
AlloyDB for PostgreSQL Data Audit Trail

Every security officer eventually asks the same question: “Can I trust the numbers in my database?”
With AlloyDB for PostgreSQL Data Audit Trail strategies in place, the answer becomes a confident yes. This article shows how to build a living, searchable record of every touch on your data—leveraging Google Cloud’s native audit capabilities, DataSunrise’s powerful overlay, and a dash of generative AI for real‑time anomaly detection.
Why an Audit Trail Still Matters
Threat actors automate, regulations proliferate, and engineering teams move faster than ever. An audit trail is the immutable narrative that unifies these forces: it proves compliance with GDPR, HIPAA, PCI‑DSS and emerging AI acts, traces insider or external breaches down to the row‑level statement, and feeds security analytics and machine‑learning pipelines with high‑fidelity events. Google Cloud’s own overview calls audit logs “the backbone of your risk‑management story.” (AlloyDB Security & Privacy documentation) Yet the raw logs are only half the picture. We’ll start there, then layer on masking, discovery, and generative reasoning.
From Logs to Real‑Time Intelligence
An effective AlloyDB for PostgreSQL Data Audit Trail hinges on capturing all activity as it happens—no overnight exports, no blind spots. The two native streams that matter are Cloud Audit Logs (Admin & Data Access) for infrastructure‑level events (Configure Data Access Audit Logs) and the pgAudit extension for fine‑grained session and object access inside AlloyDB (View pgAudit logs in AlloyDB). A common architecture sends both streams to BigQuery for long‑term retention and to Google Security Operations or a SIEM for live queries, usually in under ten seconds—so “real‑time audit” is more than marketing talk.
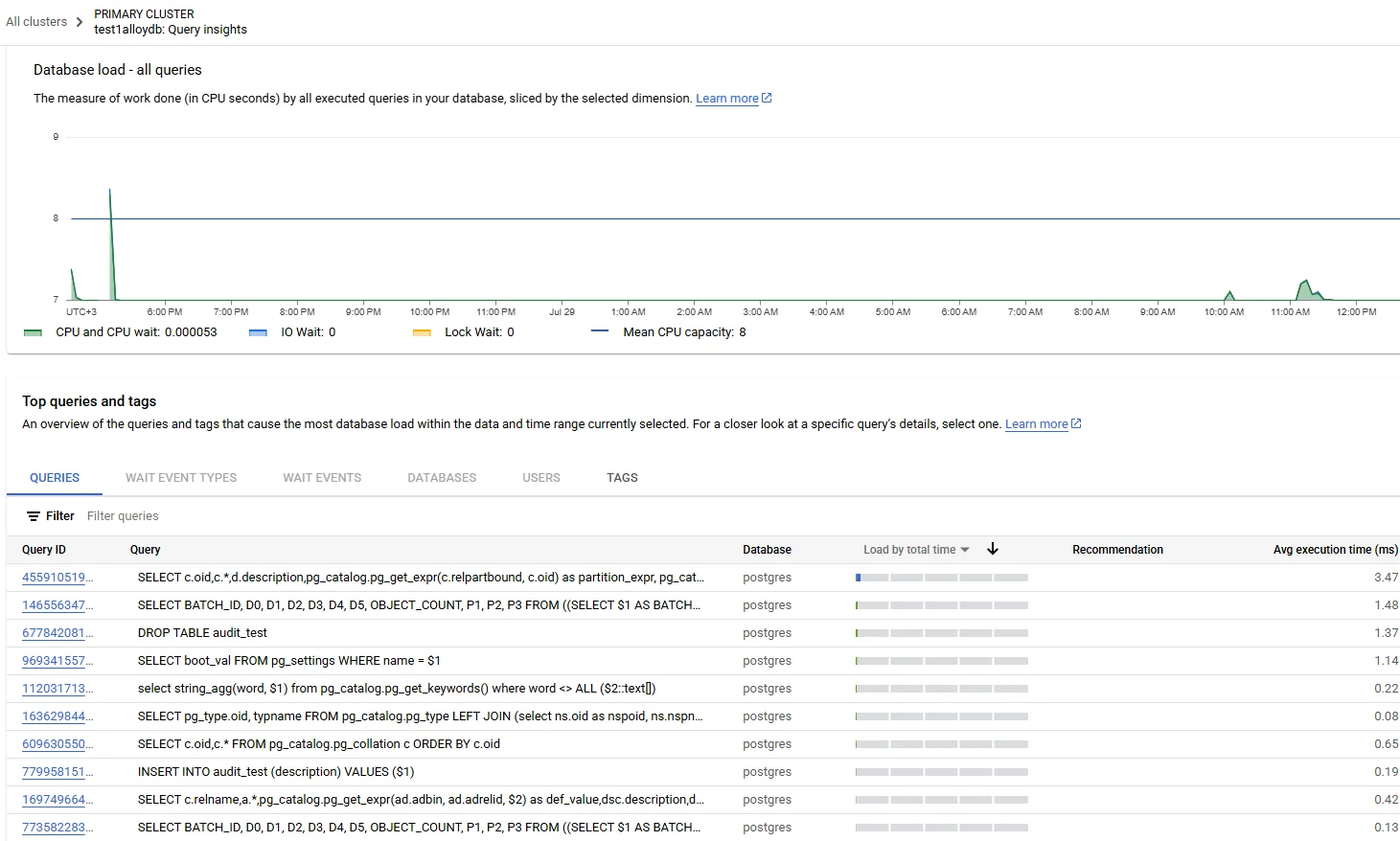
Tip — Correlate quickly: store pgAudit’s session_id in Cloud Audit Logs’ protoPayload.authenticationInfo.principalEmail field to stitch statements to identities without JOIN gymnastics.
Native Audit: Enabling pgAudit on AlloyDB
Despite its managed veneer, AlloyDB remains Postgres under the hood—meaning the beloved pgaudit extension just works. First, activate the extension via the Google Cloud CLI:
gcloud alloydb clusters update prod-cluster \
--database-flags shared_preload_libraries=pgaudit \
--database-flags pgaudit.log=read,write,ddl,role
Then reload or restart the instance and verify with:
SHOW pgaudit.log;
SELECT pgaudit_get_current_config();
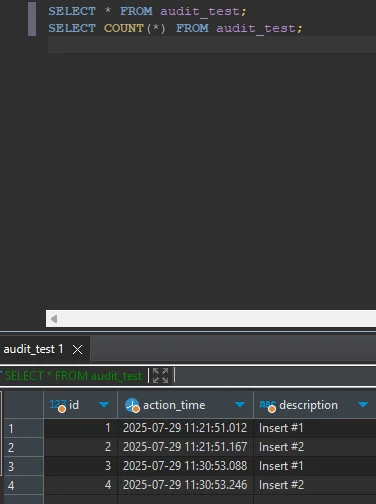
Logs now surface in cloudsql.googleapis.com/postgres.log and can be filtered by jsonPayload.msg. Because pgAudit’s grammar and output match open‑source Postgres, teams migrating from self‑managed environments face no learning curve—another win for operational continuity.
Beyond the Basics: DataSunrise Audit Layer
Native logs are great, but modern security stacks crave context—user reputation, data classification, masking status, and behavior baselines. DataSunrise slides in as an inline proxy or agent, capturing row‑level audit logs, applying risk‑adaptive dynamic masking so analysts see only obfuscated data, running data discovery jobs that tag new columns the moment they appear, and offering LLM & ML tools that learn normal query shapes and flag outliers. Because DataSunrise can read pgAudit statements, you’re not duplicating workload—just enriching it.

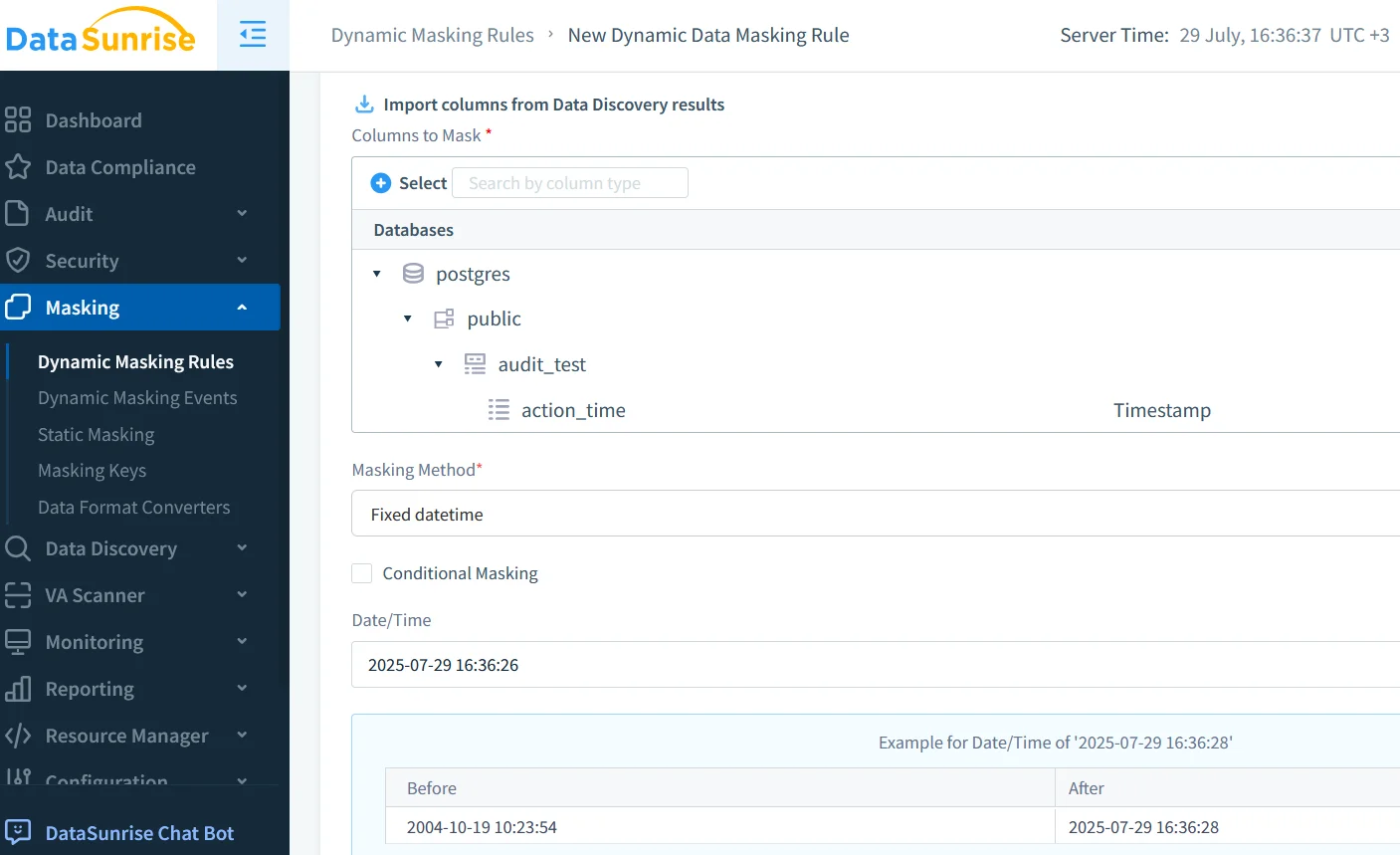
Dynamic Masking & Data Discovery: Guardrails in Motion
Real‑time audit trails shine brightest when the blast radius is already minimized. Combining pgAudit events with DataSunrise’s masking and discovery stack instantly answers questions such as whether sensitive data left the vault or when a new SSN column appeared. The result is an audit log that carries semantic weight—not just bytes.
Generative AI Meets the Audit Trail
Large Language Models are superb at pattern recognition in free‑text—exactly what audit messages look like. A lightweight Vertex AI example:
from vertexai.language_models import TextGenerationModel
model = TextGenerationModel.from_pretrained("gemini-pro")
log_line = "AUDIT: SESSION,1,SELECT,public.customers,id=42"
prompt = f"Rate the risk of this PostgreSQL audit event on a scale of 1‑5 and explain: {log_line}"
response = model.predict(prompt)
print(response.text)
Security teams often stream pgAudit lines into a Cloud Function that calls the model and posts high‑risk scores to Slack—closing the loop between raw data and human action in under a minute.
Security & Compliance Landscape
A robust AlloyDB for PostgreSQL Data Audit Trail positions you ahead of auditors. The matrix below shows how log sources cover common mandates:
| Requirement | Native | DataSunrise | Note |
|---|---|---|---|
| GDPR Art. 30 records | ✔︎ pgAudit | ✔︎ Enriched user context | Retention ≥ 5 years |
| HIPAA § 164.312(b) | ✔︎ Cloud Audit Logs | ✔︎ Masking & Alerts | Integrity checksums |
| PCI-DSS 10.x | ✔︎ pgAudit + BigQuery | ✔︎ Real-time notifications | 90-day online, 1-year archive |
For a deeper dive, see DataSunrise’s guide on data compliance regulations.
Putting It All Together
End‑to‑end flow: pgAudit and Cloud Audit Logs feed a Pub/Sub topic; a DataSunrise proxy enriches events; Cloud Functions call genAI for risk scoring; BigQuery stores the canonical audit table (dataset.alloydb_audit); and dashboards in Looker BI or notebooks provide investigation access. One query surfaces suspect reads in the last hour:
SELECT timestamp, actor_email, statement, risk_score
FROM `security.alloydb_audit`
WHERE risk_score >= 4
ORDER BY timestamp DESC
LIMIT 100;
Conclusion: Future‑Ready, Human‑Friendly
An audit trail is more than a compliance checkbox—it’s your real‑time narrative of truth. By weaving together native AlloyDB logging, DataSunrise’s enrichment, and the semantic power of generative AI, you convert dense log lines into actionable insight. Start small—enable pgAudit today—and iterate. The result is an AlloyDB for PostgreSQL Data Audit Trail that scales with your business, your threat model, and yes, even your imagination.
Explore DataSunrise’s complete data audit capabilities and begin your journey.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now