How to Manage Data Compliance for IBM Db2
Introduction
Data compliance management is the ongoing process of ensuring that sensitive information is collected, stored, and used in accordance with regulations and internal policies. It is not just about meeting requirements once but about maintaining oversight, proving accountability, and adapting controls as environments evolve.
IBM Db2 is widely used in industries where compliance is critical, such as healthcare, finance, and government. Managing compliance for Db2 means more than turning on auditing or encryption — it requires daily monitoring, consistent enforcement, and accessible evidence for auditors.
Core Activities in Data Compliance Management
Effective compliance management depends on daily activities that keep Db2 environments aligned with obligations:
- Monitoring access: Administrators must know who connected, what queries ran, and whether actions touched sensitive data.
- Controlling exposure: Db2’s Row and Column Access Control (RCAC) and Label-Based Access Control (LBAC) enforce least privilege, while masking solutions reduce exposure risk.
- Maintaining evidence: Logs, audit trails, and reports serve as proof of compliance and must be available at short notice.
- Adapting policies: As applications evolve and new data sources appear, compliance controls must adjust without creating blind spots.
These activities form the backbone of compliance management, even before external audits take place.
Native Db2 Capabilities in Compliance Management
Db2 provides several built-in features that support compliance activities:
- Auditing: The
db2auditutility records activity such as logins and schema changes.
db2audit configure scope all status both
db2audit start
db2audit extract delasc to /tmp/db2audit_logs
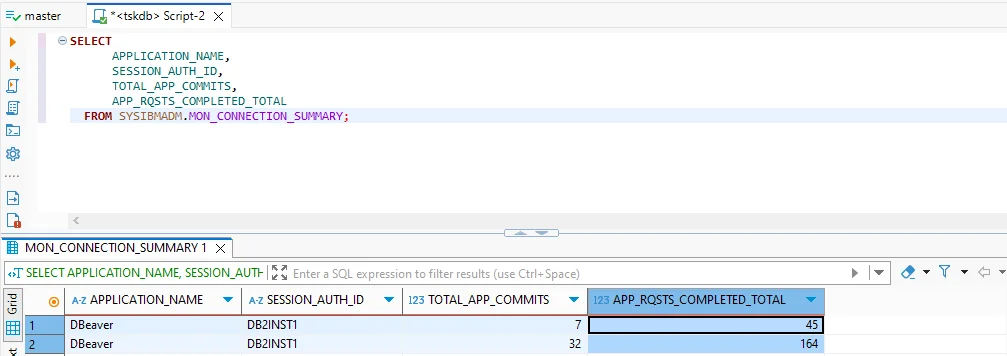
- Monitoring sessions: The
SYSIBMADM.MON_CONNECTION_SUMMARYview shows current connections, including applications and user IDs.
SELECT
APPLICATION_NAME,
SESSION_AUTH_ID,
TOTAL_APP_COMMITS,
APP_RQSTS_COMPLETED_TOTAL
FROM SYSIBMADM.MON_CONNECTION_SUMMARY;
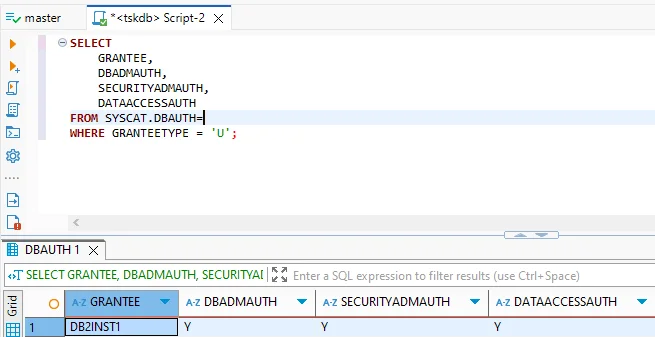
- Privilege review: The
SYSCAT.DBAUTHview helps administrators identify which accounts hold elevated rights.
SELECT
GRANTEE,
DBADMAUTH,
SECURITYADMAUTH,
DATAACCESSAUTH
FROM SYSCAT.DBAUTH
WHERE GRANTEETYPE = 'U';
- Access enforcement: RCAC and LBAC restrict data visibility by row, column, or label, ensuring users see only what they are authorized to see.
- Encryption and recovery: Protect data at rest and ensure continuity after incidents.
These features give Db2 administrators strong tools for compliance but still require significant effort to manage effectively.
Management Gaps and Risks
When management processes break down, native Db2 tools reveal important weaknesses.
| Task | Db2 Native Tool | Management Risk |
|---|---|---|
| Audit collection | db2audit logs | Logs are detailed but stored locally, making evidence slow to assemble for auditors |
| Access enforcement | RCAC / LBAC | Restrict access but do not mask sensitive data, exposing full values to insiders |
| Session monitoring | SYSIBMADM views | Provide real-time visibility but lack historical retention across instances |
| Privilege review | SYSCAT.DBAUTH | Requires manual checks, risking unnoticed privilege creep over time |
| Evidence reporting | Manual log parsing | No native reporting; teams spend days assembling compliance evidence |
These risks turn technical safeguards into operational challenges, especially in multi-instance or hybrid Db2 deployments.
Managing Compliance Effectively with DataSunrise
DataSunrise acts as a compliance management layer on top of Db2, enhancing oversight, control, and efficiency. It integrates transparently without changing application code.
- Monitor & Alert: The audit solution consolidates Db2 logs from multiple instances into centralized dashboards. Alerts highlight unusual queries or privilege changes, helping teams act quickly.
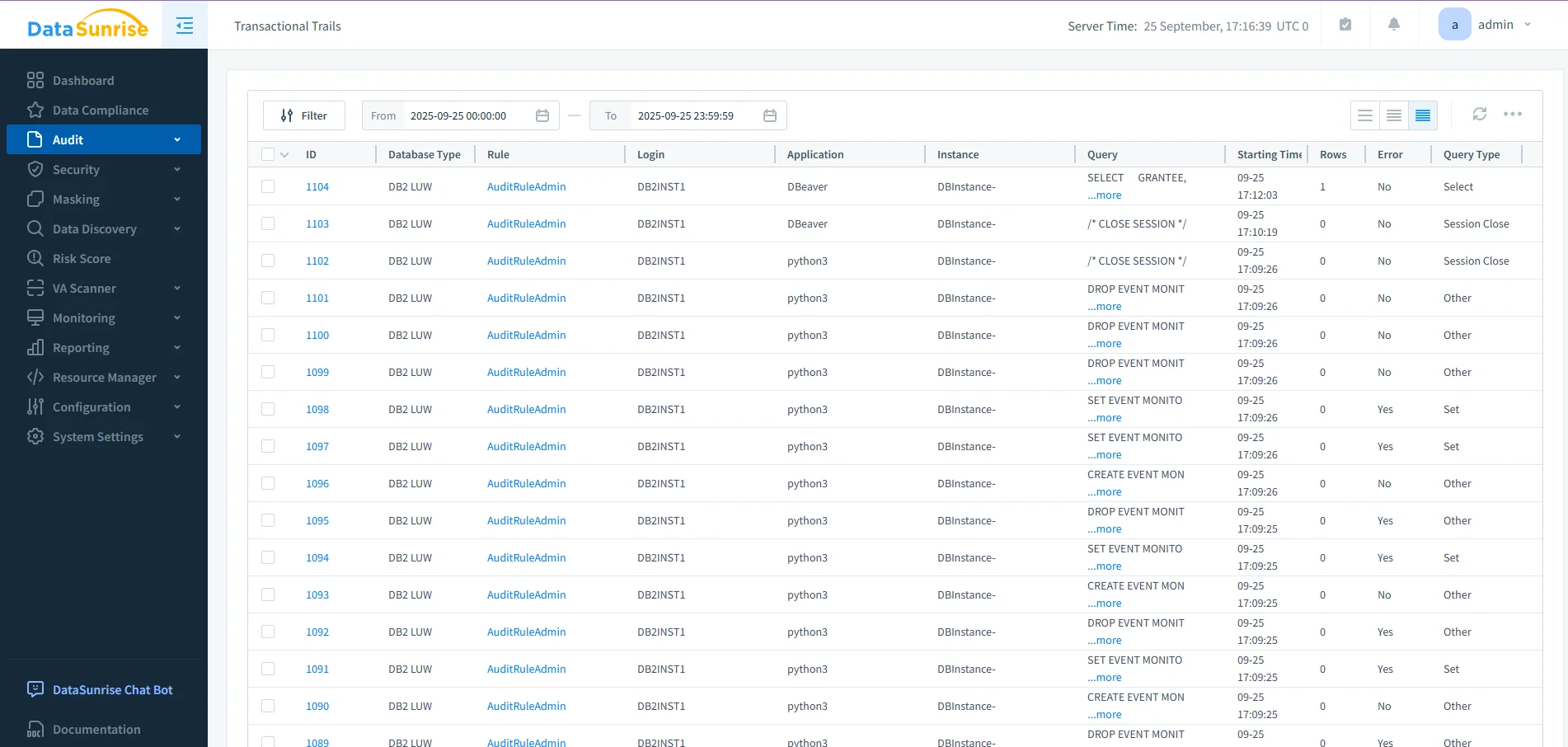
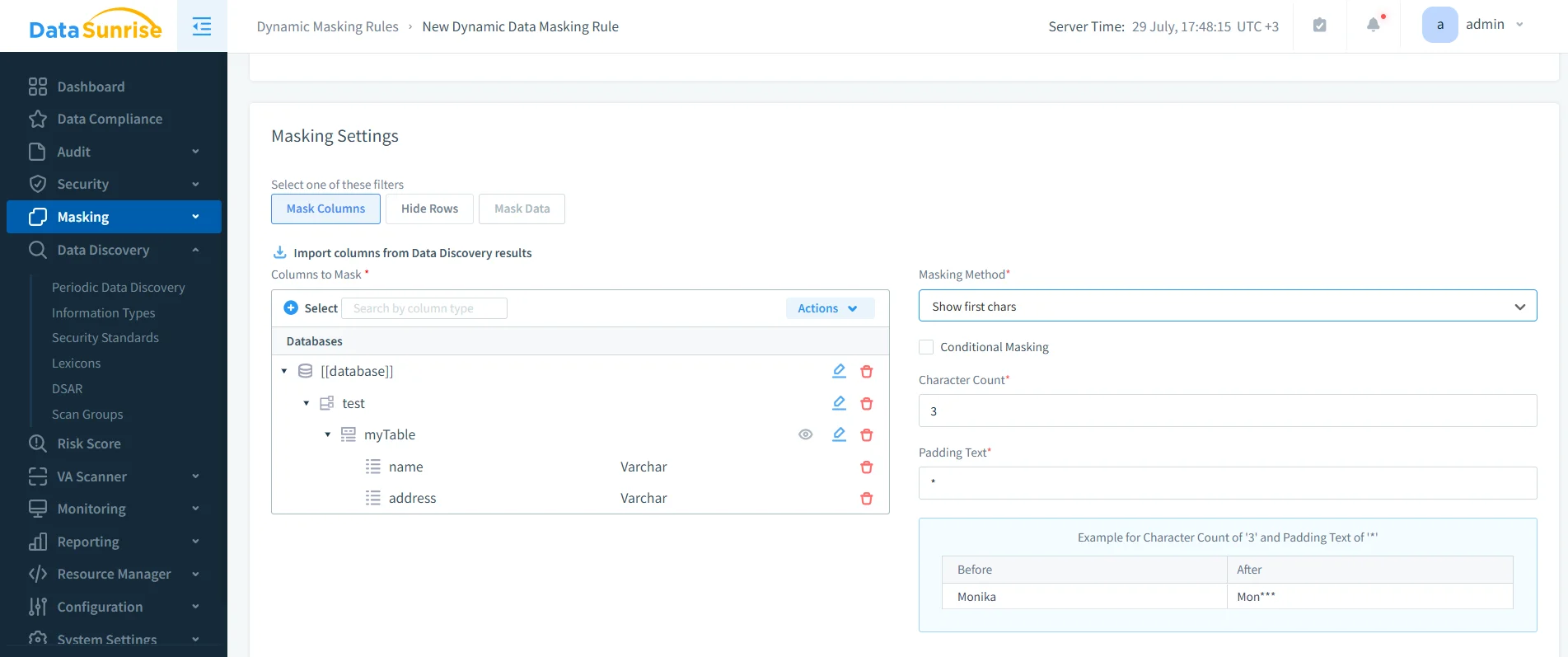
DataSunrise audit dashboard displaying Db2 LUW transactional trails, listing queries, logins, applications, timestamps, and query types for compliance review. - Protect & Control: Dynamic data masking enforces access rules by hiding sensitive values in real time, while data discovery automatically locates PII or PHI that administrators might miss.
DataSunrise masking configuration screen showing a dynamic masking rule applied to specific table columns with a “show first characters” method. - Document & Report: DataSunrise includes tools for regulatory compliance alignment and a reporting module that generate clear PDF or HTML reports. Organizations can map these capabilities to the standards they follow — whether GDPR, HIPAA, PCI DSS, or SOX — and provide auditors with structured evidence instead of raw logs.
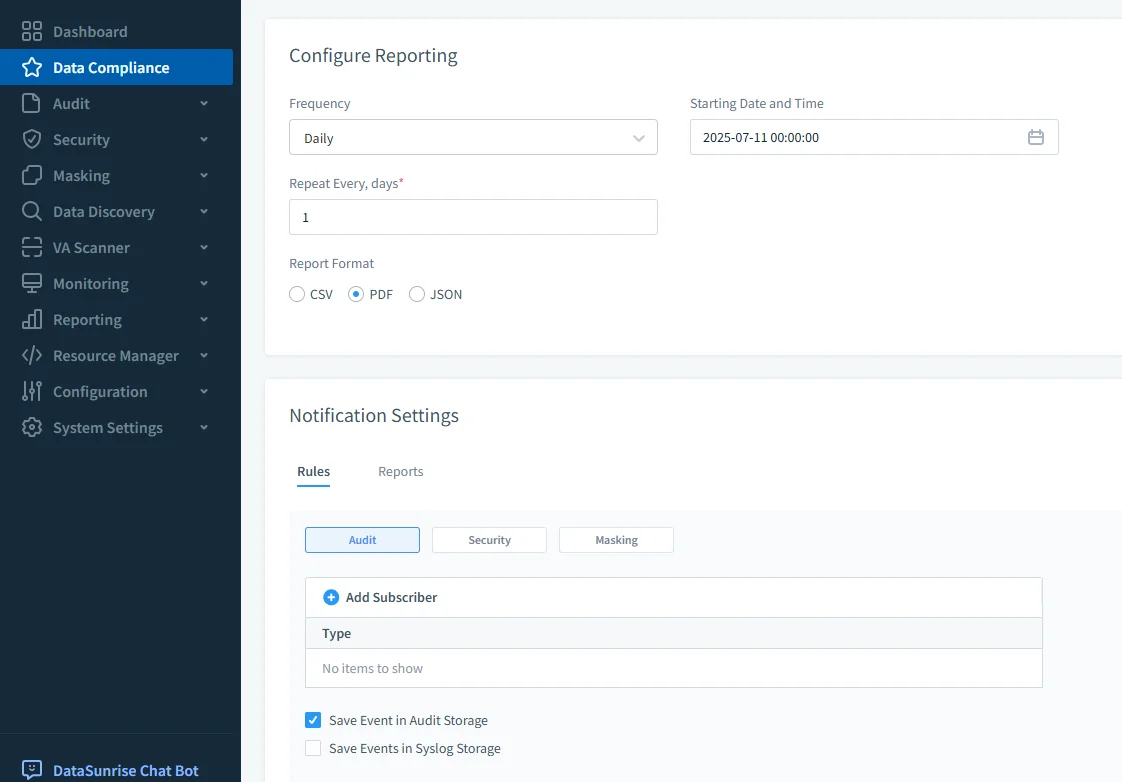
DataSunrise reporting configuration interface for scheduling daily compliance reports in PDF, CSV, or JSON formats with customizable notification settings.
Together, these workflows transform compliance from a manual burden into a managed process tailored to the regulatory standards an organization must meet.
Example Management Workflow
Imagine a mid-sized retail bank preparing for its annual PCI DSS audit.
- Access control: The Db2 team configures RCAC on the
transactionstable so tellers can only view their branch’s records, while auditors retain broader access. - Discovery: During a scheduled scan, DataSunrise flags that cardholder data also appears in a test schema created by developers. The compliance team quickly masks and relocate that data before it becomes a problem.
- Monitoring: While reviewing dashboards, security staff notice an alert — a contractor account issued dozens of unusual queries against customer balance fields outside business hours. The issue is investigated immediately.
- Reporting: At the end of the quarter, the compliance officer generates a PDF report through DataSunrise summarizing access events, masking policies, and incident responses. What used to take days of parsing raw
db2auditlogs now takes minutes.
By combining Db2’s access controls with DataSunrise’s discovery, monitoring, and reporting features, the bank not only meets regulatory obligations but also reduces the risk of exposure and shortens audit preparation significantly.
Conclusion
Managing data compliance in Db2 requires more than enabling features. It involves daily oversight of access, exposure, and evidence. Db2 provides the technical foundation, but without centralized management, compliance risks accumulate.
DataSunrise strengthens Db2 by automating discovery, masking sensitive values, consolidating audit logs, and generating ready-to-use reports. With Db2 as the base and DataSunrise as the management layer, organizations can manage compliance efficiently, continuously, and with confidence.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now