IBM Db2 Compliance Management
Introduction
Compliance management is the ongoing process of ensuring that an organization consistently meets legal, regulatory, and internal policy requirements. Unlike one-time compliance checks, compliance management focuses on maintaining controls, monitoring activity, and proving alignment over time.
IBM Db2 is a core database platform in industries like finance, healthcare, and government — all of which operate under strict compliance frameworks. Because Db2 often stores sensitive and regulated data, organizations must adopt structured compliance management strategies that combine native tools with specialized platforms.
Compliance Management Challenges in Databases
Managing compliance inside a database is rarely straightforward. Modern environments store data across multiple schemas, applications, and even hybrid cloud deployments. Privilege creep — where users accumulate roles and access over time — can go unnoticed until an audit exposes it. Audit logs may exist, but extracting clear, regulator-ready evidence from them can take days.
In Db2, these challenges surface clearly. A healthcare provider may enable db2audit to capture logins and data changes, yet still struggle to present HIPAA-compliant reports when requested. A financial team may configure RCAC policies, but without centralized visibility across multiple instances, their SOX compliance posture remains uncertain.
Compliance management requires not only the right technical settings but also streamlined oversight and reporting.
Native Db2 Compliance Controls
Db2 provides several mechanisms that form the technical foundation of compliance management:
- Auditing: The
db2auditutility captures events such as logins and object changes. Administrators can extract logs for review.
db2audit configure scope all status both
db2audit start
db2audit extract delasc to /tmp/db2audit_logs
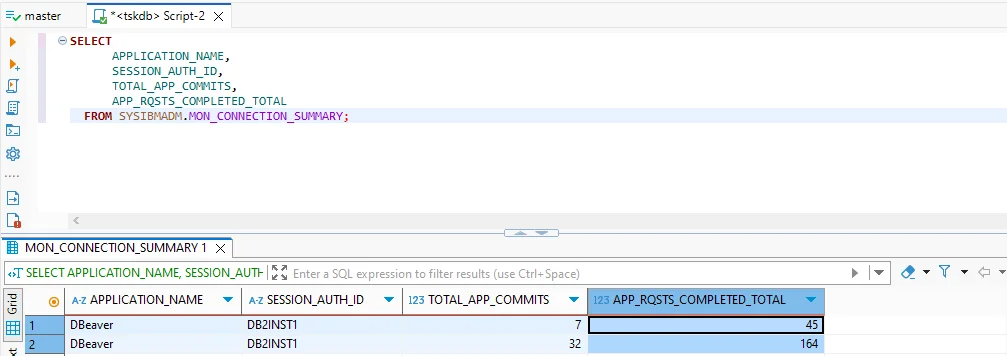
- Monitoring views: Administrative views such as
SYSIBMADM.MON_CONNECTION_SUMMARYgive real-time visibility into sessions.
SELECT
APPLICATION_NAME,
SESSION_AUTH_ID,
TOTAL_APP_COMMITS,
APP_RQSTS_COMPLETED_TOTAL
FROM SYSIBMADM.MON_CONNECTION_SUMMARY;
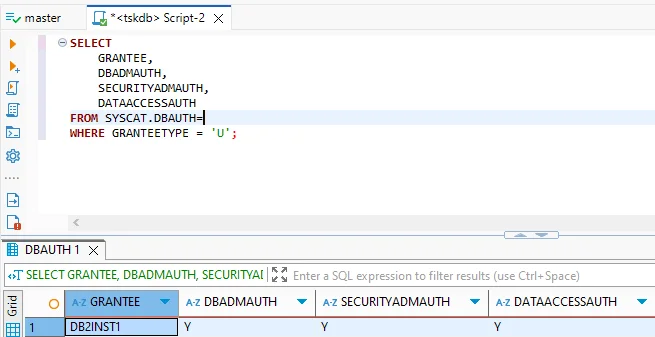
- Access control: Row and Column Access Control (RCAC) and Label-Based Access Control (LBAC) restrict what data users can access.
- Encryption and recovery: Native encryption protects data at rest, and rollforward recovery ensures data integrity after incidents.
These features allow administrators to configure compliance at the technical level and provide a foundation for audits.
Where Native Db2 Falls Short
Native Db2 controls are effective, but managing compliance at scale highlights several gaps.
| Control | Limitation | Compliance Risk |
|---|---|---|
| Auditing | Logs stored locally, difficult to parse at scale | Delayed response to auditor requests, incomplete reporting |
| Access Control | RCAC/LBAC restrict access but do not mask sensitive data dynamically | Risk of exposing full values to users with legitimate access |
| Monitoring Views | Provide real-time data but lack centralized storage or history | No long-term visibility into suspicious trends |
| Encryption/Recovery | Protects integrity but does not address policy alignment | Meets security needs but not audit evidence requirements |
These gaps illustrate why Db2 alone cannot deliver complete compliance management — it secures data but does not simplify oversight or reporting.
Managing Compliance with DataSunrise
DataSunrise is a data security and compliance platform designed to protect sensitive information across databases, data warehouses, and cloud services. For Db2, it transforms technical controls into a manageable compliance framework. It integrates transparently, without application changes, and provides governance teams with the tools needed for oversight.
- Centralization: The audit solution aggregates Db2 logs into a single dashboard. Activity from multiple instances is unified, making it possible to search, filter, and alert in real time.
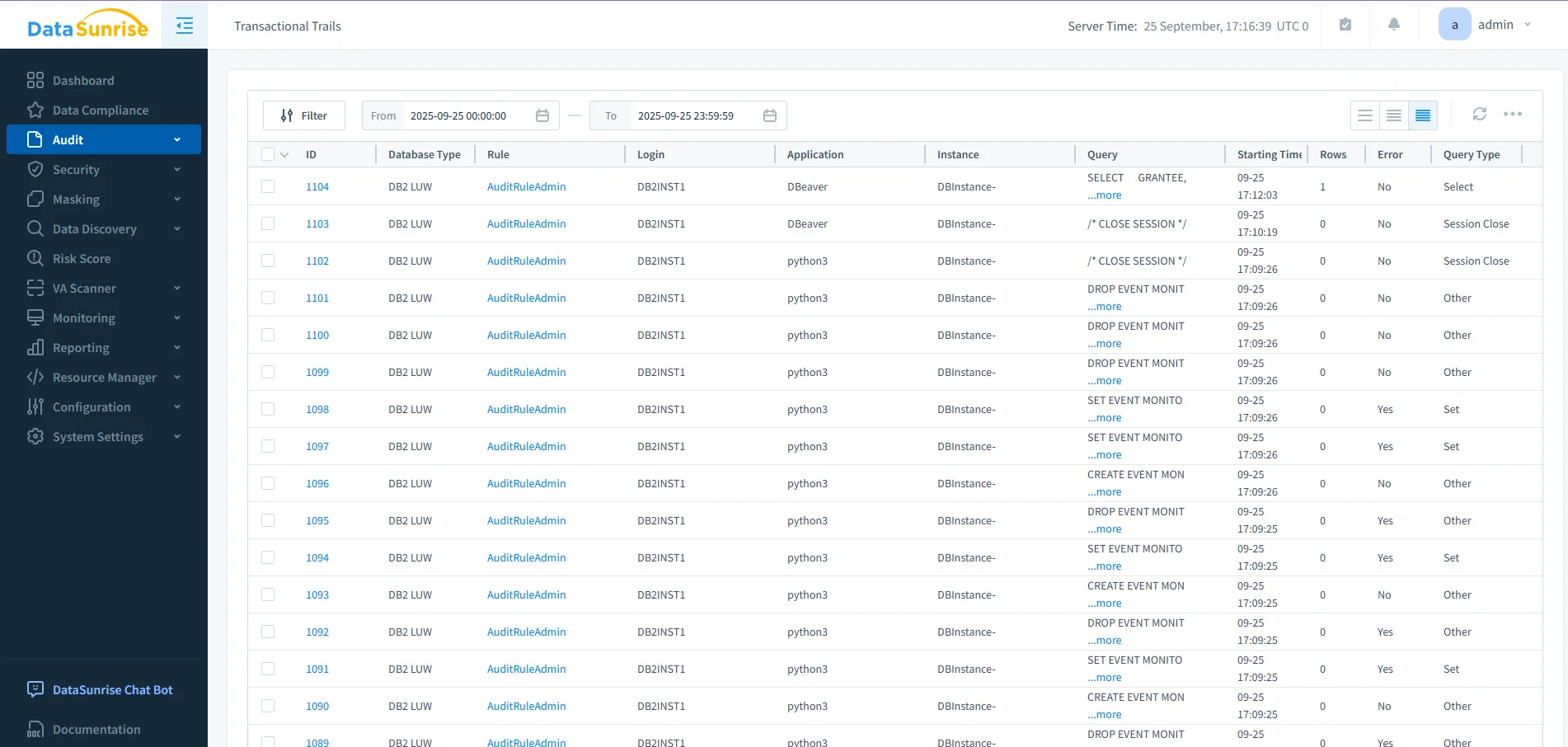
DataSunrise audit dashboard showing transactional trails for Db2 LUW, including queries, logins, applications, and timestamps for compliance tracking. - Automation: With Compliance Autopilot, policies for GDPR, HIPAA, PCI DSS, and SOX remain continuously enforced. As Db2 roles and schemas evolve, enforcement adjusts automatically.
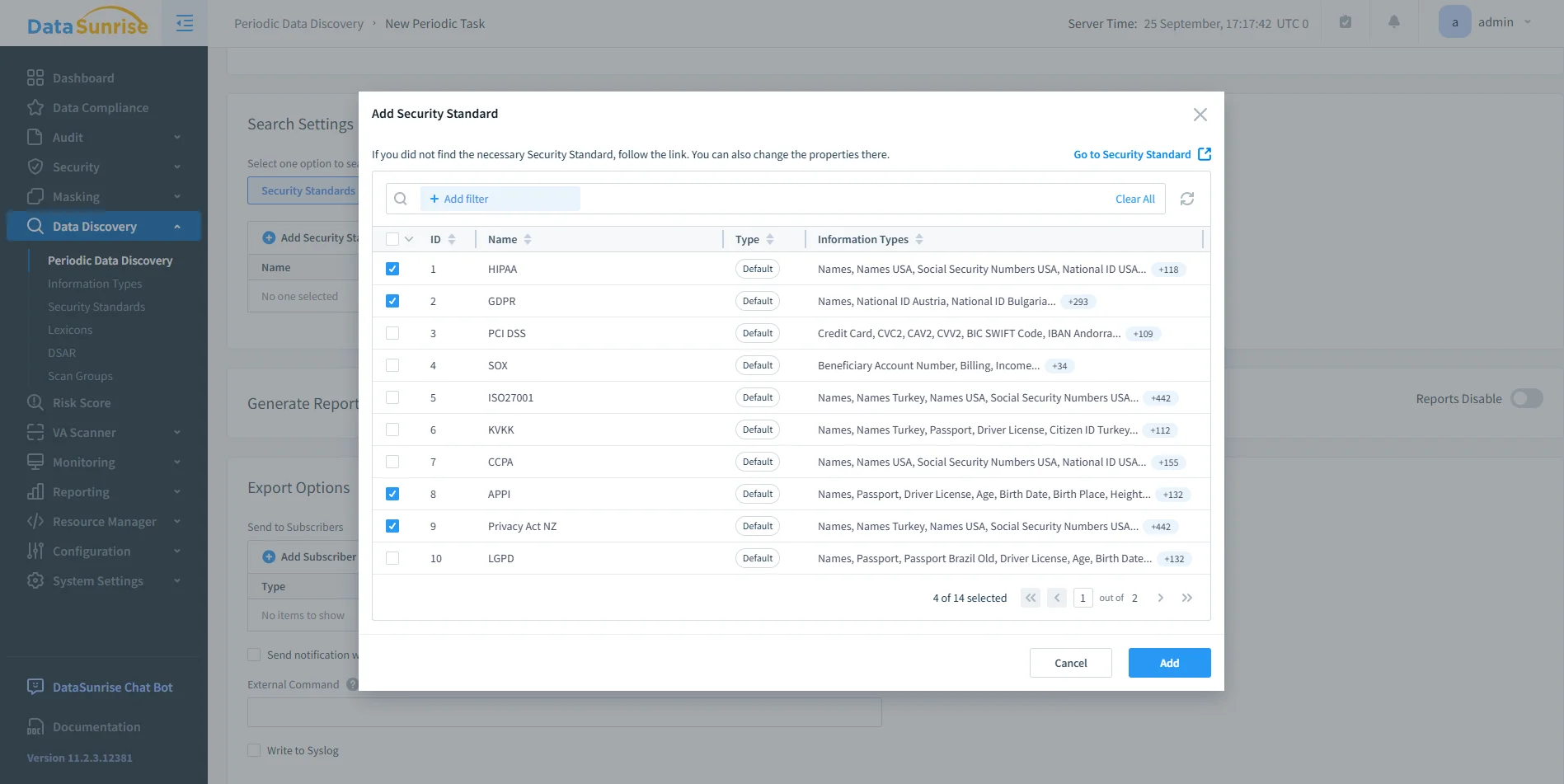
DataSunrise data discovery configuration window for selecting multiple security standards such as HIPAA, GDPR, PCI DSS, and SOX. - Protection: Dynamic data masking and sensitive data discovery ensure that administrators can both locate regulated fields and prevent unauthorized exposure in real time.
- Reporting: The reporting module generates PDF or HTML reports with one click, eliminating the need to manually parse
db2auditlogs.
Instead of replacing Db2 features, DataSunrise enhances them with management capabilities that address oversight, consistency, and audit readiness.
Compliance Oversight: Db2 Alone vs. Db2 with DataSunrise
The table below highlights how compliance management tasks differ when relying only on Db2 native tools compared to when DataSunrise is added.
| Compliance Task | Db2 Native | Db2 + DataSunrise |
|---|---|---|
| Audit Management | Raw logs from db2audit, stored locally and parsed manually |
Centralized dashboards with search, filtering, and alerts |
| Access Control | RCAC and LBAC restrict access but show full values | Dynamic masking hides sensitive values according to user role |
| Data Awareness | Manual catalog inspection for sensitive fields | Automated discovery of PII/PHI across schemas |
| Policy Enforcement | Requires manual configuration per instance | Compliance Autopilot enforces GDPR, HIPAA, PCI DSS, SOX across environments |
| Audit Reporting | No built-in reporting; manual assembly of evidence | One-click PDF/HTML reports, auditor-ready |
Practical Example: Compliance in Action
Consider how a financial institution manages SOX compliance with Db2 and DataSunrise:
- Capture: Db2’s
db2auditrecords schema changes and privileged user actions. - Aggregate: DataSunrise collects and normalizes this activity across all Db2 instances.
- Analyze: Alerts flag unusual activity, such as a role receiving expanded privileges.
- Report: A one-click PDF provides auditors with a structured summary, replacing days of manual log analysis.
This workflow demonstrates compliance management in practice — Db2 provides the technical base, while DataSunrise ensures oversight and efficiency.
Conclusion
Compliance management in Db2 requires more than enabling auditing or access controls. While native tools provide essential safeguards, they leave organizations struggling with oversight, consistency, and reporting.
DataSunrise addresses these challenges by centralizing activity, enforcing policies automatically, protecting sensitive fields, and simplifying audit preparation. With Db2 as the foundation and DataSunrise as the management layer, organizations can sustain compliance continuously — not just during audits.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now