How to Ensure Compliance for Amazon DynamoDB
Introduction
Ensuring compliance for Amazon DynamoDB requires more than enabling encryption and turning on infrastructure logs. DynamoDB is commonly used to store customer profiles, session data, transactions, and application metadata—much of which qualifies as regulated information under modern data protection frameworks.
While AWS provides strong infrastructure security, regulatory compliance focuses on data access behavior, not just service configuration. Organizations must be able to demonstrate who accessed which items, under what context, and whether that access aligned with internal data security policies and regulatory requirements.
This article explains how compliance works in DynamoDB environments, outlines the limitations of native AWS tooling, and shows how centralized platforms such as DataSunrise enable audit-ready activity monitoring and regulation-aligned compliance for DynamoDB workloads.
What Compliance Means for DynamoDB
Compliance in DynamoDB environments is defined by data interaction visibility, not schema design. Since DynamoDB is a fully managed NoSQL service, organizations do not control the underlying database engine. Instead, compliance depends on observing and governing access paths.
Key compliance expectations include:
- Traceability of read and write operations through structured data activity history
- Attribution of access to identities and applications using role-based access controls
- Protection of sensitive attributes within items, including regulated personal information
- Audit evidence suitable for regulatory review
- Continuous enforcement across environments
These requirements map directly to regulations such as GDPR, HIPAA, PCI DSS, and SOX, all of which emphasize accountability, least-privilege access, and monitoring of data usage rather than infrastructure ownership.
Native AWS Capabilities for DynamoDB Compliance
AWS offers several foundational controls that contribute to DynamoDB compliance, but these controls operate at different architectural layers and address different aspects of security and governance. As a result, they form a baseline rather than a complete compliance framework.
IAM-Based Access Controls
AWS Identity and Access Management (IAM) defines who can access DynamoDB tables and which operations they are allowed to perform. IAM policies can restrict actions such as GetItem, PutItem, and Scan, and scope permissions to specific tables, indexes, or AWS resources.
Below is a simplified IAM policy example that allows read-only access to a specific DynamoDB table:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"dynamodb:GetItem",
"dynamodb:Query",
"dynamodb:Scan"
],
"Resource": "arn:aws:dynamodb:us-east-1:123456789012:table/CustomerProfiles"
}
]
}
While IAM is effective for enforcing least-privilege access at the API level, it does not provide visibility into actual data usage. IAM does not record which attributes within an item were accessed, nor does it capture the data context of read and write operations. From a compliance perspective, this limits its usefulness for demonstrating how regulated data was handled after access was granted.
Encryption and Key Management
Amazon DynamoDB encrypts data at rest by default using AWS-managed or customer-managed keys through AWS Key Management Service. This satisfies baseline encryption requirements defined by most regulatory frameworks and protects data against physical storage compromise.
A DynamoDB table configured with a customer-managed KMS key may look like this:
{
"TableName": "CustomerProfiles",
"SSESpecification": {
"Enabled": true,
"SSEType": "KMS",
"KMSMasterKeyId": "arn:aws:kms:us-east-1:123456789012:key/abcd-1234-efgh-5678"
}
}
However, encryption at rest does not address runtime exposure. Authorized identities can still access and misuse decrypted data during normal operations, and encryption alone does not provide audit visibility or behavioral controls. As a result, encryption is a necessary but insufficient compliance measure on its own.
CloudTrail API Logging
AWS CloudTrail records DynamoDB API calls, including management operations and optional data events. These logs confirm that a request occurred and identify the calling identity, time, and API action.
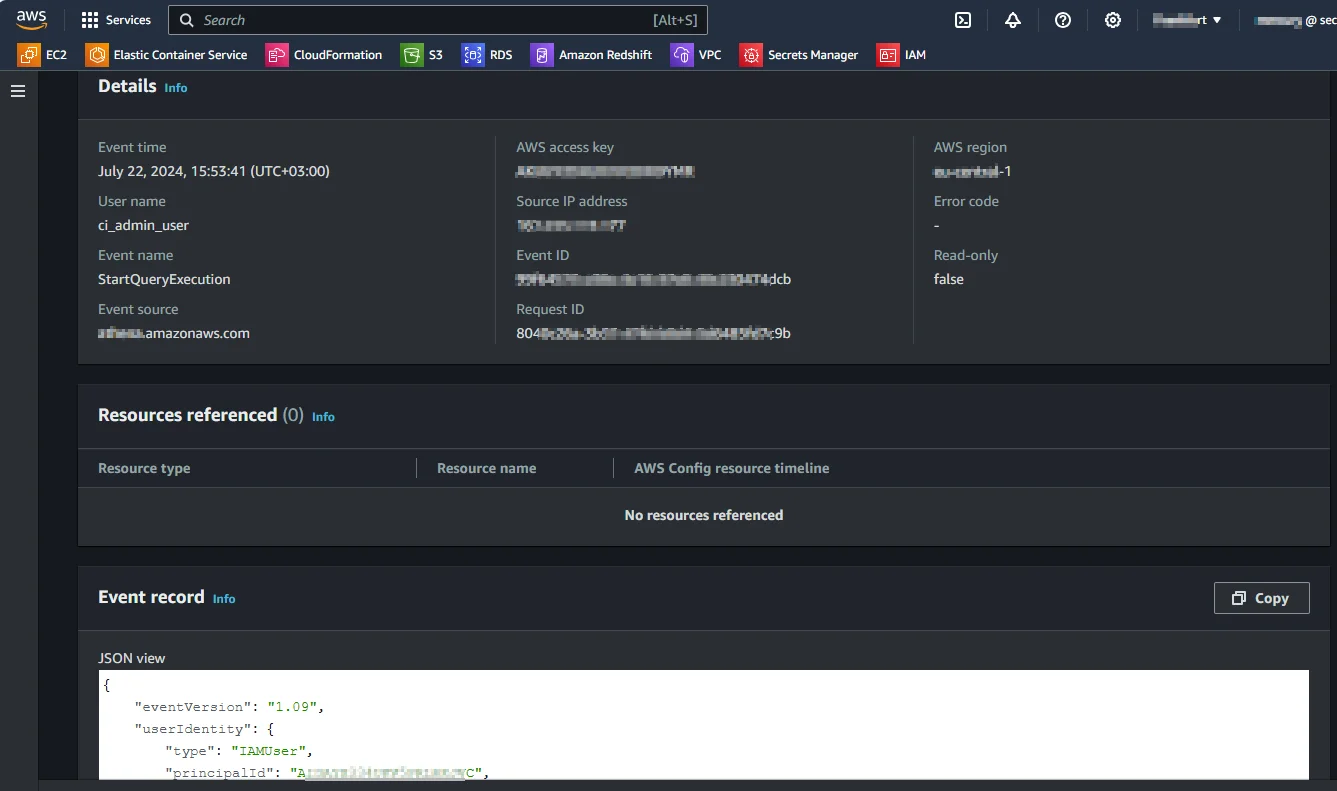
What CloudTrail does not provide is data-level context. It does not show which attributes were accessed, whether sensitive data was involved, or whether the operation aligned with internal compliance policies. CloudTrail logs are also high-volume and low-semantic, requiring significant post-processing to extract compliance-relevant evidence. There is no native mechanism for policy-driven filtering or real-time compliance alerting.
As a result, CloudTrail is valuable for forensic timelines and infrastructure audits, but it is insufficient as a standalone control for demonstrating continuous, regulation-aligned compliance in DynamoDB environments.
Compliance-Aware Activity Monitoring with DataSunrise
DataSunrise introduces compliance-aware monitoring for DynamoDB by observing access paths and applying policy logic at runtime. Instead of relying on raw infrastructure logs, the platform evaluates database activity against regulatory intent and internal governance requirements.
Audit policies are rule-based and aligned with specific compliance goals, allowing organizations to control which operations are monitored and how they are interpreted. Context-aware filtering takes into account operation type, calling identity, and access patterns, enabling fine-grained visibility into how data is actually used. As a result, audit records are structured in a way that supports regulatory review and investigation. Audit logs become actionable compliance artifacts rather than unstructured telemetry that requires extensive manual analysis.
Policy-Driven Protection Across Environments
Compliance and security policies in DataSunrise are centrally managed and environment-agnostic. This is particularly important for DynamoDB-based architectures where the same data models are deployed across development, analytics, and production environments, often spanning multiple AWS accounts or regions.
Policy-driven enforcement ensures that the same controls apply consistently regardless of environment. Security and compliance logic is not embedded into application code, reducing operational coupling and maintenance risk. Centralized policies also minimize the likelihood of misconfiguration as environments scale or change, providing a predictable compliance posture over time. In practice, policies follow the data itself rather than the deployment topology.
- Centralized policies eliminate configuration drift between development, staging, and production DynamoDB environments.
- Environment-agnostic enforcement reduces reliance on application-level controls and custom compliance logic.
- Unified policy management simplifies governance across multiple AWS accounts and regions.
- Consistent controls improve auditability by ensuring identical compliance behavior regardless of deployment scope.
- Predictable policy behavior lowers operational risk as DynamoDB architectures scale and evolve.
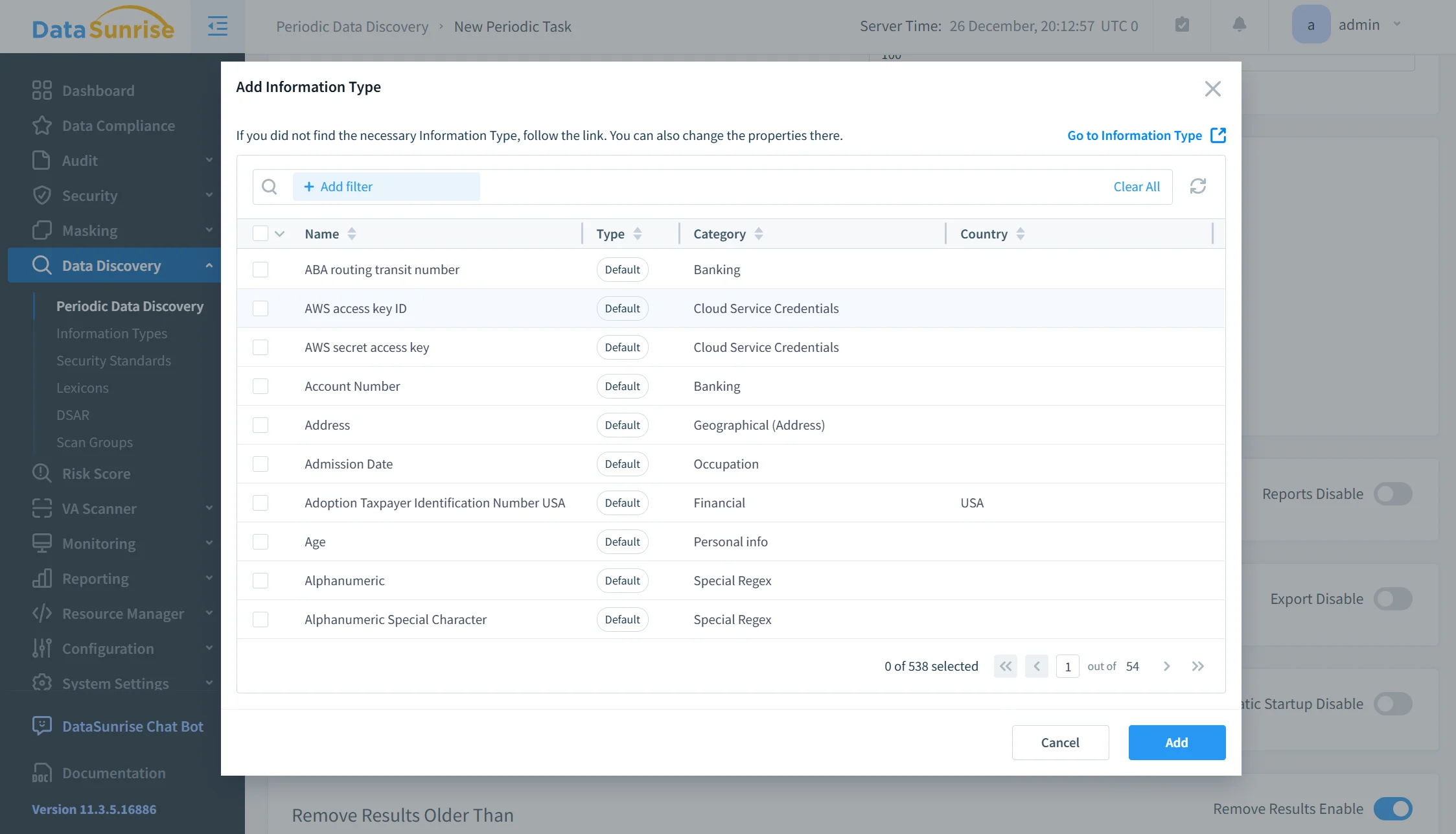
Sensitive Data Protection for DynamoDB Workloads
DynamoDB tables frequently contain personal, financial, and operational data that must be protected at the attribute level. DataSunrise supports sensitive data discovery and protection workflows that go beyond simple access denial and coarse-grained permission models.
The platform identifies regulated data elements such as PII and other sensitive fields, applies context-aware data masking where appropriate, and controls exposure based on user role and access purpose. These protections are designed to preserve application behavior and query logic, allowing production data to be reused safely for analytics, support, or troubleshooting without violating privacy obligations.
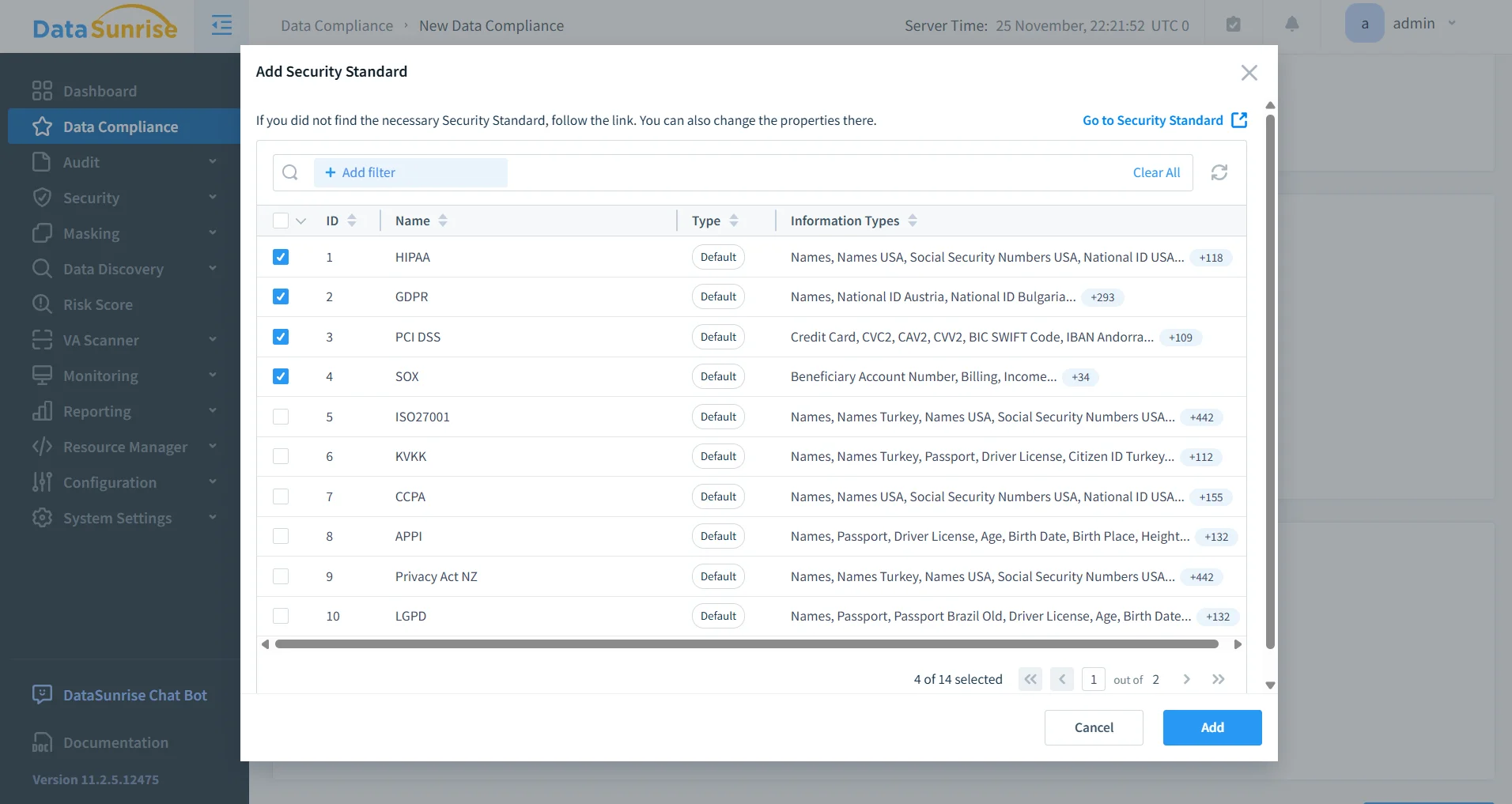
Regulatory Alignment and Audit Readiness
DataSunrise automates regulatory alignment by correlating observed activity patterns with specific compliance requirements. Built-in compliance logic supports major regulatory frameworks, including GDPR, HIPAA, PCI DSS, and SOX, enabling organizations to maintain continuous alignment rather than periodic, manual checks.
Automated reporting transforms audit preparation into a repeatable process. Compliance teams can generate audit-ready documentation directly from structured audit records, eliminating the need to reconstruct timelines from fragmented infrastructure logs and significantly reducing the operational cost of compliance.
Business Impact of Centralized DynamoDB Compliance
| Impact Area | Operational Effect |
|---|---|
| Audit preparation | Reduced audit preparation time through automated, structured compliance reporting |
| Regulatory risk | Lower risk of regulatory findings due to continuous, policy-driven enforcement |
| Data visibility | Improved visibility into how DynamoDB data is accessed and used across services |
| Accountability | Clear attribution of data access to users, roles, and applications |
| Incident response | Faster investigation and response through centralized, searchable audit records |
Centralized compliance transforms DynamoDB governance from reactive evidence collection into proactive, continuous risk control.
Conclusion
Amazon DynamoDB provides secure, scalable infrastructure, but regulatory compliance does not stop at infrastructure security. While native AWS controls handle access management, encryption, and basic logging, compliance requires deeper visibility into how data is actually used, especially in the context of modern data compliance regulations.
DataSunrise extends DynamoDB environments with compliance-aware activity monitoring, centralized policy enforcement, and audit-ready compliance reporting. By transforming raw activity into structured compliance evidence, organizations can meet regulatory expectations without slowing down cloud-native development.
For teams operating DynamoDB in regulated environments, compliance is no longer a documentation burden—it becomes a built-in operational capability aligned with continuous database security practices.
