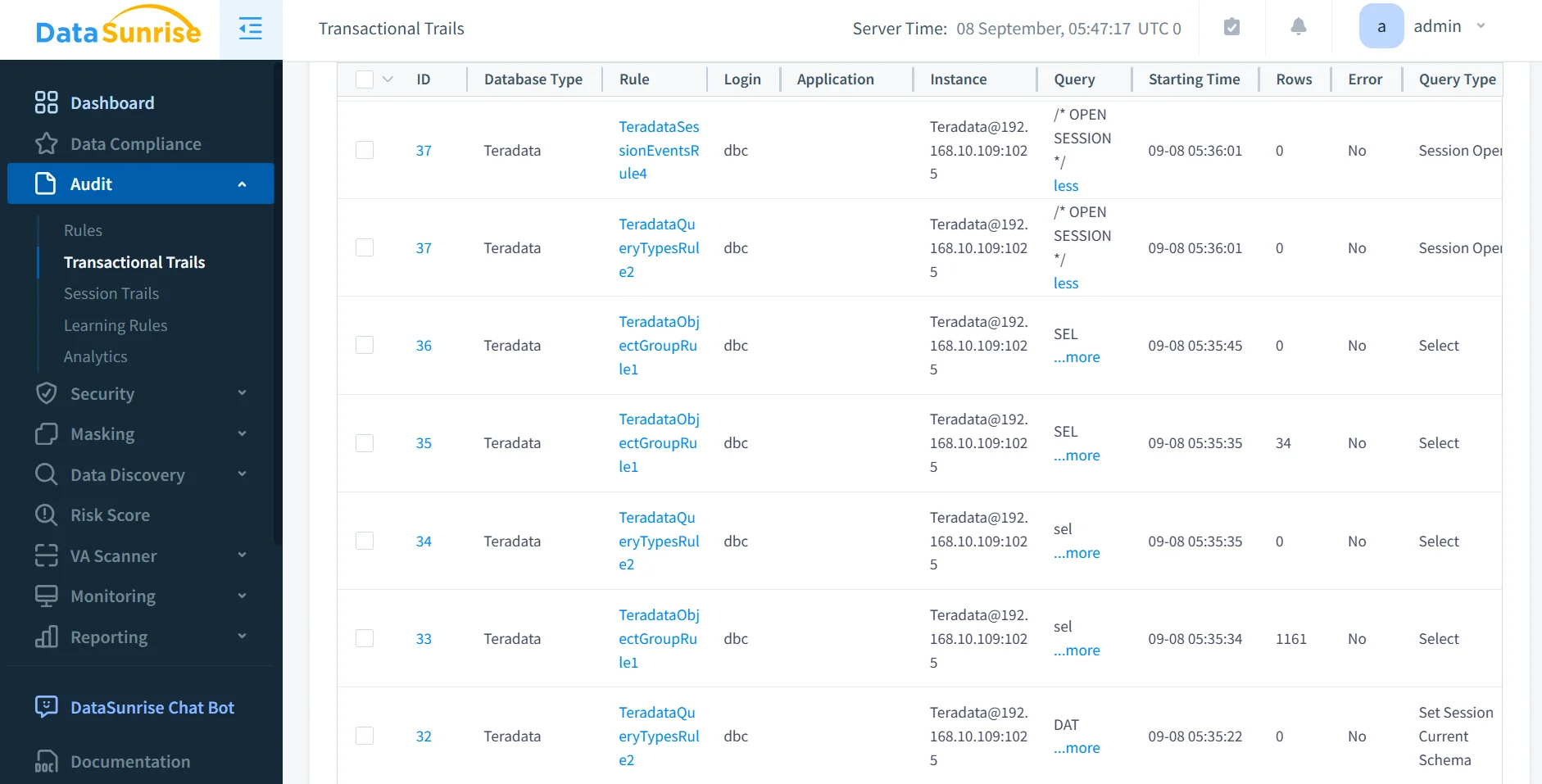
1. Audit and Monitoring
Unlike static logs, DataSunrise provides real-time data activity history for Teradata. Administrators gain visibility into queries, schema changes, and failed access attempts.
It applies ML audit rules to detect anomalies, such as repeated failed logins, unusual query spikes, or excessive access to sensitive records.
The platform generates audit-ready reports mapped to GDPR, HIPAA, PCI DSS, and SOX . These reports can be scheduled or generated instantly for regulators.
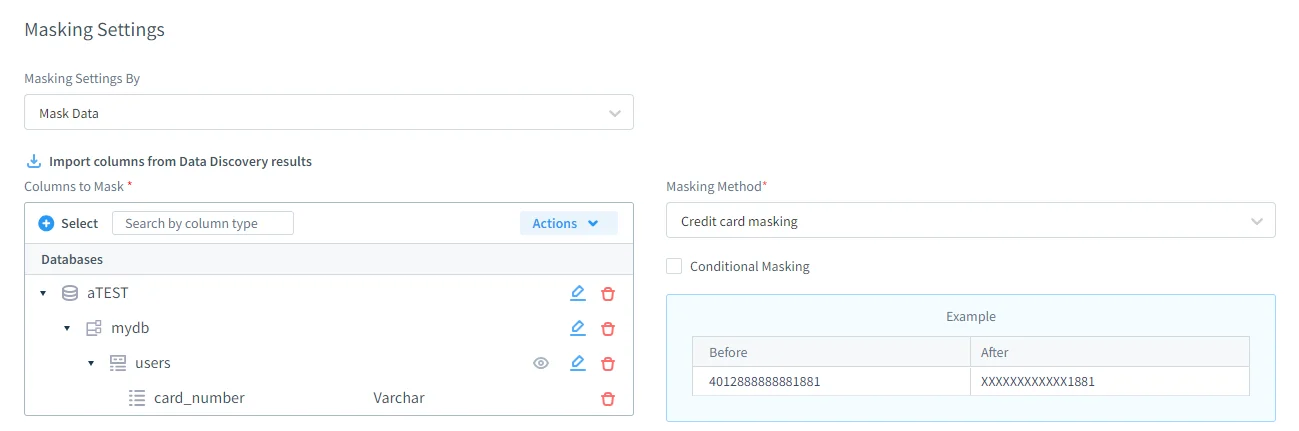
2. Dynamic Data Masking
DataSunrise enforces zero-touch dynamic masking that applies in real time, without altering the underlying database. Unauthorized users see masked values, while authorized users retain full access.
For example:
- Customer support may see
XXXX-XXXX-XXXX-1234for card numbers. - Auditors with clearance see the original values.
It implements surgical precision masking at column and row level. Policies are role- and context-aware, ensuring compliance with PCI DSS and GDPR’s data minimization principle.
3. Compliance Autopilot
DataSunrise Compliance Autopilot provides continuous regulatory calibration, automatically updating rules to align with evolving standards.
It offers centralized dashboards where compliance teams can monitor Teradata instances, track violations, and remediate issues across cloud, on-premises, or hybrid environments.
This reduces manual oversight, eliminates compliance drift, and ensures audit readiness at all times.
- Real-time regulatory alignment with frameworks such as GDPR, HIPAA, PCI DSS, and SOX
- Automated compliance policy updates without manual intervention
- Unified monitoring across multiple Teradata environments (cloud, on-premises, hybrid)
- Proactive detection of compliance drift with instant remediation options
- Audit-ready evidence generation for regulators and internal teams
4. Sensitive Data Discovery
DataSunrise automates scanning of Teradata tables to locate sensitive data such as PII, PHI, and financial information. It uses pattern matching, dictionaries, and contextual analysis to identify regulated content.
Beyond structured tables, it also supports OCR-driven discovery for unstructured data like scanned documents, images, or log files, ensuring no compliance blind spots across the enterprise data landscape.
The system generates visual classification reports aligned with GDPR and HIPAA. These reports highlight where regulated data resides, classify its type (names, addresses, card numbers, medical records), and show which business units or users have access.
Discovery tasks can be scheduled to run periodically, so any newly added data is automatically scanned and classified. This ensures continuous coverage without requiring constant manual intervention.
Finally, DataSunrise integrates discovery results directly with its masking and auditing engines. Once sensitive data is identified, policies can be applied automatically, creating a seamless workflow from discovery to protection.
- Automated discovery of PII, PHI, and financial information across Teradata tables
- OCR-driven analysis of unstructured sources such as scanned documents, images, and log files
- Visual classification reports aligned with GDPR and HIPAA compliance standards
- Scheduled discovery tasks for continuous monitoring of newly added data
- Direct integration with masking and auditing engines for seamless protection workflows
Business Impact of DataSunrise for Teradata Compliance
| Benefit | Impact |
|---|---|
| Regulatory Alignment | Automates compliance with GDPR, HIPAA, PCI DSS, and SOX, reducing manual workload. |
| Risk Reduction | Real-time monitoring and ML-driven detection cut insider and outsider threat exposure. |
| Audit Efficiency | One-click reporting accelerates audit preparation and ensures accountability. |
| Operational Scalability | Supports hybrid Teradata environments (cloud, on-prem, multi-cluster) with seamless integration. |
| Cost-Effective Compliance | Reduces total cost of compliance through automation and centralized policy orchestration. |
| Improved Transparency | Centralized dashboards enhance visibility for executives, auditors, and compliance teams. |
| Faster Incident Response | Real-time alerts enable rapid remediation of suspicious activities and policy violations. |
Conclusion
While Teradata provides a strong foundation for regulatory compliance, modern enterprises require more advanced, automated solutions to meet today’s complex frameworks. DataSunrise delivers a Compliance Autopilot—with zero-touch data masking, real-time regulatory alignment, and continuous compliance posture management—ensuring your Teradata workloads remain secure, compliant, and audit-ready.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now