Audit Guide
The data auditing capability enables real-time database activity monitoring and logging the information about queries reaching the database, such as database content modification, extraction or deletion. DataSunrise provides real-time tracking of database user actions, also monitors changes in database configuration and system settings. In this audit guide, we demonstrate how to configure DataSunrise to audit all queries directed to the target database.
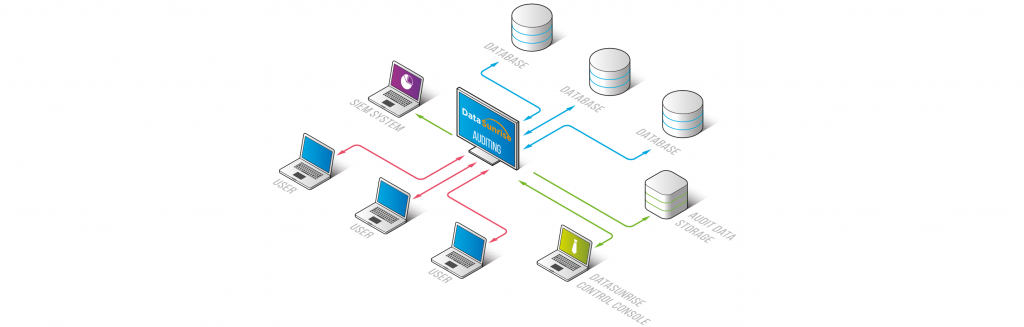
The audit logs are stored in the DataSunrise-integrated SQLite database or in an external database. Logged data helps to comply with requirements of regulatory standards such as SOX, HIPAA, PCI DSS, and other regulators and acts.
Data Audit function is available in Sniffer mode and in Proxy mode. You can create new Data Audit Rules or edit existing ones in the Data Audit section. Rules can be set to audit transaction on a certain database or from certain database users, IP addresses and client applications.
To enhance your understanding of data auditing, we highly recommend visiting our YouTube channel to watch our videos on this topic. These videos not only showcase our auditing solution but also familiarize you with alternative data auditing methods using native DBMS features.
Why Database Auditing Matters
Database auditing is critical for detecting unauthorized access, monitoring administrator actions, and ensuring traceability of all operations involving sensitive data. This is especially important in industries subject to regulations such as GDPR, SOX, HIPAA, and PCI DSS, where proving control over data access is legally required.
By implementing granular auditing rules with tools like DataSunrise, organizations can detect anomalous behavior, investigate incidents faster, and demonstrate compliance through auditable trails. Without such mechanisms, even a minor breach or insider misuse can go undetected—posing financial and reputational risks.
What is DataSunrise Data Audit?
DataSunrise Data Audit is a core feature of the platform that enables fine-grained logging of all database activity—across users, applications, and environments. It operates in real time and captures every query, modification, or connection attempt that passes through the proxy or sniffer mode.
This capability allows organizations to enforce least-privilege access, monitor privileged users, and satisfy requirements from compliance frameworks like HIPAA, SOX, and PCI DSS. With built-in filters and alerting, the DataSunrise Data Audit system acts as both a forensic tool and a compliance enabler.
Creating an Audit Rule
Let’s assume that you’ve already created the target database profile. Then to audit our test database, it is necessary to create and configure an Audit Rule. In this case, the sequence of actions is the following:
- Navigate to Audit → Rules. Then click Add Rule to create a new Audit Rule.
- Configure your Audit Rule to log all queries to the database (see notes below).
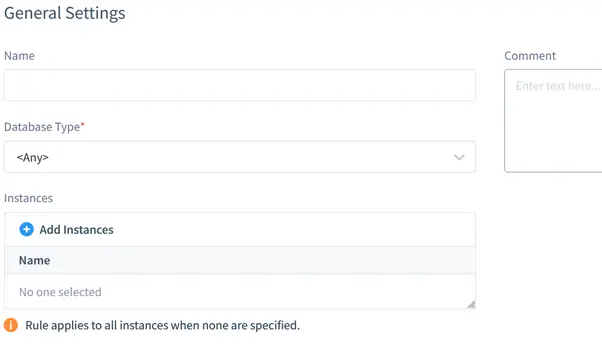
In the Main section subsection, the target database information is specified. It includes database type (PostgreSQL), database instance (as the target database entry is named in the Configurations) and the Rule’s logical name.
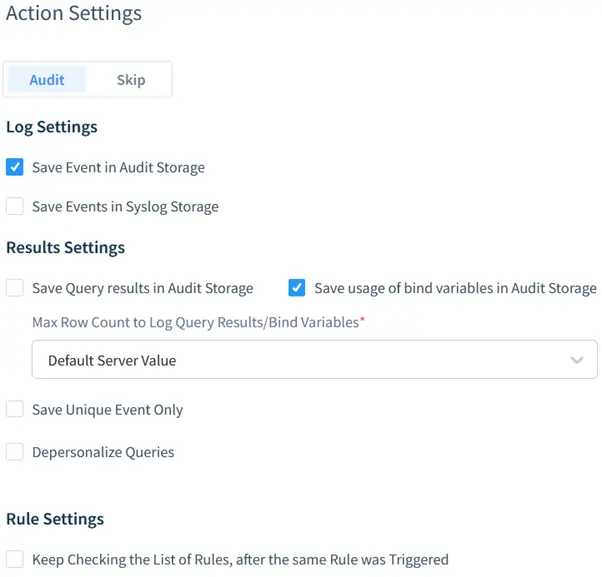
By default, the “Audit” action is selected. It means that DataSunrise will audit user queries when the rule is triggered. To log database responses (the output), the Log Data checkbox is checked.
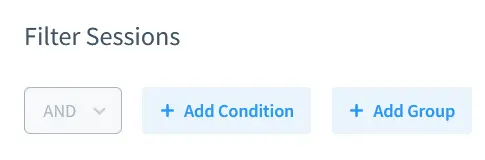
Since the current scenario requires all user queries to be audited, Filter Sessions are left as by default. Thus, any query to the database regardless of its source IP address will trigger the rule.
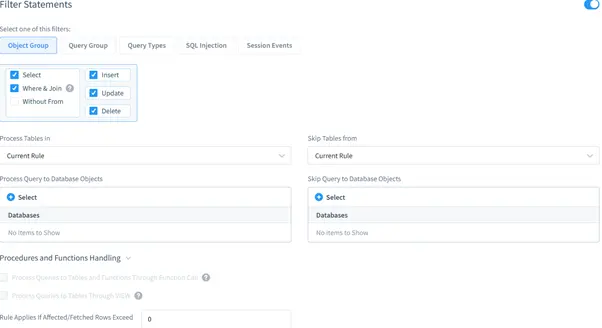
Filter Statements settings are as by default as well. Thus, DataSunrise will audit all queries directed to all database objects.
Viewing Database Audit Results
This stage includes demonstration of auditing results. The Audit Rule which was created at the previous stage is configured to be triggered by any incoming user query. Here’s what happens when DataSunrise receives a user query.
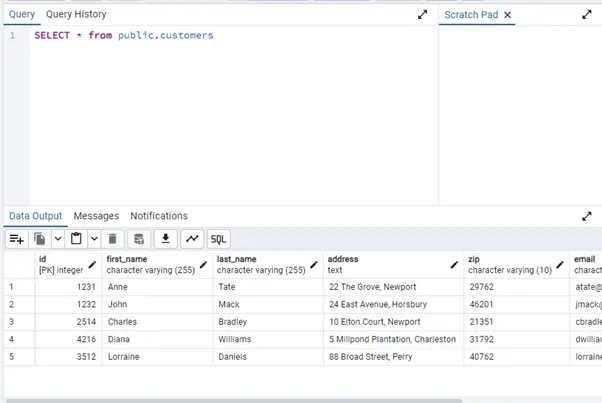
- Let’s send the following query via PGAdmin:
- The database outputs the table contents:
- Now let’s check the auditing results in the DataSunrise’s Web Console. Navigate to the Data Audit → Transactional Trails subsection.
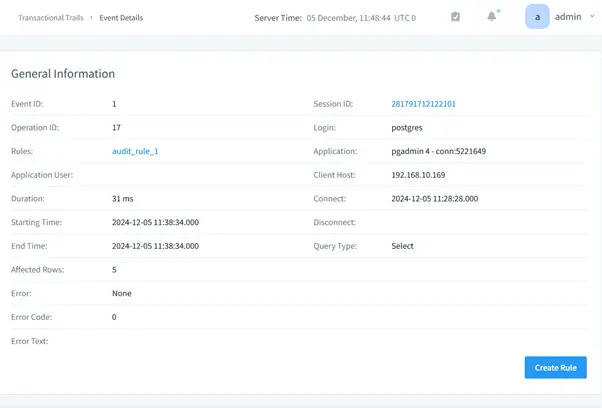
- To view detailed information about some event, click event’s ID. In a new tab, the event’s details will be displayed: code of the query, basic information, session information, database objects involved in the query and the query results.
SELECT * FROM public.customers;
Each event logs comprehensive metadata including IP addresses, application names, timestamps, and execution details.
Scrolling down reveals additional event details, including the complete SQL query statement and database objects the query touches. The query accessed sensitive data fields including credit card numbers, email addresses, and ZIP codes.
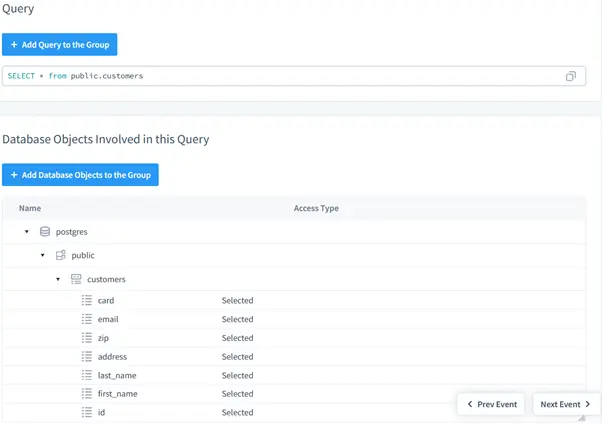
Query results can be displayed, but enabling this feature significantly impacts audit database storage consumption.
Real-World Use Cases: Applying DataSunrise Data Audit
The DataSunrise Data Audit engine isn’t just a logging tool—it’s a compliance enabler and incident response ally. Here’s how organizations use it to meet regulatory and operational requirements in live environments:
| Use Case | How DataSunrise Helps |
|---|---|
| SOX Compliance | Tracks privileged user activity on financial systems and logs changes to critical configurations. Supports external audit reviews with detailed transaction histories. |
| HIPAA Monitoring | Audits all queries involving PHI, including read access to medical records. Captures session metadata for accountability and breach investigation. |
| PCI DSS Enforcement | Monitors credit card data access in real time and logs queries that touch PAN fields. Supports alerting on unauthorized access attempts. |
| Data Exfiltration Detection | Flags suspicious query volumes, DUMP statements, and unapproved exports—especially from new IPs or clients. |
| Insider Threat Visibility | Captures admin actions, schema modifications, and unusual object access—all correlated with user identities and timestamps. |
Because DataSunrise works at the proxy layer, it can enforce auditing even when the database’s native logging is disabled or bypassed. This makes it an essential part of modern data security and governance strategies.
Conclusion
Robust database auditing is critical for detecting abnormal behavior, ensuring regulatory compliance, and maintaining accountability in today’s data-driven environments. DataSunrise enables teams to implement detailed, real-time logging of queries and transactions—without impacting database performance or disrupting application operations.
Through capabilities such as role-based access filtering, proxy-level auditing, and session metadata collection, organizations gain complete insight into who accessed specific data, when, and through which methods. This results in a centralized audit log that accelerates incident response, streamlines compliance with frameworks like SOX, HIPAA, and PCI DSS, and helps prevent unauthorized data access.
Whether you’re auditing a few sensitive tables or your entire production infrastructure, DataSunrise delivers the automation, scalability, and precision required to secure your data and meet regulatory demands.