Vertica Compliance Management
Vertica Compliance Management is becoming increasingly critical as Vertica is often deployed at the center of analytical ecosystems, powering BI dashboards, ML pipelines, and regulated workflows. As these environments grow, organizations must demonstrate that sensitive data follows internal policies and external regulations such as GDPR, HIPAA, PCI DSS, and SOX. Because Vertica’s architecture prioritizes speed and distributed processing rather than built-in compliance controls, enterprises increasingly require a dedicated governance layer that maintains visibility, consistency, and auditability. As a result, DataSunrise operates as this compliance control plane—centralizing classification, masking, auditing, and evidence generation for Vertica workloads.
Moreover, Vertica’s distributed execution model, its ROS/WOS storage engine, and its projection-based architecture introduce unique challenges for compliance management. Sensitive fields frequently appear in multiple projections, delete vectors complicate retention enforcement, and distributed query execution makes unified auditing difficult. Consequently, Vertica Compliance Management demands an architecture-aware strategy that unifies Vertica’s internal metadata with an external enforcement layer.
Vertica Architecture and Compliance Considerations
Vertica operates as a shared-nothing analytical engine. It stores data in ROS containers, maintains recent changes in WOS, and organizes data into projections optimized for specific workloads. These architectural choices influence compliance requirements because:
- Sensitive attributes may appear in multiple projections.
- Logical deletes remain active via delete vectors until Vertica compaction processes them.
- Distributed execution requires unified, correlated auditing.
- High concurrency demands consistent enforcement across diverse access paths.
Therefore, DataSunrise layers compliance controls around Vertica, intercepting SQL traffic, enforcing masking and security rules, and consolidating audit records. This externalized enforcement model creates strong compliance guarantees without modifying Vertica internals.
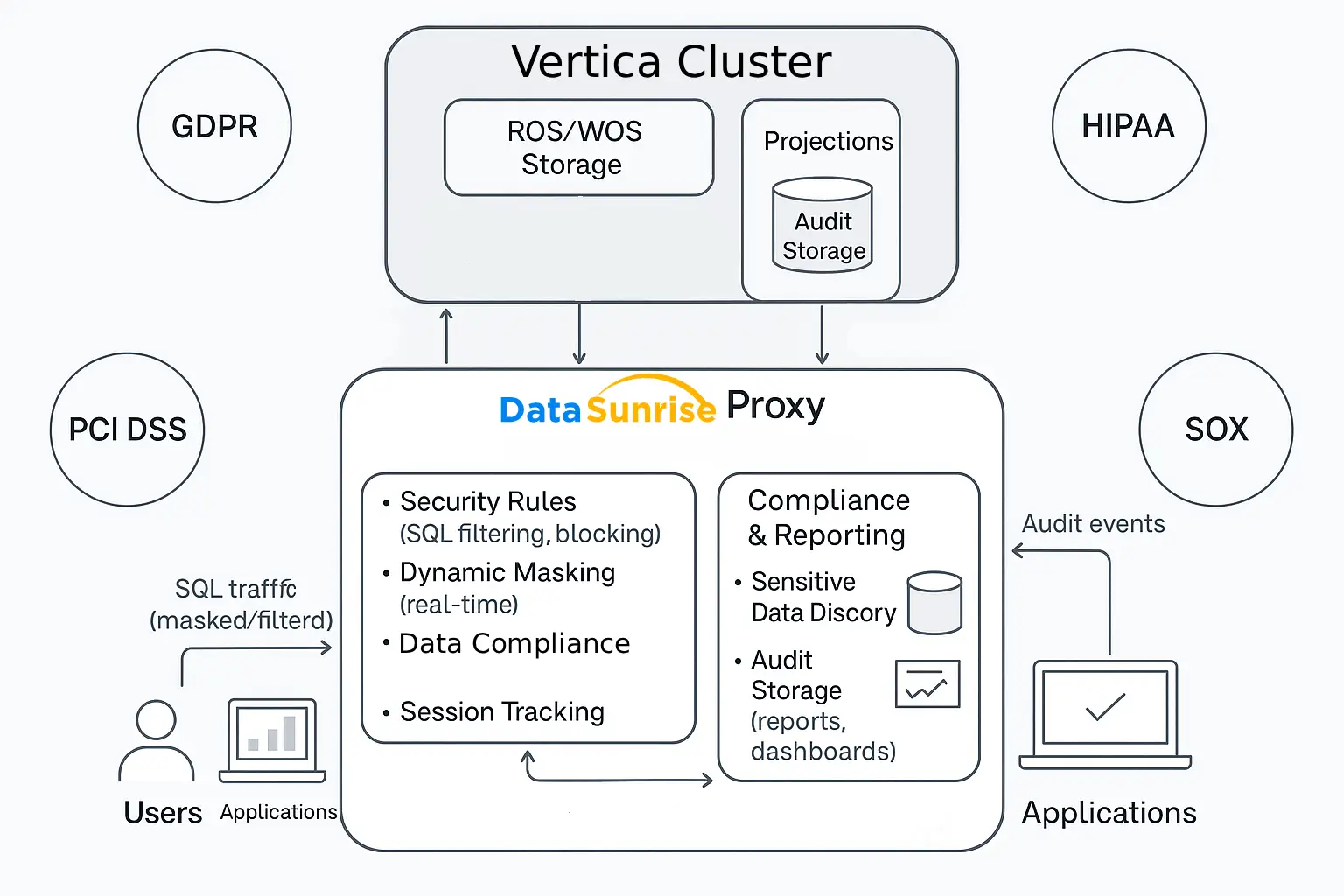
Detecting and Mapping Regulated Data
Effective Vertica Compliance Management begins with identifying where sensitive data resides inside schemas, projections, and storage layers. Because projections may differ significantly from logical table definitions, compliance teams must examine both schema objects and storage-level mappings. Manual inspection becomes impractical as datasets grow and evolve.
For example, compliance analysts frequently begin with catalog queries such as:
SELECT table_schema, table_name, column_name FROM columns WHERE column_name ILIKE '%email%' OR column_name ILIKE '%card%' OR column_name ILIKE '%ssn%';
However, catalog-only discovery rarely provides complete coverage. Consequently, DataSunrise Sensitive Data Discovery identifies regulated elements such as PII, PHI, payment data, and tokenized identifiers through automated scanning. It tags each discovery with classification metadata, enabling compliance teams to maintain a continuously updated compliance map.
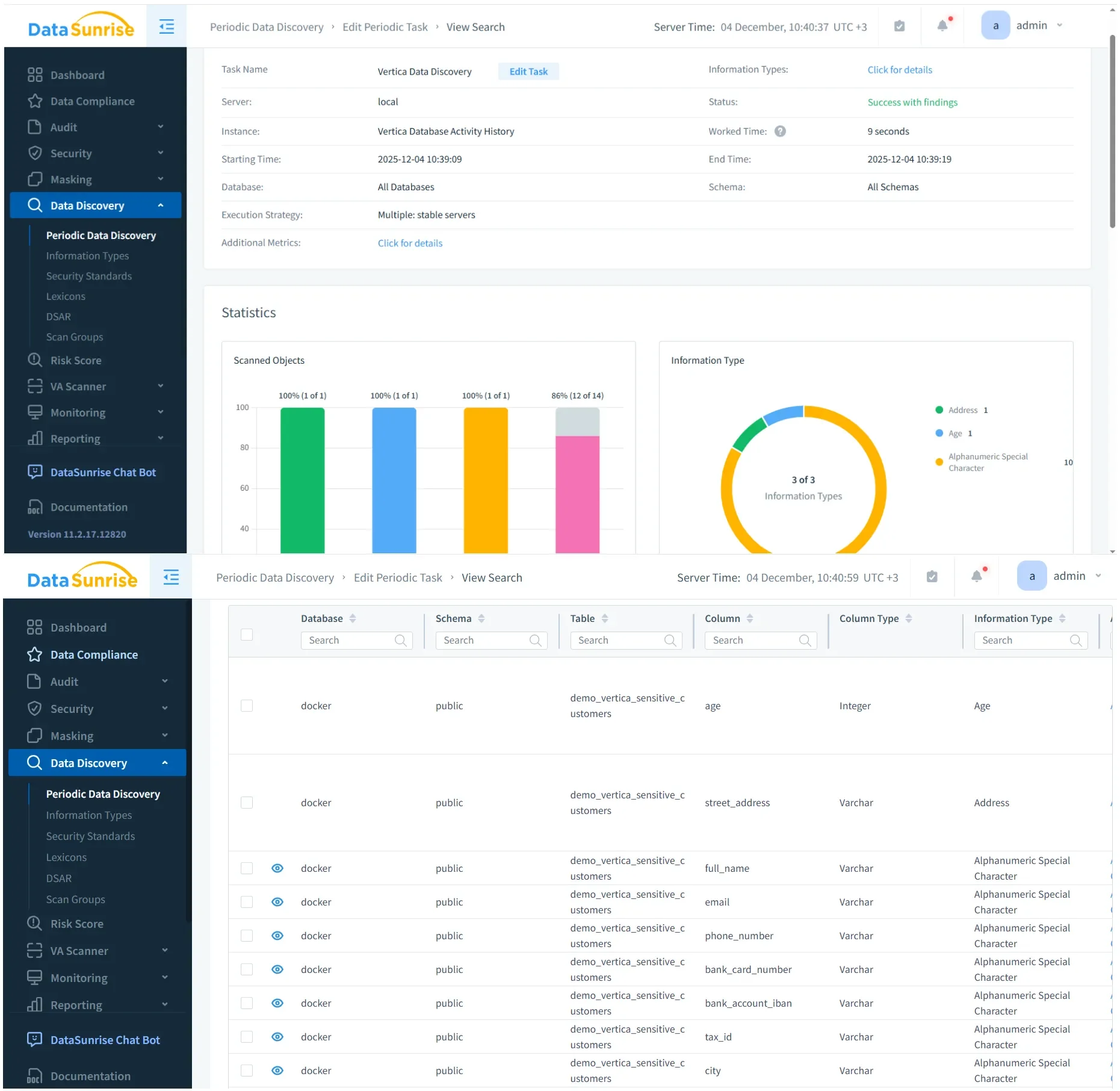
As a result, these classification outputs support masking rules, retention enforcement, and compliance scoping. Furthermore, automatic updates ensure that the mapped landscape adapts to schema drift and new data ingestion.
Policy Enforcement and Compliance-Aware Access Control
Although Vertica implements role-based access control (RBAC), compliance requires deeper context evaluation. Policies must consider user identity, workload characteristics, query intent, and associated regulated elements. DataSunrise evaluates SQL statements before execution, which ensures that:
- Least-privilege access remains consistently enforced.
- Unauthorized roles receive masked data instead of sensitive values.
- High-risk query patterns undergo blocking or controlled rewriting.
- Applications adhere to compliance-aligned access restrictions.
Therefore, policy behavior stays deterministic across BI tools, ETL jobs, SQL editors, and embedded analytics pipelines.
Masking and Pseudonymization in Vertica Compliance Architecture
Masking remains a critical element of Vertica Compliance Management. Because Vertica does not supply native masking, DataSunrise enforces masking and pseudonymization externally to prevent exposure of sensitive data. It applies masks dynamically in real time, ensuring that only authorized roles access real values.
Masking rules adapt based on:
- User role or group identity
- Application type (BI tools, JDBC, ETL systems)
- Network segment or access location
- Column-level sensitivity labels
This separation of storage and masking logic ensures high performance while maintaining regulatory alignment. For deeper masking strategies, see Dynamic Data Masking.
Unified Auditing and Compliance Evidence Collection
Vertica emits logs across numerous system tables, but raw logs do not satisfy audit or regulatory requirements. Compliance demands structured, correlated, chronological evidence across all query paths. As a result, DataSunrise consolidates:
- User sessions and access metadata
- SQL statements and parameters
- Masking decisions
- Security rule outcomes
- Cross-node execution information
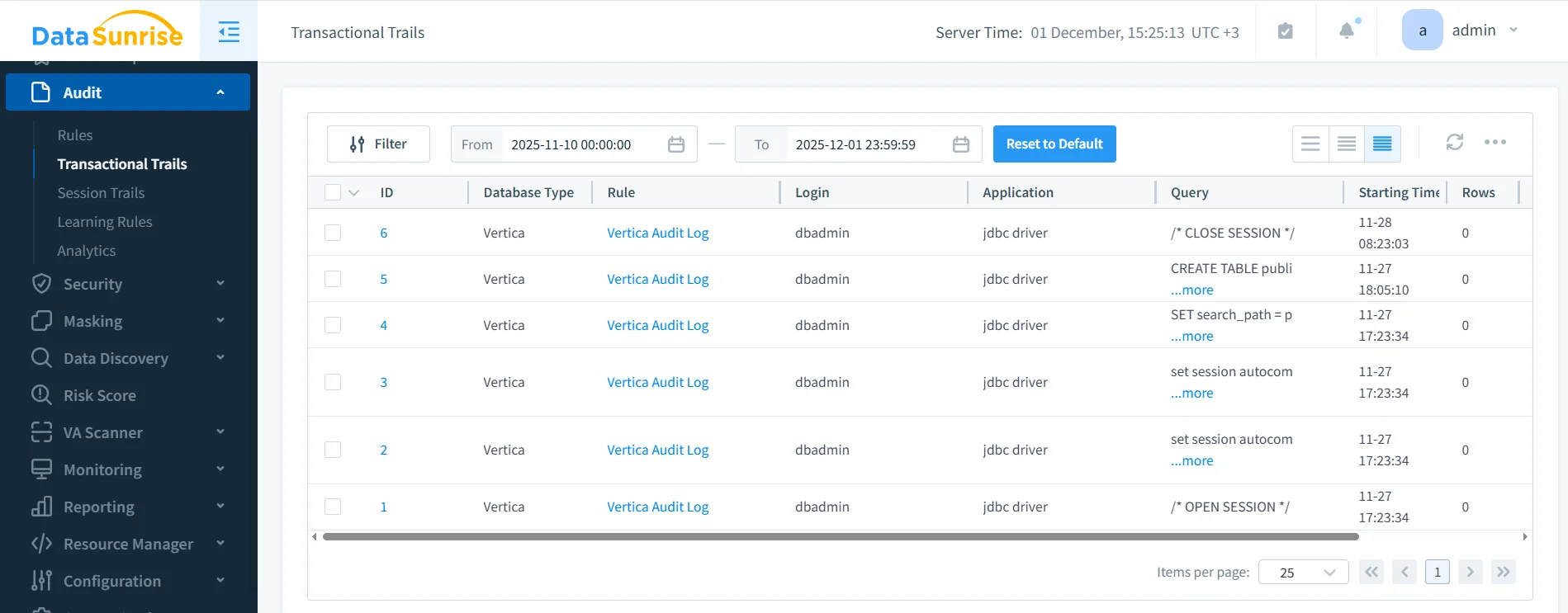
Compliance Manager uses these unified audit logs to generate automated reports aligned with GDPR, PCI DSS, SOX, and HIPAA. Consequently, teams gain verifiable, repeatable evidence for internal and external audits. For additional detail, refer to Audit Logs.
Compliance Domain Mapping: Vertica vs. DataSunrise
The table below summarizes how Vertica and DataSunrise share responsibilities across compliance domains.
| Compliance Domain | Vertica Capability | DataSunrise Capability |
|---|---|---|
| Data Identification | System catalogs and metadata queries | Automated Sensitive Data Discovery with classification tagging |
| Access Governance | RBAC permissions | Context-aware policy rules and identity-based enforcement |
| Masking | No masking features | Dynamic and static masking for PII/PHI data |
| Audit Evidence | Distributed logs across multiple system tables | Unified, correlated compliance audit streams |
| Regulatory Reporting | Manual SQL-based report creation | Automated Compliance Manager dashboards and evidence exports |
Conclusion
Vertica Compliance Management requires an architecture-aware strategy that accounts for projections, distributed execution, ROS/WOS lifecycle behavior, and concurrent analytical workloads. Because traditional governance mechanisms fail when applied to columnar analytical engines, organizations increasingly externalize compliance logic through DataSunrise.
DataSunrise provides a unified compliance control plane—offering discovery, masking, access governance, auditing, and automated reporting without modifying Vertica’s internals. Together, Vertica and DataSunrise deliver a compliance-ready analytical architecture where performance, scale, and regulatory controls coexist seamlessly.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now