
Navigating Data Compliance Regulations

Introduction
In the modern digital landscape, data has become one of the most valuable strategic assets an organization can possess. However, this value also introduces significant responsibility to protect it from unauthorized access, misuse, or loss. As businesses expand globally and operate within increasingly interconnected ecosystems, the importance of strong data governance and ethical data-handling practices continues to grow. Solutions such as DataSunrise Data Discovery play a key role by helping organizations locate and classify sensitive data as part of a holistic governance approach.
Comprehensive compliance frameworks — including GDPR, HIPAA, and CCPA — provide the legal and operational foundation for ensuring that personal and sensitive information is managed responsibly throughout its entire lifecycle. The European Commission’s official GDPR guidance stresses the importance of strict data protection principles centered on transparency, accountability, and individual rights. Adhering to these standards enables organizations to preserve customer trust, avoid substantial regulatory penalties, and align their operations with internationally recognized expectations for responsible data use. Beyond meeting legal requirements, effective compliance demonstrates a long-term commitment to data integrity, corporate credibility, and the sustainable growth of digital business.
Understanding Data Compliance Regulations
Data compliance focuses on following legal requirements that define how sensitive or personal information is collected, stored, processed, and protected. These regulations are intended to shield individuals from misuse, breaches, and unauthorized access to their data.
Notable examples of these frameworks include:
- GDPR – sets the standard for data privacy within the European Union
- HIPAA – regulates healthcare data in the United States
- PCI DSS – protects payment and credit card data across industries
Mapping each framework’s requirements to specific technical safeguards—like access controls and data masking—simplifies implementation and audit readiness.
Data Compliance — Summary, Steps, and Quick Checks
Summary
- Scope: GDPR (EU personal data), HIPAA (US healthcare), PCI DSS (card data), SOX (financial records).
- Minimum controls everywhere: access control, encryption, audit trails, retention & deletion policy.
- Evidence: reproducible reports, immutable logs, and mapped safeguards per framework.
Implementation Steps (8)
- Classify data (PII/PHI/PCI/financial) and assign owners.
- Apply least-privilege access controls with MFA.
- Enable encryption in transit/at rest (GDPR Art.32).
- Turn on audit trails; standardize fields (actor, object, action, status, time, source IP).
- Set retention & deletion aligned to regs (e.g., PCI ≈ 12 months, SOX up to 7 years).
- Automate reports for GDPR, HIPAA, PCI DSS, SOX.
- Route alerts/evidence to SIEM; review failed logins, role changes, bulk exports weekly.
- Document everything (policies, exceptions, DPAs) and re-test quarterly.
Regulations → Safeguards
| Framework | Key Expectation | Safeguard |
|---|---|---|
| GDPR | Transparency, rights, breach notice | Data inventory, consent logs, encryption, deletion workflows |
| HIPAA | Audit controls & PHI integrity | Access logging, tamper-evident storage, minimum necessary |
| PCI DSS | Link actions to authenticated users | Field-level masking, role-based access, network segmentation |
| SOX | Financial record integrity | Change logging, segregation of duties, immutable evidence |
Quick Checks
- Can you show last 90 days of access logs for PII/PHI tables?
- Is encryption on for all regulated datasets (at rest + TLS)?
- Do you have evidence of deletion/retention policy enforcement?
- Are privileged role changes reviewed and signed off weekly?
Where Compliance Applies: Common Data Sources
Data compliance regulations affect several categories of information processed by organizations, including:
- Customer data: Contact details, billing info, purchase history
- Employee records: Social security numbers, job performance evaluations, health coverage
- Financial systems: Transactions, banking details, credit information
- Medical records: Electronic Protected Health Information (ePHI)
As data volumes grow and digital infrastructure expands, applying strong compliance principles to each data source is critical for legal and operational continuity.
| Tier | Examples | Controls |
|---|---|---|
| Public | Marketing brochures | None / MD5 checksum |
| Internal | Employee directory | MFA, VPN |
| Confidential | Customer e-mail, invoices | Role-based access, TLS |
| Restricted | SSNs, card data, ePHI | Field-level masking, HSM-backed keys |
Security Foundations of Compliance
Most compliance frameworks are built on core information security principles. These are not optional suggestions — they are mandated controls that reduce exposure to loss, theft, or unauthorized access. Key components include:
- Access controls: Restrict access to authorized personnel only
- Encryption: Protect data at rest and in transit
- Data backups: Ensure availability in case of system failure
- Regular auditing: Assess security effectiveness and identify weaknesses
By implementing these controls, businesses demonstrate a commitment to data governance and gain trust with regulators, customers, and business partners alike.
Real-World Examples of Data Compliance
GDPR: Consent and Erasure Rights
Under GDPR, any organization processing EU residents’ data must follow strict transparency and consent guidelines. For instance, sending marketing emails requires companies to:
- Clearly state what data is being collected and why
- Obtain affirmative consent (opt-in)
- Offer opt-out and data deletion options at any time
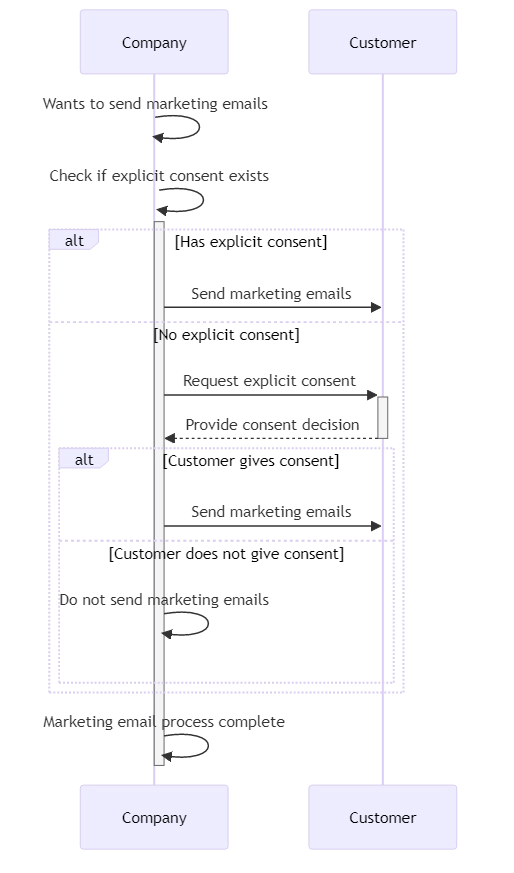
Failing to meet these obligations can lead to significant fines and reputational loss. Therefore, robust consent management is essential for GDPR compliance.
HIPAA: Access Logging in Healthcare
HIPAA requires detailed logging of how and when patient data is accessed. Organizations must know:
- Which user accessed the record
- The time and date of access
- The type of interaction (e.g., view, edit, delete)
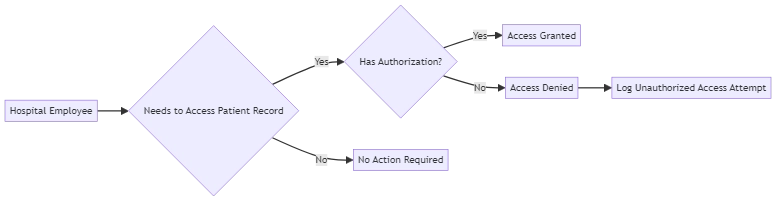
Here’s a simplified example of a PostgreSQL logging mechanism that supports HIPAA-aligned visibility:
-- PostgreSQL: Basic HIPAA-style access log
CREATE TABLE ephi_access_log (
id SERIAL PRIMARY KEY,
user_name TEXT,
action TEXT,
accessed_at TIMESTAMP DEFAULT current_timestamp,
table_name TEXT,
query TEXT
);
CREATE OR REPLACE FUNCTION log_access()
RETURNS EVENT_TRIGGER AS $$
BEGIN
INSERT INTO ephi_access_log(user_name, action, table_name, query)
VALUES (
current_user,
tg_tag,
tg_table_name,
current_query()
);
END;
$$ LANGUAGE plpgsql;
However, native logging has limitations. A platform like DataSunrise offers enhanced capabilities such as read-level tracking, anomaly detection, and seamless SIEM integration — aligning with both technical and regulatory expectations.
Why Data Compliance Matters Beyond Fines
Compliance is often framed around penalties, but the real business impact goes deeper. Strong data compliance reduces breach response times, builds customer trust, and opens the door to partnerships with regulated industries. Organizations that align with GDPR, HIPAA, and PCI DSS are not only protecting sensitive information — they are proving reliability to auditors, clients, and regulators alike. In competitive markets, being able to produce clean, audit-ready evidence can be the difference between winning contracts and being disqualified at the RFP stage.
Challenges in Data Compliance
Data compliance is not without its hurdles. Organizations often face challenges such as:
- Evolving regulations: Keeping up with changes in data protection laws like GDPR or HIPAA.
- Data volume: Managing increasing amounts of sensitive data across diverse platforms.
- Employee awareness: Ensuring employees understand the importance of data security and privacy.
- Compliance fatigue: Balancing compliance efforts with day-to-day business operations.
Addressing these challenges requires not just adherence to regulations but a proactive approach using the right tools and policies to mitigate risks. Research from PwC’s Global Compliance Survey consistently shows that organizations across industries face these same compliance challenges, highlighting the universal nature of these data protection hurdles.
Mapping Data Compliance Regulations to Safeguards
Each framework emphasizes accountability, traceability, and secure handling of sensitive information. The table below shows how data compliance regulations translate into technical safeguards:
| Framework | Key Requirement | Technical Safeguard |
|---|---|---|
| GDPR | Data subject rights, lawful processing, breach notification | Access controls, encryption, audit-ready evidence packs |
| HIPAA | Audit controls, PHI integrity, access traceability | Audit trails, anomaly detection, tamper-evident logs |
| PCI DSS | Link actions to authenticated users, protect cardholder data | Field-level masking, session logging, role-based access |
| SOX | Financial record integrity, privileged activity logging | Role escalation monitoring, immutable log storage |
By aligning safeguards with regulatory mandates, DataSunrise simplifies compliance audits, reduces manual overhead, and strengthens overall security posture.
Native Compliance Logging Examples
Every compliance framework expects organizations to demonstrate user accountability and audit integrity. Most databases provide basic hooks, but each works differently. Here are two common native approaches:
SQL Server: Audit for PCI DSS & SOX
-- Create a server audit
CREATE SERVER AUDIT PCI_Audit
TO FILE (FILEPATH = 'C:\SQLAudits\', MAXSIZE = 1 GB, MAX_ROLLOVER_FILES = 10);
ALTER SERVER AUDIT PCI_Audit WITH (STATE = ON);
-- Capture activity in the FinanceDB schema
CREATE DATABASE AUDIT SPECIFICATION PCI_DB_Audit
FOR SERVER AUDIT PCI_Audit
ADD (SELECT, INSERT, UPDATE, DELETE ON SCHEMA::FinanceDB BY PUBLIC),
ADD (SCHEMA_OBJECT_CHANGE_GROUP);
ALTER DATABASE AUDIT SPECIFICATION PCI_DB_Audit WITH (STATE = ON);
-- Review recent audit entries
SELECT event_time, server_principal_name, statement
FROM sys.fn_get_audit_file('C:\SQLAudits\*.sqlaudit', DEFAULT, DEFAULT)
WHERE event_time > DATEADD(HOUR, -2, GETDATE());
MySQL: Enterprise Audit JSON Logs
-- Enable the audit plugin
INSTALL PLUGIN audit_log SONAME 'audit_log.so';
-- Log all activity (scope to tables in production)
SET PERSIST audit_log_policy = ALL;
SET PERSIST audit_log_format = JSON;
-- View logs
tail -f /var/lib/mysql/audit.log
Native logging can prove access history but requires heavy customization to meet GDPR or HIPAA reporting standards. This is where automation platforms step in.
Ensuring Audit Log Integrity
For compliance, it’s not enough to collect audit data—you must prove it hasn’t been altered. A common technique is chaining cryptographic hashes across rows in PostgreSQL:
-- Requires pgcrypto
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE TABLE audit_events (
id BIGSERIAL PRIMARY KEY,
actor TEXT,
action TEXT,
ts TIMESTAMPTZ DEFAULT now(),
prev_hash BYTEA,
row_hash BYTEA
);
CREATE OR REPLACE FUNCTION audit_events_chain()
RETURNS TRIGGER AS $$
DECLARE v_prev BYTEA;
BEGIN
SELECT row_hash INTO v_prev FROM audit_events ORDER BY id DESC LIMIT 1;
NEW.prev_hash := v_prev;
NEW.row_hash := digest(
coalesce(NEW.actor,'') || '|' || coalesce(NEW.action,'') || '|' || NEW.ts::text || '|' || encode(coalesce(NEW.prev_hash,'\x'),'hex'),
'sha256'
);
RETURN NEW;
END;
$$ LANGUAGE plpgsql;
CREATE TRIGGER trg_chain
BEFORE INSERT ON audit_events
FOR EACH ROW EXECUTE FUNCTION audit_events_chain();
Run a verification query to check that each row’s prev_hash matches the previous record. Any mismatch signals tampering—supporting SOX and GDPR integrity requirements.
GDPR Max Fine
€20 M
or 4 % of global turnover
HIPAA Tier 4
$1.9 M
per violation, annual cap
PCI DSS
$500 K
per incident + surcharge
Weekly Compliance Health-Check
Database tasks
- Verify backups completed & test restore
- Rotate admin credentials if aged > 90 days
- Review failed-login trends in SIEM
Application layer
- Run dependency-vulnerability scan (e.g., Snyk)
- Confirm TLS cert expiry < 30 days alerts
User awareness
- Send 60-second phishing drill mail
- Publish weekly security tip on intranet
Compliance Outcomes That Matter
| Outcome | Without Automation | With DataSunrise |
|---|---|---|
| Audit Preparation | Manual evidence gathering (weeks) | Pre-built reports (hours) |
| Breach Detection | Reactive, post-incident | Real-time alerts & anomaly detection |
| Regulatory Risk | High exposure to fines | Aligned controls across GDPR, HIPAA, PCI DSS |
Industry Use Cases
- Finance: SOX-ready logs and PCI DSS payment protection
- Healthcare: Full traceability of PHI for HIPAA audits
- SaaS/Cloud: Multi-tenant activity monitoring for GDPR accountability
- Government: Tamper-evident logs to support transparency mandates
Automation: A Strategic Advantage in Compliance
Manual compliance management often leads to delays, blind spots, and inconsistent enforcement. That’s why forward-thinking organizations are increasingly turning to automation platforms like DataSunrise to enforce policies, detect anomalies, and generate real-time compliance reports. By integrating compliance automation into daily operations, businesses reduce overhead, speed up audits, and ensure policy adherence at scale — even as data environments grow more complex.
# datasunrise_report.yml — weekly ISO 27001 evidence pack
report:
title: "ISO 27001 Annex A.12 Audit Log Review"
schedule: "0 3 * * 1" # Mondays 03:00 UTC
include:
- failed_logins
- privilege_escalations
- data_export > 10k rows
deliver_via:
email:
to: [email protected]
attach: PDF
Drop this file in /opt/datasunrise/reports/; the platform auto-schedules generation.
Scaling Data Compliance with Policy-Driven Architecture
Enterprise-grade compliance doesn’t stop at encryption or logging — it’s about aligning controls with clear, enforceable data policies. The most effective compliance programs use policy-driven architectures that map regulation to specific technical safeguards and behavioral rules.
- Data Classification Policies: Identify and tag PII, PHI, and financial data using automated discovery tools. Apply masking, alerting, or encryption based on sensitivity level and user role.
- Retention Policies: Define time-based rules per regulation (e.g., 7 years for SOX, 1 year for PCI DSS) to control when data can be purged or archived. Ensure these policies are enforced at the storage layer.
- Access Control Policies: Use zero-trust principles to restrict access by IP range, role, or risk score. Monitor and log deviations from policy with contextual alerts sent to SIEM platforms.
- Audit Policies: Generate scheduled, scoped audit reports for GDPR, HIPAA, ISO 27001, and more. Platforms like DataSunrise allow teams to define policy rules in YAML or via GUI and apply them across multi-cloud environments.
By adopting policy-as-code, organizations create a flexible foundation for scaling compliance across teams, regions, and tech stacks — without relying on brittle manual checklists or siloed tools.
Data Compliance FAQ
How long should we keep audit logs?
Align with your strictest framework: SOX may require retention up to 7 years; PCI DSS typically expects ~12 months. Define and enforce policy per dataset, and apply immutable storage where required.
Do we need a Data Protection Officer (DPO)?
GDPR requires a DPO for large-scale monitoring or processing of special-category data. Otherwise, appoint an accountable owner and document responsibilities to demonstrate compliance readiness.
What does data compliance mean?
Data compliance means following laws and regulations that govern how sensitive data is collected, processed, stored, and shared. It ensures protection of personal and financial information against misuse or exposure.
Which regulations are most common?
Widely applied frameworks include GDPR (EU data privacy), HIPAA (US healthcare data), and PCI DSS (payment card security). Many organizations fall under multiple frameworks.
What data sources fall under compliance rules?
Customer records, employee HR files, medical data, and financial transactions are commonly regulated. Logs, backups, and derived datasets can also fall within scope if they contain sensitive fields.
How do organizations prove compliance?
- Maintain audit logs and access records with integrity checks.
- Apply access controls, encryption, and masking policies.
- Produce evidence reports for regulators and auditors.
- Demonstrate retention, deletion, and consent practices.
What tools simplify compliance?
Platforms like DataSunrise automate sensitive data discovery, centralized auditing, real-time alerting, and compliance reporting, reducing manual effort and audit risk.
The Future of Data Compliance
Data compliance is no longer static. Emerging trends are reshaping how organizations protect sensitive data:
- AI-Assisted Auditing: Machine learning detects anomalies in user behavior and automatically generates compliance evidence.
- Continuous Controls: Policies mapped as code allow real-time enforcement across multi-cloud and hybrid systems.
- Zero-Trust Data Access: Every query, API call, and login is verified contextually, limiting exposure to insider threats.
- Immutable Evidence Stores: Blockchain-backed or hash-chained logs ensure tamper-proof audit records for regulators.
Forward-looking companies adopt these methods not just to avoid penalties but to prove resilience and trustworthiness in competitive markets.
Conclusion
Global data protection standards such as GDPR, HIPAA, and PCI DSS define the foundation of responsible data management across industries. These frameworks promote transparency, reduce both operational and reputational risk, and ensure that personal and sensitive information is handled ethically and securely. For modern organizations, especially those operating in regulated or competitive sectors, maintaining compliance is no longer just a legal obligation — it is a strategic differentiator that strengthens customer confidence and supports sustainable business growth.
Yet, compliance is a constantly moving target. Regulatory landscapes evolve, threats become more sophisticated, and manual oversight can no longer keep pace. This makes automation and intelligent policy enforcement indispensable. With DataSunrise, organizations can simplify and automate every stage of the compliance process — from continuous auditing and proactive policy management to generating detailed, audit-ready reports in real time. The platform provides unified visibility and control across hybrid and multi-cloud environments while ensuring seamless and uninterrupted operations.
By integrating compliance directly into day-to-day database workflows, enterprises can detect anomalies early, respond swiftly to risks, and present verifiable proof of accountability to regulators and stakeholders. This proactive approach not only minimizes the likelihood of breaches and penalties but also enhances organizational resilience and brand integrity in a dynamic regulatory environment. Take the next step toward intelligent compliance — book a live demo to experience how DataSunrise automates and simplifies compliance from the very start.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now