
MySQL Audit Tools

Modern data platforms live under a microscope of regulations and cyber‑threats. MySQL Audit Tools are the instruments that let teams watch every read, write, and configuration change while meeting GDPR, HIPAA, PCI‑DSS, and SOX obligations. In this article we explore how real‑time auditing, dynamic masking, and data discovery work together, and then dive deep into configuring both the native MySQL audit plugin and the DataSunrise suite. Along the way you’ll see practical SQL, links to hands‑on guides, and an honest comparison of toolsets.
Real‑Time Audit & Data Discovery in Context
Real‑time audit is no longer a nice‑to‑have—it is the heartbeat of anomaly detection. Native MySQL streams events into the Performance Schema, but that only tells part of the story. Platforms such as DataSunrise extend visibility to cross‑database sessions, cloud endpoints, and even proxies, while its built‑in Data Discovery engine scans tables for sensitive columns and automatically marks them for monitoring. Combining discovery with continuous auditing ensures that newly added Personally Identifiable Information (PII) never hides in the shadows.
Because discovery operates continuously, every change in schema structure triggers a re‑evaluation of audit policies. That feedback loop keeps security posture aligned with an agile development cadence and avoids manual blind spots that plague quarterly review cycles.
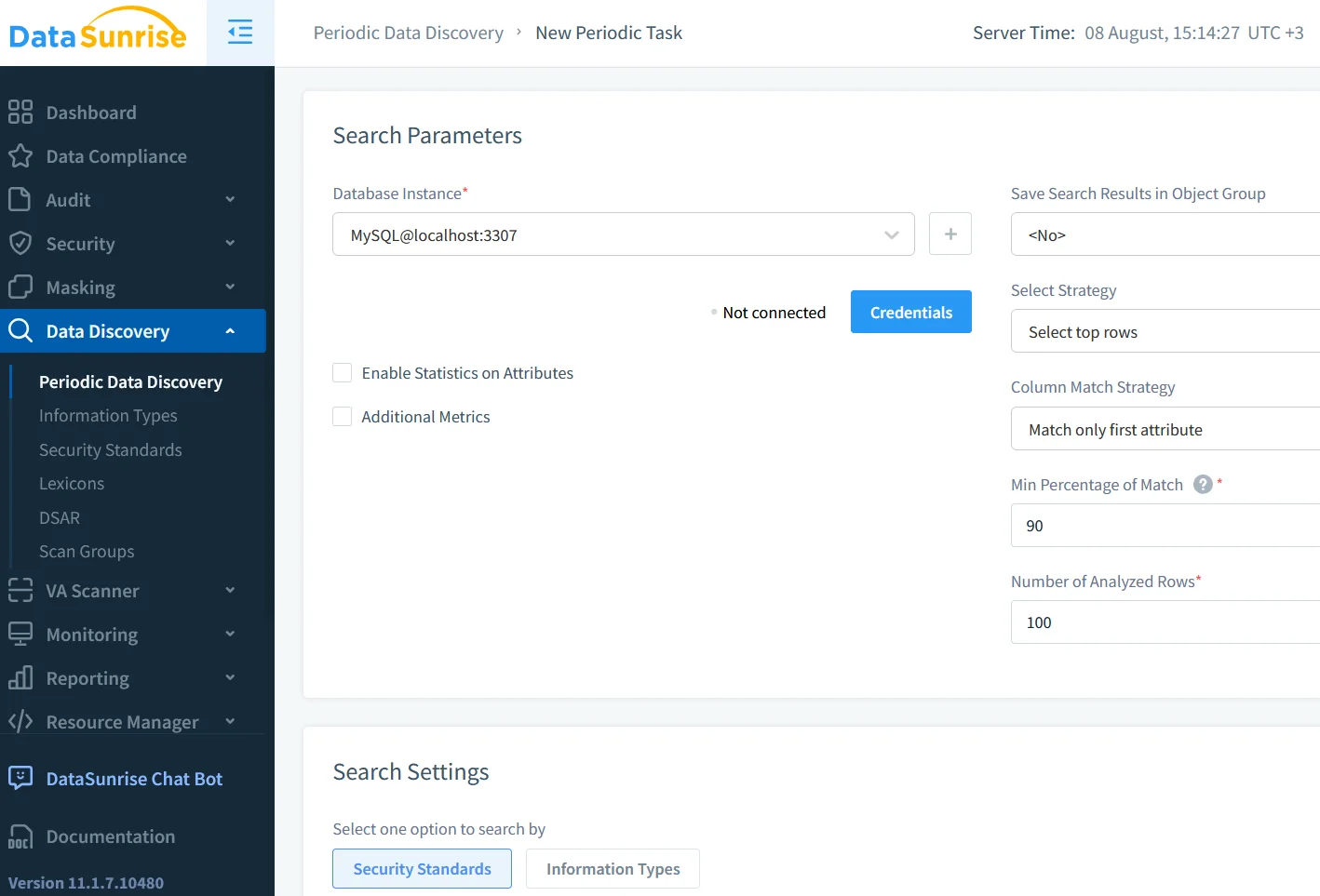
Dynamic Data Masking for Live Environments
Even the best audit trail can leak secrets if analysts view raw production data. Native MySQL supports column‑level Dynamic Data Masking only indirectly (think views and stored routines). DataSunrise’s dynamic data masking layer intercepts SQL and rewrites results on the fly—credit‑card PANs become XXXX‑XXXX‑XXXX‑1234, e‑mail addresses lose their domain, and dates of birth shift inside a tolerance window. Masking occurs after query planning, so there is no impact on the optimizer—as confirmed by A/B latency tests in staging.
The real payoff appears in incident‑response war rooms: investigators get immediate access to queries and bind variables without waiting for a data‑protection officer to scrub exports. Masking policies sit in the same rule engine as audit filters, so a single configuration change propagates to both visibility and obfuscation layers.
Security & Compliance Foundations
Audit does more than record DML; it proves intent. Regulators routinely ask, “Show me everyone who touched encrypted credit‑card blobs in May.” MySQL Audit Tools combine cryptographically signed logs with a tamper‑evident chain of custody. When those tools feed DataSunrise’s Compliance Manager users can build one‑click evidence packs for auditors covering GDPR, HIPAA, or PCI‑DSS without writing ad‑hoc queries.
On the preventive side, DataSunrise’s Database Firewall blocks suspect statements before they hit the server, while the audit trail captures the attempt. That union of “shield” and “camera” is a hallmark of modern Zero Trust reference architectures.
Configuring the Native MySQL Audit Plugin
Out of the box, MySQL Community Edition ships without an enterprise‑grade audit plugin, but users can load Oracle’s open‑sourced audit_log plugin (or Percona’s fork) in minutes. Below is a minimal configuration that logs only write statements to reduce overhead while keeping forensic value high.
-- Enable MySQL Enterprise Audit plugin
INSTALL PLUGIN audit_log SONAME 'audit_log.so';
-- Verify plugin status
SELECT PLUGIN_NAME, PLUGIN_STATUS
FROM INFORMATION_SCHEMA.PLUGINS
WHERE PLUGIN_NAME='audit_log';
-- Persist across restarts
SET GLOBAL audit_log_policy = 'WRITE';
SET PERSIST audit_log_policy = 'WRITE';
-- Reduce noise by ignoring replication user events
SET PERSIST audit_log_filter_id = JSON_ARRAY('ignore_repl');
-- Read back the last 10 events
SELECT
json_extract(event, '$.command_type') AS cmd,
json_extract(event, '$.sql_text') AS sql_text,
json_extract(event, '$.user') AS user,
json_extract(event, '$.host') AS host,
json_extract(event, '$.timestamp') AS ts
FROM mysql.audit_log
ORDER BY id DESC
LIMIT 10;
A few best practices immediately follow:
- Location of log files — Store audit JSON on a partition separate from
ibdatato avoid I/O contention. - Encryption at rest — Mount the log directory on a filesystem managed by Linux eCryptfs or use block‑level encryption in cloud volumes.
- Streaming to SIEM — Ship events to OpenSearch or Splunk using Filebeat for cross‑correlation with application logs.
Detailed reference documentation can be found in the Percona Advanced Auditing guide.
Deep‑Dive into DataSunrise Audit
Where native audit focuses on the server itself, DataSunrise adds a middle‑tier proxy that inspects traffic across heterogeneous clusters. Deployment is quick thanks to container images and Terraform modules (see the deployment modes diagram). Once in place you can craft granular rules such as “Alert on UPDATEs to salary outside business hours” or “Block SELECT * on customer tables for BI roles.”
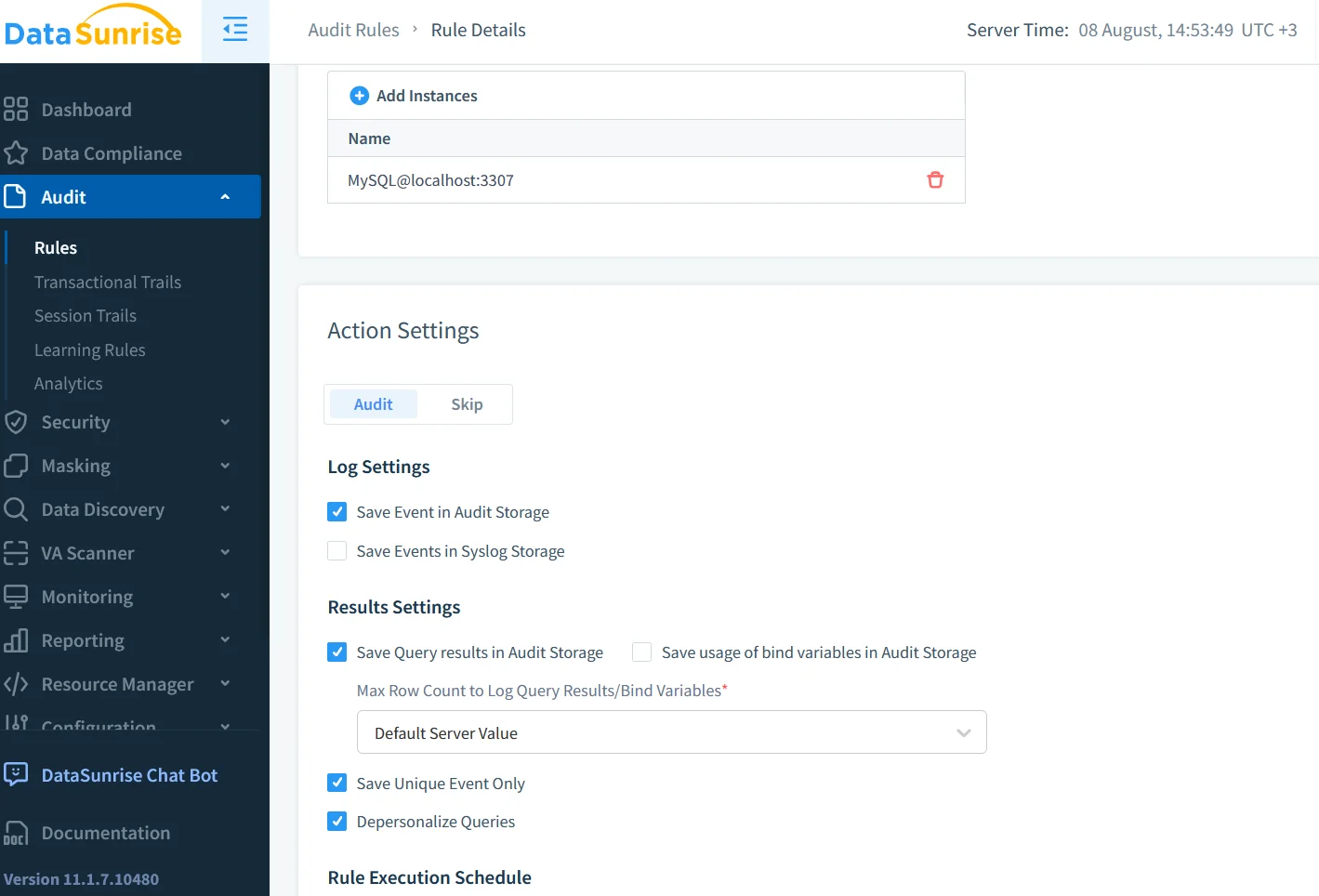
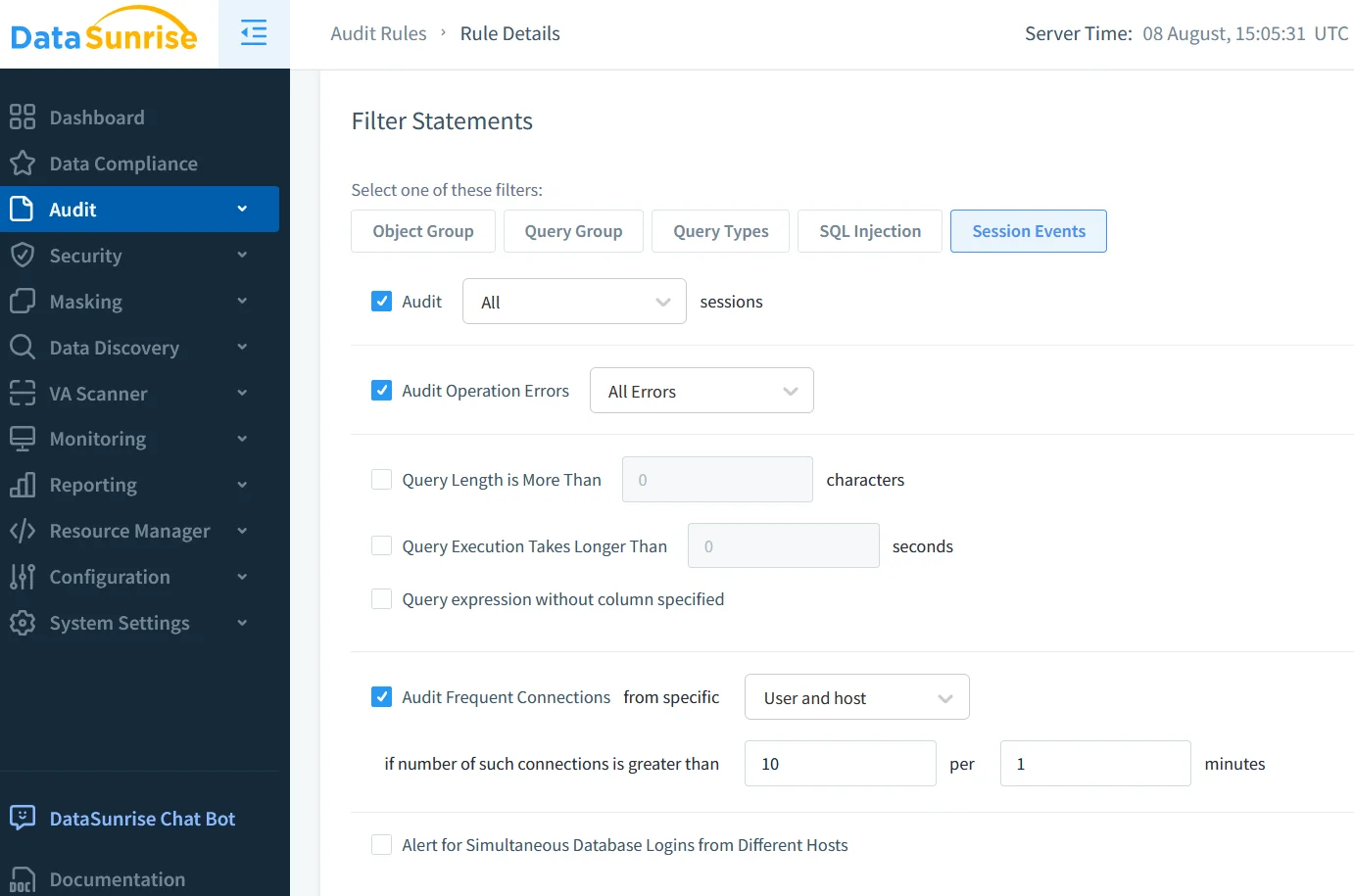
Rule Creation Walk‑Through
- Define an Audit Rule: In the UI select Audit → Rules → New and choose Table: employees, Column: salary.
- Add Condition:
NOT (USER_ROLE IN ('HR_ADMIN') OR TIME_RANGE('08:00','18:00')). - Attach Action: Notify via e‑mail and Slack webhook.
Behind the scenes DataSunrise converts this DSL to an optimized DFA and caches it per connection, so performance stays linear even with hundreds of active rules.
Real‑Time Analytics & Reporting
A popular pairing is DataSunrise’s REST API with Grafana Loki. The audit service exposes an /events endpoint that streams JSON lines; a simple Fluent Bit config pushes those into Prometheus and Grafana dashboards in under ten minutes. Native histograms show spikes in DDL during releases, while anomaly charts overlay masked leak attempts.
Choosing the Right Toolset
- Native Plugin — Lightweight, zero license cost, perfect for single‑tenant environments or dev sandboxes.
- DataSunrise — Enterprise‑grade features (masking, discovery, firewall), multi‑database coverage, compliance bundles.
- Open‑Source Alternatives — McAfee MySQL Audit or
audit_proxyUDF exist but lag behind in maintenance.
Teams often deploy both: keep native audit as a failsafe and layer DataSunrise for enriched context and real‑time blocking. Because DataSunrise reads the original wire protocol, it captures events even when rogue admins disable server‑side plugins.
Practical Reporting & Visualization
Logs are only as useful as the stories they tell. Pipe MySQL JSON and DataSunrise events into an ELK stack or cloud observability platform. From there you can:
- Build heatmaps of failed logins by source IP.
- Trigger AWS Lambda functions when the audit frequency of
DROP TABLEexceeds a baseline. - Generate PDF evidence packs every quarter with DataSunrise’s Report Generator and e‑mail them to your auditor.
These integrations transform passive logs into proactive risk indicators.
Conclusion
In 2025 the conversation about MySQL Audit Tools is no longer just “Do we have logs?” but “Can we respond in seconds, prove compliance, and mask data before it leaves the wire?” Native MySQL audit gets you foundational visibility; DataSunrise adds a security fabric woven from discovery, masking, and firewalling. Combine both—and you gain the observability, control, and regulatory confidence demanded by modern data stewardship.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now