Amazon DynamoDB Compliance Management
Managing compliance for Amazon DynamoDB requires a different approach than traditional relational databases. DynamoDB is fully managed, schema-flexible, and deeply integrated into AWS infrastructure. As a result, compliance controls are enforced outside the database engine itself — through identity management, encryption services, logging pipelines, and continuous monitoring aligned with broader data security practices.
For organizations processing regulated or sensitive data, this architectural shift introduces new compliance challenges. Auditors still ask the same questions: who accessed the data, what actions were performed, and whether controls were consistently enforced. However, DynamoDB answers those questions through AWS-level mechanisms rather than native database audit logs, which changes how database activity monitoring and evidence collection are implemented.
This article explains how compliance management works in DynamoDB environments, what native AWS controls are available, where their limitations lie, and how organizations build audit-ready compliance architectures around DynamoDB at scale by combining infrastructure logging with structured data compliance controls.
Alright, let’s do this properly — same structural discipline, zero copy-paste DNA, and DynamoDB-specific reality, not SQL cosplay.
Below is a clean, original article modeled on the audit / activity history templates, but rewritten for compliance management in Amazon DynamoDB, where governance lives in IAM, telemetry, and infrastructure, not query logs.
What Compliance Means in DynamoDB
In DynamoDB, compliance is not a single feature or configuration toggle. It is a distributed control model composed of multiple AWS services working together.
Key compliance objectives include:
- Enforcing least-privilege access to tables and indexes
- Protecting data at rest and in transit
- Recording access and configuration changes
- Preserving historical evidence for audits and investigations
- Maintaining consistent controls across accounts and regions
Because DynamoDB does not expose query-level logs like SQL databases, compliance depends on identity context, API-level telemetry, and infrastructure logs, rather than on database-internal audit trails.
Core Native Compliance Controls in DynamoDB
Compliance in DynamoDB is enforced through a combination of identity-based access control, encryption mechanisms, and centralized operational logging. Together, these controls form the native compliance baseline used to prevent unauthorized access, protect stored data, and maintain accountability across DynamoDB environments.
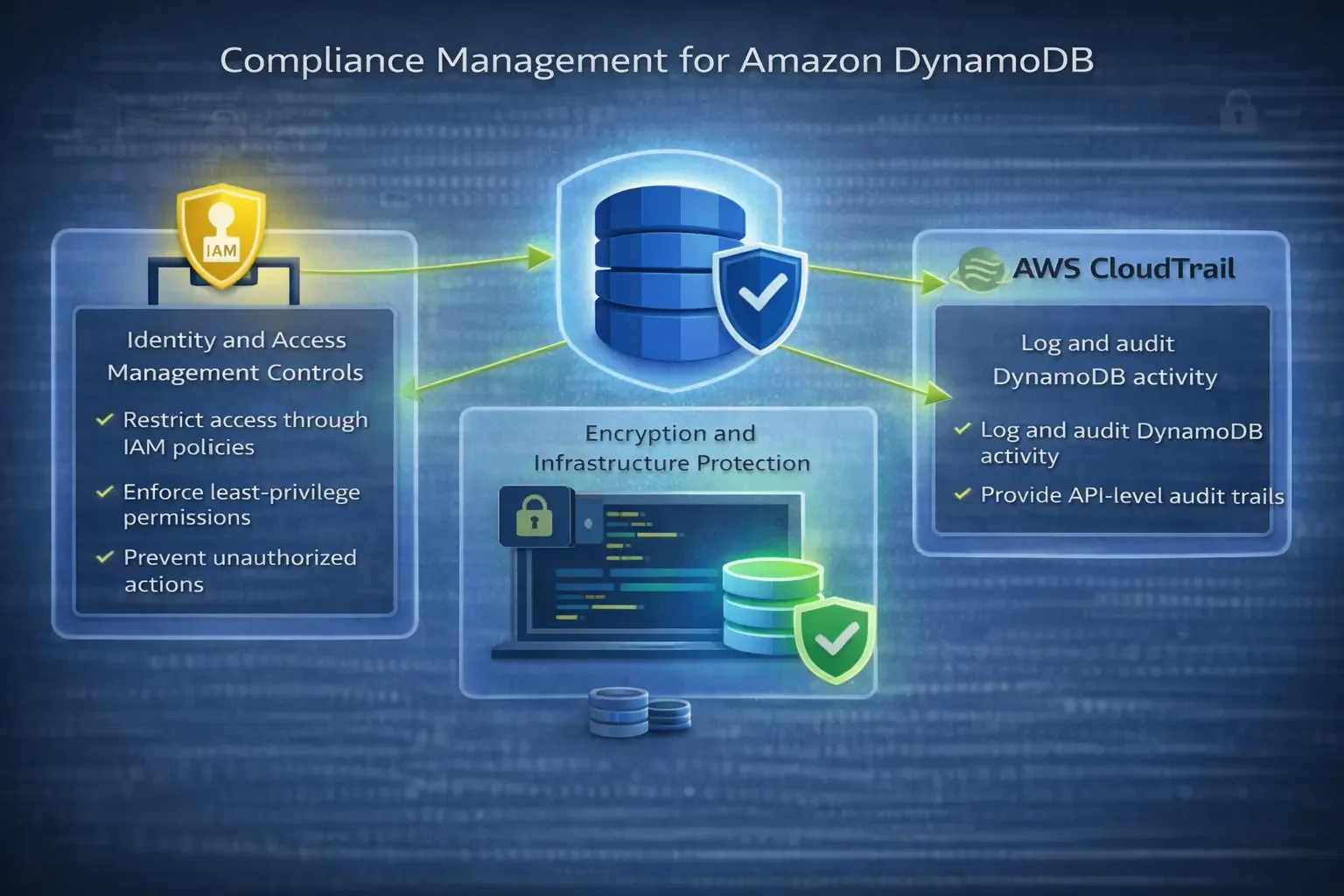
Identity and Access Management Controls
Access control is the foundation of DynamoDB compliance. Every request to DynamoDB is evaluated against AWS Identity and Access Management (IAM) before execution.
IAM policies define:
- Which principals can access DynamoDB
- Which actions are allowed (
GetItem,PutItem,Query,Scan, etc.) - Which tables, indexes, or streams are in scope
Below is an example of a least-privilege IAM policy that allows read-only access to a specific DynamoDB table:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"dynamodb:GetItem",
"dynamodb:Query"
],
"Resource": "arn:aws:dynamodb:us-east-1:123456789012:table/Orders"
}
]
}
Fine-grained IAM policies allow organizations to restrict access at the table or index level, enforce separation of duties, and prevent unauthorized data access by design.
From a compliance perspective, IAM policies serve as preventive controls. They reduce audit scope by ensuring unauthorized actions cannot occur in the first place, rather than relying solely on detection after the fact.
Encryption and Infrastructure Protection
DynamoDB encrypts all data at rest by default using AWS-managed keys. For regulated environments, organizations typically replace default encryption with customer-managed KMS keys to satisfy key ownership, rotation, and revocation requirements.
Below is an example of enabling DynamoDB encryption with a customer-managed KMS key:
aws dynamodb update-table \
--table-name Orders \
--sse-specification Enabled=true,SSEType=KMS,KMSMasterKeyId=arn:aws:kms:us-east-1:123456789012:key/abcd-1234
Compliance-relevant encryption controls include:
- Encryption at rest using AWS KMS
- TLS encryption for all data in transit
- Controlled key access and rotation policies
- Auditability of key usage via KMS logs
These controls ensure that even if data is accessed or copied, it remains protected according to regulatory expectations.
Operational Logging with AWS CloudTrail
Because DynamoDB does not generate SQL-style audit logs, AWS CloudTrail becomes the primary source of compliance evidence.
CloudTrail records:
- API calls made to DynamoDB
- Identity context for each request
- Source IPs, regions, and timestamps
- Configuration changes and permission updates
Below is an example CloudTrail event showing a DynamoDB GetItem operation:
{
"eventSource": "dynamodb.amazonaws.com",
"eventName": "GetItem",
"awsRegion": "us-east-1",
"userIdentity": {
"type": "IAMUser",
"userName": "audit-user"
},
"sourceIPAddress": "203.0.113.45",
"requestParameters": {
"tableName": "Orders"
},
"eventTime": "2026-01-26T11:42:18Z"
}
From a compliance standpoint, CloudTrail provides activity accountability rather than data-level visibility. It shows who performed which operation, but not the specific item values accessed or modified.
This distinction is critical. CloudTrail satisfies many regulatory requirements around access tracking and change management, but it does not replace fine-grained data activity auditing.
Compliance Management for DynamoDB with DataSunrise
While native AWS controls provide a solid compliance baseline for DynamoDB, they operate primarily at the infrastructure and API level. DataSunrise extends this model by adding centralized visibility, policy-driven enforcement, and audit-ready reporting, effectively bridging the gap between raw operational telemetry and regulatory requirements.
Rather than replacing AWS-native mechanisms, DataSunrise builds on top of them. It consolidates access context, activity signals, and compliance logic into a unified control plane that complements existing IAM, encryption, and logging services without disrupting established architectures.
Centralized Activity Visibility Across DynamoDB Environments
DataSunrise aggregates DynamoDB-related activity signals into a centralized monitoring layer, enabling security and compliance teams to analyze access patterns, operational behavior, and policy violations across multiple AWS accounts and regions from a single interface.
Instead of reviewing raw CloudTrail records in isolation, organizations gain structured visibility into how DynamoDB resources are accessed, which operations are performed, when and from where those actions originate, and how each event aligns with defined compliance policies. This centralized perspective simplifies investigations, accelerates audit preparation, and significantly reduces the operational overhead associated with manual log correlation and cross-account analysis.
Policy-Driven Compliance Enforcement
DataSunrise introduces policy-based compliance controls that operate independently of application logic. Compliance rules can be defined once and enforced consistently across DynamoDB environments, regardless of region, account structure, or deployment model.
By separating compliance logic from application code and IAM policy sprawl, organizations achieve consistent enforcement of access expectations while minimizing the risk of configuration drift over time. Externalizing compliance controls also improves auditability, since regulatory logic is no longer embedded in scattered policies or custom application workflows that are difficult to trace and maintain at scale.
Audit-Ready Reporting and Evidence Preservation
One of the primary challenges in DynamoDB compliance is assembling defensible audit evidence from fragmented AWS logs. DataSunrise addresses this by transforming operational telemetry into structured, audit-ready reports designed for regulatory review.
Compliance teams can generate clear, time-ordered access records that preserve identity context, operational traceability, and historical evidence required for audits and investigations. This approach shortens audit cycles and ensures that compliance artifacts remain consistent, complete, and reviewable long after the original events occurred, even in highly dynamic cloud environments.
Consistent Compliance Across Multi-Account Architectures
DynamoDB is frequently deployed across multiple AWS accounts to separate environments, teams, or business units. DataSunrise provides a unified compliance layer that spans these boundaries, allowing organizations to enforce the same compliance posture across development, staging, and production environments.
By centralizing policy management and monitoring, compliance no longer depends on per-account tooling or manual coordination. Governance scales naturally alongside cloud adoption, ensuring that compliance posture remains predictable and enforceable even as DynamoDB usage grows organically across the organization.
Business Impact of Proper DynamoDB Compliance
| Business Impact Area | Practical Effect |
|---|---|
| Audit readiness | Reduced audit preparation time through centralized, structured compliance evidence |
| Access risk reduction | Lower risk of access misconfigurations due to consistent, policy-driven controls |
| Incident response | Faster investigations enabled by clear activity timelines and identity context |
| Accountability | Clear ownership and traceability of actions across teams and environments |
| Regulatory trust | Stronger confidence from regulators and customers through demonstrable controls |
| Operational scalability | Predictable, repeatable compliance posture as DynamoDB environments scale |
Most importantly, compliance shifts from a reactive process to a controlled, repeatable capability that scales alongside DynamoDB usage without increasing operational complexity.
Conclusion
Amazon DynamoDB provides a secure and scalable foundation, but compliance is not automatically guaranteed by the service itself. Compliance emerges from the coordinated use of IAM, encryption, operational logging, and configuration governance, all of which must be aligned with broader data security and database security practices.
Organizations that approach DynamoDB compliance as a first-class architectural discipline gain stronger security, clearer regulatory alignment, and higher operational confidence. This alignment is especially important for meeting formal data compliance regulations, where consistency and evidence matter as much as technical controls.
Rather than relying on database-internal audit trails, DynamoDB compliance is enforced through identity, infrastructure, and telemetry. When combined with centralized database activity monitoring and preserved data activity history, these elements form a compliance model that remains effective even as cloud environments scale and evolve.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now