IBM Db2 Data Governance
Introduction
Data governance defines how organizations manage, control, and protect their information. It is not limited to compliance with external regulations but extends to ensuring that data remains accurate, secure, and trustworthy for decision-making.
IBM Db2 is a mission-critical relational database widely used in finance, healthcare, and government systems. Because Db2 often stores regulated and sensitive data, effective governance is essential to balance availability with accountability.
Data Governance Principles Applied to Db2
Strong governance in Db2 can be viewed through four key pillars:
- Integrity: Ensuring that data remains accurate and consistent across transactions and reporting.
- Accountability: Being able to trace who accessed or changed data and when.
- Security: Protecting sensitive information through access controls and encryption.
- Transparency: Demonstrating compliance through clear policies and auditable records.
These principles guide how administrators configure and oversee Db2 environments.
Native Governance Mechanisms in Db2
Db2 provides several built-in tools that support governance objectives:
- Access controls: Row and Column Access Control (RCAC) and Label-Based Access Control (LBAC) restrict which users can see or modify specific data.
ALTER TABLE patients ACTIVATE ROW ACCESS CONTROL;
CREATE PERMISSION doctor_only
ON patients
FOR ROWS WHERE CURRENT USER = doctor_id
ENFORCED FOR ALL ACCESS
ENABLE;
- Auditing: The
db2auditfacility and system views such asSYSIBMADM.MON_CONNECTION_SUMMARYcapture authentication events and query activity.
SELECT
APPLICATION_NAME,
SESSION_AUTH_ID,
TOTAL_APP_COMMITS,
APP_RQSTS_COMPLETED_TOTAL
FROM SYSIBMADM.MON_CONNECTION_SUMMARY;
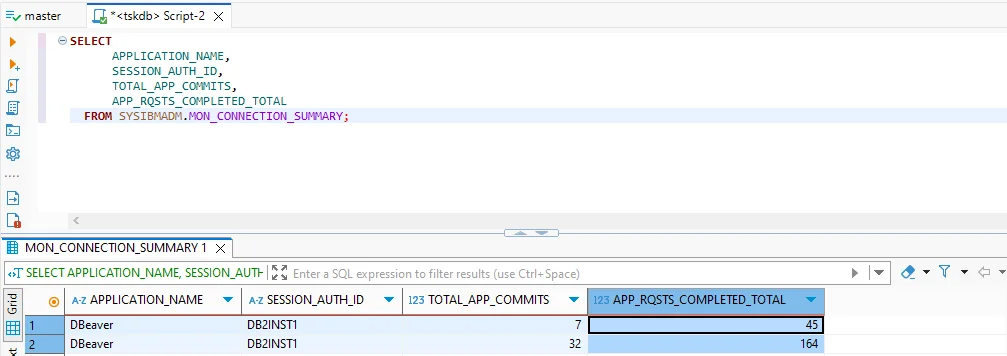
Tip: Regularly export session data to a secure repository. This provides historical visibility and helps spot unusual access trends that might not be obvious in real-time monitoring.
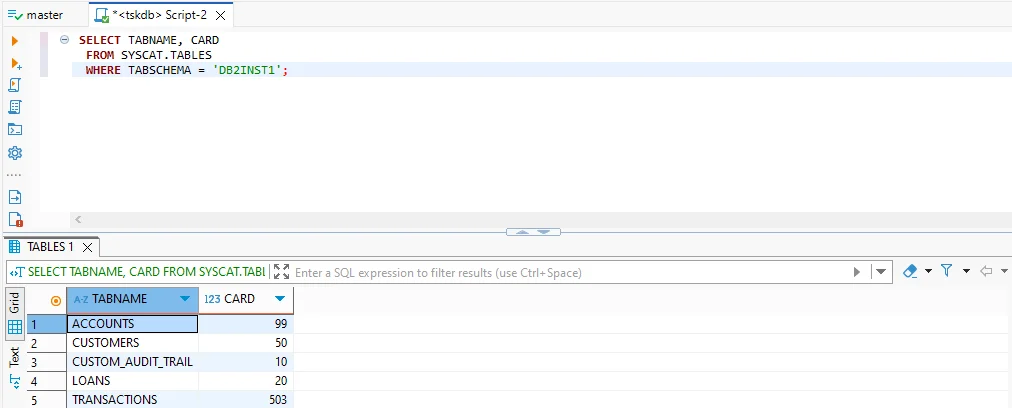
- Table inventory from the catalog: Administrators can query
SYSCAT.TABLESto see table names and cardinality (row counts) within a schema. This helps track growth, detect anomalies, and maintain governance over data volume.
SELECT TABNAME, CARD
FROM SYSCAT.TABLES
WHERE TABSCHEMA = 'DB2INST1';
- Metadata catalog: The SYSCAT views act as a reference for schema objects, privileges, and dependencies, forming part of the governance record.
- Backup and recovery: Rollforward recovery and transaction logging protect data integrity and availability.
These features allow Db2 administrators to create the foundation of a governance program.
Governance Gaps in Db2 Native Tools
While the foundation is strong, sustaining governance with Db2 alone presents challenges.
| Feature | Governance Limitation | Impact |
|---|---|---|
| Access controls (RCAC, LBAC) | Rules must be created manually and do not mask data dynamically | Users with broad privileges may still see sensitive values |
| db2audit | Generates raw logs that are difficult to parse and correlate | Auditors face delays when requesting clear activity reports |
| SYSCAT catalog | Provides metadata but no automated discovery of PII/PHI | Administrators may overlook sensitive data in large schemas |
| Instance-level governance | No central view across multiple Db2 deployments or hybrid clouds | Policy drift and inconsistent enforcement across environments |
Governance in Action: How DataSunrise Complements Db2
DataSunrise strengthens Db2 governance by addressing these gaps directly. It operates transparently, without requiring changes to applications.
- Dynamic enforcement: With data masking, Db2 values are protected in real time, ensuring sensitive fields are only visible to authorized users.
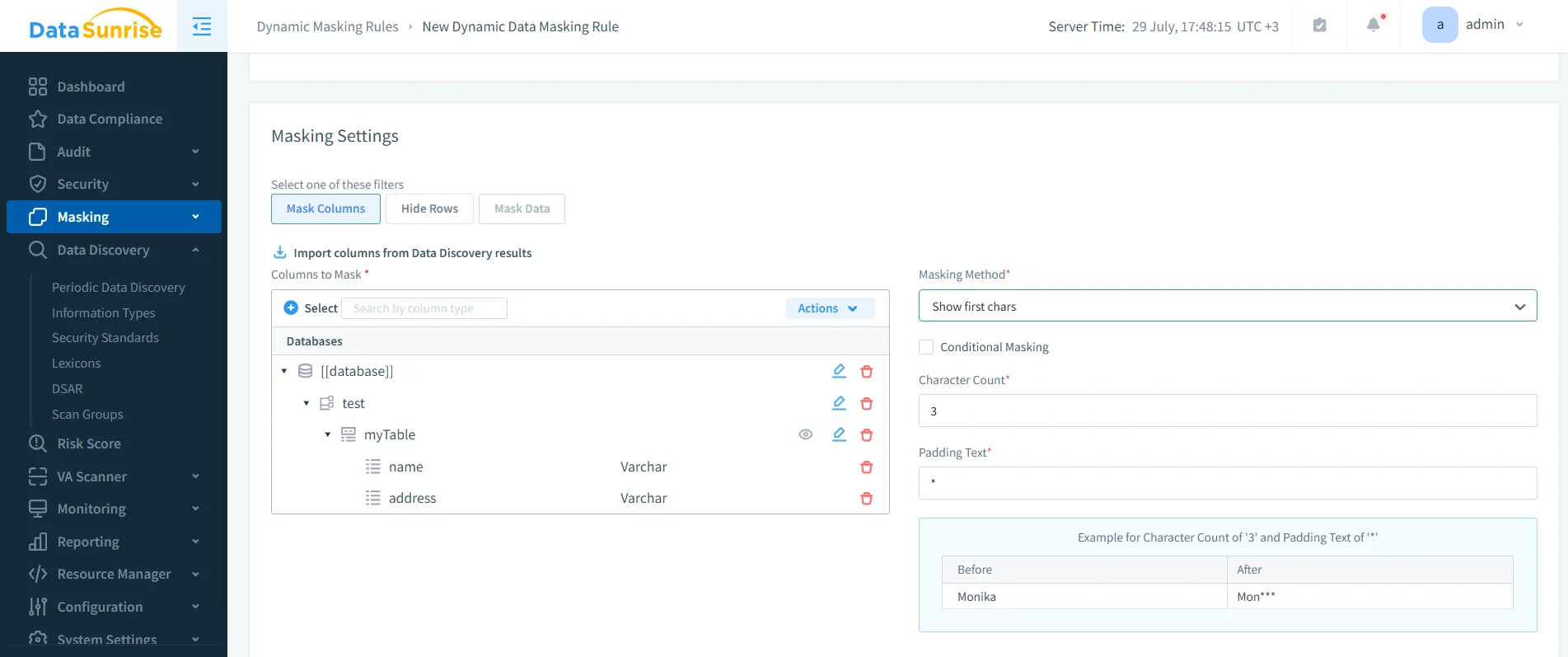
DataSunrise masking settings interface for creating a dynamic masking rule, configured to reveal only the first characters of a field and mask the rest. - Unified visibility: The audit solution aggregates activity across Db2 and other databases, presenting clear dashboards and alerts for governance teams.
- Data awareness: Built-in discovery tools automatically scan Db2 schemas to locate and classify sensitive data such as PII and PHI.
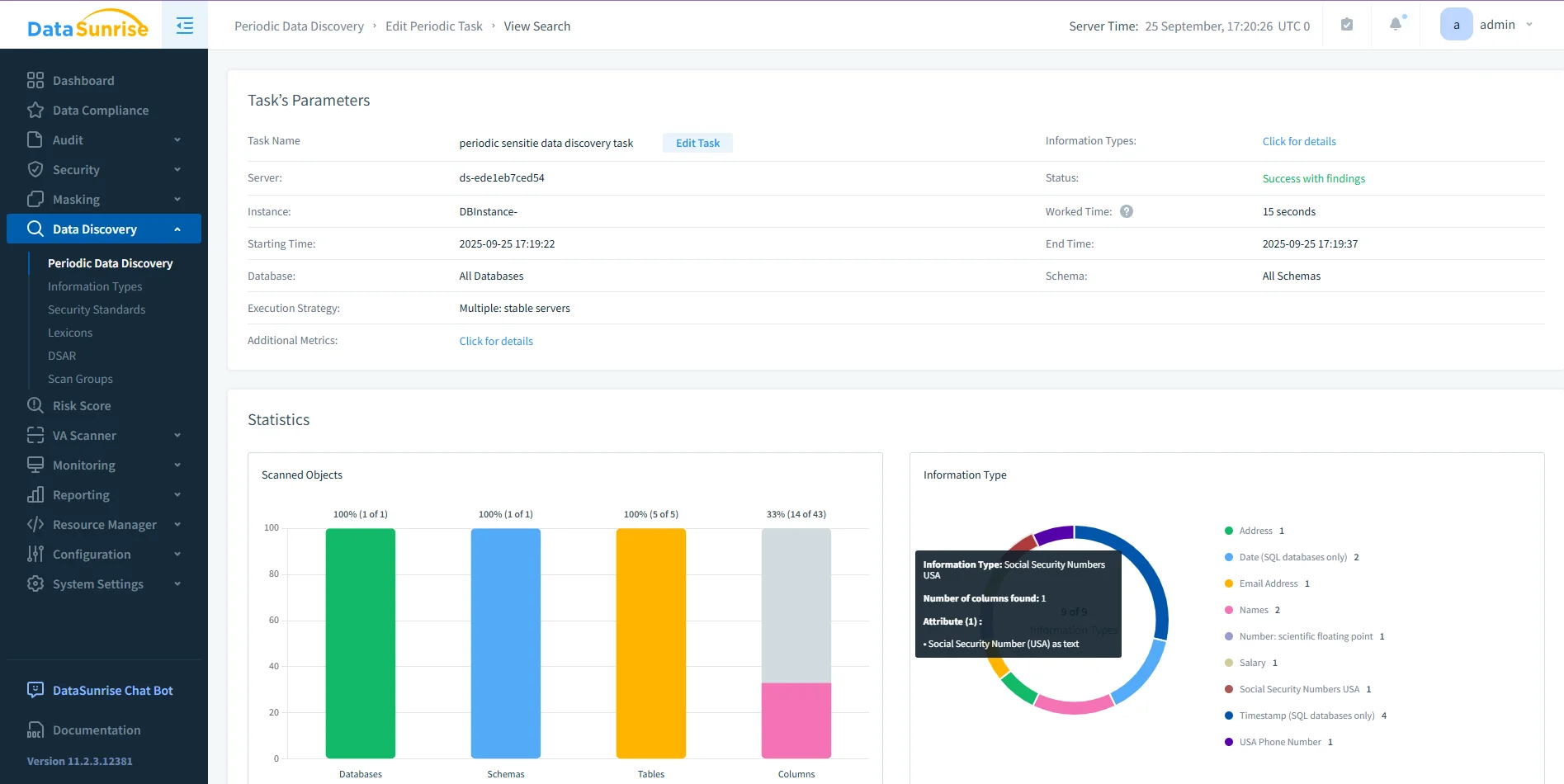
DataSunrise data discovery dashboard with task parameters and scan results, highlighting sensitive data types such as Social Security Numbers. - Continuous governance: The regulatory compliance framework enforces GDPR, HIPAA, PCI DSS, and SOX rules dynamically, while automated reports provide auditors with ready evidence.
Together, these capabilities ensure that governance is not just theoretical but actively enforced in day-to-day Db2 operations.
Governance as a Lifecycle in Db2
Effective governance is not static. It should follow a lifecycle:
- Discover sensitive data and classify it properly.
- Protect that data using access policies, encryption, and masking.
- Monitor all interactions with real-time auditing.
- Report activity to stakeholders and regulators.
- Adjust policies as new risks, users, and data sources appear.
Db2 provides the basic tools for some of these steps. DataSunrise enables the entire cycle to operate seamlessly across both on-premises and hybrid environments.
Conclusion
Data governance in Db2 is more than a compliance checkbox. It ensures that information remains trustworthy, secure, and properly managed across the enterprise. Native Db2 capabilities establish a baseline, but they leave critical blind spots when organizations scale or face regulatory audits.
DataSunrise complements Db2 by automating discovery, enforcing masking, unifying audit trails, and providing continuous governance across environments. With both Db2’s foundation and DataSunrise’s advanced capabilities, organizations can build a governance program that is resilient, transparent, and ready for scrutiny.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now