How to Ensure Compliance for IBM Db2
Introduction
Compliance is the process of aligning database operations with laws, regulations, and industry standards that govern sensitive data. Failing to meet these requirements can result in penalties, reputational damage, and security incidents.
IBM Db2 is a relational database platform used in finance, healthcare, government, and many other industries where strict compliance is mandatory. Ensuring compliance for Db2 means combining native features with specialized tools to secure data, track activity, and generate audit-ready evidence.
Compliance Frameworks That Matter
For teams managing Db2, regulations are not just abstract rules — they directly shape how databases must be configured and monitored.
- GDPR requires organizations to locate and minimize the use of personal data from EU citizens. For Db2, this often means discovering where PII is stored and enforcing masking for analysts.
- HIPAA obligates healthcare providers to safeguard patient health records. Db2 deployments in hospitals need row-level access control so clinicians only see their patients’ information.
- PCI DSS defines strict controls around cardholder data. Payment processors running Db2 must log every access to credit card tables and use encryption and masking to prevent leaks.
- SOX enforces accountability in financial reporting. In practice, Db2 administrators must capture schema changes and maintain audit trails that link activity back to individuals.
By translating these frameworks into database-level requirements, organizations can turn abstract compliance obligations into concrete technical measures inside Db2.
Native Db2 Capabilities for Compliance
Db2 includes several features that help address compliance requirements:
1. Enable and Review Auditing
Db2 provides built-in administrative views that allow administrators to monitor activity in real time. One useful query shows who is connected and how much work each session has done:
SELECT
APPLICATION_NAME,
SESSION_AUTH_ID,
TOTAL_APP_COMMITS,
APP_RQSTS_COMPLETED_TOTAL
FROM SYSIBMADM.MON_CONNECTION_SUMMARY;
This output reveals which applications are active, which users are connected, and how many requests they have completed.
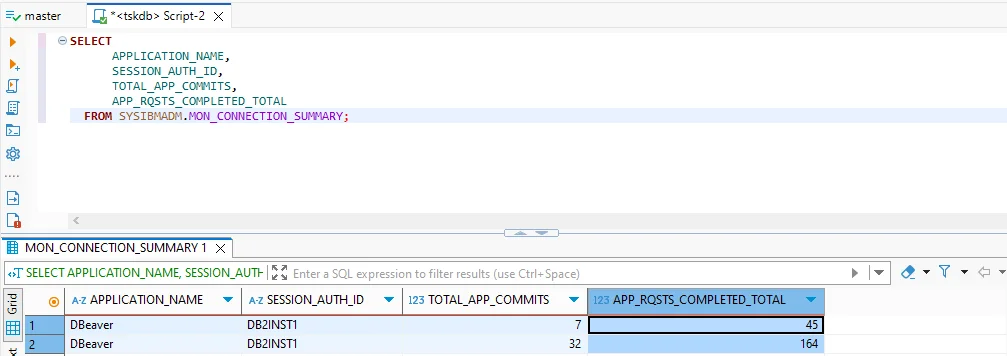
2. Control User Access
Db2 supports Row and Column Access Control (RCAC) to enforce least-privilege access:
ALTER TABLE patients ACTIVATE ROW ACCESS CONTROL;
CREATE PERMISSION doctor_only
ON patients
FOR ROWS WHERE CURRENT USER = doctor_id
ENFORCED FOR ALL ACCESS
ENABLE;
This ensures doctors see only their patients’ records — an essential step for HIPAA compliance.
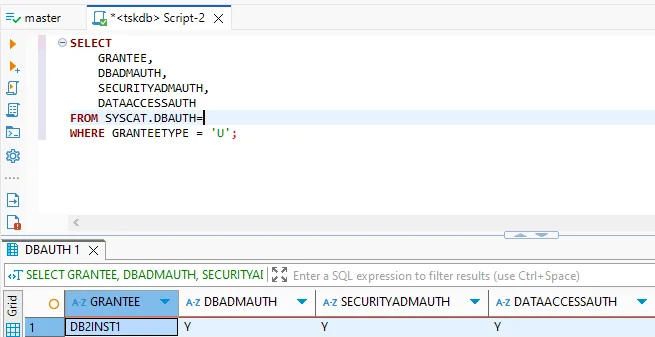
3. Monitor Privileges and Sessions
Built-in catalog views provide insight into who has elevated roles:
SELECT GRANTEE, DBADMAUTH, SECURITYADMAUTH, DATAACCESSAUTH
FROM SYSCAT.DBAUTH
WHERE GRANTEETYPE = 'U';
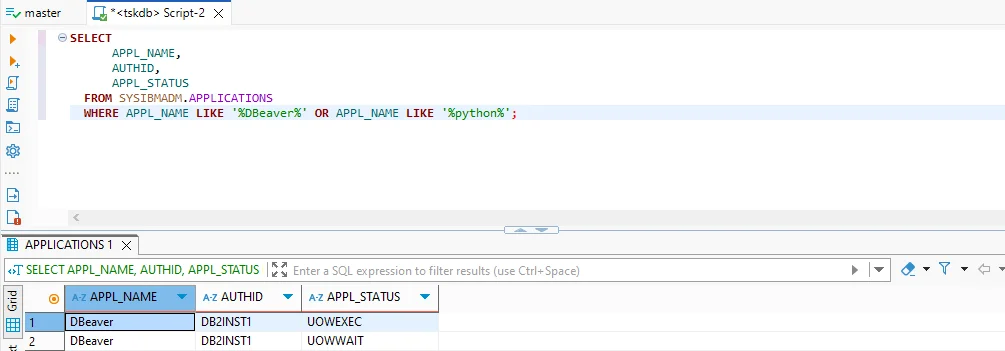
Monitoring active connections is also critical:
SELECT APPLICATION_NAME, SESSION_AUTH_ID, TOTAL_APP_COMMITS
FROM SYSIBMADM.MON_CONNECTION_SUMMARY;
Gaps in Native Compliance
Db2 lays a strong foundation, but several gaps remain:
| Gap | Why It Matters |
|---|---|
| No dynamic data masking | Sensitive fields like card numbers or medical records remain fully visible to anyone with query access, raising insider threat and data leak risks. |
| No automated discovery of PII/PHI | Regulated data may sit unnoticed across schemas and tables. Without scanning, admins can miss exposures, leading to audit failures. |
| Complex db2audit logs | Raw audit output is hard to parse at scale. Teams struggle to produce clear evidence quickly, slowing audits and increasing compliance costs. |
| No centralized compliance management | Each Db2 instance must be configured separately. In large or hybrid environments, this causes inconsistent policies and blind spots in oversight. |
How DataSunrise Ensures Compliance for Db2
DataSunrise is a database security and compliance platform that integrates with Db2 without requiring application code changes. It extends compliance by providing:
- Unified audit trails: Db2 activity can be consolidated with logs from other platforms in a single dashboard, with alerts and evidence available through the DataSunrise audit solution.
- Dynamic data masking: Sensitive values such as credit card numbers or diagnoses are hidden in real time, enforced by role-based rules defined in the dynamic masking module.
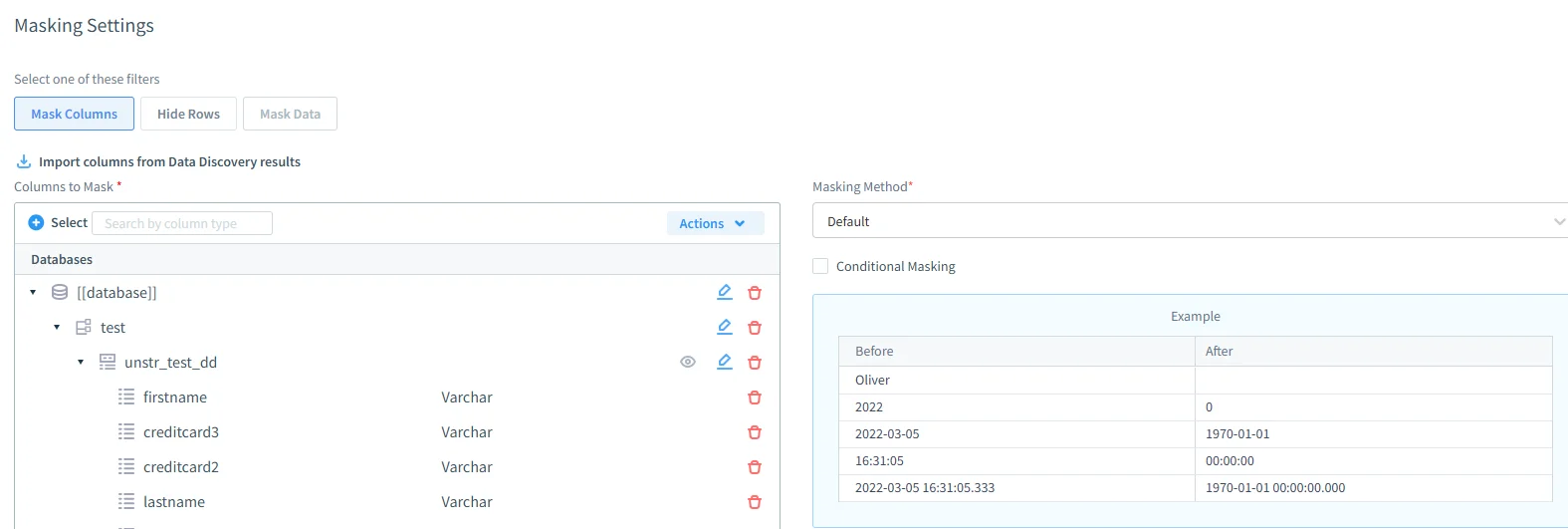
DataSunrise masking settings interface for configuring column-level dynamic masking with before-and-after value examples. - Sensitive data discovery and classification: PII and PHI are automatically located across Db2 schemas, a capability built into the DataSunrise discovery engine.
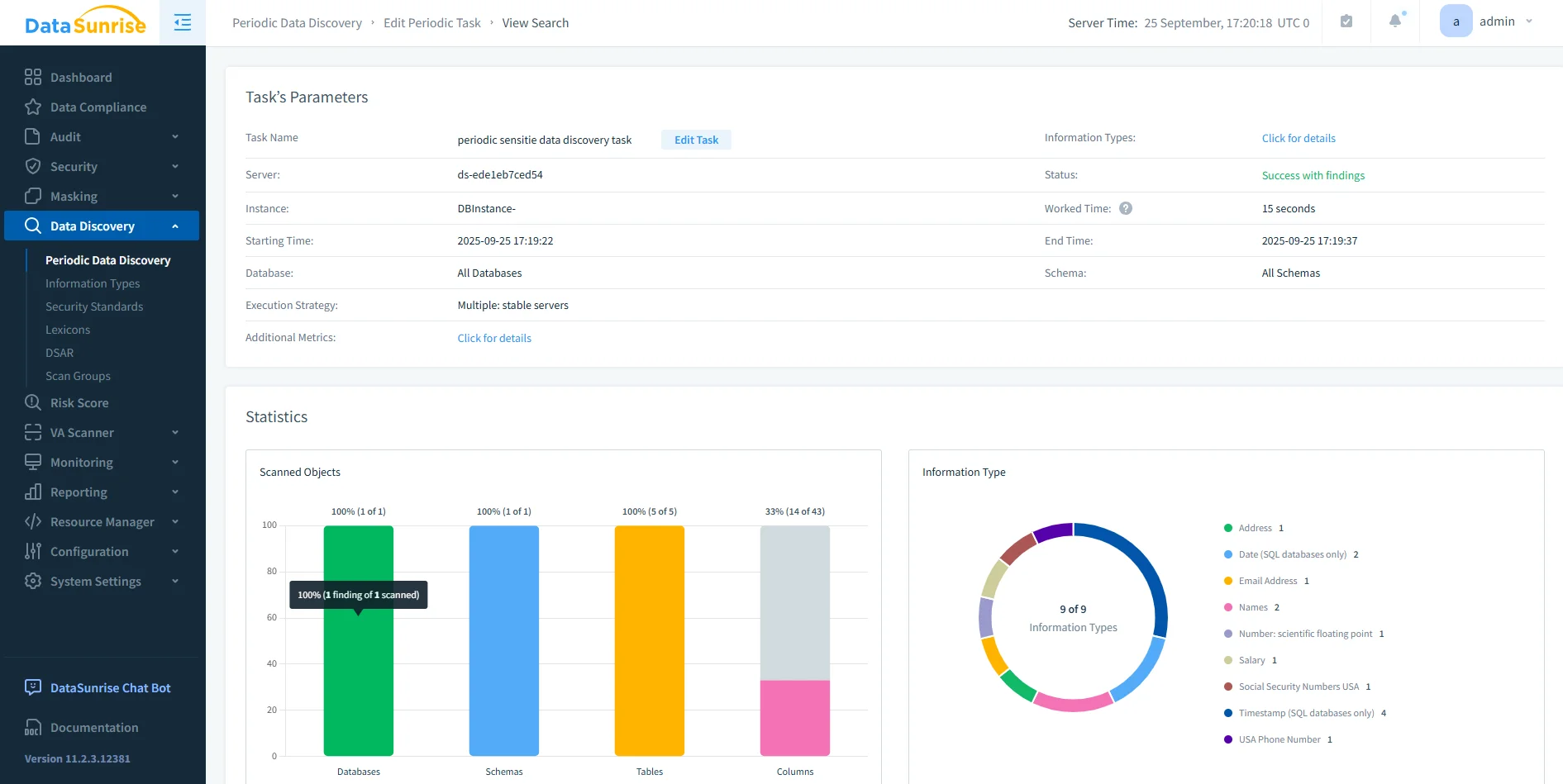
DataSunrise data discovery dashboard showing task parameters, scan statistics, and detected sensitive data types across schemas and tables. - Automated compliance reporting: Audit-ready PDF or HTML reports are produced in one click with the DataSunrise compliance reporting tool.
Best Practices for Db2 Compliance
Ensuring Db2 compliance goes beyond enabling features. Organizations should adopt processes that keep compliance effective and sustainable:
- Centralize and retain logs: Move audit files into a secure repository with retention policies that match regulations.
- Review roles regularly: Schedule periodic access reviews to confirm least-privilege access.
- Automate reporting: Use tools like DataSunrise to generate scheduled compliance reports.
- Test compliance readiness: Run internal audits before external reviews to catch issues early.
- Integrate with SIEM: Send Db2 audit data into security monitoring systems for real-time detection.
Comparison Table
| Feature | Db2 Native | With DataSunrise |
|---|---|---|
| Audit Logging | ✅ db2audit | ✅ Centralized with dashboards and alerts |
| Access Controls | ✅ RCAC, LBAC | ✅ Extended with role-aware masking |
| Data Discovery | ❌ Manual inspection | ✅ Automated scanning & classification |
| Compliance Reporting | ❌ | ✅ One-click PDF/HTML reports |
| Multi-DB Support | ❌ Db2 only | ✅ Unified across hybrid environments |
Conclusion
Ensuring compliance for Db2 requires both technical controls and disciplined processes. Native features such as auditing, RCAC, and LBAC provide a solid foundation, but they do not fully address the challenges of managing sensitive data in highly regulated industries.
When organizations rely only on built-in capabilities, they face risks such as incomplete visibility into sensitive data, difficulty producing audit-ready evidence, and inconsistent policy enforcement across multiple environments. These shortcomings can increase the chance of audit findings, data leaks, and costly remediation efforts.
DataSunrise closes these gaps by adding real-time data masking, automated discovery of PII and PHI, streamlined reporting, and unified compliance dashboards across hybrid and multi-database environments. This not only reduces administrative overhead but also improves confidence during regulatory audits.
Ultimately, compliance is not a one-time configuration—it is an ongoing practice. Combining Db2’s built-in features with DataSunrise’s advanced compliance capabilities and adopting best practices such as centralized logging and regular access reviews allows organizations to maintain a proactive and resilient compliance posture.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now