
Sybase Data Governance

Sybase Adaptive Server Enterprise (ASE) remains a trusted database platform in industries such as finance, government, and telecommunications, where mission-critical workloads demand stability and performance. However, handling sensitive information in these environments requires more than just reliable database operations. Data governance in Sybase is about ensuring that data is accurate, secure, accessible to authorized users, and compliant with applicable regulations.
Effective governance practices integrate policies, procedures, and technologies to oversee data usage, maintain integrity, and enforce compliance with frameworks like GDPR, HIPAA, and SOX.
What is Data Governance and Why It Matters
Data governance is the practice of managing the availability, usability, integrity, and security of data throughout its lifecycle. It defines the framework for how data is stored, accessed, shared, and protected within an organization. This includes setting policies for data quality, assigning roles and responsibilities, and ensuring that regulatory requirements are met.
In the context of Sybase ASE, strong data governance ensures that sensitive business information is not only protected against unauthorized access but is also accurate and reliable for decision-making. Poor governance can lead to data breaches, compliance violations, financial penalties, and reputational damage. On the other hand, well-implemented governance improves operational efficiency, builds customer trust, and enables organizations to leverage their data as a valuable strategic asset.
Native Sybase Data Governance Capabilities
Sybase ASE provides several built-in features that can be adapted to a governance framework. While not labeled strictly as “data governance” tools, they form the foundation for oversight and compliance.
1. Role-Based Access Control (RBAC)
Administrators can define granular roles and assign them to users based on job functions, limiting exposure to sensitive data.
-- Create a read-only role for financial analysts
create role finance_readonly;
-- Grant SELECT on a sensitive table
grant select on dbo.transactions to finance_readonly;
-- Assign the role to a user
sp_addrolemember 'finance_readonly', 'analyst_user';
This ensures only authorized personnel can view specific datasets, a critical part of governance and compliance.
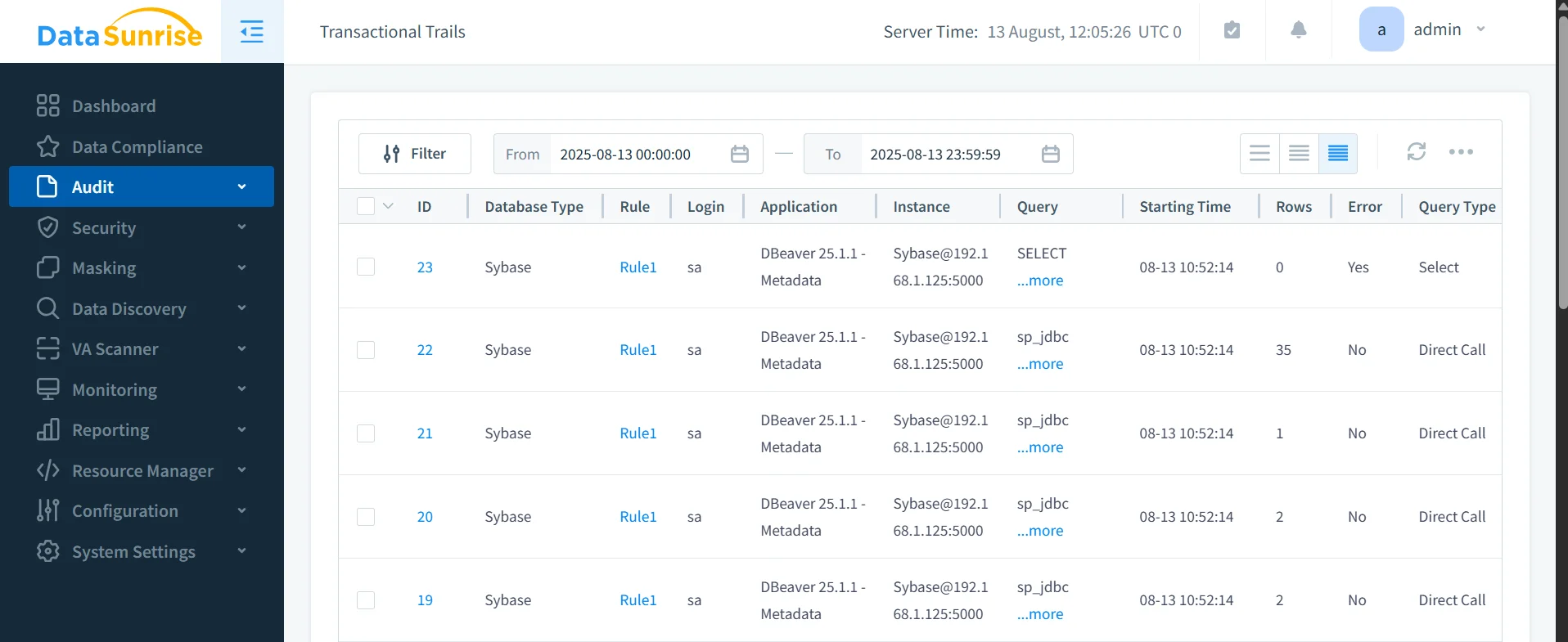
2. Auditing with sp_audit
Sybase’s native audit feature can track data access, modifications, and administrative changes.
-- Enable auditing for SELECT and UPDATE on the customers table
sp_audit 'select', 'dbo', 'customers', 'on'
sp_audit 'update', 'dbo', 'customers', 'on'
-- Review audit settings
sp_displayaudit;
Audit records can later be extracted for compliance reporting or integrated into a SIEM for further analysis.
3. Enforcing Data Integrity
Constraints and triggers ensure that data entered into the database complies with business rules.
-- Ensure email format validation
alter table customers
add constraint chk_email_format
check (email like '%_@__%.__%');
Such constraints help maintain high-quality, trustworthy data — a core governance principle.
4. Encryption & Sensitive Data Protection
Sybase supports column-level encryption to secure sensitive values such as personal identifiers.
-- Create encryption key
create encryption key ssn_key
with algorithm = aes_256
encrypted with password 'StrongKeyPass!';
-- Encrypt SSN column
alter table customers
modify ssn encrypt with ssn_key;
Native encryption enhances confidentiality but often needs to be paired with masking and access policies for full governance coverage.
Extending Governance with DataSunrise
While Sybase ASE’s built-in features provide a governance baseline, DataSunrise elevates these capabilities into a fully integrated governance and compliance framework.
Centralized Policy Management: Define and enforce security, masking, and audit policies across multiple Sybase instances from one interface. This eliminates the need for repetitive configuration changes on each database, ensuring uniform governance across the organization. Policies can be updated in real time and applied instantly, reducing the risk of policy drift and ensuring consistent protection.
Dynamic Data Masking: Automatically conceal sensitive fields at query time based on user roles, without altering the underlying data. This ensures that even privileged users can only see the information they are authorized to access. Masking rules are applied transparently to applications, preventing any impact on business workflows or application logic.
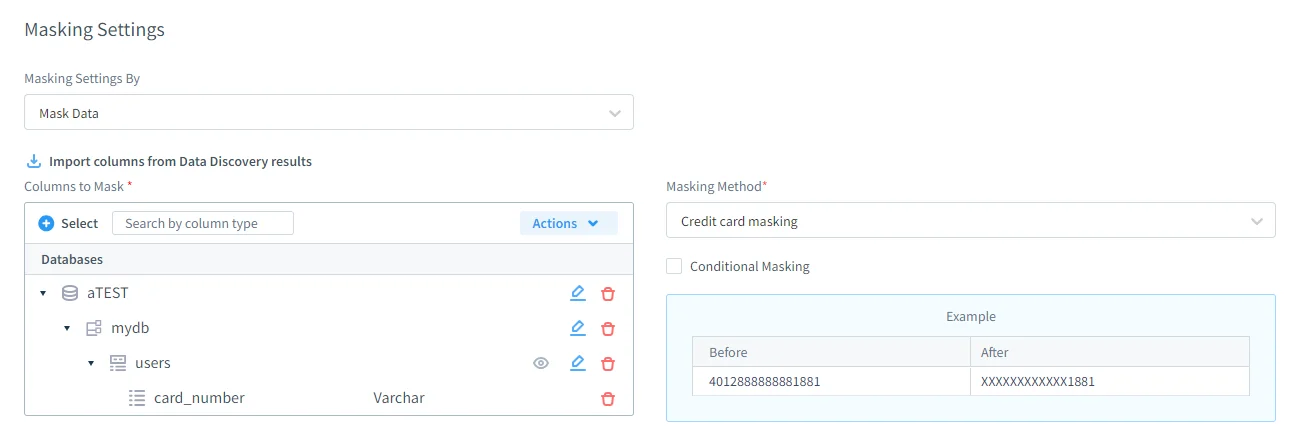
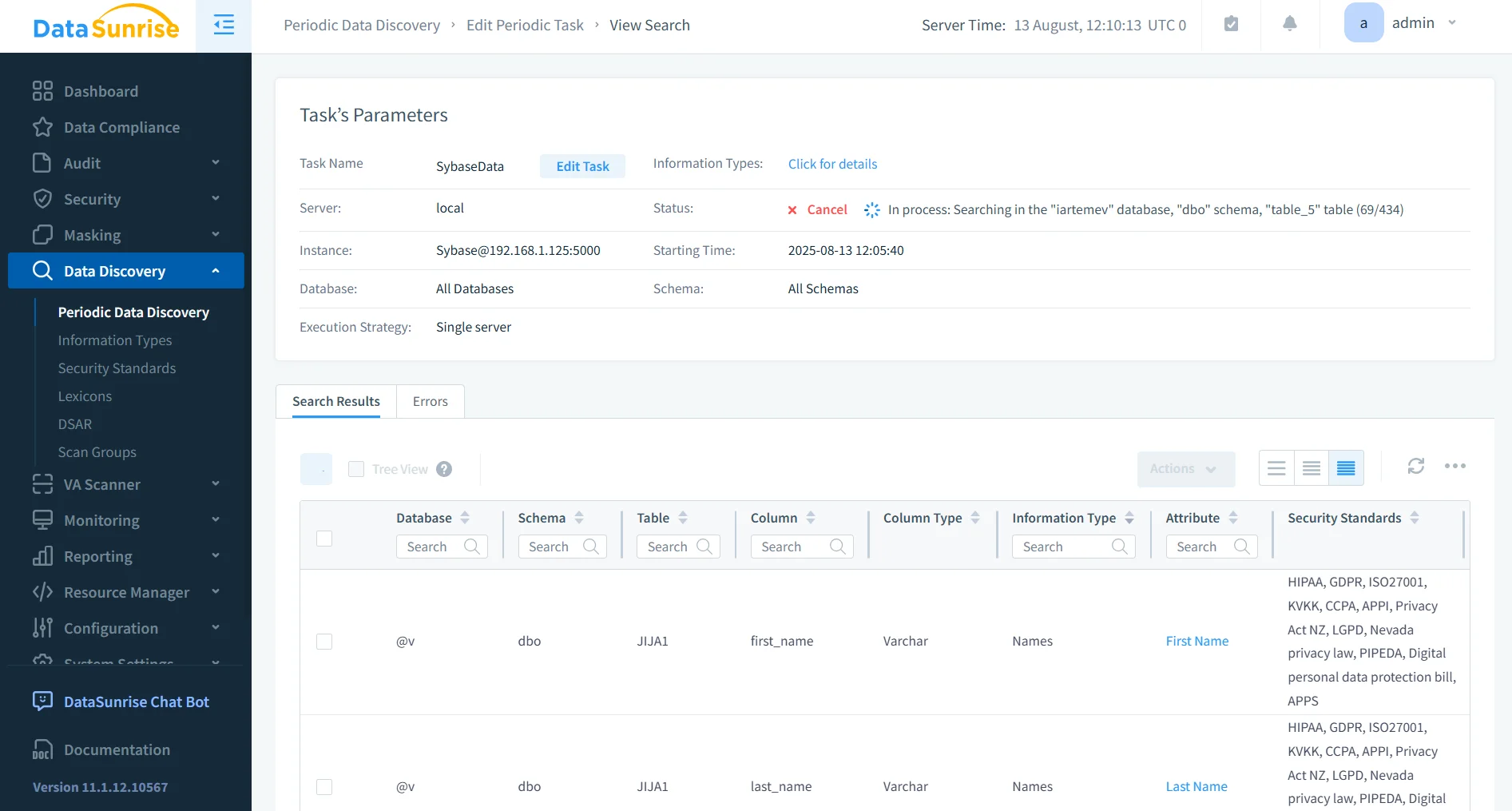
- Advanced Data Discovery: Continuously scan for PII, PHI, and financial data across your Sybase environment to identify compliance gaps. The discovery process uses intelligent pattern recognition and classification to detect sensitive content even in unstructured or semi-structured formats. Regular scans help organizations stay ahead of regulatory changes and evolving internal security requirements.
- Real-Time Alerts: Detect suspicious access patterns instantly and send notifications to security teams. Alerts can be configured to trigger based on specific user actions, query anomalies, or unusual data access times. Integration with SIEM and messaging platforms ensures that incidents are escalated quickly for rapid investigation.
Automated Compliance Reporting: Generate auditor-ready evidence for GDPR, HIPAA, SOX, and PCI DSS with minimal manual effort. Reports can be customized to highlight specific controls or incidents relevant to each regulation. Scheduling capabilities allow reports to be generated automatically at predefined intervals, ensuring that compliance documentation is always up to date.
User Behavior Analytics: Identify anomalies in query patterns to proactively address insider threats. By learning typical user activity over time, the system can detect deviations that may indicate malicious intent or compromised accounts. These insights support faster, more targeted investigations and can be used to refine security policies continuously.
Business Impact
| Governance Objective | Native Sybase ASE | With DataSunrise |
|---|---|---|
| Access Control | RBAC with manual configuration and per-instance setup | Centralized, role-aware policies applied across multiple environments instantly |
| Audit Trails | Table/object-level auditing with manual log review | Granular, rule-based auditing with real-time alerting and visual history tracking |
| Sensitive Data Protection | Column encryption only | Dynamic masking + encryption + automated discovery of sensitive fields |
| Compliance Reporting | Manual log extraction and formatting for audits | Automated, export-ready reports tailored to GDPR, HIPAA, SOX, PCI DSS |
| Threat Detection | Limited to periodic manual checks | Behavioral analytics, anomaly detection, and instant notifications for high-risk events |
| Scalability & Consistency | Policies must be recreated for each server | Single interface for managing all Sybase instances and scaling governance policies efficiently |
Conclusion
Sybase ASE provides strong foundational tools for data governance — including role-based access, auditing, integrity constraints, and encryption. However, achieving enterprise-grade governance with streamlined compliance processes requires extending these native features.
DataSunrise transforms Sybase governance from a collection of manual processes into an automated, centralized, and intelligent framework. By combining real-time monitoring, dynamic masking, and advanced reporting, organizations can minimize compliance risks, enhance operational efficiency, and protect sensitive data more effectively.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now