How to Apply Static Masking in MariaDB
As databases increasingly support analytics, testing, reporting, and development workloads, production data often moves beyond tightly controlled environments. As a result, teams must protect sensitive information such as personal identifiers, financial records, or contact details while preserving schema integrity and application logic.
To address this challenge, static data masking permanently transforms sensitive values before teams share, export, or replicate data. Unlike runtime controls, static masking changes the data itself and, therefore, ensures that exposed datasets remain safe by design.
This article explains how teams can apply static masking in MariaDB. In addition, it outlines common native techniques and shows how centralized platforms such as DataSunrise extend static masking into a policy-driven, auditable, and compliance-aligned process.
What Is Static Data Masking?
Static data masking irreversibly transforms sensitive data values and stores the masked results either in place or in a separate dataset. After masking, teams cannot reconstruct original values from the transformed data. Consequently, organizations use this approach as a core technique within broader data masking strategies to protect sensitive information outside production systems.
Common static masking use cases include:
- Preparing production-like datasets for development and QA as part of structured test data management workflows
- Sharing data with third-party vendors or offshore teams without exposing regulated fields
- Creating compliance-safe backups or archives to meet regulatory requirements
- Supporting analytics while avoiding exposure of regulated information such as personally identifiable information
Because teams apply masking before data access occurs, static masking removes reliance on runtime enforcement. As a result, it significantly reduces the risk of accidental disclosure caused by misconfigured permissions or access controls.
Native Static Masking Options in MariaDB
MariaDB does not provide a dedicated static masking engine. However, administrators often rely on SQL-level techniques to approximate static masking behavior.
Views with Transformed Columns
One common approach is to expose masked values through views:
/*CREATE VIEW masked_customers AS
SELECT
id,
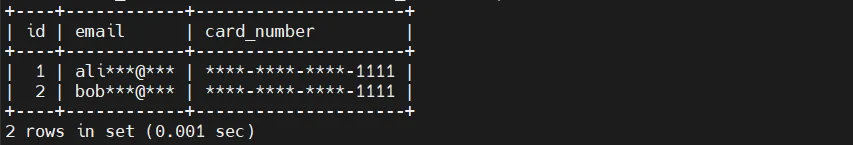
CONCAT(SUBSTRING(email, 1, 3), '***@***') AS email,
'****-****-****' AS card_number
FROM customers;*/
This method allows applications or users to query masked representations of data without modifying base tables.
Update-Based In-Place Masking
Another approach is to overwrite sensitive values directly using UPDATE statements:
/*UPDATE customers
SET email = CONCAT(SUBSTRING(email, 1, 3), '***@masked.local');*/
This technique permanently replaces original values and is often used when preparing non-production copies of data.
Masked Copies for Non-Production Use
Teams may also create separate masked tables or schemas during data replication:
/*INSERT INTO customers_masked
SELECT
id,
SHA2(email, 256),
NULL
FROM customers;*/
This approach keeps production data intact while supplying masked datasets for testing or analytics.
Static Masking in MariaDB with DataSunrise
DataSunrise enables centralized, rule-based static masking for MariaDB, removing dependence on application logic or manual SQL scripts. Masking policies are defined once and reused across environments, turning static masking into a controlled and repeatable process aligned with broader data masking practices.
Because masking operates outside the database engine, production schemas and applications remain unchanged while compliance-safe datasets are generated for secondary use, supporting secure test data management workflows.
Automated Sensitive Data Discovery
Before masking is applied, DataSunrise automatically scans MariaDB schemas to detect sensitive data based on column metadata, naming patterns, and content analysis. This discovery process is part of a broader data discovery capability that ensures sensitive fields are identified even as schemas evolve or new tables appear.
Discovered data is classified into categories such as personal, financial, or healthcare-related information, including personally identifiable information, providing a consistent foundation for masking policies.
Rule-Based Static Masking by Data Type
Instead of configuring masking rules for individual columns, DataSunrise applies policies at the data category level. Once defined, rules automatically cover all matching fields across databases and schemas.
- Centralized masking rules defined once and reused across environments
- Automatic coverage of new tables and columns as schemas evolve
- Consistent masking behavior across multiple databases and schemas
- Reduced manual effort compared to column-level SQL configuration
Typical transformations include synthetic email substitution, phone number tokenization, irreversible hashing of identifiers, and format-preserving masking of financial values. Masking follows the data itself, not static schema definitions, which simplifies long-term policy maintenance.
Controlled Masking Workflows
Static masking is applied during defined workflows such as database cloning, backup restoration, data export, or test data provisioning. This approach ensures sensitive values are transformed before data leaves protected environments and complements broader data security controls.
- Masking applied only during approved data movement operations
- Clear separation between production and non-production datasets
- Predictable and repeatable masking execution
- Reduced risk of accidental exposure during data sharing
Auditable Masking Operations
All masking operations are logged and traceable. Audit records show which datasets were masked, which rules were applied, when masking occurred, and who initiated the operation. This visibility integrates static masking into a unified database activity monitoring and governance process.
- Complete visibility into masking execution history
- Traceability of masking rules and affected datasets
- Clear accountability for manual and automated operations
- Audit-ready evidence for internal reviews and compliance checks
Compliance and Risk Reduction
Static masking supports regulations such as GDPR, HIPAA, PCI DSS, and SOX by permanently removing sensitive values from non-production datasets. When combined with centralized classification and reporting in DataSunrise, static masking becomes a verifiable compliance control rather than an informal practice.
Business Impact of DataSunrise
| Business Area | Impact |
|---|---|
| Data exposure risk | Significantly reduced risk of sensitive data leakage outside protected environments |
| Development & testing | Faster delivery of compliance-safe, production-like datasets for non-production use |
| Audit readiness | Clear, auditable evidence of masking controls during regulatory and internal audits |
| Operational efficiency | Lower operational overhead compared to manual, script-based masking approaches |
| Security assurance | Stronger confidence that sensitive data remains protected across its entire lifecycle |
Conclusion
MariaDB offers flexible SQL capabilities that allow teams to implement basic static masking techniques. However, as data environments scale, masking requirements quickly extend beyond isolated scripts and manual workflows, especially when databases become part of broader data security and compliance programs.
By introducing automated discovery, rule-based masking, and auditable execution, DataSunrise transforms static masking into a centralized and repeatable process aligned with modern security and compliance expectations, including structured data compliance workflows.
For organizations treating non-production data as part of their regulated surface, static masking is not an optional enhancement—it is a foundational control.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now