How to Apply Dynamic Masking in MongoDB
Modern applications built on MongoDB store sensitive data such as personal identifiers, financial details, and authentication metadata. Growing regulatory pressure and expanding insider risk make real-time protection a business necessity.
Although MongoDB includes native access controls and encryption mechanisms, it lacks field-level dynamic masking for query responses. This limitation creates operational and compliance challenges, especially for organizations that must satisfy GDPR, HIPAA, PCI DSS, or SOX requirements. To reduce exposure risks, teams must implement structured data security controls alongside centralized dynamic data masking policies.
This guide shows how MongoDB manages data exposure at the native level and demonstrates how you can apply Zero-Touch Dynamic Masking with DataSunrise to enforce context-aware protection without modifying application code.
Importance of Dynamic Masking
Sensitive data does not become dangerous only when it is stolen. It becomes dangerous when it is unnecessarily exposed. In many MongoDB environments, developers, analysts, support engineers, and third-party integrations legitimately query production datasets. Without dynamic masking, those queries often return full, readable values for PII, financial records, or authentication attributes.
Static protection methods such as encryption at rest protect storage. Role-Based Access Control restricts who can connect. However, neither approach controls how sensitive fields are displayed in real time once access is granted. That is the exact gap dynamic masking addresses. Implementing structured access controls alongside runtime protection strengthens governance without disrupting workflows.
Dynamic masking enforces context-aware protection at query runtime. Instead of blocking access, it transforms sensitive fields based on identity, role, location, or policy conditions. The database remains usable, analytics continue functioning, and applications do not require modification. This model aligns with modern database security practices focused on minimizing data exposure rather than simply restricting connectivity.
This approach directly supports:
- Zero-Trust Data Access models
- Least privilege enforcement
- Reduced insider risk
- Compliance with GDPR, HIPAA, PCI DSS, and SOX
Unlike static masking, which permanently alters data, dynamic masking preserves original values in storage while protecting them during retrieval. Combined with continuous database activity monitoring and centralized dynamic data masking policies, organizations gain both visibility and control over sensitive information flows.
In regulated environments, dynamic masking becomes not just a security enhancement but a compliance necessity.
Understanding Native Data Protection in MongoDB
MongoDB includes multiple built-in mechanisms for limiting data exposure. These include Role-Based Access Control (RBAC), Client-Side Field Level Encryption (CSFLE), schema validation rules, and aggregation pipeline projections. Together, these features create a foundational security layer for controlling access and protecting stored information.
However, despite their usefulness, these controls do not provide centralized, runtime masking of returned data based on user identity or contextual access conditions. They regulate access and storage, but they do not dynamically transform sensitive fields at query time.
Using Role-Based Access Control (RBAC)
MongoDB supports RBAC to restrict access at the database and collection level. Administrators can define roles and assign specific privileges that determine which users can execute certain operations.
Example:
use admin
db.createRole({
role: "readLimited",
privileges: [
{ resource: { db: "sales", collection: "customers" }, actions: [ "find" ] }
],
roles: []
})
RBAC controls who can query a database or collection, but it does not control how returned fields are displayed. If a user has read permission for a collection, they can view all permitted fields in plain text.
In other words, RBAC enforces connectivity boundaries, not field-level runtime transformation. It defines access scope, but once access is granted, data is delivered without contextual masking.
For more on structured access governance, see:
Role-Based Access Controls
Using Aggregation for Field Redaction
MongoDB allows projections and conditional field manipulation through the aggregation framework. Developers can use $project to modify how certain fields are returned in query results.
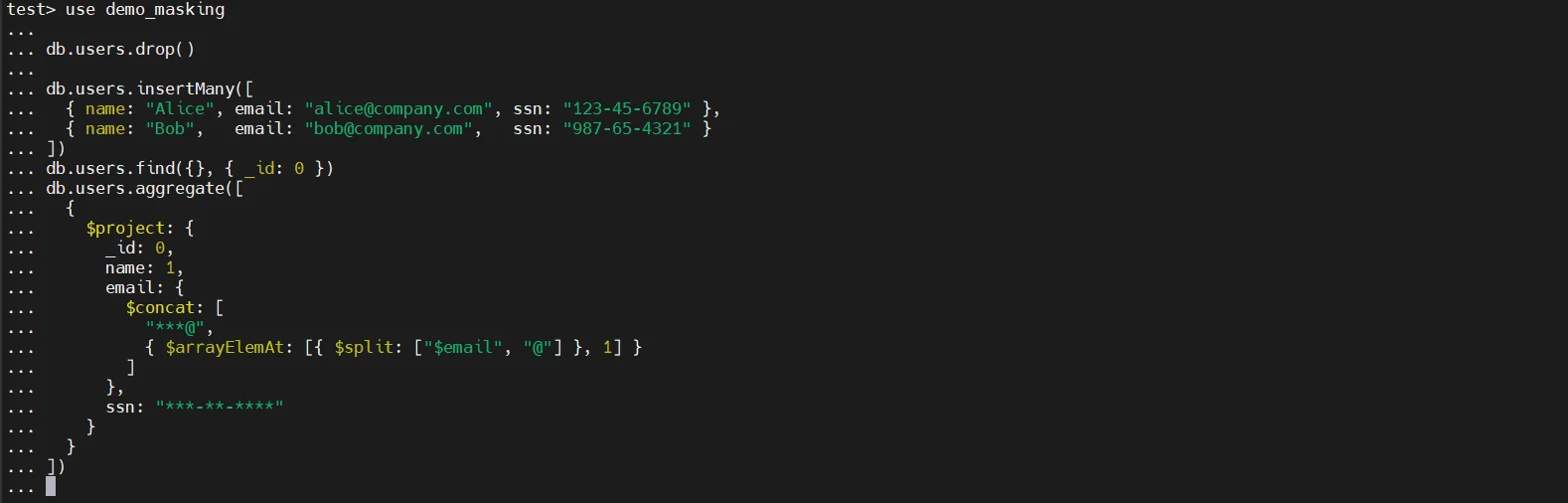
This approach can partially redact fields within specific queries. It enables developers to limit or transform sensitive values before returning them to the client.
However, it has several operational limitations. It requires application logic modification, meaning developers must explicitly implement redaction rules inside each query or service layer. It cannot enforce policies globally across all queries. It is also difficult to standardize across multiple teams and microservices. Most importantly, it lacks centralized compliance enforcement.
Each application must explicitly implement redaction logic, which increases complexity, introduces inconsistency, and creates room for human error.
Client-Side Field Level Encryption (CSFLE)
Client-Side Field Level Encryption encrypts selected fields before they are stored in the database. Sensitive values remain encrypted at rest and in transit, and only authorized clients with appropriate keys can decrypt them.
Below is a simplified CSFLE example with automatic encryption enabled for the ssn field:
const client = new MongoClient(uri, {
autoEncryption: {
keyVaultNamespace: "encryption.__keyVault",
kmsProviders: { local: { key: masterKey } },
schemaMap: {
"sales.customers": {
bsonType: "object",
properties: {
ssn: {
encrypt: {
bsonType: "string",
algorithm: "AEAD_AES_256_CBC_HMAC_SHA_512-Deterministic"
}
}
}
}
}
}
});
In this configuration, the ssn field is encrypted before being written to MongoDB. The database stores ciphertext, and only properly configured clients can decrypt the value.
While effective for protecting data structurally, CSFLE introduces operational considerations. It requires application-level key management, increases DevOps complexity, and can limit analytics capabilities because encrypted fields are not easily searchable or indexable. It also does not support dynamic policy switching per user role at query time.
Encrypted fields remain unreadable without decryption keys, but encryption decisions are static and embedded into application workflows. Once a client has decryption rights, the full value is revealed.
Core Capabilities of DataSunrise for Dynamic Masking in MongoDB
DataSunrise extends MongoDB with autonomous, policy-driven protection that operates transparently and without application changes. Its dynamic masking architecture is designed to enforce real-time security controls while preserving performance, usability, and data integrity. Below are the core capabilities that define how DataSunrise enhances MongoDB environments.
Autonomous Zero-Touch Dynamic Masking
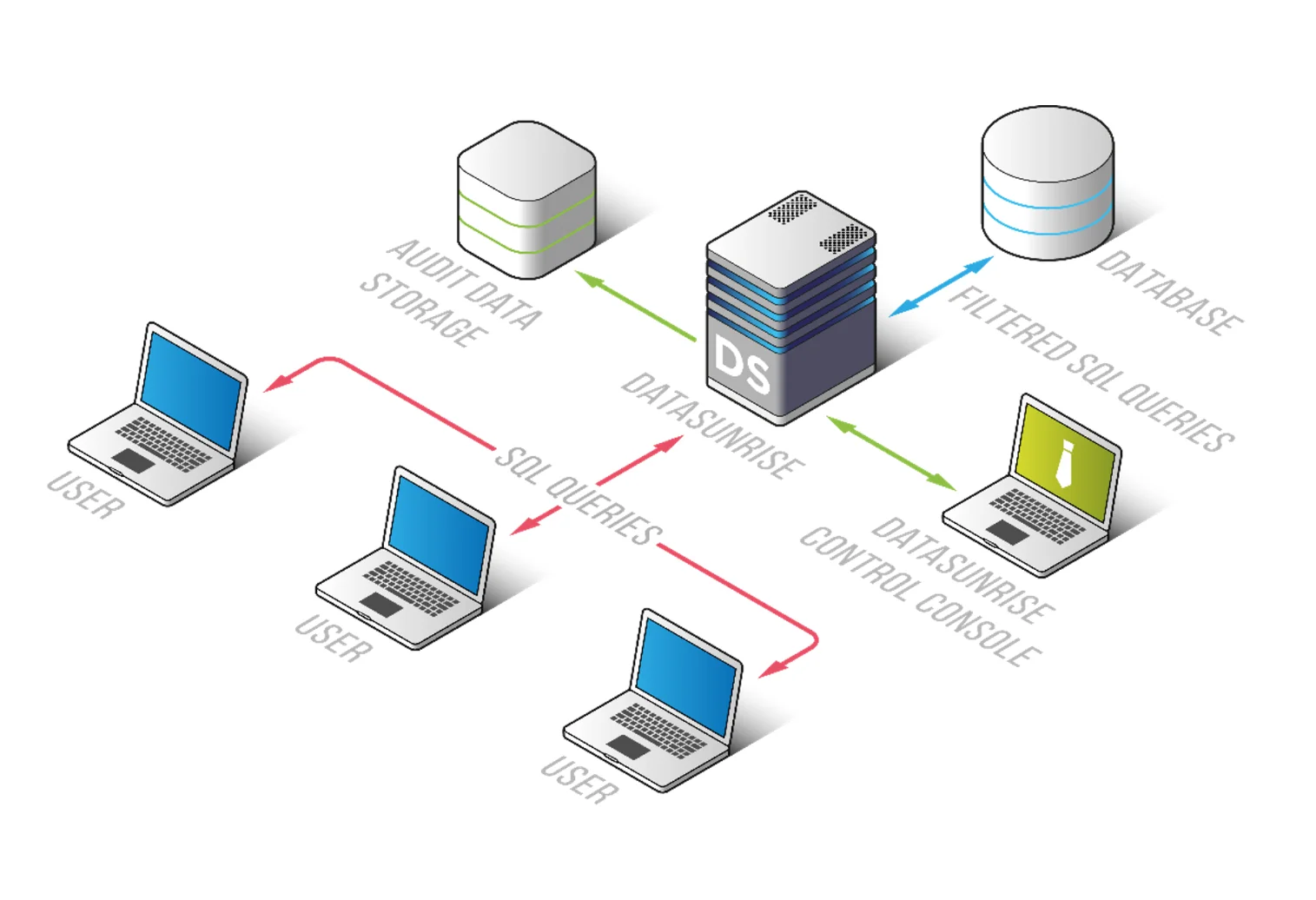
DataSunrise enforces masking policies at the proxy layer, which eliminates the need to modify queries, application code, or database schema. Instead of embedding redaction logic inside services or rewriting aggregation pipelines, masking is applied transparently as queries pass through the security layer.
Sensitive fields are transformed in real time based on contextual conditions such as user identity, role, source IP address, query type, or time-based access rules. This enables precise, context-aware protection aligned with Zero-Trust Data Access principles.
Importantly, masking is applied dynamically while original values remain intact in storage. No data is overwritten, altered, or destructively modified. This ensures operational continuity, preserves data integrity, and allows privileged users to access full values when authorized.
Flexible, Non-Intrusive Deployment Modes
DataSunrise integrates seamlessly into existing infrastructures without disrupting production workloads. It supports Proxy Mode, Sniffer Mode, and Native Log Trailing Mode, allowing organizations to select the most appropriate integration model based on architecture and compliance requirements.
These deployment options enable consistent protection across on-premises environments, AWS, Azure, and hybrid infrastructures. Because integration does not require database restructuring or code modification, organizations can deploy security controls without introducing operational complexity.
Automated Sensitive Data Discovery
Before applying masking, DataSunrise performs intelligent discovery across structured and semi-structured datasets. This automated analysis identifies sensitive data fields that require protection.
Capabilities include pattern-based detection, NLP-powered classification, machine learning-based identification, and OCR scanning for sensitive text within unstructured content. This ensures comprehensive visibility into regulated information across the environment.
As a result, organizations can accurately detect PII such as Social Security numbers, passport identifiers, credit card numbers, and medical records while significantly reducing manual oversight and configuration effort.
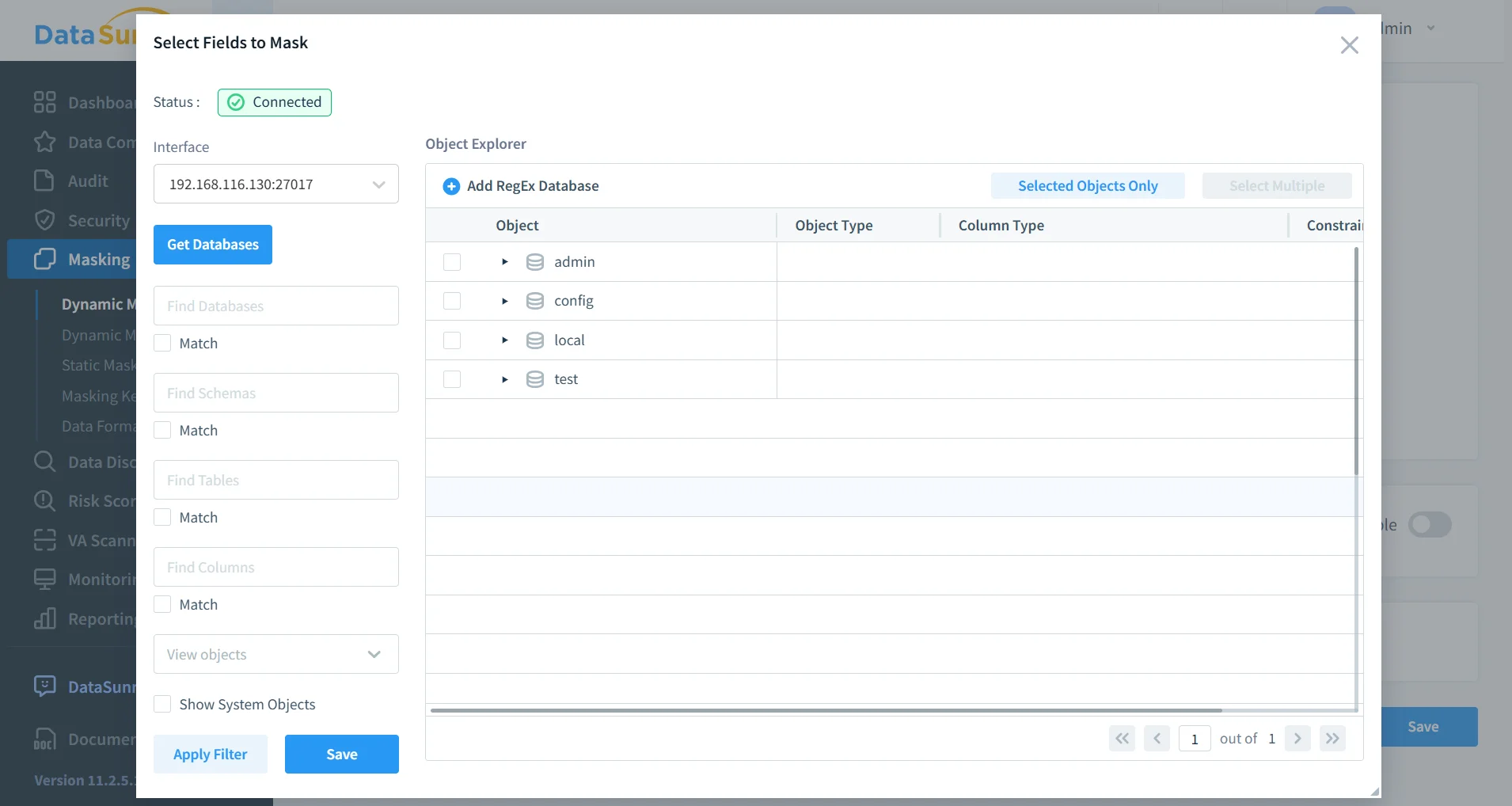
Granular Policy Orchestration
Dynamic masking rules in DataSunrise can be defined with fine-grained precision. Policies can specify database and collection scope, individual fields such as ssn or credit_card, masking types including partial redaction, randomized substitution, format-preserving masking, or full null replacement, and conditional enforcement based on identity or role.
Policies are centrally managed and consistently enforced across environments, ensuring standardized protection without requiring distributed configuration in each application or microservice.
Compliance Autopilot and Regulatory Alignment
DataSunrise automates regulatory mapping and enforcement across frameworks such as GDPR, HIPAA, PCI DSS, SOX, ISO 27001, and NIST. Instead of manually aligning database controls with compliance requirements, security teams generate policies automatically and maintain continuous oversight through built-in monitoring.
The platform supports automatic policy generation, continuous compliance drift detection, and one-click audit evidence reporting. As a result, organizations shorten regulatory preparation cycles and strengthen their audit defensibility.
Unified Security and Monitoring Framework
Dynamic masking functions within a broader security architecture. It integrates directly with database activity monitoring, user behavior analytics, real-time alerting systems, and machine learning–driven audit rules.
Together, these components form a centralized, enterprise-grade framework that delivers context-aware masking, proactive threat detection, behavioral anomaly monitoring, and audit-ready reporting from a single control layer.
Unlike fragmented tools that demand constant manual tuning, DataSunrise provides autonomous protection across MongoDB and heterogeneous data environments, ensuring consistent governance at scale.
Business Impact of Dynamic Masking in MongoDB
| Business Area | Impact of Autonomous Dynamic Masking |
|---|---|
| Breach Risk Management | Reduces breach impact exposure by preventing full sensitive values from being displayed to unauthorized users. |
| Compliance Operations | Significantly decreases manual compliance effort through centralized policy enforcement and automated controls. |
| Audit Readiness | Accelerates audit preparation cycles with structured, policy-driven masking and reporting consistency. |
| Insider Threat Mitigation | Minimizes insider data leakage risk by enforcing context-aware field transformation at runtime. |
| Operational Efficiency | Improves productivity across development, analytics, and support teams by maintaining data usability while protecting sensitive fields. |
Dynamic masking transforms sensitive data governance from reactive remediation to proactive, policy-driven control, reducing exposure without disrupting business workflows.
Conclusion
MongoDB delivers strong foundational security controls. However, its native capabilities do not provide centralized, policy-driven dynamic masking at runtime.
DataSunrise closes this gap with Zero-Touch Data Masking, Compliance Autopilot, Autonomous Compliance Orchestration, Continuous Regulatory Calibration, and centralized policy management designed for modern regulated environments.
By combining dynamic data masking, advanced database activity monitoring, integrated data compliance management, and a unified database security framework, organizations gain precise control over how sensitive data is exposed, accessed, and monitored.
Organizations can deploy these capabilities across on-premise, cloud, and hybrid infrastructures without rewriting applications or redesigning database architecture.
Explore the full platform capabilities or request a live demonstration to see enterprise-ready dynamic masking for MongoDB in action.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now