Sensitive Data Protection in MariaDB
Modern database environments rarely serve a single purpose. Instead, organizations often use the same MariaDB instance for production workloads, analytics, internal tooling, and automated integrations. As a result, different users, applications, and services access sensitive information under very different security requirements.
In this context, sensitive data protection in MariaDB focuses on controlling exposure without disrupting workflows. Rather than simply blocking access, teams must ensure that legitimate access does not automatically expose raw sensitive values.
Therefore, this article explains how teams can implement sensitive data protection in MariaDB using native mechanisms. In addition, it shows how centralized platforms such as DataSunrise extend these controls into a consistent, policy-driven security layer.
What Is Sensitive Data?
In MariaDB, sensitive data includes information that creates security, privacy, or compliance risks when users access it outside its intended scope. From a governance perspective, organizations must apply additional controls aligned with established data security and database security practices.
In practice, sensitive data typically includes the following categories:
- Personal identifiers such as names, email addresses, phone numbers, and national IDs, which fall under personally identifiable information (PII)
- Financial data, including card numbers, account balances, and transaction records
- Authentication material such as passwords, tokens, API keys, and secrets
- Regulated datasets governed by GDPR, HIPAA, PCI DSS, or SOX and tracked as part of broader data compliance initiatives
However, protecting sensitive data does not always require encrypting everything at rest or in transit. In many real-world MariaDB environments, teams focus instead on controlled visibility. This approach allows users and applications to work with real schemas and queries while preventing unnecessary exposure of raw values.
Ultimately, security should restrict what is visible, not what is usable.
Native Sensitive Data Protection Capabilities in MariaDB
MariaDB includes several native mechanisms that can be used to limit exposure of sensitive data. These tools provide foundational controls, but they require careful design and ongoing maintenance and are usually implemented as part of broader database security and data security strategies.
Privilege-Based Access Control
MariaDB relies on role- and privilege-based access control to restrict who can read or modify sensitive objects. Column-level privileges allow administrators to expose only specific fields.
/*-- Create a role for analysts
CREATE ROLE analyst_role;
-- Grant column-level SELECT privileges
GRANT SELECT (email, phone)
ON customers
TO analyst_role;
-- Assign the role to a user
GRANT analyst_role TO 'analyst_user'@'%';*/
This approach limits access at the column level and prevents unauthorized queries against sensitive fields. It is commonly used as a baseline control in environments implementing access controls.
However, once access is granted, users still see full, unmasked values. Privileges control who can access data, not how that data is presented.
Views with Masked Output
Views are commonly used to expose masked representations of sensitive columns while keeping the underlying table unchanged.
/*-- Create a masked view over the base table
CREATE VIEW masked_customers AS
SELECT
id,
-- Partially mask email address
CONCAT(
SUBSTRING(email, 1, 3),
'***@***'
) AS email,
-- Mask phone number completely
'***-****' AS phone
FROM customers;
-- Grant access only to the view
GRANT SELECT ON masked_customers TO analyst_role;*/
Applications and analysts query the view instead of the base table, allowing schemas and relationships to remain intact while hiding raw values. This technique is often discussed alongside data masking approaches.
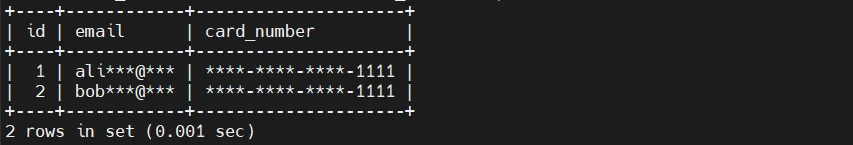
This model works best in tightly controlled environments where direct access to base tables is strictly enforced and well-governed.
Stored Functions for Conditional Masking
Stored functions allow masking logic to be applied dynamically and reused across multiple views or queries.
/*DELIMITER //
CREATE FUNCTION mask_email(val VARCHAR(255))
RETURNS VARCHAR(255)
DETERMINISTIC
BEGIN
RETURN CONCAT(
SUBSTRING(val, 1, 3),
'***@***'
);
END;
//
DELIMITER ;*/
The function can then be reused consistently:
/*SELECT
id,
mask_email(email) AS email
FROM customers;*/
Functions help standardize transformations and reduce duplication. At the same time, masking logic becomes embedded in database code, which increases maintenance effort and complicates auditing and compliance validation as environments scale and regulatory requirements grow.
Centralized Sensitive Data Protection with DataSunrise
DataSunrise introduces an external security layer that protects sensitive MariaDB data without modifying database schemas or application logic. Instead of embedding controls into SQL or applications, the platform enforces protection rules transparently while processing queries. As a result, security controls operate independently of application development and database structure. This approach fits naturally into broader data security and database security architectures.
Sensitive Data Discovery and Classification
DataSunrise automatically scans MariaDB schemas and identifies sensitive data such as personally identifiable information, financial values, and authentication credentials. Rather than relying on static naming conventions, the platform analyzes data content and patterns, which aligns with modern data discovery practices. Consequently, protection policies remain consistent even as schemas evolve.
As a result, organizations maintain a continuously updated inventory of sensitive data assets that directly supports protection, auditing, and compliance workflows.
Dynamic Data Masking
DataSunrise applies dynamic data masking in real time as users execute queries. Depending on execution context, the same column may appear masked or unmasked. For example, masking decisions can consider the database user or role, the application or service account, the client IP address or network segment, and session attributes.
Therefore, teams gain precise control over data visibility without rewriting SQL, changing application logic, or maintaining parallel schemas. In practice, organizations commonly implement this model as dynamic data masking at the access layer.
Static Masking for Non-Production Use
For development, testing, analytics, and data sharing scenarios, DataSunrise supports static masking through controlled workflows. During database cloning, backup restoration, test data provisioning, or export operations, the platform transforms sensitive values before data leaves protected environments.
Accordingly, these workflows align with established static data masking and test data management practices, reducing exposure while preserving dataset usability.
Unified Audit and Protection Visibility
DataSunrise records every access to sensitive data—whether masked or unmasked—as part of a unified audit trail. Audit records clearly show who accessed sensitive fields, whether masking applied, and when and from where access occurred.
By directly linking protection decisions with activity tracking, this approach complements database activity monitoring and simplifies both investigations and compliance verification.
Compliance Alignment
DataSunrise aligns sensitive data protection with regulatory requirements such as GDPR, HIPAA, PCI DSS, and SOX. In addition, preconfigured policies and automated reporting support ongoing data compliance efforts, which reduces manual audit preparation while maintaining technical accuracy across environments.
Business Impact of Sensitive Data Protection in MariaDB
| Business Area | Impact |
|---|---|
| Risk reduction | Minimizes the risk of accidental exposure and insider misuse of sensitive data by enforcing controlled visibility |
| Operational consistency | Ensures uniform protection across users, applications, and environments without relying on ad-hoc SQL logic |
| Compliance readiness | Accelerates compliance audits through centralized visibility into data access and protection decisions |
| Maintenance efficiency | Reduces long-term maintenance effort compared to SQL-based masking and view-level controls |
| Security governance | Makes security controls predictable, testable, and auditable across the entire MariaDB estate |
Conclusion
MariaDB offers essential access control mechanisms, but effective sensitive data protection requires more than permissions and SQL constructs alone.
By combining centralized discovery, real-time masking, auditable enforcement, and compliance-aligned reporting, DataSunrise turns sensitive data protection in MariaDB into a consistent, policy-driven process that preserves application flexibility while delivering the visibility and control required in regulated environments.
