IBM Db2 Regulatory Compliance
Introduction
Regulatory compliance ensures that organizations manage, process, and protect data according to international standards and laws. By enforcing these requirements, businesses reduce risk, prevent penalties, and safeguard sensitive information.
IBM Db2 is a widely used relational database system supporting enterprise applications across industries. Since it often stores sensitive business and customer data, adherence to compliance frameworks becomes critical in these environments. In sectors such as healthcare, finance, and government, administrators must align database operations with compliance obligations to stay secure and audit-ready.
Frameworks like GDPR, HIPAA, PCI DSS, and SOX define how sensitive information must be handled. Aligning Db2 with these standards helps organizations avoid breaches, maintain trust, and pass audits effectively.
What is Compliance?
Compliance in database systems means adhering to laws and frameworks designed to protect data:
- GDPR governs how personal data of EU citizens is collected and processed.
- In healthcare, HIPAA protects health records and ensures patient privacy.
- The PCI DSS standard defines how organizations handle payment card data securely.
- Meanwhile, SOX sets accountability requirements for financial reporting in public companies.
These frameworks influence how Db2 administrators manage security, auditing, and access controls.
Native DB2 Tools for Compliance
Db2 includes a set of native features that help administrators meet compliance obligations. These can be tested directly in Db2 environments and provide practical value for security and audit readiness.
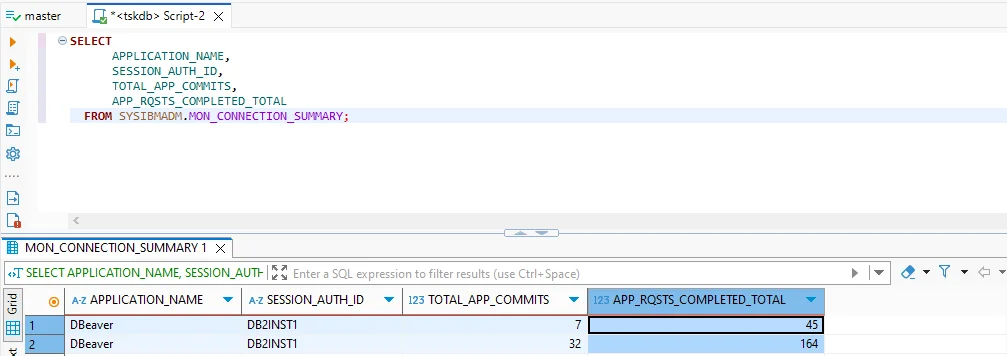
1. Monitoring Active Connections
Db2 provides built-in administrative views for real-time oversight. For example, you can monitor active sessions and their activity:
SELECT
APPLICATION_NAME,
SESSION_AUTH_ID,
TOTAL_APP_COMMITS,
APP_RQSTS_COMPLETED_TOTAL
FROM SYSIBMADM.MON_CONNECTION_SUMMARY;
This query shows which applications are connected, which user IDs are active, and how many requests they have processed.
2. Checking User Privileges
Compliance often requires proof of least-privilege access. Db2 allows you to check which users hold sensitive roles:
SELECT
GRANTEE,
DBADMAUTH,
SECURITYADMAUTH,
DATAACCESSAUTH
FROM SYSCAT.DBAUTH
WHERE GRANTEETYPE = 'U';
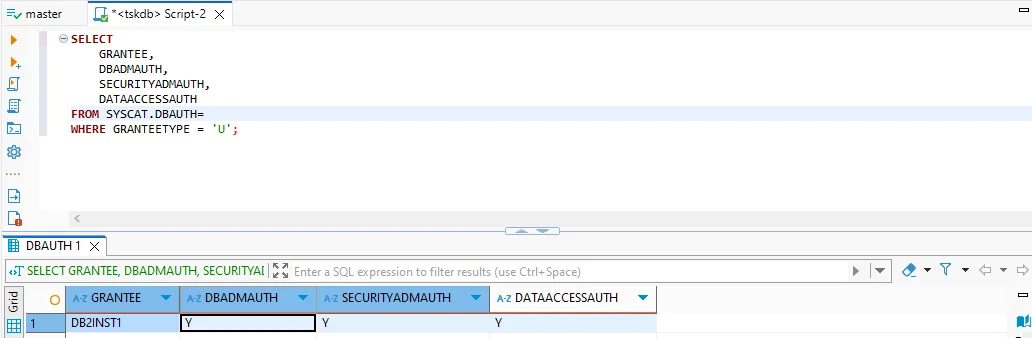
This query helps administrators identify accounts with database admin, security admin, or unrestricted data access permissions.
3. Event Monitor for Connections
Db2 can record connection activity using event monitors. This enables a persistent log of who accessed the database and when:
CREATE EVENT MONITOR connection_audit_monitor
FOR CONNECTIONS
WRITE TO FILE '/tmp/connection_audit'
BUFFERSIZE 8
BLOCKED;
SET EVENT MONITOR connection_audit_monitor STATE 1;
Once enabled, all new connections will be logged to the specified directory, making it easier to provide auditors with evidence of access events.
Limitations of Native DB2 Compliance
Despite strong foundations, Db2 has gaps that limit full regulatory alignment:
- No built-in dynamic masking of sensitive fields.
- No automated discovery or classification of PII/PHI.
- Audit logs from db2audit require complex parsing and external tools for analysis.
- No centralized compliance management across multiple Db2 or mixed environments.
These challenges make audits labor-intensive and risk human error.
How DataSunrise Extends DB2 Compliance
DataSunrise is a data security and compliance platform designed to protect sensitive information across databases, data warehouses, and cloud services. Unlike Db2’s local compliance tools, DataSunrise provides a centralized layer that integrates directly with Db2 without changing application code.
Building on Db2’s foundation, it delivers advanced security, compliance automation, and clear visibility for teams that manage regulated data. Here are the key advantages:
- Unified audit trails: Centralize Db2 audit activity with logs from other platforms. Review everything in one dashboard and receive alerts when policies are breached. See the DataSunrise audit page.
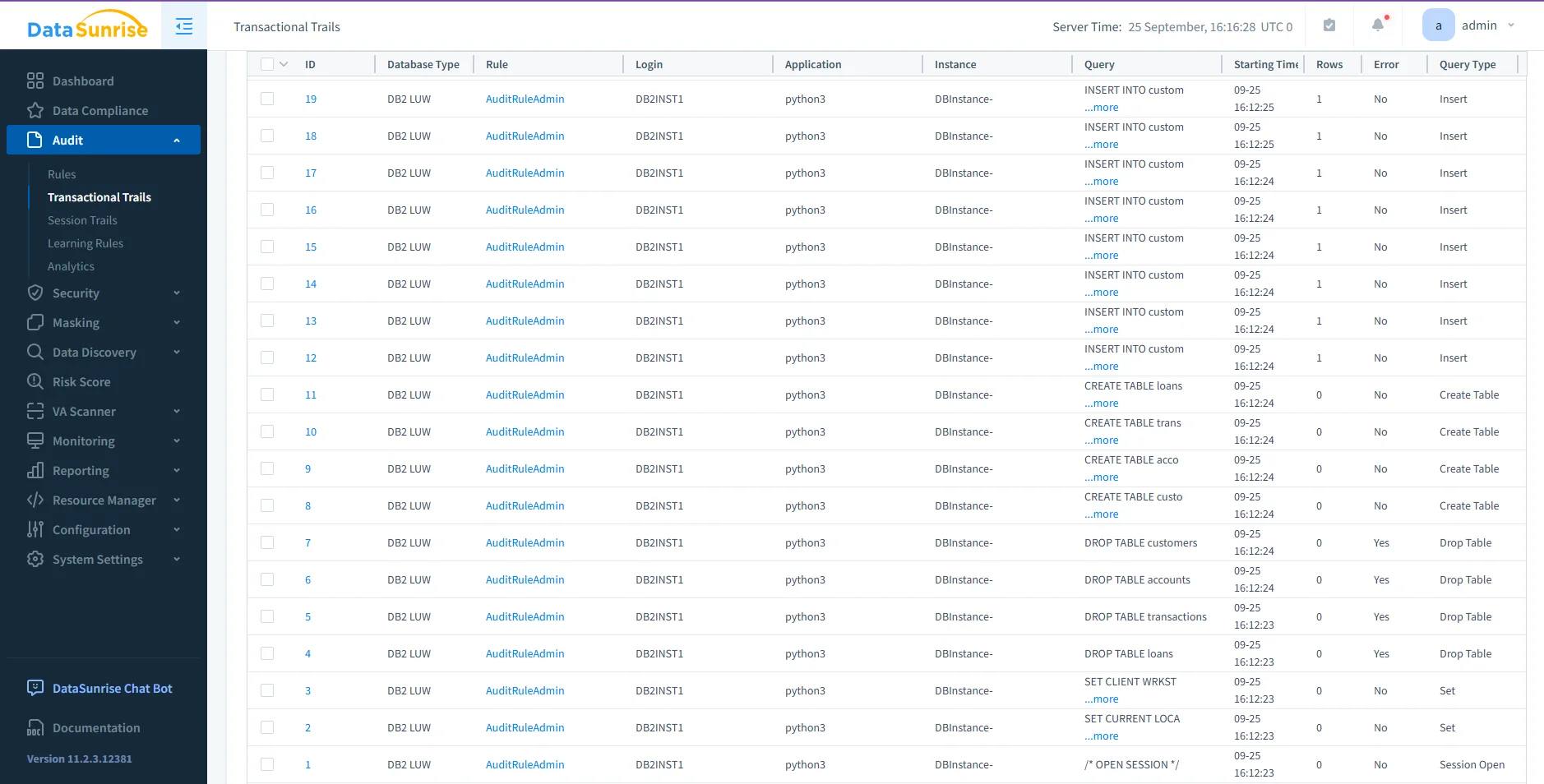
DataSunrise audit dashboard listing Db2 transactional trails with detailed query activity, users, and applications. - Dynamic data masking: Protect sensitive fields—such as card numbers or diagnoses—in real time. Masking rules adapt to user roles and business policy. Details in the DataSunrise dynamic masking overview.
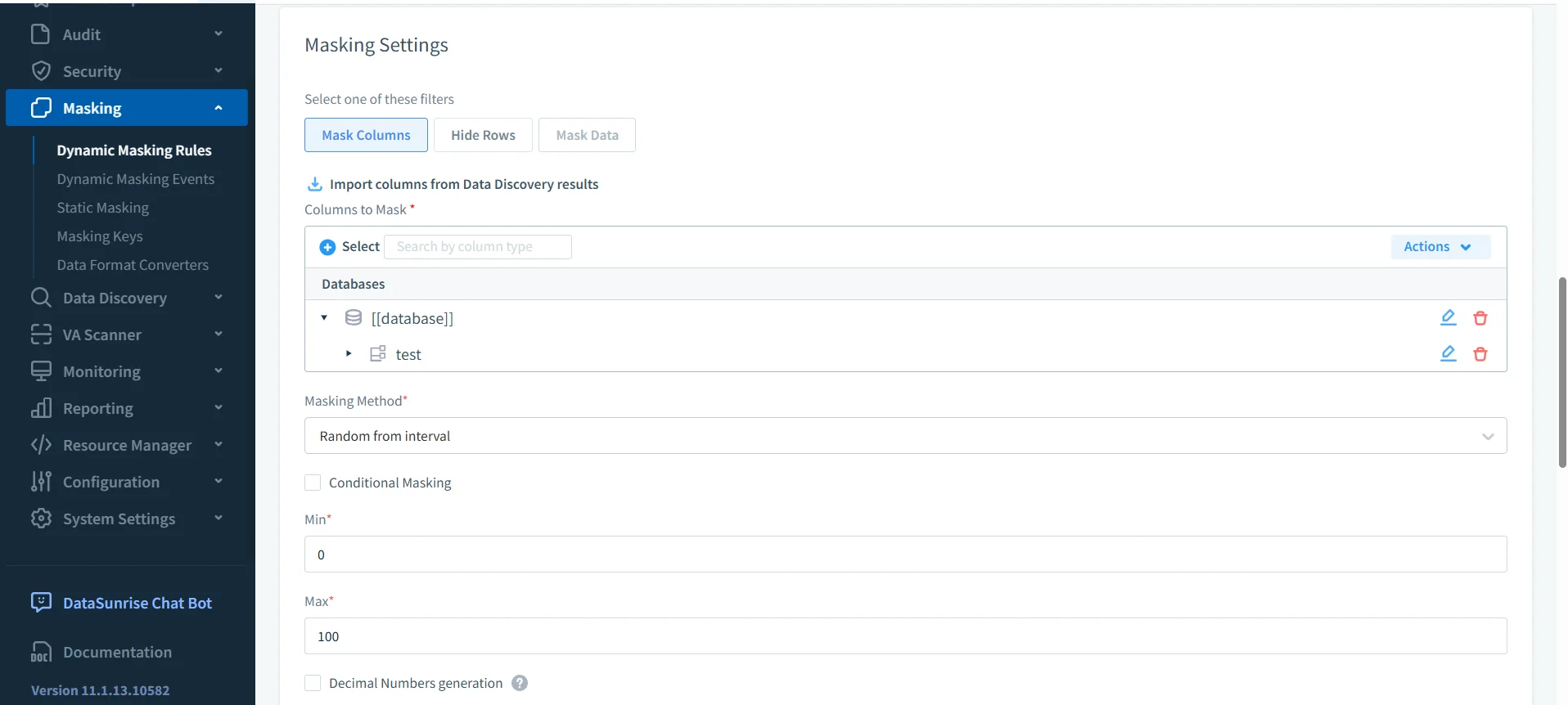
DataSunrise masking configuration screen for setting dynamic column masking rules with customizable methods. - Sensitive data discovery and classification: Scan Db2 automatically to detect and classify PII and PHI. Replace manual schema inspection with clear findings and reports. Learn more in the DataSunrise data discovery section.
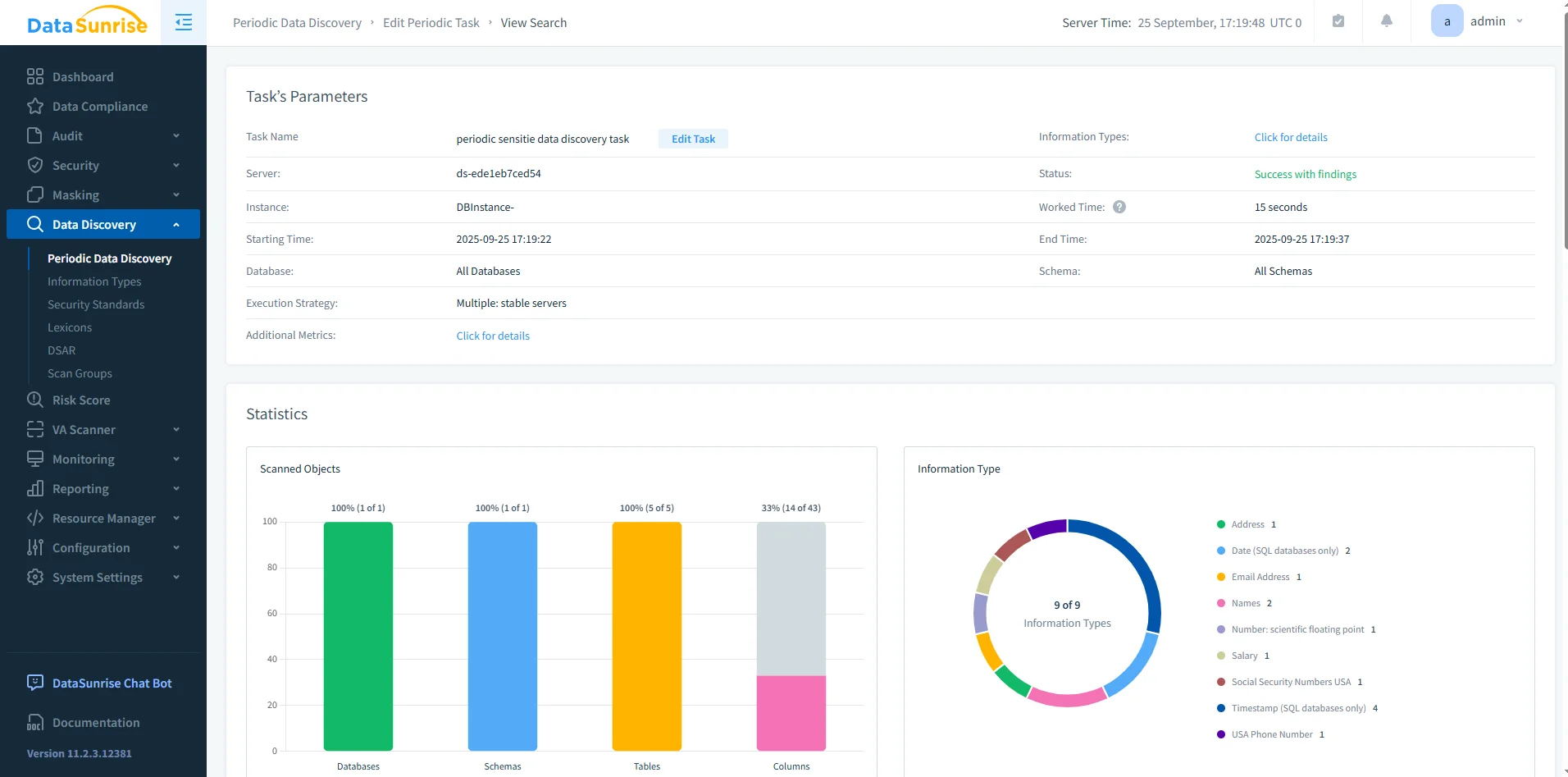
DataSunrise data discovery task results highlighting detected sensitive data types across databases, schemas, tables, and columns. - Automated compliance reporting: Generate PDF or HTML reports for auditors with one click. Cut manual prep and shorten audit cycles. See the DataSunrise compliance section.
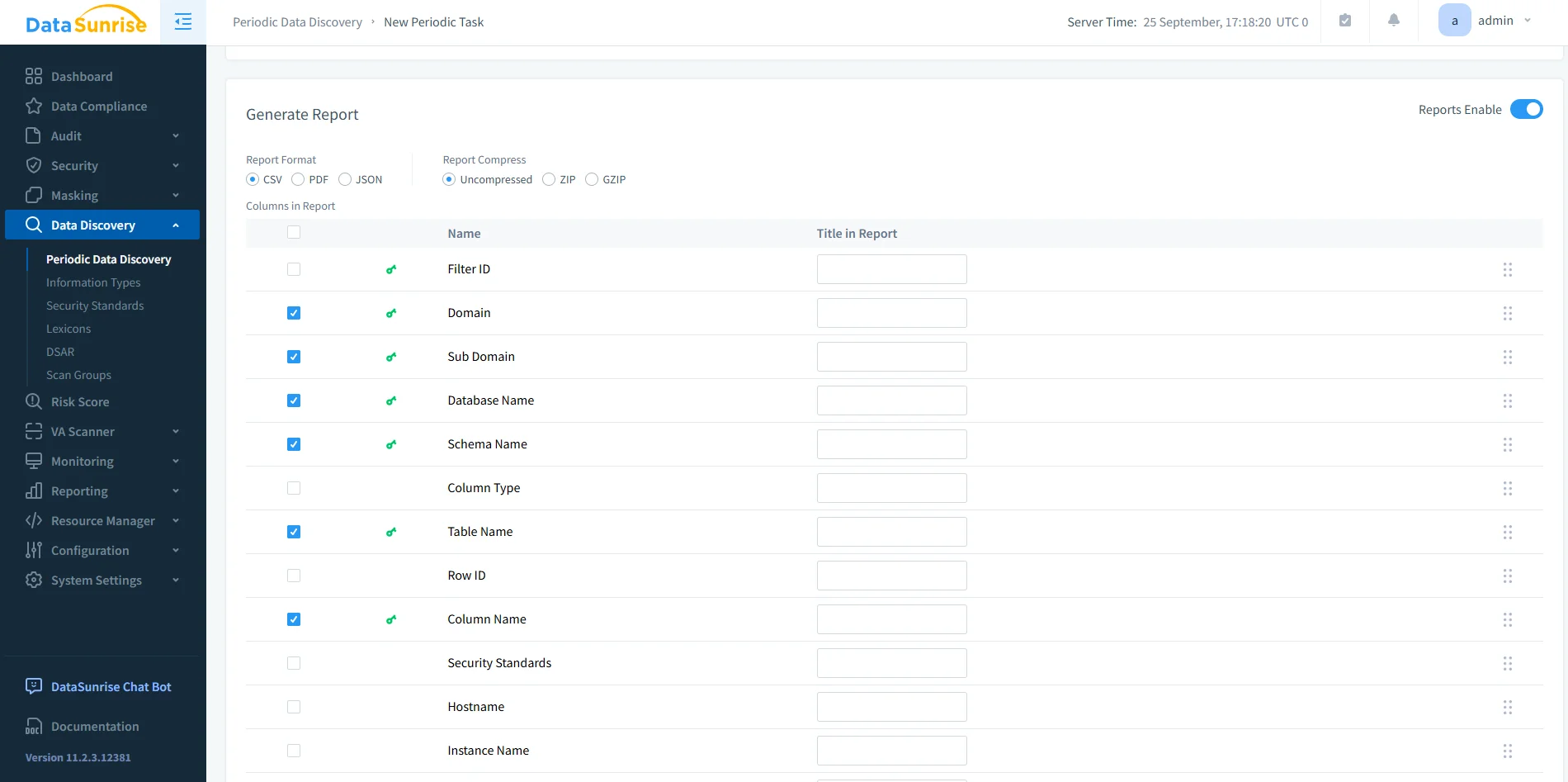
DataSunrise reporting setup interface for generating compliance-ready reports in CSV, PDF, or JSON formats.
Business Impact / Comparison Table
| Feature | DB2 Native | With DataSunrise |
|---|---|---|
| Audit Logging | ✅ db2audit, event monitors | ✅ Centralized with alerts |
| Dynamic Masking | ❌ | ✅ Role-aware real-time masking |
| Data Discovery | Manual schema inspection | ✅ Automated scanning & classification |
| Compliance Reporting | ❌ | ✅ One-click PDF/HTML reports |
| PITR | ✅ Rollforward recovery | ✅ Integrated with compliance workflows |
Real-World Compliance Scenarios with Db2
Understanding compliance is easier when looking at real industries and how Db2 features map to their obligations.
Healthcare (HIPAA): A hospital storing patient records in Db2 must ensure that only authorized doctors can see full medical histories. Using Row and Column Access Control (RCAC), the hospital can restrict each doctor to only their patients’ data. If combined with DataSunrise’s dynamic masking, non-clinical staff like billing clerks would only see masked values for sensitive fields such as diagnoses.
Banking and Payments (PCI DSS): A payment processor managing card transactions in Db2 must protect cardholder data. While Db2 provides audit trails of who accessed the tables, DataSunrise can add real-time masking of card numbers and generate audit-ready PCI DSS reports automatically. This reduces manual checks before regulatory reviews.
Public Companies (SOX): A financial firm using Db2 to store reporting data must track all schema changes and user activities. db2audit can log every ALTER TABLE or role change, but parsing the raw output is time-consuming. DataSunrise provides centralized dashboards and automated reports, giving executives and auditors clear visibility into compliance status.
Retail and Customer Analytics (GDPR): An e-commerce company storing European customer information in Db2 must honor GDPR’s principle of data minimization. Db2’s LBAC (Label-Based Access Control) can restrict access to customer addresses, while DataSunrise’s data discovery continuously scans schemas to detect if personal data is stored outside approved tables.
Conclusion
Db2 provides reliable compliance foundations with auditing, access controls, and recovery features. However, organizations handling sensitive or regulated data often need more advanced capabilities. DataSunrise extends Db2 with dynamic masking, automated discovery, audit centralization, and compliance reporting—reducing manual work while ensuring regulatory alignment.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now