
Athena Security
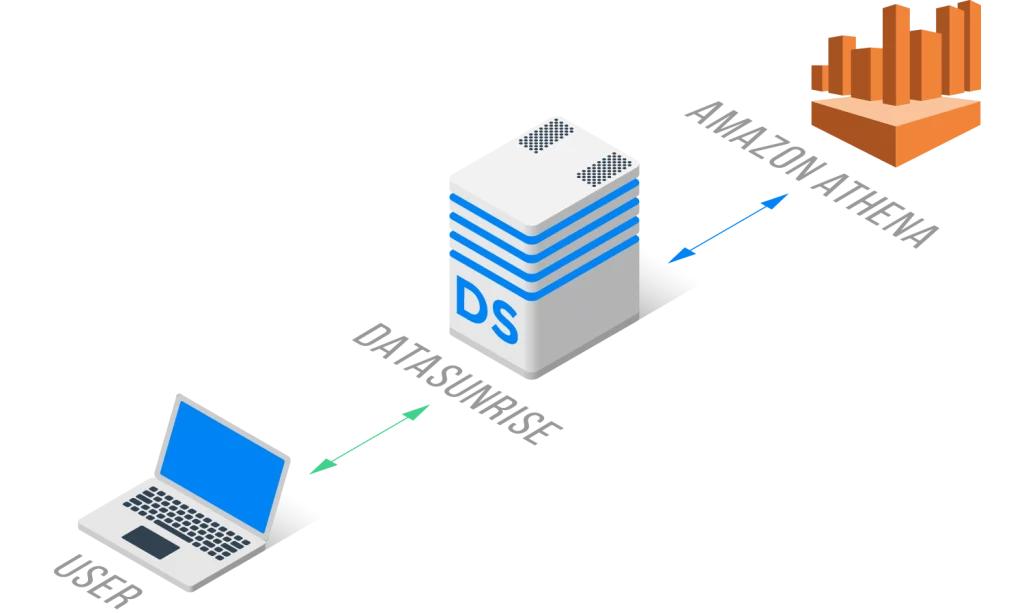
Contents:
- Understanding Athena
- Athena Workflow Overview
- Handling New Data in Athena
- The Security Perspective
- Built-in AWS Security Features for Athena
- Logging and Monitoring: Specifics for Athena
- Enhancing Athena Security with DataSunrise
- Key Considerations for Athena Database Instances
- Audit and Masking of Athena Queries in DataSunrise
- Conclusion: Enhancing Athena Security with DataSunrise
Understanding Athena
Imagine a scenario where you need to collect data from various log files and store it in a database. However, the challenge lies in the multitude of log file types and formats – CSV, JSON, TSV, and more. Wouldn’t it be convenient to have an S3 bucket where simply placing a file automatically makes its data accessible through standard SQL queries?
Amazon Athena is considered a serverless service provided by Amazon Web Services (AWS). It allows you to query data stored in Amazon S3 using standard SQL syntax without the need to manage any infrastructure. This serverless nature means that you don’t need to provision or manage any servers; you only pay for the queries you run.
In this article, we will explore the built-in AWS security features and how DataSunrise can further enhance Athena security.
Athena Workflow Overview
When you create a table in Athena, you specify the location of the data in an S3 bucket, and Athena scans the data to infer the schema and metadata for that table. This inference process typically occurs when you execute a query against the table.
Handling New Data in Athena
If you add new files to the same S3 location after the table has been created, Athena will not automatically create new tables for each file. Instead, it will automatically recognize and incorporate the new files into the existing table’s schema if they have the same structure (i.e., same column names and data types) as the original file(s) used to create the table.
The existing table in Athena will represent all the data files in the specified S3 location as a single logical dataset. Athena treats the combined data from all these files as part of the same table, allowing you to query the entire dataset seamlessly without needing to create additional tables.
However, if the new files have a different schema from the original file(s), Athena may not be able to automatically incorporate them into the existing table, and you may need to manually update the table schema or create a new table to accommodate the new file structure.
The Security Perspective
Built-in AWS Security Features for Athena
AWS provides several built-in security measures to protect your Athena environment. These include:
- IAM Policies: Manage user permissions and control access to Athena resources.
- Encryption: Secure data at rest using Amazon S3 server-side encryption or client-side encryption.
- Network Isolation: Use Amazon VPC to isolate your Athena network environment.
- Logging and Monitoring: Utilize AWS CloudTrail and Amazon CloudWatch for auditing and real-time monitoring of Athena activities.
These foundational features form the bedrock of Athena security, ensuring that your data is protected from the ground up.
Logging and Monitoring: Specifics for Athena
Amazon Athena comes with several built-in monitoring and logging features as part of the AWS cloud ecosystem. However, despite having many essential monitoring tools that provide row usage data, it lacks database-oriented security rules, sensitive data discovery, masking and user behavior analysis capabilities natively provided by DataSunrise. While built-in tools are crucial for enhancing security, they require additional data analysis and processing.
- Query Execution Metrics: Amazon Athena provides detailed query execution metrics.
- AWS CloudWatch Logs Integration: Athena can publish query execution logs to Amazon CloudWatch Logs.
- AWS CloudTrail Integration: Athena integrates with AWS CloudTrail, which provides a comprehensive audit trail of API activity and resource usage within your AWS account.
- Query History: Amazon Athena maintains a query history that allows you to view details of past query executions.
- Amazon S3 Access Logs: If your Athena queries access data stored in Amazon S3 buckets, you can enable S3 Server Access Logging to track S3 API requests.
- Cost Explorer: AWS Cost Explorer allows you to visualize and analyze your AWS usage and spending, including costs associated with Athena queries.
Enhancing Athena Security with DataSunrise
DataSunrise takes Athena security to the next level with its suite of security tools designed specifically for Amazon Athena. Here’s how DataSunrise fortifies Athena security:
- Real-Time Monitoring: Continuously monitors database activity, detecting and alerting on suspicious events.
- Database Firewall: Protects against SQL injection and unauthorized access attempts, blocking malicious queries instantly.
- Sensitive Data Discovery: Identifies and masks sensitive data to comply with regulatory standards.
- Two-Factor Authentication: Adds an extra layer of security for database access.
- Masking: Obscures specific data. To enable either type of masking, DataSunrise must be deployed in Proxy Mode.
By integrating DataSunrise with Athena, organizations can achieve a more robust security posture.
Key Considerations for Athena Database Instances
When working with Athena database instances, it’s crucial to keep the following in mind:
- Query Access Management: Ensure that only authorized users can run queries on sensitive data.
- Cost Management: Be mindful of query costs and optimize queries to prevent unnecessary expenses.
- Data Classification: Classify data based on sensitivity and apply appropriate security controls.
These considerations are especially important for Athena instances due to their serverless nature and direct interaction with data stored in S3.
As the Athena service differs from regular databases, there may be some distinctions in its integration with DataSunrise. When creating an instance for Athena in DataSunrise, the user generates a new SSL keypair for the proxy. However, for other database types, there is an option for ‘Without SSL Keys Group’. In Dynamic Masking, only mask data is available in the Masking Settings. Remember to refer to the documentation when necessary.
Audit and Masking of Athena Queries in DataSunrise
DataSunrise offers a flexible and user-friendly interface for setting up audit and masking functionalities. The images below highlight the DataSunrise setup process and the outcomes of executing a SELECT * request.
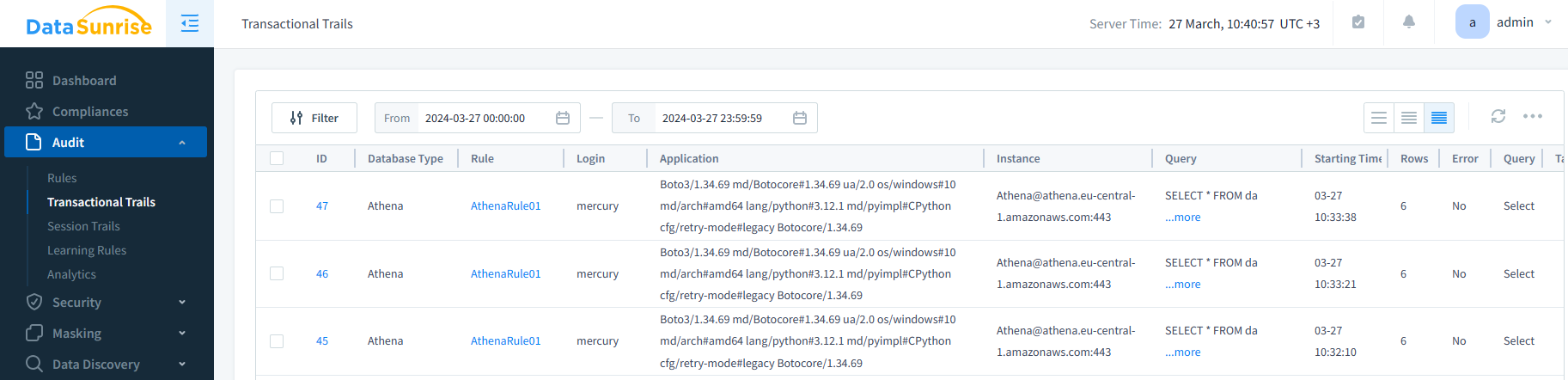
Figure 1: The requests for a table in Athena undergo auditing. The audit rule log captures various information about the request, including its result if necessary.
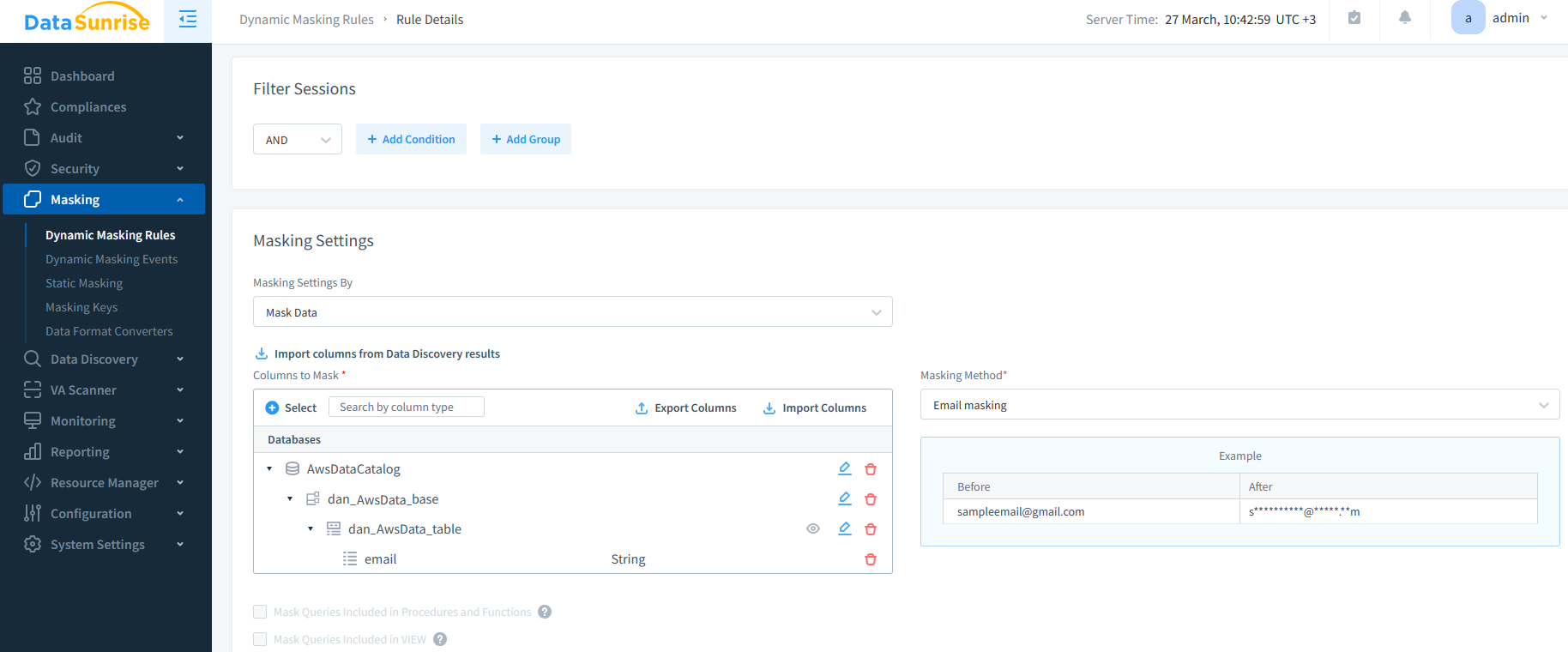
Figure 2: Masking settings for the Athena service are shown. Note the ability to specify the column for masking and the chosen masking method.
At DataSunrise, we offer unparalleled flexibility in data masking, allowing you to fine-tune your data protection strategies according to your unique requirements. Whether it’s applying simple masking techniques to conceal all data with empty lines or preserving specific formats such as emails while masking other columns, our platform empowers you to customize your data security measures with precision and ease.<\p> 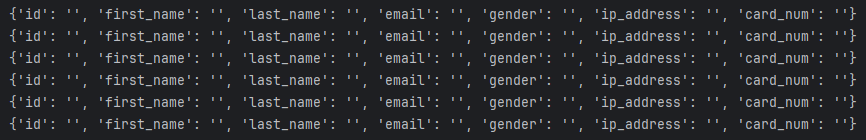
Figure 3: The whole table selected for masking. All data in the query result is replaced with empty lines.
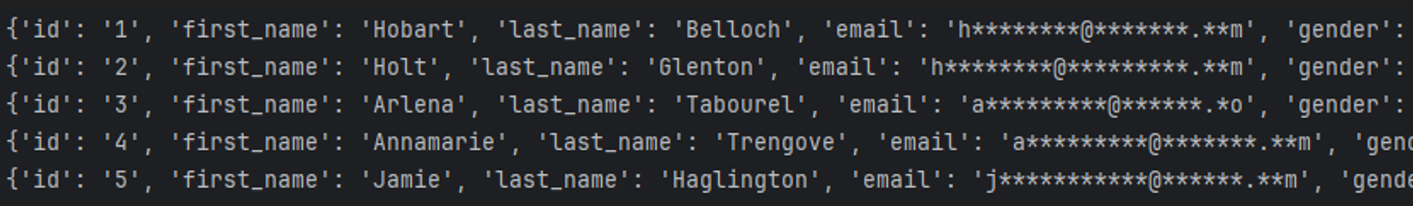
Figure 4: The ’email’ column after masking. The ‘Email Masking’ method was selected in DataSunrise Dynamic Masking rule setup.
Explore the comprehensive functionality of DataSunrise, extending beyond Audit and Masking capabilities, with exceptional coverage across various databases, including Athena by AWS. Contact our team today for an insightful demonstration, and unlock the full potential of data security with DataSunrise.
Conclusion: Enhancing Athena Security with DataSunrise
In conclusion, while AWS provides strong foundational security features for Athena, DataSunrise enhances Athena security by offering additional layers of protection. With its comprehensive monitoring, firewall capabilities, and sensitive data management, DataSunrise ensures that your cloud corporate infrastructure remains secure and compliant. By leveraging both AWS’s built-in features and DataSunrise’s advanced tools, organizations can create a more reliable and safe environment for their data in Amazon Athena.
