Vertica Regulatory Compliance
Vertica regulatory compliance requires organizations to discover, protect, and monitor the sensitive information stored inside Vertica. Since Vertica often functions as a high-performance analytical warehouse, it quickly accumulates large volumes of regulated data such as personal identifiers, payment details, and operational activity records. Therefore, teams need both native Vertica controls and specialized tooling to align their environments with frameworks like GDPR, HIPAA, PCI DSS, SOX, and CCPA.
DataSunrise helps Vertica teams meet these obligations by combining automated discovery, masking, auditing, and reporting within a single platform. Throughout this article, we highlight which regulations typically apply to Vertica, what native features exist, and how DataSunrise enhances them to support real compliance workflows. For additional guidance on continuous compliance workflows, see the DataSunrise Compliance Manager documentation.
Why Compliance Matters for Vertica
Vertica frequently serves as the analytical backbone for BI dashboards, reporting platforms, and data marts. These workloads often merge data from several operational systems, which means regulated content ends up consolidated inside Vertica. As a result, a single Vertica environment may contain cardholder information, healthcare data, authentication logs, and personal identifiers. Without proper controls, it becomes difficult to prove that access is limited, monitored, and justified.
Regulations expect more than basic permissions. They require clear visibility into access events, verifiable masking for sensitive fields, and strong retention and deletion policies. Consequently, Vertica environments that store regulated data need a combination of discovery, protection, and auditing tools to align with compliance requirements.
Key Regulatory Frameworks Affecting Vertica
A Vertica deployment often touches several compliance frameworks, including:
- GDPR: Protects personal data, enforces data-subject rights, and demands transparent processing records. Related guidance: GDPR Info.
- HIPAA: Requires safeguards for PHI, including auditability, access logging, and security controls. Documentation: CDC HIPAA overview.
- PCI DSS: Mandates strict protection of cardholder data, including masking, logging, and controlled access. Reference: PCI DSS Library.
- SOX: Requires reliable audit trails, change monitoring, and evidence of financial integrity controls.
- CCPA: Focuses on consumer privacy, transparency, and access control around personal information.
Although these frameworks differ, they share common technical expectations: discover sensitive data, enforce least privilege, monitor usage, and provide evidence that controls work as intended. Vertica delivers part of this foundation, but complete coverage usually requires complementary tooling.
Native Vertica Features for Compliance
Vertica includes several capabilities that support compliance efforts:
- Role-based access control (RBAC): Provides granular access control for schemas, tables, and views.
- TLS encryption: Protects data transmitted between clients and Vertica nodes.
- Authentication integration: Supports LDAP, Kerberos, and local accounts for consistent identity policy enforcement.
- Monitoring views: Tables such as
v_monitor.query_requestsandv_monitor.sessionsreveal query activity and session details.
Despite these strengths, Vertica does not automatically classify sensitive data, apply masking, or generate compliance-ready documentation. It also stores logs locally, which complicates large-scale or multi-cluster analysis. Therefore, teams often require a dedicated compliance platform to unify controls and provide consistent monitoring.
Discovering Sensitive Data in Vertica with DataSunrise
Regulatory alignment always begins with identifying where sensitive data resides. DataSunrise automates discovery across Vertica schemas and recognizes personal identifiers, financial attributes, healthcare fields, and other regulated values. This capability significantly reduces manual assessment time while improving scoping accuracy for compliance enforcement.
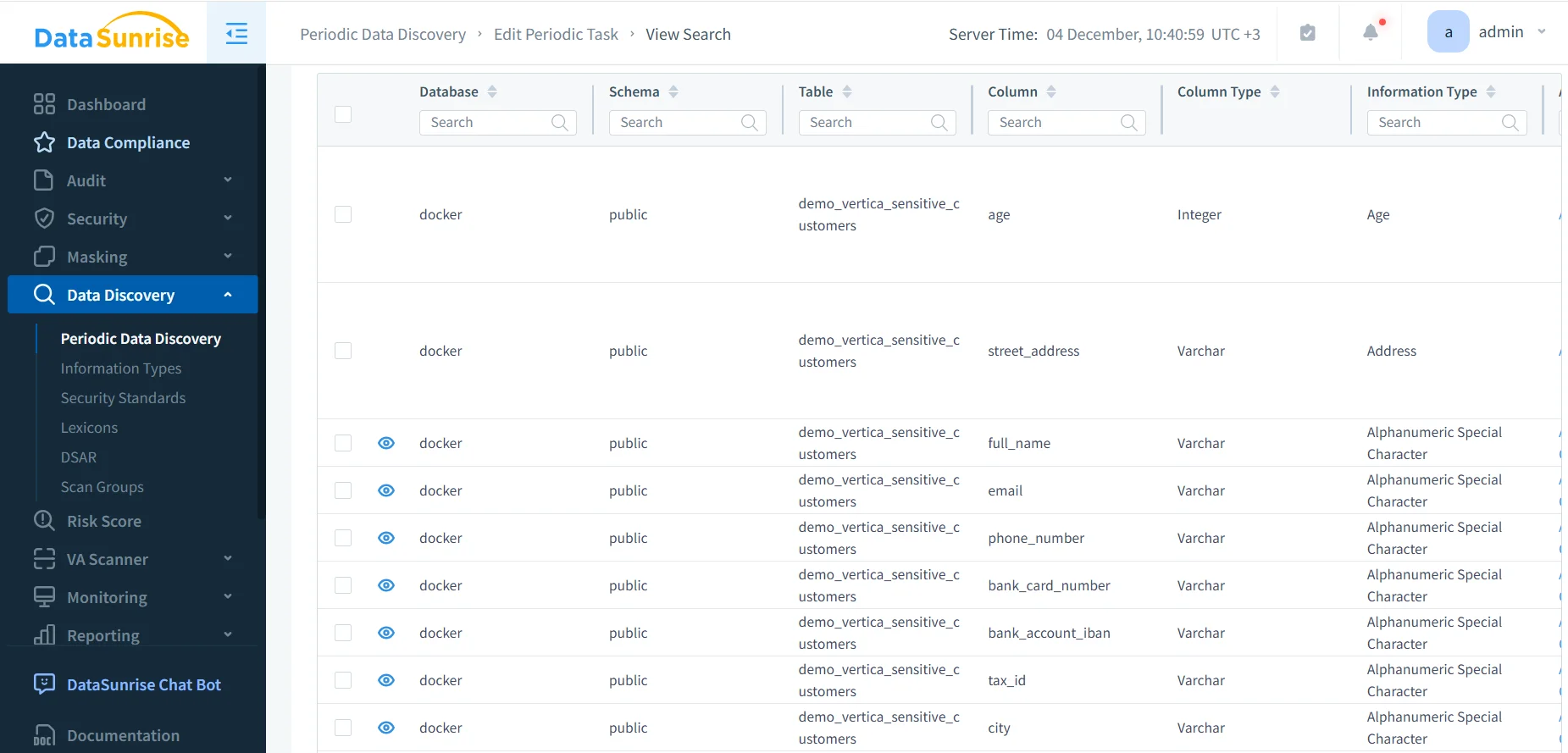
When DataSunrise identifies sensitive fields, teams can immediately apply masking rules, refine access control, or extend auditing. Because discovery results integrate directly into Compliance Manager, Vertica regulatory compliance becomes a continuous and auditable process.
Configuring Vertica Compliance Tasks
After sensitive data is identified, organizations need a repeatable mechanism for assessing compliance posture. DataSunrise provides compliance tasks that run on a schedule and verify whether Vertica still contains unprotected sensitive fields, overly permissive access, or incomplete audit logging. As a result, compliance verification becomes predictable and operationally consistent.
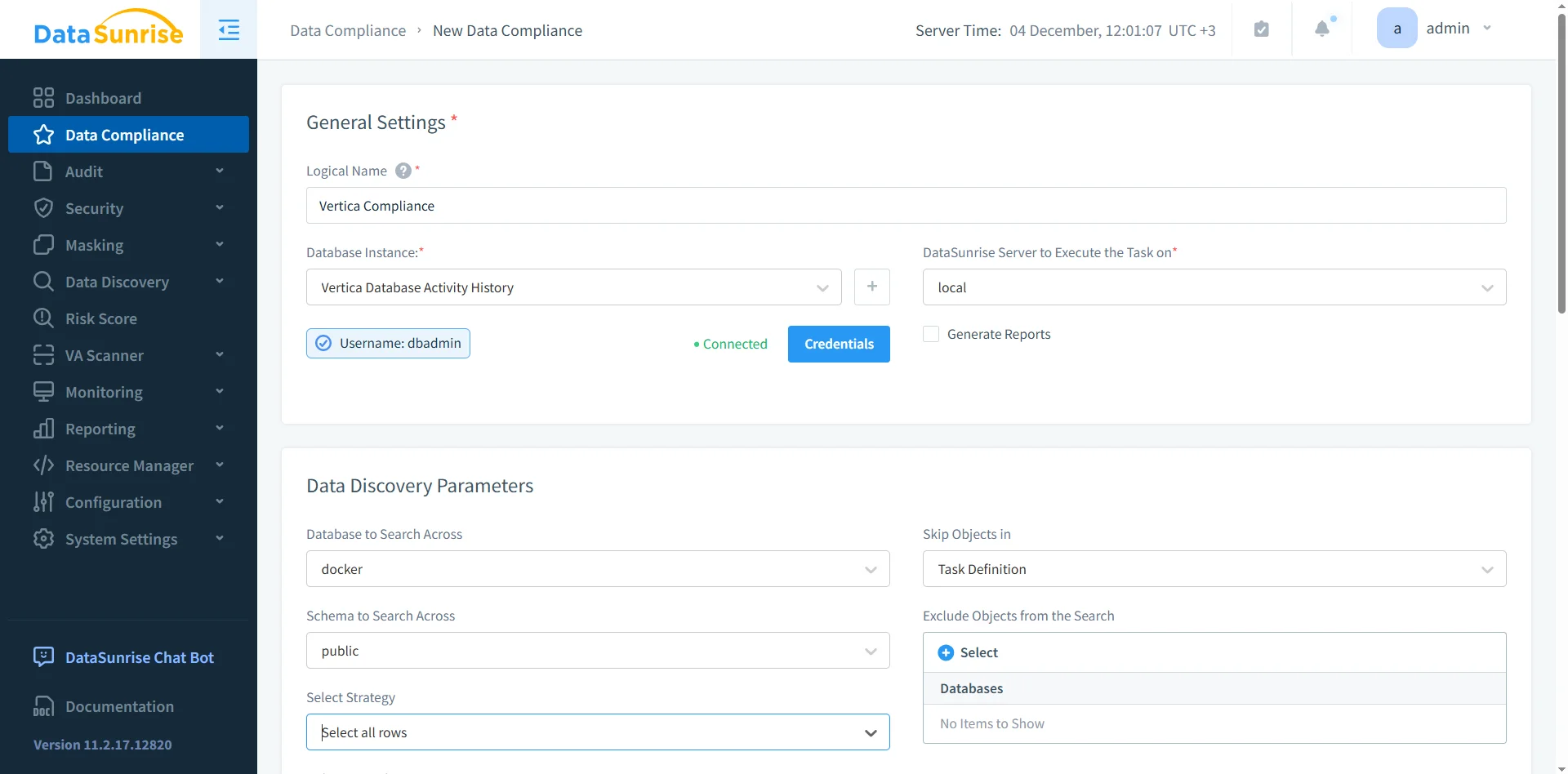
These tasks help identify missing masking policies, inconsistent access restrictions, and audit blind spots. They also produce an audit trail of compliance checks—something auditors frequently request. In combination with DataSunrise Sensitive Data Discovery, Masking, and Audit Logs, compliance tasks form a consistent control framework around Vertica data.
Compliance Capabilities Summary
The table below outlines how Vertica and DataSunrise fulfill key regulatory requirements.
| Requirement | Native Vertica | DataSunrise for Vertica |
|---|---|---|
| Identify sensitive data | Manual discovery | Automated classification and tagging |
| Restrict access | RBAC | Policy-based monitoring + masking |
| Monitor activity | v_monitor views + logs | Centralized event history with retention |
| Reduce exposure | Encryption in transit | Dynamic/static masking for PII, PCI, PHI |
| Compliance reporting | Manual exports | Compliance tasks + policy templates |
Best Practices for Vertica Regulatory Compliance
To keep Vertica deployments aligned with regulatory expectations, consider the following practices:
- Run sensitive-data discovery regularly to maintain an accurate inventory.
- Apply masking rules to high-risk Vertica columns, especially in development or shared environments.
- Combine RBAC with DataSunrise access policies to enforce least-privilege access.
- Centralize Vertica audit logs inside DataSunrise for investigations and compliance validation.
- Schedule compliance tasks and review their outcomes with security and governance teams.
Conclusion
Vertica provides valuable performance and security features; however, regulatory compliance requires more than native RBAC and logging. Organizations must continuously identify sensitive data, control access to it, monitor usage, and demonstrate consistent enforcement. DataSunrise augments Vertica with automated discovery, masking, auditing, and compliance reporting. Together, these tools create a unified Vertica regulatory compliance strategy that simplifies audits and strengthens data protection.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now