Data Masking Tools and Techniques for MariaDB
Modern database environments rarely serve a single purpose. A typical MariaDB deployment supports applications, analytics, support teams, automated jobs, and external integrations. In many cases, all of them work with the same datasets. When those datasets contain personal, financial, or regulated information, unrestricted visibility quickly becomes a liability.
For an overview of MariaDB’s architecture and use cases, see the official documentation: https://mariadb.org/
Data masking addresses this problem by transforming sensitive values before users or applications receive them. Unlike encryption, masking keeps database structure and query behavior intact. At the same time, it limits what users can actually see. As a result, masking naturally complements broader data security
and database security strategies.
Meanwhile, regulatory pressure continues to grow, and insider risk becomes harder to ignore. Because of this, data masking has moved from a “nice-to-have” feature to an operational requirement. In regulated environments, organizations closely tie masking to data compliance regulations
and the protection of personally identifiable information (PII).
This article explains how teams can implement data masking in MariaDB using native techniques. It also shows how centralized platforms extend masking into a policy-driven, auditable, and compliance-aligned control through mechanisms such as dynamic data masking.
What Is Data Masking?
Data masking is a data protection technique that replaces sensitive values with modified, obfuscated, or synthetic equivalents. Its goal is to reduce the risk of exposure while keeping data usable for development, analytics, and operational workflows. In practice, masking works alongside broader data security
initiatives.
Organizations can implement masking in several ways. For example, teams may apply it statically to data copies, enforce it dynamically at query time, or adjust it based on user identity, role, or access path. Although each approach serves different operational needs, all of them share the same objective: limiting unnecessary visibility of sensitive values.
Most organizations use masking to protect personally identifiable information (PII), financial records, authentication secrets, and business-sensitive attributes. These data types appear across many workflows and user groups. Therefore, selective exposure becomes essential and directly supports data compliance regulations.
Unlike access controls, data masking assumes that access will happen. Instead of blocking queries, it controls what users see in query results. This approach reduces risk without disrupting normal database usage.
Native Data Masking Techniques in MariaDB
MariaDB does not provide a dedicated, built-in data masking framework. Instead, masking is typically approximated using standard SQL constructs. These approaches can be useful for demonstrations, limited environments, or narrowly scoped use cases, but they rely on manual discipline rather than enforced policy.
Views with Transformed Columns
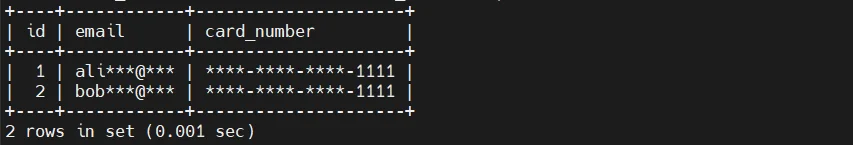
One of the most common techniques is exposing masked data through SQL views that transform sensitive columns before returning results.
/*CREATE VIEW masked_customers AS
SELECT
id,
CONCAT(SUBSTRING(email, 1, 3), '***@***') AS email,
'****-****-****' AS card_number
FROM customers;*/
In this model, applications and users are expected to query the view instead of the underlying table. The transformation logic is embedded directly into the view definition, which tightly couples masking behavior to schema design and query routing. As a result, data protection depends on consistent usage patterns rather than enforced controls.
Limitations
- Effective only if all access is strictly routed through the view
- Does not protect direct table access or ad-hoc queries
- Requires ongoing maintenance as schemas evolve
- Becomes difficult to manage across many tables and databases
Stored Functions for Conditional Masking
Another approach is to use stored functions to encapsulate masking logic and apply it conditionally based on user context or session variables.
/*CREATE FUNCTION mask_email(email VARCHAR(255))
RETURNS VARCHAR(255)
DETERMINISTIC
RETURN CONCAT(SUBSTRING(email, 1, 3), '***@***');*/
This function can then be referenced in SELECT statements or views, allowing the same masking logic to be reused across queries. In more complex setups, additional logic can be introduced to vary masking behavior depending on the connected user or role. However, enforcement remains entirely dependent on how queries are written and executed.
Limitations
- Requires disciplined and consistent query usage
- Masking logic must be manually applied everywhere it is needed
- No centralized enforcement or visibility
- Easy to bypass by querying base tables directly
Separate Masked Copies of Data
For non-production environments such as development or testing, organizations often create permanently masked copies of production data.
/*CREATE TABLE customers_masked AS
SELECT
id,
SHA2(email, 256) AS email,
NULL AS card_number
FROM customers;*/
This approach produces a dataset where sensitive values are irreversibly altered, making it safer to share with developers or external teams. However, the masking process is detached from live data access and must be repeated whenever data is refreshed.
Limitations
- Results in data duplication and additional storage overhead
- Masked datasets become outdated as production data changes
- No protection for production access or live queries
- Masking rules must be re-applied each time data is refreshed
While these native techniques can reduce accidental exposure in limited scenarios, they do not provide consistent, scalable, or auditable data masking. As environments grow and access patterns diversify, relying solely on SQL-based masking becomes increasingly fragile and difficult to govern.
Centralized Data Masking for MariaDB with DataSunrise
DataSunrise moves MariaDB masking beyond SQL-level workarounds by introducing a centralized, policy-driven security layer. Instead of embedding masking logic into queries, views, or schemas, the platform enforces masking externally. As a result, teams protect data without modifying application code or changing database structure. This model naturally aligns masking with broader data security and database security practices.
Dynamic Data Masking
Dynamic masking operates in real time while queries run. Depending on execution context, the same column can appear masked or unmasked. Therefore, teams gain fine-grained control over data exposure without rewriting SQL or maintaining parallel schemas. In practice, this approach implements dynamic data masking, where protection remains fully transparent at query time.
DataSunrise evaluates masking decisions using contextual signals such as database user or role, client IP address, application source, and session attributes. Because of this, analysts see masked values, applications continue to process real data, and administrators retain full visibility. All of this works without altering queries or application logic.
Policy-Based Masking by Data Type
Once teams discover and classify sensitive data, DataSunrise applies masking rules automatically across schemas and databases based on data type rather than individual columns. This approach builds on automated data discovery and classification processes. Consequently, protection scales as environments grow.
For example, the platform replaces emails with randomized but valid formats, tokenizes phone numbers, irreversibly hashes identifiers, and masks financial values using format-preserving substitutions. Since masking rules follow data categories instead of hardcoded schema definitions, long-term maintenance effort drops significantly.
Static Masking for Non-Production Workflows
For non-production scenarios such as development, testing, or analytics, DataSunrise supports controlled static masking during operational workflows. These workflows include database cloning, backup restoration, data export, and test data provisioning. In this context, the platform follows established static data masking practices that allow teams to reuse production data safely outside controlled environments.
As a result, masked datasets remain consistent, irreversible, and auditable. This makes them suitable for compliance-sensitive workflows without exposing real values.
Auditable Masking Operations
DataSunrise records all masking activity in a unified activity history. Each event captures who accessed the data, which masking rule applied, and when and from where the access occurred. Therefore, teams directly connect masking controls to database activity monitoring and compliance workflows.
By centralizing enforcement, visibility, and policy management, DataSunrise turns data masking for MariaDB into a consistent, scalable, and compliance-ready control rather than a collection of fragile SQL patterns.
Business Benefits of Centralized Data Masking
| Business Area | Impact |
|---|---|
| Breach risk reduction | Limits exposure of sensitive values even when access occurs, reducing the impact of insider threats and credential misuse |
| Regulatory compliance | Simplifies alignment with GDPR, HIPAA, PCI DSS, and SOX by enforcing consistent masking policies |
| Analytics and testing safety | Enables use of realistic data in analytics and test environments without duplicating or exposing production data |
| Operational visibility | Provides unified audit trails showing who accessed masked data, when, and under which policy |
| Long-term maintainability | Eliminates fragile, schema-bound SQL masking logic, reducing ongoing maintenance effort |
Conclusion
MariaDB allows basic masking through SQL-based techniques, but these approaches rely on manual enforcement and do not scale with growing environments. As access patterns and compliance requirements increase, they fail to deliver consistent protection or visibility.
Centralized platforms like DataSunrise turn data masking into a policy-driven, auditable, and context-aware control that operates independently of application logic and schemas. This makes masking reliable, enforceable, and suitable for regulated or shared-data environments.
For organizations treating MariaDB as production or compliance-critical infrastructure, data masking should be a deliberate security control—not an improvised workaround.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now