
AlloyDB for PostgreSQL Database Activity History

AlloyDB for PostgreSQL fuses Google‑scale elasticity with the comfort of vanilla psql. That freedom widens the blast radius of a typo or breach, so Database Activity History—a chronologically ordered map of every session‑ and object‑level event—becomes indispensable. Whether you are chasing a runaway UPDATE or proving PCI‑DSS compliance, the story starts here.
Real‑time Audit: Getting 360° Visibility
AlloyDB exposes two complementary audit channels. Google Cloud Cloud Audit Logs records administrative actions, while the open‑source pgAudit extension traces user‑generated SQL. Turning the firehose on is a single command:
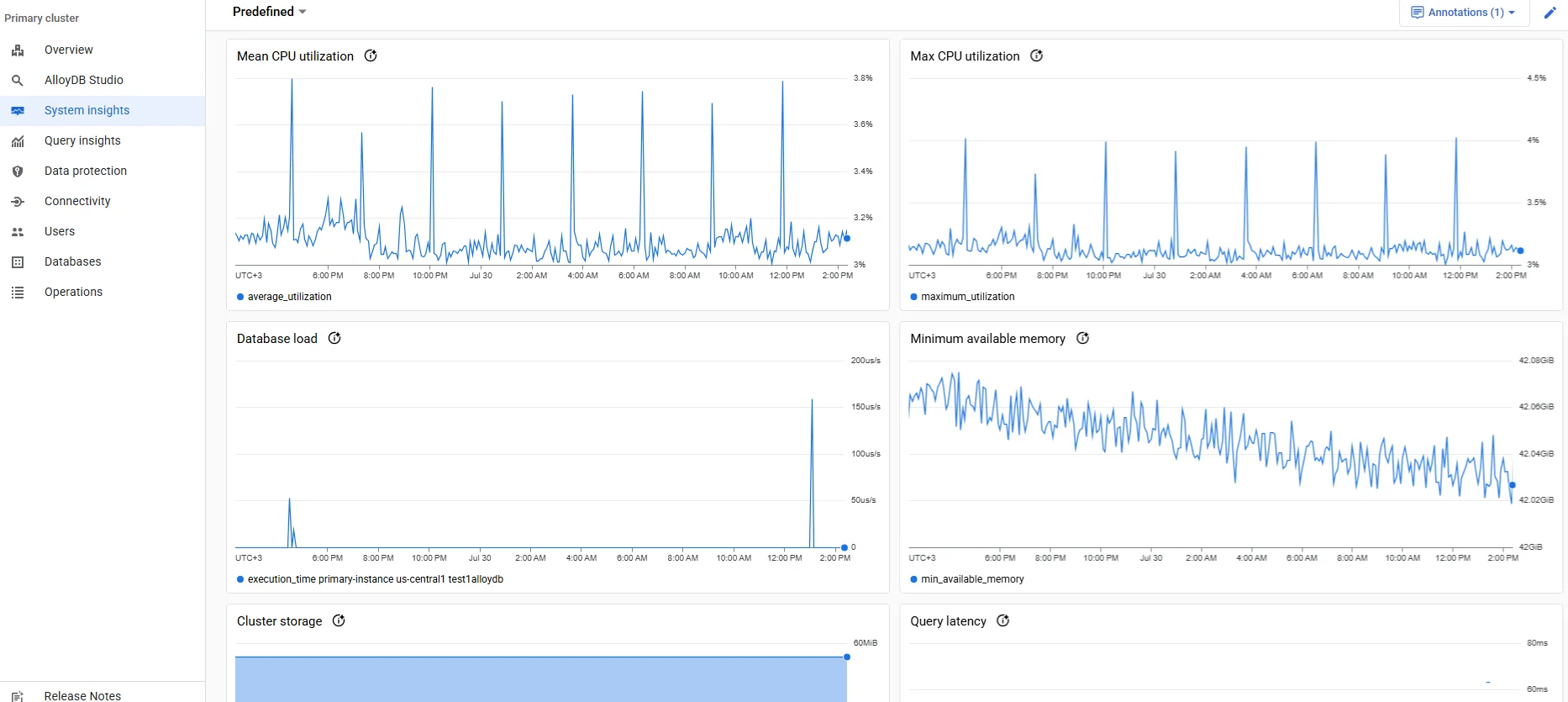
gcloud alloydb clusters update my-cluster \
--region=us-central1 \
--database-flags=alloydb.enable_pgaudit=on,pgaudit.log='all'
# then inside psql
CREATE EXTENSION pgaudit;
Fresh entries appear in Logs Explorer almost instantly, where they can be streamed to BigQuery, Pub/Sub, or your SIEM.
Native Audit in Google Cloud (Almost PostgreSQL)
Because AlloyDB inherits PostgreSQL’s catalog, the audit configuration is nearly identical to upstream. The official walkthrough, Enable pgAudit in AlloyDB, covers every flag. For a production‑grade posture you will also want to understand the Audit log schema reference, Route AlloyDB audit logs to BigQuery for long‑term analytics, and Monitor audit logs in Cloud Logging for real‑time alerting.
GenAI Meets DBA: Autonomous Threat Narratives
Reading thousands of JSON lines is nobody’s hobby. Generative AI can compress hours of parsing into a single paragraph. The PL/Python snippet below grabs the last 100 pgAudit records, sends them to Gemini via the Vertex AI SDK, then stores a human‑friendly summary back in AlloyDB:
CREATE OR REPLACE FUNCTION summarize_audit()
RETURNS void LANGUAGE plpython3u AS $$
from google.cloud import aiplatform, logging_v2
import datetime, plpy
rows = plpy.execute("SELECT payload FROM audit_log ORDER BY ts DESC LIMIT 100")
text = '\n'.join([r['payload'] for r in rows])
model = aiplatform.TextGenerationModel.from_pretrained('gemini-1.5-pro-preview')
pred = model.predict(text)
plpy.execute("INSERT INTO audit_summaries(ts, summary) VALUES (%s, %s)",
(datetime.datetime.utcnow(), pred.text))
$$;
For additional recipes—embeddings, vector search, and anomaly detection—see the Vertex AI generative‑AI cookbook.
Dynamic Masking & Data Discovery
Generative models love data; auditors insist on hiding it. DataSunrise demonstrates several run‑time patterns in its explainer on dynamic data masking. The masking engine relies on a catalogue populated by data discovery, tagging each column against GDPR and PCI‑DSS taxonomies so that sensitive literals never leave production.
Compliance Without the Spreadsheet
Standards like SOX and GDPR demand evidence that access is authorised and logged. DataSunrise’s Compliance Manager reconciles live activity with regulation‑specific baselines, as outlined in the note on data compliance regulations. Violations surface as alerts or can even trigger dynamic masking in‑flight.
Plug‑in Monitoring with DataSunrise
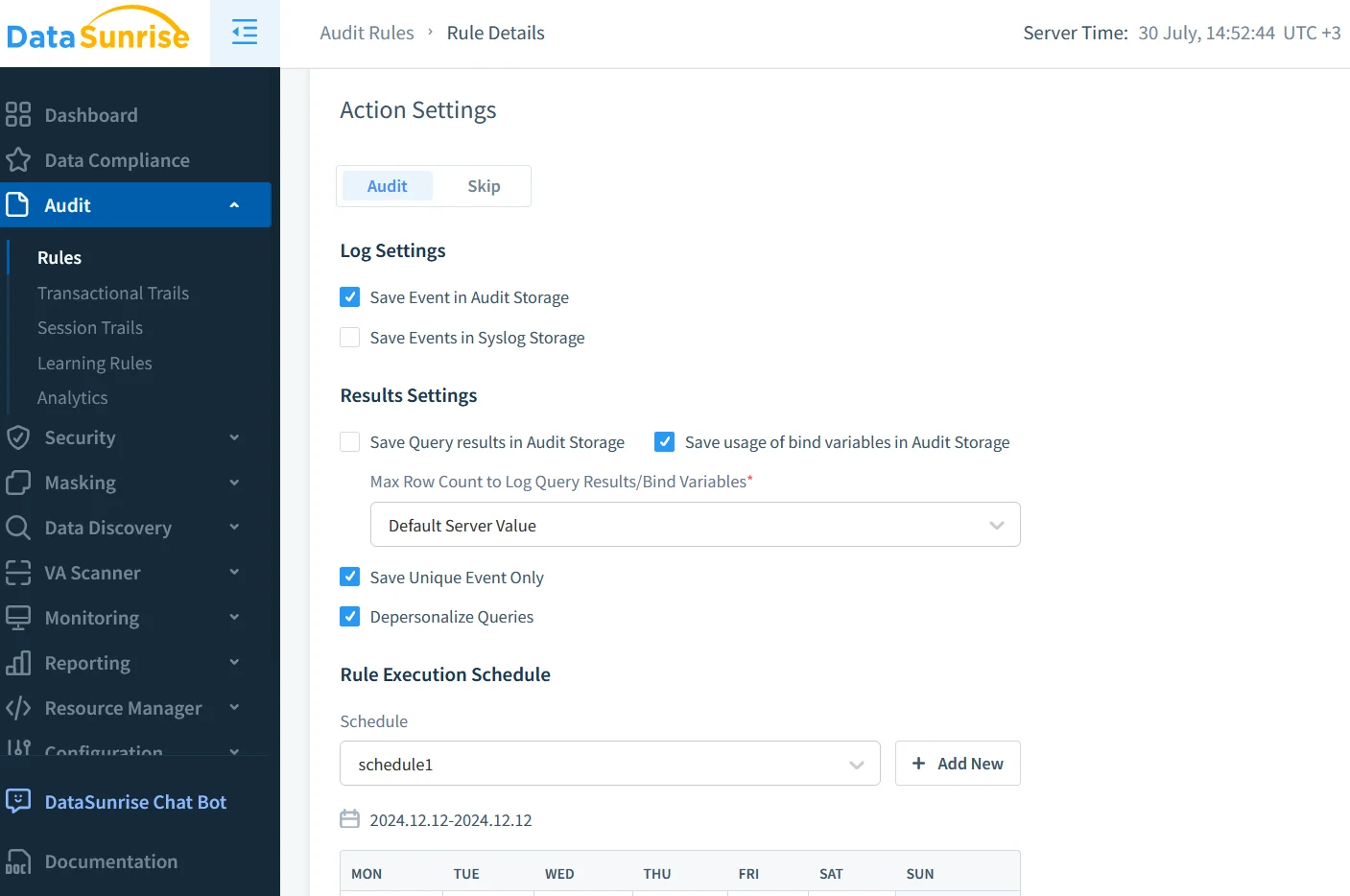
Native logs are necessary but not always sufficient. DataSunrise operates as a reverse proxy, writing its own Database Activity History and blocking malicious statements in real time. The wizard under Settings → Audit lets you declare rules (“log every DROP on schema public”) and choose storage—PostgreSQL, Kafka, or object storage. Details live in the audit guide.
Because DataSunrise speaks the PostgreSQL wire protocol, AlloyDB sessions simply point to the proxy address. Logs flow into the Data Activity History viewer—see database activity history—where GenAI summaries can be added via the integration described in LLM and ML tools for database security.
Security Beyond the Logs
Audit trails illuminate past behaviour, but proactive defence needs in‑line enforcement. DataSunrise’s policy engine ships with SQL‑injection detectors, role‑based access control, and streaming behavioural analytics.
Streaming Everything to BigQuery
Many teams glue the pieces together by creating a Log Router sink that forwards pgAudit entries to Pub/Sub and finally to BigQuery, partitioned on ts. A single view can join those rows with DataSunrise proxy logs, opening the door to federated queries such as:
SELECT s.summary, d.client_ip
FROM audit_summaries s
JOIN `proxy_logs.events` d
ON s.session_id = d.session_id
WHERE d.action = 'DROP TABLE'
AND s.ts > TIMESTAMP_SUB(CURRENT_TIMESTAMP(), INTERVAL 1 HOUR);
Materialise that view into Looker Studio and you have a live storyboard of hostile activity.
Cross‑Domain Intelligence with Security Command Center
Routing AlloyDB and DataSunrise logs into Google’s Security Command Center lets you correlate database events with IAM changes and network anomalies. A single dashboard can answer: Did the same IP that created a public firewall rule also exfiltrate salary data? Learn more in Investigating threats in Security Command Center.
Governance as Code
Modern compliance tooling prefers Git over spreadsheets. Terraform providers exist for both AlloyDB and DataSunrise, allowing you to encode audit configuration in pull requests. A single plan can pin the alloydb.enable_pgaudit flag and provision a DataSunrise rule, guaranteeing drift detection during CI.
Future Outlook
PostgreSQL 17 is set to ship native declarative audit syntax, which AlloyDB will adopt soon after. Meanwhile, Gemini is learning to emit SQL directly from natural‑language playbooks, meaning your incident binder may soon be a chat window. Staying ready means keeping the AlloyDB for PostgreSQL Database Activity History complete, trustworthy, and readable—delivered today by pgAudit, DataSunrise, and GenAI.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now