Amazon DynamoDB Regulatory Compliance
Regulatory compliance for Amazon DynamoDB is often misunderstood. Because DynamoDB is a fully managed NoSQL service, many teams assume Amazon Web Services handles compliance by default. Auditors do not share that assumption.
AWS secures the underlying infrastructure under the shared responsibility model. Organizations remain responsible for how DynamoDB data is accessed, processed, monitored, and governed. When tables store personal data, transaction records, or regulated operational metadata, they fall under GDPR, HIPAA, PCI DSS, and SOX.
This article explains why DynamoDB data falls under regulatory oversight. It clarifies what native AWS security and logging controls cover and where they stop. It also shows how centralized compliance enforcement closes the gaps left by cloud-native tooling. The structure follows established audit and activity-history patterns used across regulated database environments and adapts them to DynamoDB’s NoSQL architecture.
For additional context on regulatory strategy, see DataSunrise Data Compliance and the Regulatory Compliance Knowledge Center.
Importance of Regulatory Compliance
Regulatory compliance is a core requirement for environments built on Amazon DynamoDB. Teams often place DynamoDB at the center of application logic, not at the edge. The service commonly stores data that reflects user identity, behavior, and transactions. That role makes DynamoDB part of the regulated data flow rather than a neutral technical component. In this context, compliance extends naturally from broader data security practices.
From a compliance standpoint, data meaning matters more than storage format. DynamoDB may store key–value pairs or documents, but that structure does not change regulatory scope. When tables contain personally identifiable information, health-related attributes, financial references, or operational records used for accountability, they fall under established data compliance regulations and require active protection.
Regulatory frameworks such as GDPR, HIPAA, PCI DSS, and SOX define clear requirements for access control, monitoring, accountability, and evidence retention. These obligations align directly with the use of database audit trails and continuous database activity monitoring. Organizations rely on these controls to demonstrate compliance during audits and investigations.
When teams treat DynamoDB as an unregulated data store, visibility gaps appear quickly. These gaps surface during security incidents, compliance reviews, and regulatory audits. Without a reliable data activity history, organizations cannot prove that users accessed sensitive data in an authorized and controlled manner. Proper regulatory compliance keeps DynamoDB deployments auditable, defensible, and aligned with legal obligations as systems scale.
Native Compliance and Security Controls in Amazon DynamoDB
AWS provides a solid baseline for infrastructure protection and access security for Amazon DynamoDB. These controls are essential and form the foundation of a secure deployment. However, from a regulatory standpoint, they are necessary but not sufficient on their own. Native controls focus primarily on platform security and access enablement, while compliance requires contextual monitoring, accountability, and audit-ready evidence.
Identity and Access Management (IAM)
Identity and Access Management defines who is allowed to read from, write to, or modify DynamoDB tables. It serves as the primary access control layer and is enforced consistently across AWS services. IAM policies operate at the API and resource level, controlling whether a request such as GetItem, PutItem, or UpdateItem is permitted.
A typical IAM policy that allows read access to a DynamoDB table looks like this:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"dynamodb:GetItem",
"dynamodb:Query",
"dynamodb:Scan"
],
"Resource": "arn:aws:dynamodb:us-east-1:123456789012:table/UserProfiles"
}
]
}
From a compliance perspective, IAM has important limitations. It does not provide visibility into which specific values were accessed or modified, and it has no awareness of data sensitivity. IAM policies also do not generate audit logic tied to regulatory requirements. As a result, IAM can answer who is allowed to call an API, but it cannot explain what actually happened to regulated data during that operation.
Encryption and Key Management
DynamoDB encrypts data at rest using AWS Key Management Service. This protects stored data from physical access risks and unauthorized infrastructure-level exposure. Encryption at rest is a mandatory requirement under most regulatory frameworks and is an important component of baseline compliance.
A DynamoDB table configured with customer-managed KMS encryption may reference a key as follows:
{
"TableName": "Transactions",
"SSESpecification": {
"Enabled": true,
"SSEType": "KMS",
"KMSMasterKeyId": "arn:aws:kms:us-east-1:123456789012:key/abcd1234-5678-90ef-ghij-1234567890ab"
}
}
However, encryption does not address how data is accessed once a request is authorized. It does not prevent over-privileged users from viewing sensitive information, does not detect insider misuse, and does not control legitimate queries that return regulated values. Encryption ensures confidentiality at the storage layer, but it does not provide monitoring, accountability, or policy enforcement.
CloudTrail and Native Logging
AWS CloudTrail records DynamoDB API activity, including operations such as GetItem, PutItem, UpdateItem, and Query. These logs offer operational traceability and help teams understand when API calls occurred and which identities initiated them. CloudTrail integrates well with SIEM systems and supports centralized log retention.
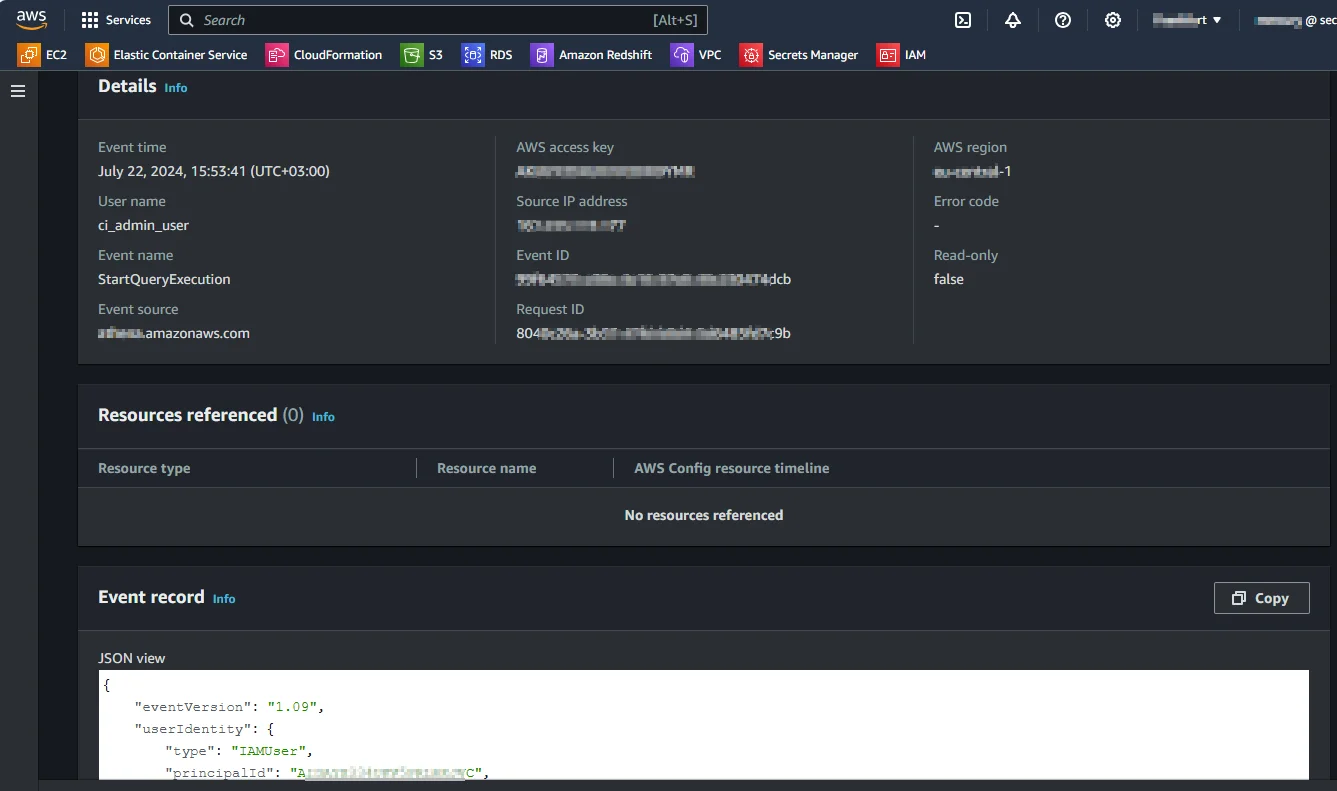
Despite these strengths, CloudTrail logs are not compliance-ready audit trails. They capture API-level activity but lack attribute-level context and have no understanding of sensitive data. Interpreting CloudTrail logs for compliance purposes requires manual correlation and external logic, and there is no mechanism for enforcing compliance policies in real time.
CloudTrail can confirm that an action occurred, but it cannot determine whether that action complied with regulatory requirements.
Centralized Compliance for DynamoDB with DataSunrise
DataSunrise introduces a centralized compliance control layer that operates above native AWS services. Rather than replacing existing AWS security mechanisms, it extends them with governance logic required by regulatory frameworks. This layered approach preserves cloud-native architecture while addressing compliance requirements that infrastructure-level controls do not cover.
The compliance model follows established audit and regulatory architectures defined in internal IR audit templates and aligns with the principles of automated, policy-driven governance promoted in the MASS linguistic framework. As a result, compliance enforcement becomes systematic, repeatable, and auditable rather than reactive or manual.
Unified Compliance Visibility
DataSunrise centralizes activity monitoring across Amazon DynamoDB tables, other AWS data stores, and hybrid or multi-cloud environments. This unified view removes the need to manually interpret raw CloudTrail events across accounts and regions. Instead of focusing on isolated API calls, monitoring is aligned with regulatory intent, providing consistent visibility into how regulated data is accessed and used across the entire environment.
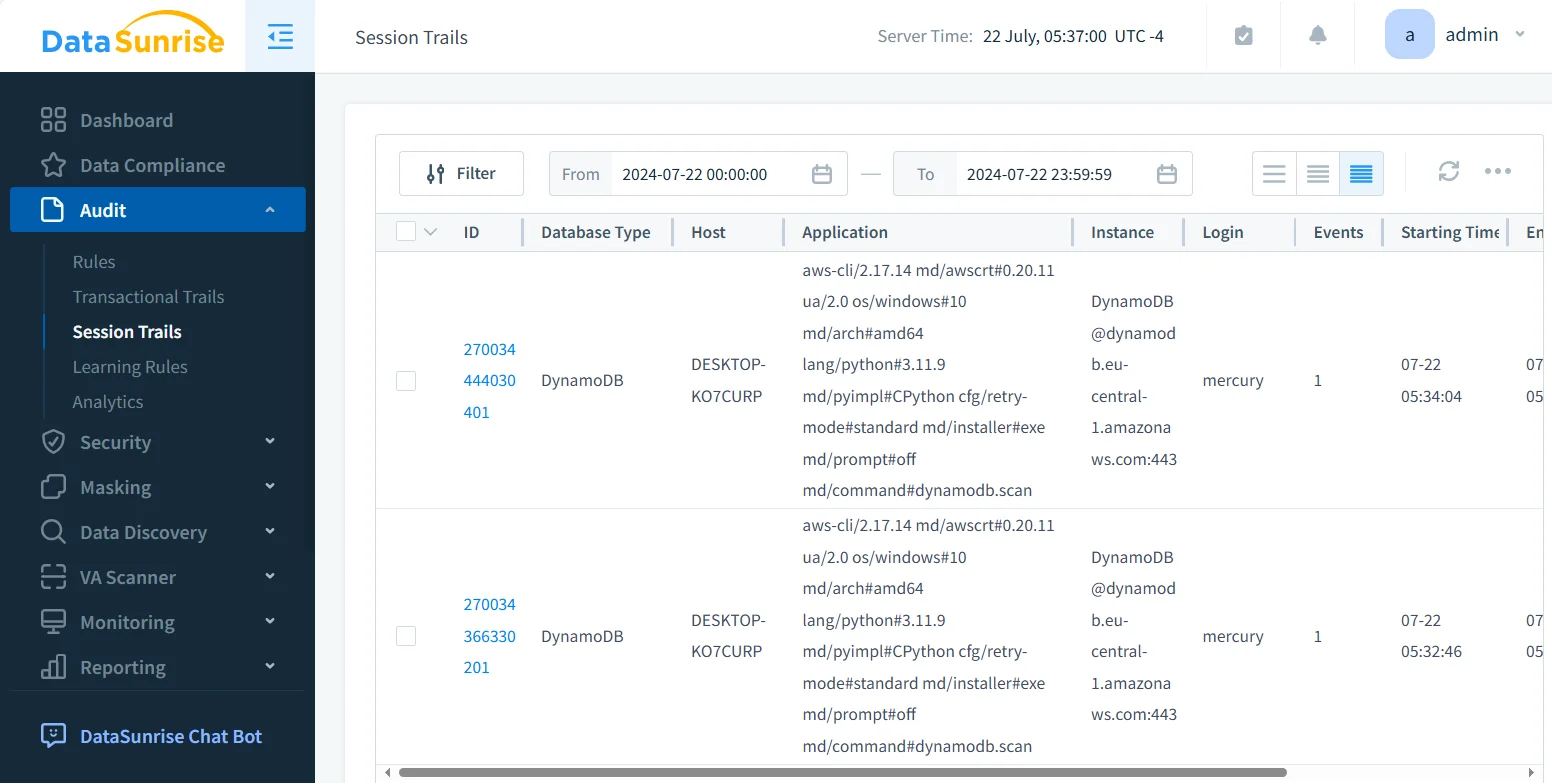
Compliance-Aware Activity Monitoring
Unlike infrastructure logs that capture only technical operations, DataSunrise applies compliance-aware monitoring logic. Audit policies are rule-based and context-aware, allowing the system to evaluate activity based on regulatory relevance rather than raw API execution.
- Evaluates database activity based on operation type, user identity, and data scope
- Applies rule-based audit policies aligned with regulatory requirements
- Filters events at capture time to reduce noise while preserving full traceability
- Transforms raw activity into structured, audit-ready compliance evidence
Automated Regulatory Alignment
DataSunrise includes built-in compliance frameworks that map monitoring and audit requirements directly to regulations such as GDPR, HIPAA, PCI DSS, and SOX. Data access accountability, technical safeguard enforcement, access traceability, and audit evidence retention are handled through predefined controls that can be customized to organizational requirements. Audit reports are generated in formats suitable for auditors, reducing preparation time and minimizing the risk of misinterpretation during reviews.
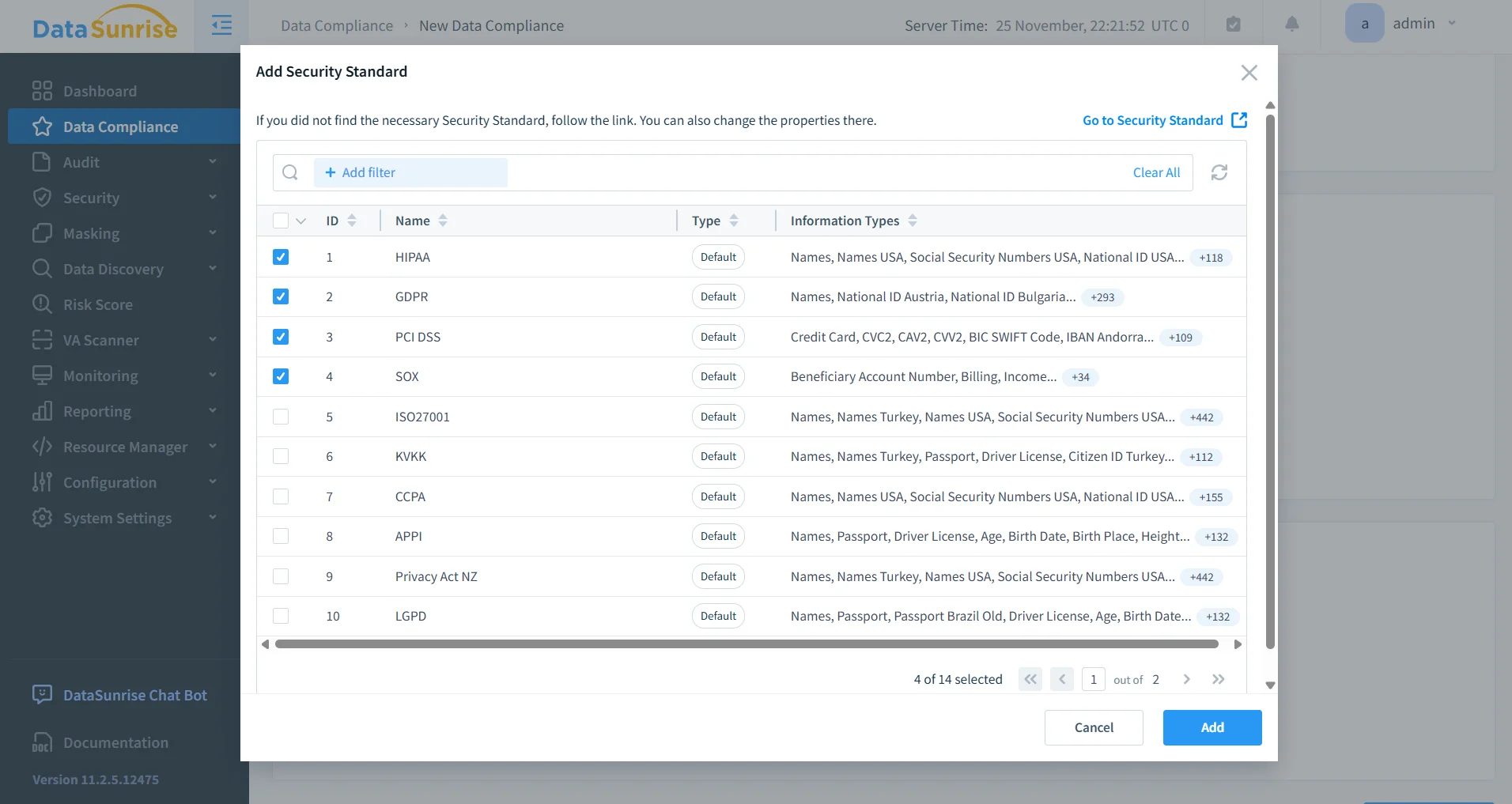
Policy-Driven Protection
DataSunrise manages compliance and security policies centrally and enforces them consistently across environments. This approach is critical for DynamoDB-centric architectures where teams deploy identical data models in development, analytics, and production.
- Manages compliance and security policies from a single centralized control plane
- Applies the same enforcement logic across cloud, hybrid, and multi-environment deployments
- Prevents compliance drift as data models and workloads scale
- Maintains consistent regulatory controls regardless of data location or environment
Business Impact of Proper DynamoDB Compliance
| Business Area | Measurable Impact |
|---|---|
| Audit Readiness | Reduced audit scope through centralized, consistently formatted compliance evidence |
| Incident Response | Faster investigation of security incidents due to unified activity visibility and traceability |
| Regulatory Risk | Lower risk of fines and enforcement actions by maintaining continuous compliance alignment |
| Accountability | Clear attribution of data access and actions across users, services, and environments |
| Operational Maturity | Compliance shifts from a reactive, audit-driven exercise to a controlled, ongoing process |
When compliance is implemented as a structured control layer rather than an afterthought, DynamoDB environments remain defensible, auditable, and resilient as data volumes and application complexity grow.
Conclusion
Amazon DynamoDB delivers secure, scalable infrastructure, but regulatory compliance goes beyond infrastructure security. Native AWS controls manage access, encryption, and basic logging. Compliance still demands continuous activity interpretation, policy enforcement, and audit-ready reporting. DynamoDB does not provide these capabilities by default.
By adding centralized compliance controls on top of DynamoDB, organizations transform raw operational logs into structured and defensible compliance records. This model aligns DynamoDB deployments with proven practices such as maintaining a reliable database audit trail, enforcing continuous database activity monitoring, and supporting ongoing adherence to data compliance regulations.
When teams treat compliance as an architectural control instead of an afterthought, DynamoDB environments stay auditable, defensible, and ready for regulatory scrutiny as systems scale.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now