Vertica Data Compliance Automation
Vertica Data Compliance Automation enables organizations to enforce regulatory requirements across large, distributed analytics environments without relying on manual intervention. As Vertica clusters expand, more pipelines, applications, and users interact with sensitive data. This increases both operational risk and the complexity of managing privacy controls. Manual review of SQL workloads, log files, and schema behavior cannot keep pace with Vertica’s scale or throughput. Consequently, automation becomes the only reliable method for ensuring consistent enforcement of compliance rules.
Vertica’s architecture—built around projections, ROS/WOS storage, and distributed execution—delivers exceptional performance but introduces governance challenges. Data may exist in several physical representations, queries may run across multiple nodes simultaneously, and workloads may originate from BI dashboards, ML notebooks, automated ETL jobs, and JDBC applications. Traditional RBAC and manual oversight cannot reliably detect unauthorized access or prevent policy drift in such an environment. Therefore, organizations require an automated compliance gateway capable of inspecting every SQL request, masking sensitive output, and generating audit evidence continuously.
DataSunrise provides this automation layer by operating between applications and Vertica. It evaluates SQL traffic, applies masking rules, blocks risky operations, and aggregates audit events in real time. As a result, compliance protections remain active whether Vertica processes 100 queries per hour or 100,000 per minute.
Automating SQL Enforcement in Vertica
Automated SQL enforcement is the first critical component of Vertica Data Compliance Automation. Instead of relying solely on Vertica’s RBAC model—which controls access but not behavior—DataSunrise Security Rules analyze SQL statements dynamically. This is especially important in environments where ETL systems and reporting tools generate queries automatically. According to the Vertica documentation, distributed execution can obscure which node or process initiated a query. Automated enforcement compensates for this by intercepting traffic at the gateway level before it enters Vertica’s execution pipeline.
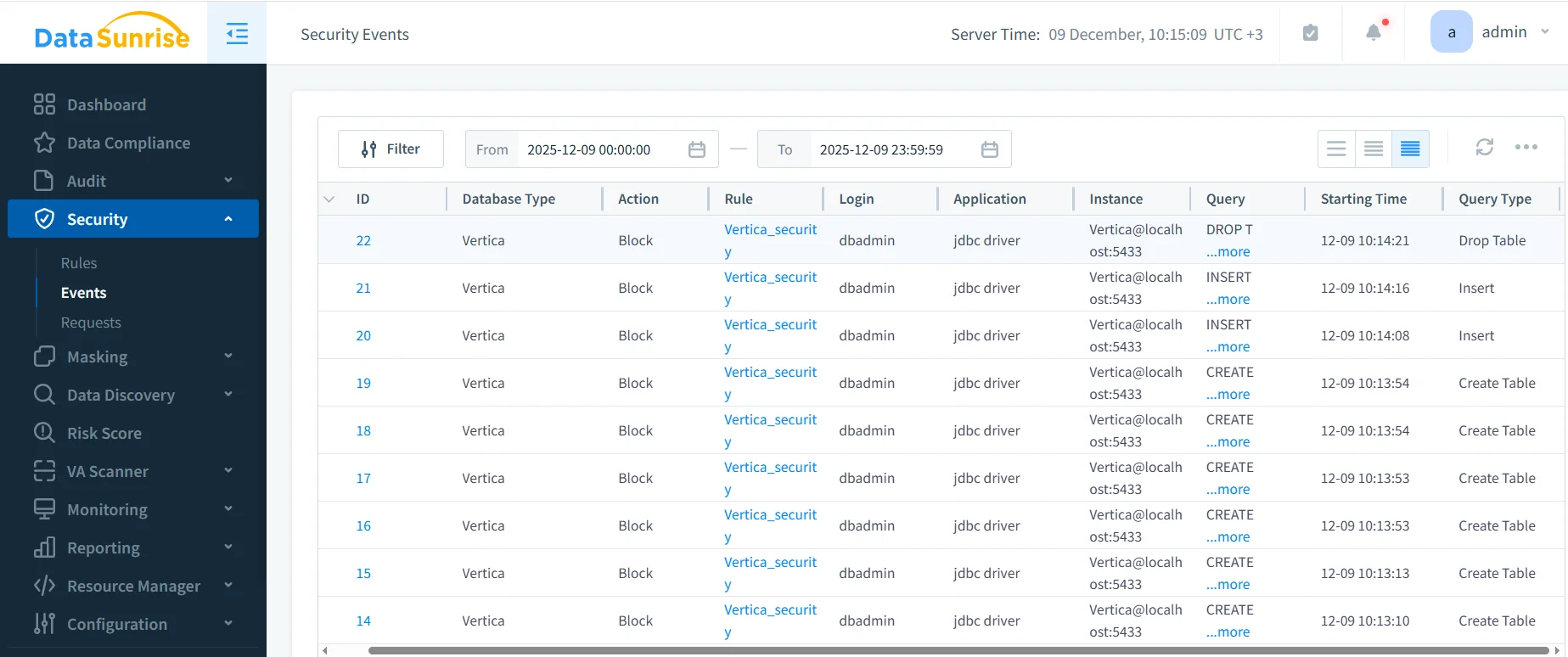
The screenshot above demonstrates automated blocking of unauthorized SQL actions, including INSERT, DROP TABLE, and CREATE TABLE. These operations may violate internal policies or external compliance requirements (e.g., PCI DSS restrictions on modifying cardholder data tables). Because enforcement happens before Vertica processes the query, organizations avoid accidental data modification, schema changes, or exfiltration attempts. Additionally, automation ensures that SQL behavior is consistent across environments—development, staging, and production—regardless of the tool issuing the request.
Real-time SQL filtering also enables more advanced automation workflows. For instance, organizations can implement:
- Time-based rules that restrict access outside approved business hours.
- Application-specific controls ensuring BI tools cannot run DDL statements.
- Data sensitivity-based controls that restrict cross-schema joins involving regulated datasets.
- High-risk pattern detection such as
SELECT *on large tables with sensitive attributes.
These automated controls prevent misuse, enforce segmentation, and reduce the burden on DBAs who would otherwise review logs manually. In multi-tenant Vertica environments, Security Rules anchor compliance boundaries between business units without requiring cluster reconfiguration.
Automated Dynamic Masking for Sensitive Vertica Data
Masking automation protects regulated data even when SQL access is permitted. GDPR, HIPAA, and PCI DSS all require that sensitive fields be masked or pseudonymized unless a user has explicit authorization. Vertica does not include native dynamic masking, so DataSunrise performs these transformations automatically at query time. This eliminates the need for custom masking views or duplicate masked datasets.
The screenshot below shows the configuration interface for selecting which Vertica columns require masking. Each field can be masked fully or partially depending on regulatory needs.
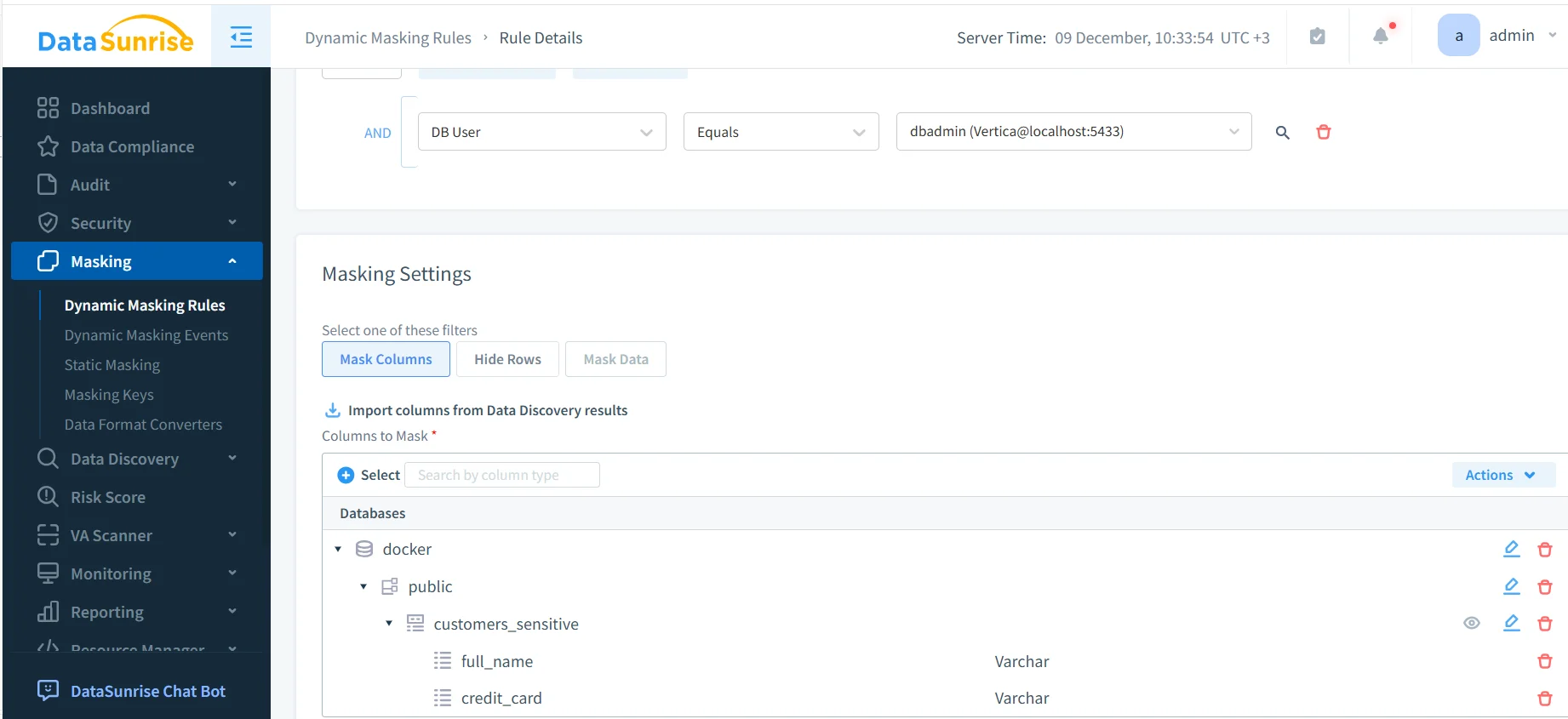
Masking column setup.
This approach allows organizations to implement privacy controls consistently across all workloads. Sensitive fields—such as full_name, phone, email, and credit_card—can be masked based on user identity, application type, or network location. For example, internal analysts may see partially masked data, external contractors may receive fully obfuscated values, and automated ETL tools may see no sensitive data at all. This fine-grained automation aligns with requirements described in GDPR pseudonymization guidance.
Furthermore, automated masking ensures that new datasets inherit compliance rules as they appear. When new columns are introduced during schema evolution or ETL updates, DataSunrise can automatically classify them and add them to masking rules without human intervention. This eliminates a major failure point in traditional manual masking strategies.
Automated Audit Trail Generation
Audit automation is a foundational requirement for regulatory compliance. GDPR Article 30, HIPAA §164.312(b), and NIST SP 800-53 require organizations to maintain detailed logs of user activity, access attempts, and data operations. Vertica provides extensive system logging, but logs are distributed across nodes and stored in multiple system tables. Manual extraction and correlation quickly become impractical.
DataSunrise resolves this challenge by automatically collecting, normalizing, and storing Vertica audit events—sessions, SQL statements, DDL, and rule-trigger actions—in a centralized audit repository.
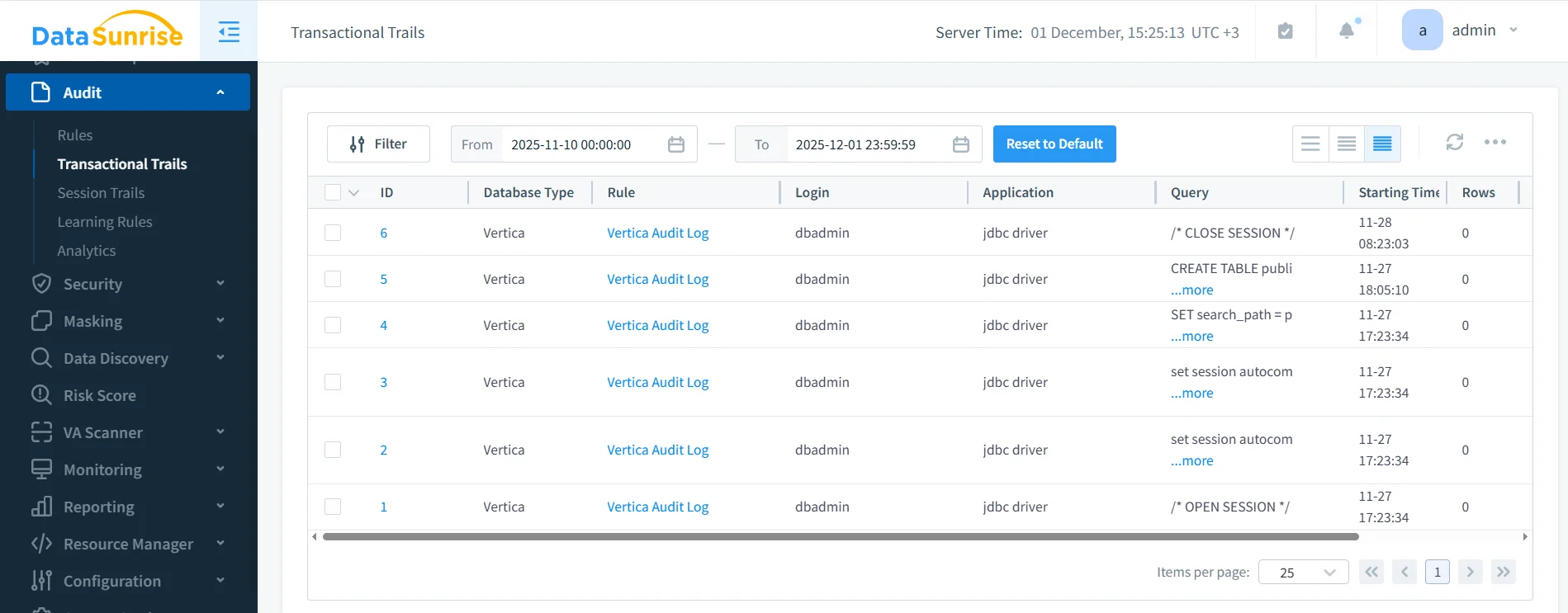
The screenshot above illustrates DataSunrise automatically recording Vertica login events, session transitions, and SQL operations. Each event includes user identity, application metadata, timestamps, and full SQL text. This eliminates the need for manual log parsing and ensures compliance teams always have reliable evidence available for internal review or external audit certification.
Organizations can extend audit automation by:
- Scheduling automated audit exports for internal compliance tasks.
- Integrating audit streams into SIEM platforms (Splunk, QRadar, Azure Sentinel).
- Configuring alert automation for suspicious patterns (e.g., unexpected DDL activity).
- Applying retention automation for audit evidence according to regulatory requirements.
Because DataSunrise captures both allowed and blocked operations, auditors can verify that compliance rules are functioning effectively across the entire Vertica footprint.
Automation Benefits Compared to Manual Processes
Automation dramatically reduces operational risk, increases consistency, and lowers compliance burden. The following table compares manual and automated compliance workflows:
| Compliance Task | Manual Approach | Automated Approach |
|---|---|---|
| SQL Enforcement | DBAs review logs after incidents | Real-time blocking before execution |
| Masking | Static views, code rewrites, slow updates | Dynamic masking applied instantly |
| Auditing | Parsing system tables on each node | Unified audit trail across environments |
| Reporting | Manual compilation of evidence | Auto-generated compliance reports |
Conclusion
Vertica Data Compliance Automation transforms how organizations manage privacy, access control, and audit obligations in distributed analytical environments. Automated SQL filtering protects against unauthorized behavior, dynamic masking safeguards sensitive fields, and centralized auditing ensures traceability across all workloads. As Vertica environments scale, automation delivers consistent enforcement that manual processes cannot match.
By combining Vertica’s analytical power with DataSunrise’s policy-driven automation layer, enterprises gain a sustainable compliance framework that supports growth, minimizes risk, and meets the expectations of GDPR, HIPAA, PCI DSS, and NIST-aligned security programs.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now