Amazon DynamoDB Data Governance
Amazon DynamoDB is widely adopted for high-scale, low-latency applications, but its managed nature often leads teams to underestimate governance requirements. While DynamoDB removes infrastructure management, it does not remove responsibility for how data is accessed, protected, classified, and retained. In practice, this places DynamoDB squarely within broader data management and data security programs rather than treating it as a purely operational service.
Amazon DynamoDB data governance focuses on defining clear rules for data ownership, access boundaries, usage accountability, and compliance enforcement across distributed and cloud-native architectures. These governance controls are closely tied to access controls, continuous database activity monitoring, and alignment with formal data compliance regulations. Without governance controls, organizations risk uncontrolled access growth, compliance blind spots, and operational inconsistency across environments.
Importance of Data Governance for Amazon DynamoDB
Data governance plays a critical role in how Amazon DynamoDB is used at scale. As DynamoDB tables become shared resources for multiple applications, teams, and automation workflows, the absence of governance quickly turns a high-performance datastore into a compliance and security liability. In this context, governance becomes an essential part of broader data management rather than an optional control layer.
Unlike traditional databases, DynamoDB does not enforce rigid schemas or usage boundaries. This flexibility accelerates development, but it also removes natural control points. Without explicit governance, access permissions tend to expand over time, data usage patterns become opaque, and accountability is lost across services and environments. These gaps directly affect overall data security and make it difficult to enforce consistent access controls.
Strong data governance establishes clear ownership and responsibility for how DynamoDB data is accessed and consumed. It ensures that access decisions are intentional, traceable, and aligned with business purpose rather than convenience or legacy configuration. Governance also provides the foundation for effective database activity monitoring, allowing organizations to detect misuse and policy violations early.
Most importantly, data governance enables organizations to scale DynamoDB usage without scaling risk. By separating governance controls from application logic, teams avoid tight coupling, reduce operational fragility, and maintain predictable security and compliance behavior as architectures evolve. This approach is essential for meeting modern data compliance regulations across cloud-native environments.
Native DynamoDB Capabilities Relevant to Governance
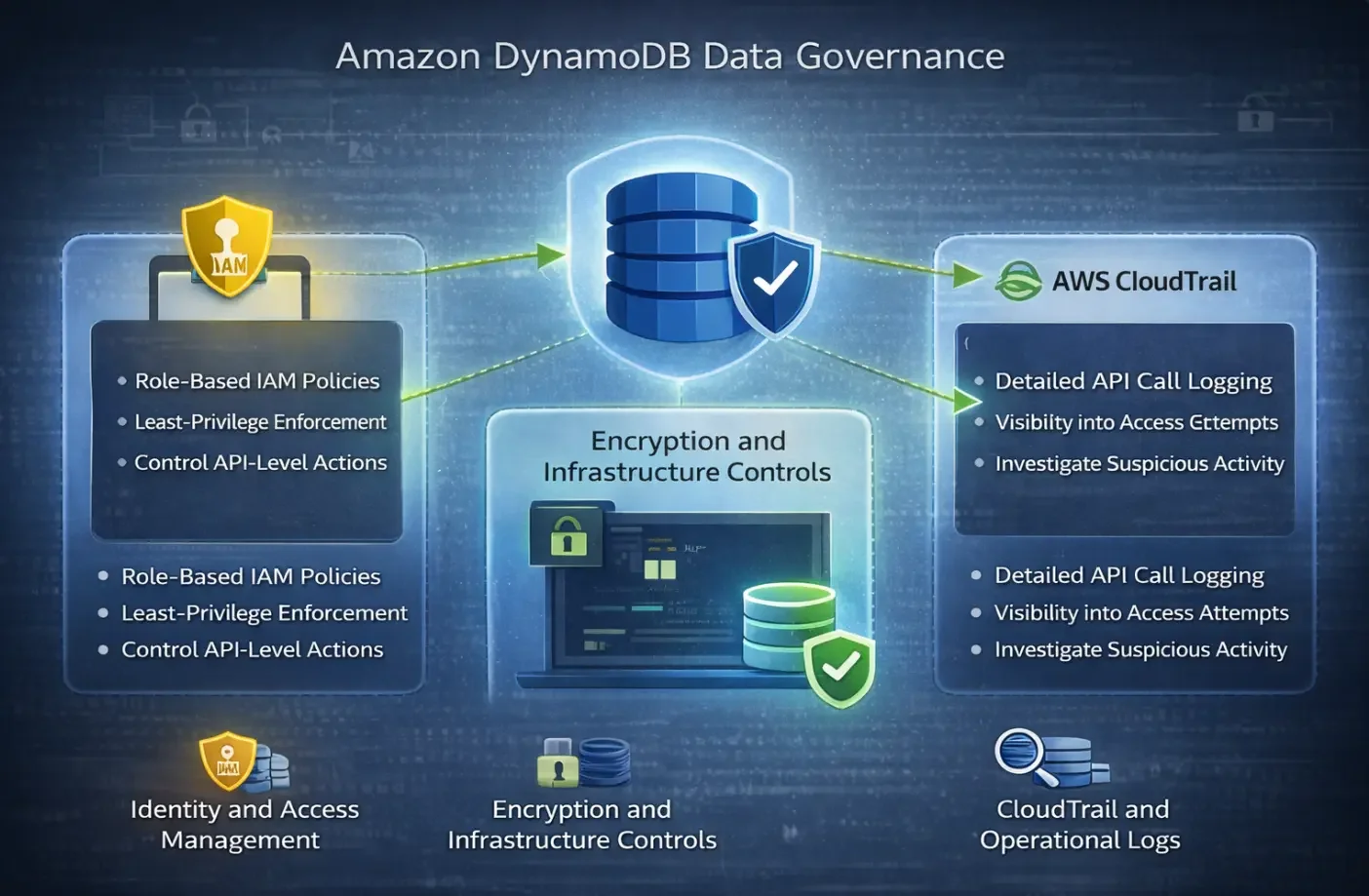
AWS provides several foundational mechanisms that contribute to DynamoDB governance. These capabilities are designed primarily for infrastructure security and access enforcement, and they establish an essential baseline for operating DynamoDB in regulated environments. However, they are not designed to function as a complete data governance framework.
Native DynamoDB controls focus on who can access the service and how requests are authorized at the API level. They do not address how data is consumed after authorization, how access aligns with business purpose, or whether usage patterns remain compliant over time. As DynamoDB deployments grow and become more distributed, these gaps become increasingly visible.
Identity and Access Management
DynamoDB relies on AWS IAM for access control. IAM policies define which principals can perform actions such as GetItem, PutItem, or Scan on specific tables or indexes. These policies are evaluated before a request reaches the DynamoDB service, making IAM the primary gatekeeper for DynamoDB access.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"dynamodb:GetItem",
"dynamodb:Query"
],
"Resource": "arn:aws:dynamodb:us-east-1:123456789012:table/Orders"
}
]
}
IAM is highly effective for enforcing least-privilege permissions at the API level. It allows organizations to restrict actions by role, service, account, or condition.
{
"Effect": "Allow",
"Action": "dynamodb:*",
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:PrincipalTag/environment": "production"
}
}
}
However, IAM operates without awareness of data sensitivity, attribute-level context, or intended usage. Once access is granted, IAM does not track how data is used or whether access patterns remain appropriate over time.
As a result, IAM enforces authorization but does not provide governance insight. It answers whether an action is allowed, not whether it should be allowed in a broader compliance or governance context.
Encryption and Infrastructure Controls
DynamoDB encrypts data at rest by default and supports customer-managed AWS KMS keys for additional control. Network-level isolation can be enforced through VPC endpoints, preventing public internet exposure and limiting access to trusted network boundaries.
{
"SSESpecification": {
"Enabled": true,
"SSEType": "KMS",
"KMSMasterKeyId": "arn:aws:kms:us-east-1:123456789012:key/abcd-1234"
}
}
VPC endpoint policies can further restrict how DynamoDB is accessed from within private networks.
{
"Statement": [
{
"Effect": "Allow",
"Principal": "*",
"Action": "dynamodb:*",
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:SourceVpc": "vpc-0a1b2c3d4e"
}
}
}
]
}
These controls are essential for protecting data confidentiality and integrity at the infrastructure level. They reduce the risk of interception, unauthorized storage access, and key misuse. However, encryption and network isolation are passive protections. They do not influence how authorized users interact with data once access is established.
From a governance perspective, these controls do not prevent over-privileged access, misuse of sensitive attributes, or violations of data usage policies. They secure the environment, but they do not govern behavior.
CloudTrail and Operational Logs
AWS CloudTrail records DynamoDB API calls, including both control-plane and data-plane operations. These logs capture information such as the calling identity, timestamp, API action, and request parameters. CloudTrail is commonly used for security investigations and infrastructure-level audits.
{
"eventSource": "dynamodb.amazonaws.com",
"eventName": "GetItem",
"awsRegion": "us-east-1",
"userIdentity": {
"type": "AssumedRole",
"arn": "arn:aws:sts::123456789012:assumed-role/app-role/session"
},
"requestParameters": {
"tableName": "Orders"
}
}
While CloudTrail provides valuable operational visibility, it is not designed to support data governance decisions. The logs do not include semantic context about the data being accessed, whether attributes contain sensitive information, or whether the access aligns with regulatory requirements or internal policies.
As a result, CloudTrail alone cannot function as a governance mechanism. It produces raw telemetry that must be heavily processed, correlated, and interpreted externally. Governance requires contextual evaluation and policy enforcement, not just event collection.
Policy-Driven Data Governance for DynamoDB
Effective DynamoDB data governance requires policy-driven controls that operate independently of application code and infrastructure configuration. In cloud-native architectures, governance logic embedded in applications quickly becomes fragmented, difficult to audit, and nearly impossible to scale consistently across teams and environments.
Policy-driven governance externalizes control logic into centralized rules that are enforced uniformly, regardless of how or where data is accessed. This approach ensures that governance decisions remain stable even as applications evolve, services are refactored, or access patterns change.
Policy-driven governance introduces centralized rules that define:
- Which identities may access sensitive attributes
- Under what conditions access is allowed
- How violations are detected and recorded
- What evidence is preserved for audits
Unlike static permission models, governance policies evaluate access in context. They consider not only who is making a request, but also what data is involved, how it is being accessed, and whether the action aligns with defined compliance and security requirements.
These policies follow the data itself, not the deployment topology. Whether DynamoDB tables are accessed from Lambda functions, ECS services, CI/CD pipelines, or external analytics tools, governance rules remain consistent. This eliminates policy drift and prevents environments from diverging in their security and compliance posture.
Extending DynamoDB Data Governance with DataSunrise
Native AWS controls establish a necessary security baseline, but they do not provide centralized data governance. They focus on authorization and infrastructure protection rather than continuous oversight of data usage. DataSunrise extends DynamoDB governance by introducing independent control layers for visibility, policy enforcement, and compliance accountability.
By operating outside application logic and AWS service boundaries, DataSunrise provides governance controls that remain consistent even as DynamoDB usage scales across accounts, regions, and environments.
Centralized Governance Control
DataSunrise provides a unified governance layer that applies consistent policies across DynamoDB tables and other data platforms. Governance rules are defined once and enforced uniformly, eliminating configuration drift between development, testing, analytics, and production environments.
Centralized control allows security and compliance teams to manage governance independently of development cycles. Policy updates do not require application redeployment or infrastructure changes, reducing operational friction while improving governance reliability.
Sensitive Data Discovery and Classification
Governance begins with knowing what data exists and where it resides. DataSunrise performs automated discovery and classification of sensitive data within DynamoDB attributes, identifying regulated information such as personal identifiers, financial data, and credentials.
This classification enables governance policies to be based on actual data content rather than table names, documentation, or assumptions. As data structures evolve, discovery processes continuously update classifications, ensuring governance rules remain accurate over time.
Governance-Aware Activity Monitoring
Instead of relying on raw operational logs, DataSunrise records governance-aware activity histories. Each access event is evaluated against governance policies in real time, allowing teams to distinguish between legitimate business usage and policy violations.
This approach transforms activity monitoring from passive logging into active governance enforcement. Suspicious access patterns, excessive data exposure, or unauthorized attribute access can be detected and recorded immediately.
Compliance Alignment and Evidence Collection
Data governance is inseparable from regulatory compliance. DataSunrise aligns DynamoDB access activity with frameworks such as GDPR, HIPAA, PCI DSS, and SOX by maintaining structured, queryable governance records.
These records provide clear, defensible evidence of how data is accessed and protected. Instead of reconstructing compliance narratives from fragmented logs, organizations can demonstrate continuous compliance through centralized governance reporting that auditors can rely on.
Operational Benefits of Strong DynamoDB Data Governance
| Operational Area | Governance Benefit |
|---|---|
| Data Security | Reduced risk of unauthorized data exposure through controlled and policy-driven access |
| Accountability | Clear ownership and traceability for who accesses data and for what purpose |
| Environment Consistency | Consistent enforcement of governance rules across development, testing, and production |
| Compliance Readiness | Faster compliance audits supported by structured, defensible evidence |
By treating DynamoDB as a governed data asset rather than a simple key-value store, organizations gain long-term operational stability and regulatory confidence.
Conclusion
Amazon DynamoDB offers scalability and performance, but governance does not come automatically with managed infrastructure. Native AWS controls address access and encryption, yet they leave critical governance gaps related to data usage, accountability, and compliance. These gaps become especially visible as DynamoDB is adopted as part of broader data management strategies across cloud-native environments.
A structured governance approach—built on policy-driven enforcement, sensitive data awareness, and centralized oversight—transforms DynamoDB from an operational datastore into a compliant, auditable, and well-governed data platform. This approach aligns governance with modern data security requirements and ensures consistent control beyond basic access controls.
DataSunrise enables this transformation by providing governance controls that operate independently of application logic and AWS infrastructure boundaries. By combining centralized policy management with continuous monitoring and reporting, organizations can maintain a predictable compliance posture and meet evolving data compliance regulations as DynamoDB architectures scale.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now