
Amazon RDS Audit Log

Modern applications that use Generative AI (GenAI) demand a new level of database visibility. The stakes are higher: unauthorized model access, prompt injection, shadow data copies, and exfiltration via inference. To maintain trust and compliance, monitoring Amazon RDS through a robust Amazon RDS Audit Log strategy becomes not just useful but essential.
This article explores how to set up native auditing in RDS, enhance visibility using DataSunrise, and apply these tools to secure GenAI workloads. It also covers real-time monitoring, dynamic masking, and sensitive data discovery, with practical examples and links to deeper resources.
Why GenAI Needs Database Audit Logs
As GenAI models increasingly rely on structured data for vector search, prompt enrichment, or fine-tuning, the database becomes a gateway to high-value content. Imagine a chatbot querying customer support histories stored in RDS:
SELECT message FROM support_logs WHERE user_id = 'u123' ORDER BY timestamp DESC LIMIT 10;
A poorly secured setup might leak PII, sentiment labels, or internal classification tags through GenAI responses. Audit logs help track who accessed what, when, and how. They also make it possible to correlate database access patterns with LLM-layer telemetry, supporting anomaly detection and improving GenAI observability. This capability is critical for building secure and reliable pipelines.
Native Amazon RDS Audit Log Configuration
Amazon RDS supports native audit logging for engines like MySQL and PostgreSQL. For PostgreSQL, pgAudit allows you to track DML, DDL, and session activity. Enabling it requires adjusting the parameter group settings:
ALTER SYSTEM SET pgaudit.log = 'all';
ALTER SYSTEM SET log_statement = 'all';
SELECT pg_reload_conf();
Audit logs can be streamed to CloudWatch or stored in S3, depending on your configuration. You can learn more from the official pgAudit documentation and AWS's PostgreSQL logging guide.
In MySQL, the general log can be enabled with a simple command:
CALL mysql.rds_enable_general_log();
You can then query the contents of mysql.general_log to inspect commands issued by applications or users. However, this log can grow rapidly, so retention and storage need careful consideration. More details are available in the RDS log access guide. Additional insight on monitoring Amazon RDS logs is provided in the AWS blog on Monitoring Aurora audit events with CloudWatch.
Extending Visibility with DataSunrise
While native logging offers a basic layer of traceability, DataSunrise expands it with intelligent audit policies, real-time behavior analytics, and dynamic masking features. It operates through a reverse proxy to inspect SQL traffic and allows granular rule-based auditing. You can log activity tied to user roles, specific tables, or even query content.
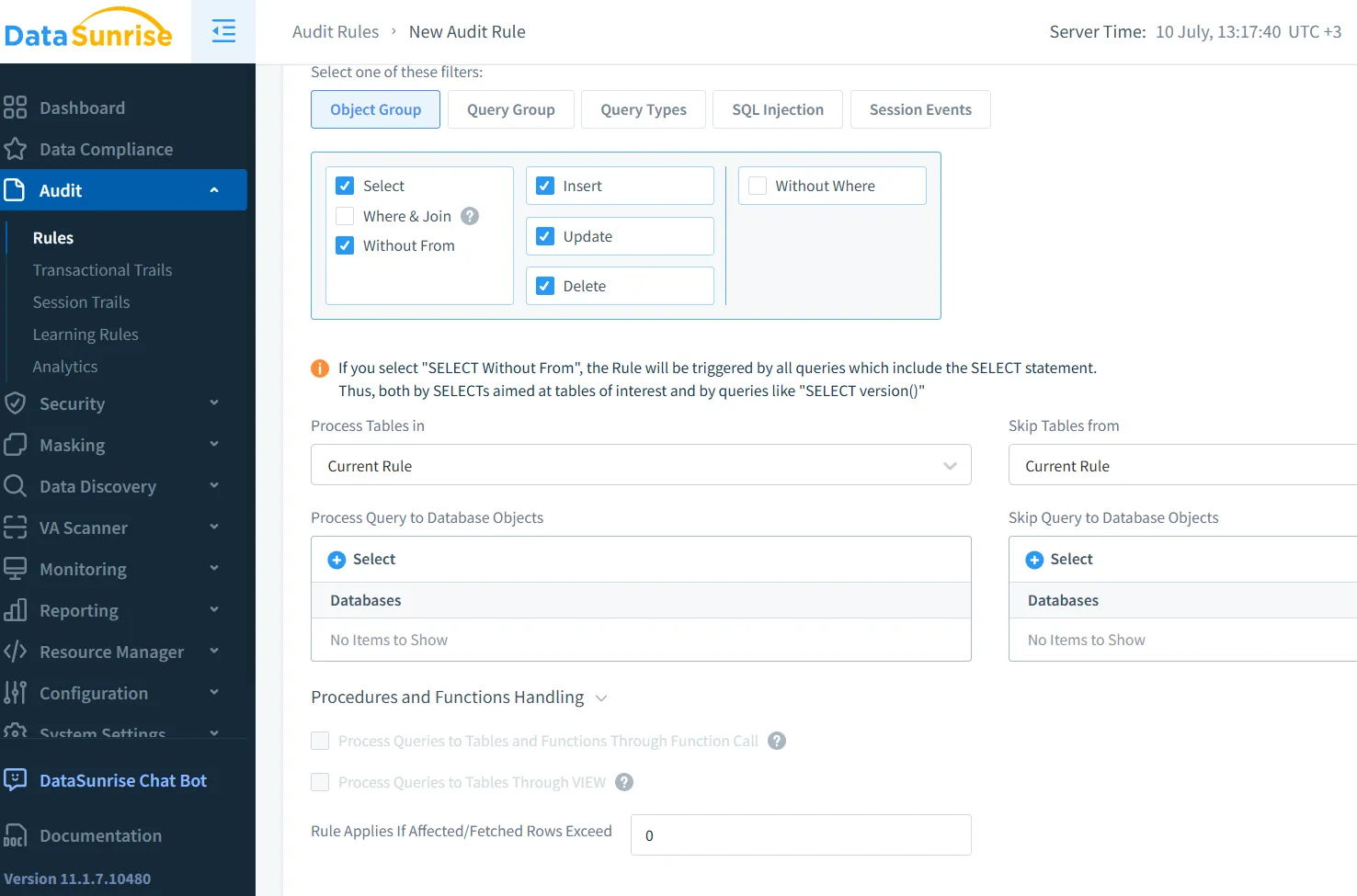
One powerful feature is conditional masking. For example, a GenAI system requesting user emails might be allowed only partial access unless a compliance officer is involved:
{
"rule": "mask_email",
"condition": "role != 'compliance_officer'",
"columns": ["email"]
}
Additionally, the system can scan the database and automatically detect sensitive data using its data discovery engine. This eliminates the need for manual tagging and improves policy accuracy.
Real-Time Monitoring and Alerts
In GenAI workloads, queries often spike as models index documents or generate embeddings. DataSunrise helps monitor these behaviors, detect anomalies, and issue alerts when patterns deviate from expected norms. Instead of relying on a fixed query limit, you can define dynamic thresholds based on user profiles or time windows.
Alerts can be routed directly to your collaboration tools. For example, a high-volume data export can trigger a message in Slack or Microsoft Teams. Setup instructions for such integrations are outlined in the Teams alerting guide. For broader guidance on monitoring and alerting in AWS environments, see the AWS Security Blog on auditing and compliance.
Compliance Through Audit Logs
Audit logs are a backbone for regulatory compliance. For GDPR, they help track user data access and support erasure requests. Under HIPAA, they ensure that all access to patient data is logged and unauthorized use is flagged. PCI DSS requires detailed access records for systems handling payment data.
With DataSunrise, these logs can be aggregated into automated compliance reports using its Compliance Manager. This reduces manual effort during audits and improves documentation for regulators.
AWS also provides compliance guidance specific to services like Amazon RDS in its Security and Compliance Center, including detailed documentation on data protection strategies.
Security Benefits Beyond Logging
Beyond simple tracking, audit logs form part of a broader security strategy. DataSunrise integrates masking, behavior analysis, and injection detection into one flow. If an LLM is exploited via a prompt injection, it might issue suspicious queries. These can be caught early by audit rules and blocked by masking or throttling policies.
This layered approach supports a Zero Trust Data Access model. Instead of assuming the model or API is trustworthy, each request is validated, logged, and constrained based on user role and context. Integration with role-based access controls and data protection policies further tightens control.
Final Thoughts
As GenAI becomes part of everyday digital experiences, the risks around sensitive data access multiply. Configuring a robust Amazon RDS Audit Log system is no longer optional. Native audit tools are a good foundation, but tools like DataSunrise provide the visibility, masking, and behavior analytics needed to secure your AI stack.
To explore more about audit configurations and security practices, visit the DataSunrise Audit Guide and Data Security section. For additional AWS guidance, refer to the official AWS RDS security documentation.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now