Data Obfuscation in Vertica
Data obfuscation in Vertica is a practical approach to protecting sensitive information while preserving the usability of analytical datasets. Vertica is widely adopted for large-scale analytics, reporting, and data science, where high query performance and flexible access are essential. However, as soon as sensitive attributes such as personal identifiers, financial details, or regulated business data appear in analytical tables, unrestricted visibility introduces serious compliance and security risks.
Unlike encryption, which protects data at rest or in transit, obfuscation focuses on controlling what users actually see in query results. In Vertica environments, where the same tables serve multiple teams and tools, data obfuscation helps organizations reduce exposure without duplicating data or changing existing queries. As a result, teams maintain analytical agility while enforcing consistent protection aligned with data privacy principles.
This article explains how data obfuscation is implemented in Vertica using centralized controls, dynamic masking techniques, and auditing, with DataSunrise acting as the enforcement layer through its Data Compliance capabilities.
Why Data Obfuscation Is Important in Vertica
Vertica’s architecture is optimized for analytical throughput. Columnar storage, ROS/WOS layers, and projection-based execution enable fast processing of large datasets. At the same time, these features make it difficult to apply fine-grained data protection using traditional methods.
In practice, several situations increase the need for obfuscation:
- Analytical tables that combine metrics with PII or payment data.
- Shared Vertica clusters accessed by analysts, applications, and automation.
- Exploratory SQL queries that expose more data than intended.
- Downstream exports or reports created directly from raw query results.
Vertica’s native role-based access control determines who can query a table. However, it does not restrict which column values appear in the result set. Once a query executes, Vertica returns all selected data in clear form. Therefore, data obfuscation closes this gap by transforming sensitive values before they reach the client, complementing advanced access controls.
For background on Vertica’s execution model, see the official Vertica architecture documentation.
Centralized Obfuscation Architecture for Vertica
Organizations typically implement data obfuscation in Vertica using a centralized gateway model. In this architecture, client applications connect through an intermediary layer rather than directly to the database. This layer inspects SQL queries, evaluates protection rules, and applies obfuscation consistently.
Many teams use DataSunrise Data Compliance to implement this model. DataSunrise operates as a transparent proxy in front of Vertica, enforcing obfuscation rules without altering schemas, projections, or application logic. In addition, it integrates with database activity monitoring to provide continuous visibility.
As a result, this approach enables:
- Uniform obfuscation across BI tools, scripts, and services.
- Policy-driven control based on user, role, or application context.
- Centralized configuration with consistent enforcement.
- Auditing with minimal impact on Vertica performance.
Dynamic Masking as an Obfuscation Technique
Dynamic data masking serves as the primary technique for data obfuscation in Vertica. Instead of permanently altering stored data, dynamic masking rewrites sensitive values in query results at runtime. Meanwhile, Vertica continues to store and process original values internally.
DataSunrise provides built-in dynamic data masking capabilities that evaluate each query against policy rules. These rules can consider:
- The database user or role.
- The client application or connection type.
- The environment, such as production or analytics.
- The sensitivity classification of individual columns.
Because obfuscation occurs only at the result level, analytical correctness remains intact. Aggregations, joins, filters, and calculations still operate on real values internally, while masked representations are returned to the user. This approach aligns with broader data security strategies.
Configuring Obfuscation Rules in Vertica
The first step in applying data obfuscation involves defining a rule that targets the Vertica instance and identifies which data should be transformed. Administrators specify the schemas or tables to protect and select the columns that require obfuscation.
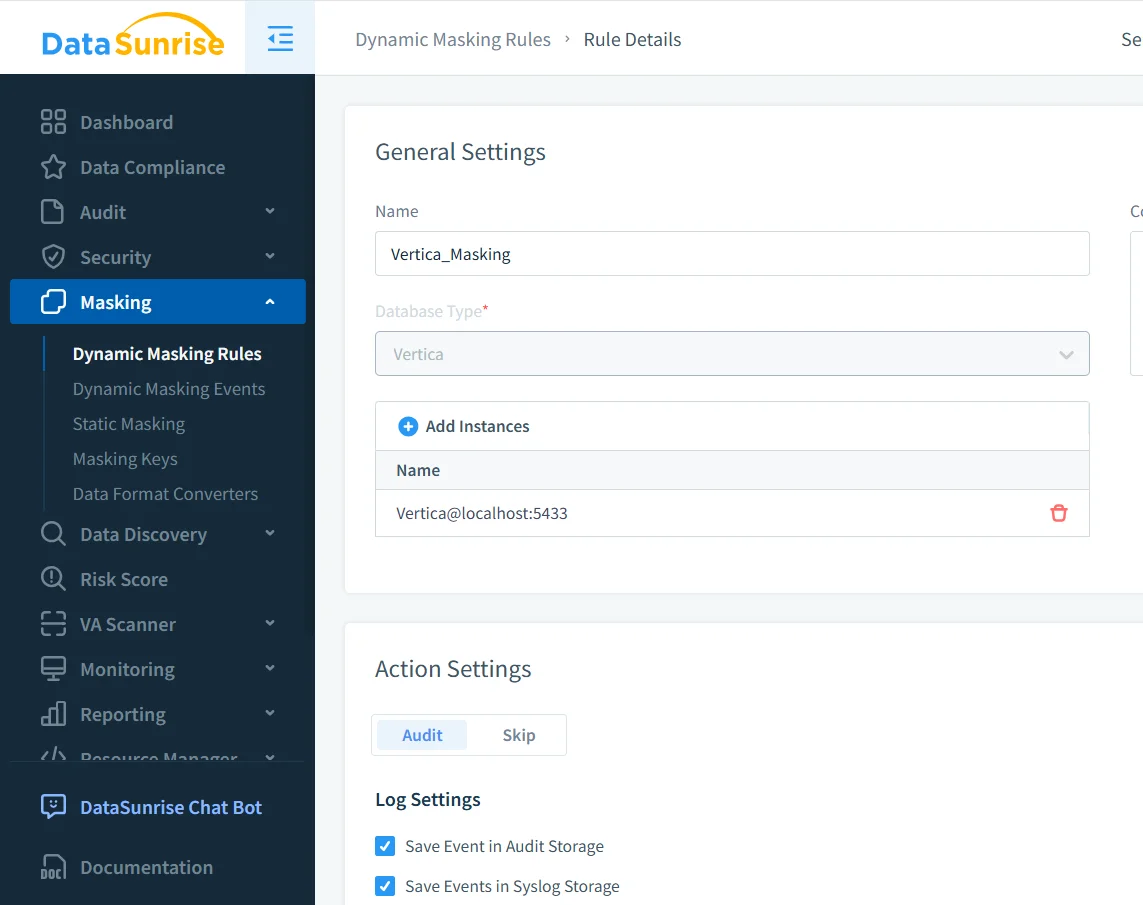
At this stage, administrators also enable auditing for obfuscation events. Consequently, the system records every transformation for compliance verification and troubleshooting, integrating with audit logs.
Run Sensitive Data Discovery before creating obfuscation rules. This discovery-driven approach ensures newly added sensitive columns inherit protection automatically as schemas evolve.
Once the rule exists, administrators define which columns should be obfuscated and how. Depending on the use case, different formats may apply, such as partial masking, token replacement, or full anonymization supported by data masking techniques.
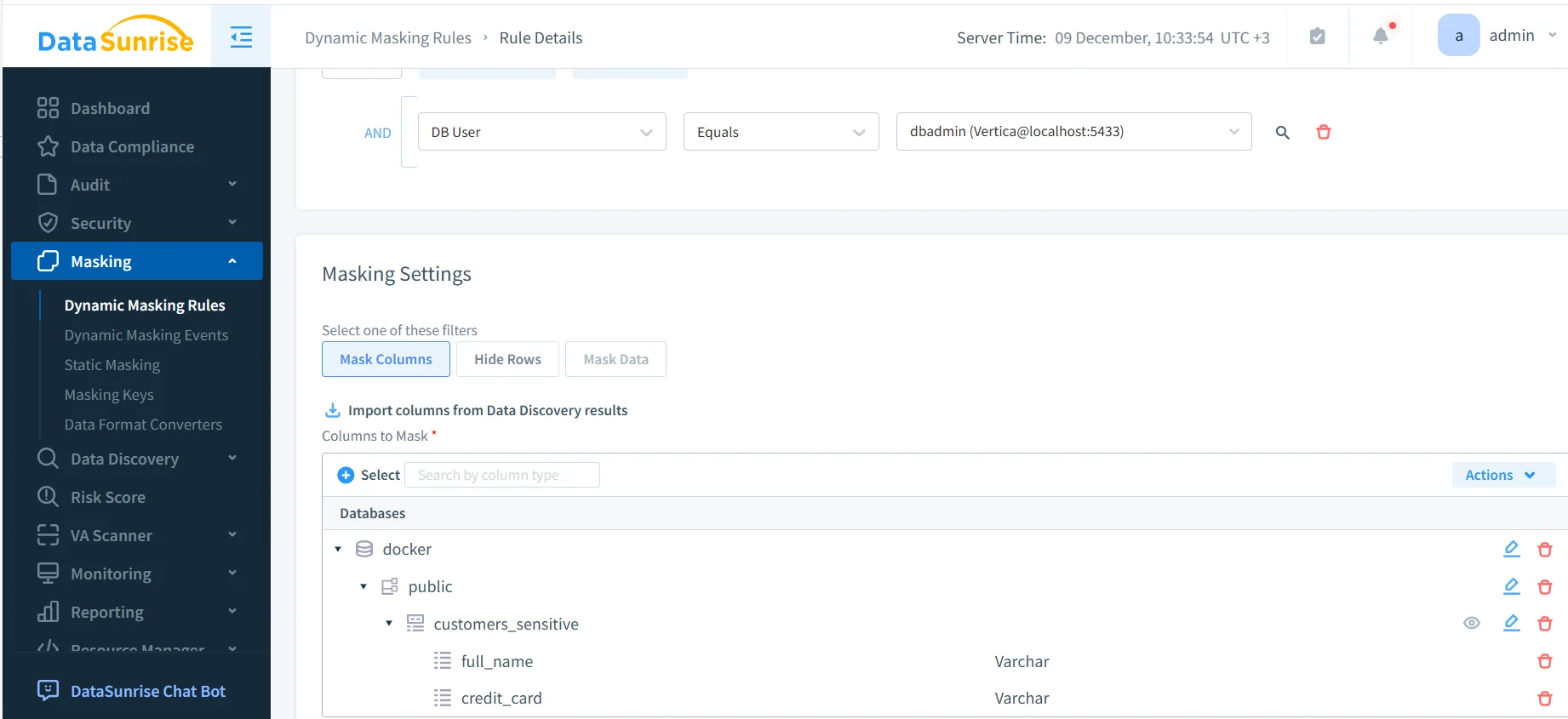
Obfuscated Results in Analytical Queries
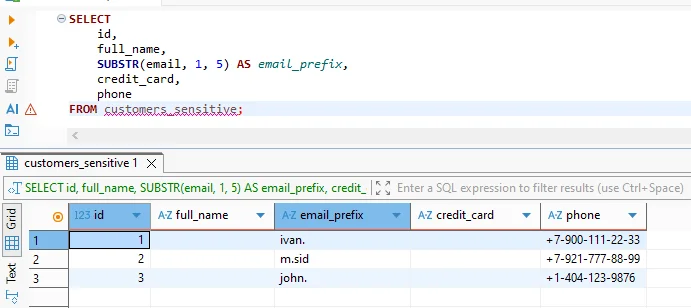
From the perspective of analysts and applications, data obfuscation remains transparent. Queries are written using standard SQL, and Vertica executes them normally. However, the returned values reflect the obfuscation policy.
Obfuscated results continue to support joins, filters, aggregations, and groupings. Therefore, the technique fits BI dashboards, exploratory analysis, and machine learning feature engineering workflows governed by data governance rules.
Because policies follow the user and execution context, teams avoid maintaining separate datasets or rewriting reports. Instead, the same Vertica tables safely serve multiple audiences with different visibility levels.
Auditing Obfuscated Data Access
Effective data obfuscation requires visibility. Organizations must demonstrate when sensitive values were transformed and who accessed the data.
DataSunrise automatically records audit events for every obfuscated query, capturing:
- The database user and client application.
- The executed SQL statement.
- The applied obfuscation rule.
- The execution timestamp and context.
These audit records integrate with Database Activity Monitoring and support compliance with regulations such as GDPR, HIPAA, and SOX. They also feed into Compliance Manager workflows.
Comparing Data Obfuscation Techniques in Vertica
| Technique | Description | Suitability for Vertica |
|---|---|---|
| Static obfuscation | Create permanently obfuscated datasets | High maintenance, limited flexibility |
| View-based obfuscation | Apply transformations via SQL views | Easily bypassed by direct access |
| Application-layer obfuscation | Obfuscation logic in BI or applications | Inconsistent enforcement |
| Dynamic obfuscation | Rewrite results at query time | Centralized and scalable |
Best Practices for Data Obfuscation in Vertica
- Identify sensitive columns using automated discovery.
- Apply obfuscation at the query layer rather than copying data.
- Test rules with real analytical workloads.
- Review audit logs regularly for unexpected access.
- Align obfuscation policies with broader data security strategies.
Conclusion
Data obfuscation in Vertica provides a flexible and scalable way to protect sensitive information in analytical environments. By applying transformations dynamically at query time, organizations reduce exposure risk without sacrificing performance or usability.
With DataSunrise acting as a centralized enforcement layer, Vertica remains a powerful analytics platform while sensitive data stays protected across dashboards, scripts, and machine learning pipelines.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now