
Machine Learning in IT Security

As machine learning revolutionizes cybersecurity operations, organizations worldwide are implementing ML-powered security solutions across critical infrastructure. While machine learning delivers unprecedented threat detection capabilities, it introduces sophisticated security challenges that traditional IT security frameworks cannot adequately address.
This guide examines machine learning applications in IT security, exploring implementation strategies that enable organizations to leverage ML's defensive potential while maintaining robust protection against evolving cyber threats.
DataSunrise's advanced ML-powered security platform delivers Zero-Touch Security Intelligence with Autonomous Threat Detection across all major database environments. Our Context-Aware Protection seamlessly integrates machine learning with traditional security controls, providing Surgical Precision threat management for comprehensive IT security protection.
Understanding Machine Learning in Cybersecurity
Machine learning transforms IT security from reactive defense to proactive threat intelligence. Unlike traditional rule-based systems, ML algorithms analyze vast datasets to identify patterns, predict threats, and adapt to emerging attack vectors in real-time.
ML-powered security encompasses anomaly detection, behavioral analysis, and automated response mechanisms. These capabilities enable organizations to detect sophisticated attacks that bypass conventional security rules while maintaining comprehensive data protection and reverse proxy architectures.
Critical ML Security Applications
Behavioral Analytics and User Monitoring
Machine learning excels at establishing baseline user behaviors and detecting deviations that indicate potential security threats. ML algorithms analyze login patterns, data access behaviors, and system interactions to identify insider threats and compromised accounts through user behavior analysis with database activity monitoring and static data masking capabilities.
Automated Threat Detection and Response
ML-powered security systems provide real-time threat detection by analyzing network traffic, system logs, and application behaviors. These systems automatically identify SQL injection attempts, malware signatures, and zero-day exploits while triggering immediate response mechanisms including database firewall protection and least privilege principle enforcement.
Technical Implementation Examples
Anomaly Detection for Security Events
This implementation demonstrates how to use machine learning for detecting unusual security patterns in database access logs. The system establishes a baseline of normal behavior and flags deviations that could indicate security threats:
import numpy as np
from sklearn.ensemble import IsolationForest
class MLSecurityDetector:
def __init__(self):
self.isolation_forest = IsolationForest(contamination=0.1)
self.baseline_established = False
def train_baseline(self, historical_data):
"""Establish normal behavior baseline"""
features = self._extract_features(historical_data)
self.isolation_forest.fit(features)
self.baseline_established = True
def detect_anomaly(self, current_activity):
"""Real-time anomaly detection"""
features = self._extract_features([current_activity])
is_anomaly = self.isolation_forest.predict(features)[0] == -1
score = abs(self.isolation_forest.decision_function(features)[0])
return {
'anomaly_detected': is_anomaly,
'risk_score': score * 100,
'threat_level': 'HIGH' if is_anomaly and score > 0.5 else 'LOW'
}
SQL Injection Detection System
This ML-based system analyzes SQL queries in real-time to detect injection attacks by examining query patterns and identifying malicious syntax commonly used in SQL injection attempts:
from sklearn.feature_extraction.text import TfidfVectorizer
from sklearn.ensemble import RandomForestClassifier
import re
class MLSQLInjectionDetector:
def __init__(self):
self.vectorizer = TfidfVectorizer(max_features=500)
self.classifier = RandomForestClassifier(n_estimators=50)
def detect_sql_injection(self, query):
"""Analyze query for SQL injection patterns"""
processed_query = re.sub(r'\s+', ' ', query.lower())
query_features = self.vectorizer.transform([processed_query])
prediction = self.classifier.predict(query_features)[0]
confidence = max(self.classifier.predict_proba(query_features)[0])
return {
'sql_injection_detected': bool(prediction),
'confidence': confidence * 100,
'recommended_action': 'BLOCK' if prediction and confidence > 0.8 else 'MONITOR'
}
Implementation Best Practices
For Organizations:
- Data Quality Foundation: Establish comprehensive data collection with audit logs for ML training
- Hybrid Approach: Combine ML capabilities with traditional access controls and test data management
- Continuous Learning: Implement feedback mechanisms for model improvement with report generation
- Human Oversight: Maintain security analyst oversight for ML-generated alerts
For Technical Teams:
- Model Validation: Regularly test ML models against new attack vectors
- Real-Time Processing: Implement low-latency ML inference for immediate threat response
- Feature Engineering: Develop security-relevant features from monitoring data and synthetic data generation
- Model Security: Protect ML models from adversarial attacks with database encryption
DataSunrise: Comprehensive ML-Powered Security Solution
DataSunrise provides enterprise-grade machine learning security designed specifically for database environments. Our solution delivers AI Compliance by Default with Maximum Security, Minimum Risk across 50+ supported platforms.
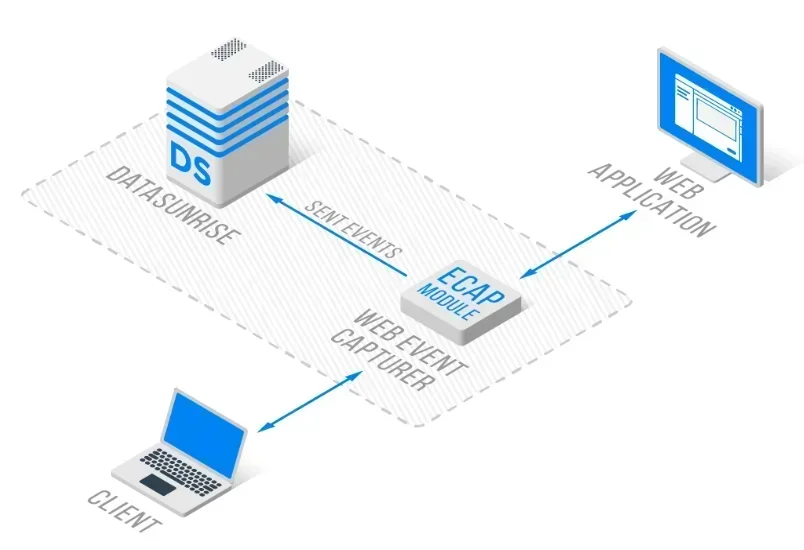
Key ML-Powered Features:
- Advanced Behavioral Analytics: ML-powered anomaly detection with user behavior monitoring
- Intelligent Threat Detection: Context-aware threat identification using machine learning algorithms
- Automated Response Systems: ML-driven incident response with real-time protection
- Dynamic Data Protection: Intelligent data masking using ML algorithms
DataSunrise's Flexible Deployment Modes support on-premise, cloud, and hybrid environments with Zero-Touch Implementation. Organizations implementing DataSunrise achieve significant reduction in false positives and faster threat detection through intelligent automation.
Regulatory Compliance Considerations
ML-powered security systems must address comprehensive regulatory requirements:
- Data Protection: GDPR compliance for ML training data and automated decision-making
- Industry Standards: Healthcare (HIPAA) and financial services (PCI DSS) requirements
- AI Governance: Emerging AI regulations requiring explainable security decisions
- Audit Requirements: Comprehensive compliance reporting for ML-driven decisions
Conclusion: Securing the Future with Intelligent Defense
Machine learning in IT security represents a fundamental evolution from reactive to predictive cybersecurity. Organizations implementing ML-powered security frameworks position themselves to defend against sophisticated threats while reducing operational overhead.
As cyber threats become increasingly sophisticated, machine learning transforms from optional enhancement to essential security capability. By implementing comprehensive ML security frameworks, organizations can confidently protect their digital assets while adapting to evolving threat landscapes.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now