
What Is MariaDB Audit Trail

The term “What Is MariaDB Audit Trail” often evokes thoughts of static log files that no‑one ever reads until something goes wrong. In modern cloud‑native estates, however, an audit trail must be alive—streaming, searchable, and smart enough to spot threats in real time. In this article we explore how a MariaDB audit trail can evolve from a basic compliance checkbox into a dynamic pillar of information security. We will cover real‑time audit processing, dynamic masking, data discovery, security and regulatory alignment, plus hands‑on configuration for both the native MariaDB Audit Plugin and the DataSunrise platform, all while weaving in the emerging role of generative AI.
The Essence of a MariaDB Audit Trail
At its core, an audit trail is a chronological record that answers four questions: who did what, when, and from where. For databases the “what” is typically a SQL statement or a call to a privileged function. Collecting this information enables root‑cause analysis, fraud detection, and evidence‑grade compliance reporting. When paired with policy engines and alerting pipelines it becomes the nervous system of your data defense.
Key takeaway: The quality of decisions you can make during an incident is limited by the granularity and integrity of your audit trail.
Real‑Time Audit Meets Generative AI
Traditional audit pipelines write to disk and are batch‑processed hours later. Modern threats move in seconds. By streaming audit events to a message bus (e.g., Apache Kafka) you can feed them into a lightweight large‑language‑model (LLM) whose job is to label each event as benign, suspicious, or critical. The LLM is few‑shot‑prompted with examples of normal and malicious activity and continuously updated with feedback from analysts.
# toy example: classify audit events with OpenAI function calling
import openai, json, os
openai.api_key = os.getenv('OPENAI_API_KEY')
def classify_audit(event_json):
messages = [
{'role': 'system', 'content': 'You are a security LLM classifying MariaDB audit entries.'},
{'role': 'user', 'content': f"Event:\n{json.dumps(event_json, indent=2)}"}
]
response = openai.ChatCompletion.create(
model='gpt-4o-mini',
messages=messages,
functions=[{
'name': 'label_event',
'parameters': {
'type': 'object',
'properties': {
'label': {'enum': ['benign', 'suspicious', 'critical']}
}
}
}],
function_call={'name': 'label_event'}
)
return json.loads(response.choices[0].message.function_call.arguments)['label']
In practice you would stream‑ingest the MariaDB audit log, call classify_audit, and push critical events into PagerDuty or Slack. The payoff is reduced analyst fatigue—humans review only a fraction of events, yet nothing is ignored.
Discovering and Masking Sensitive Data on the Fly
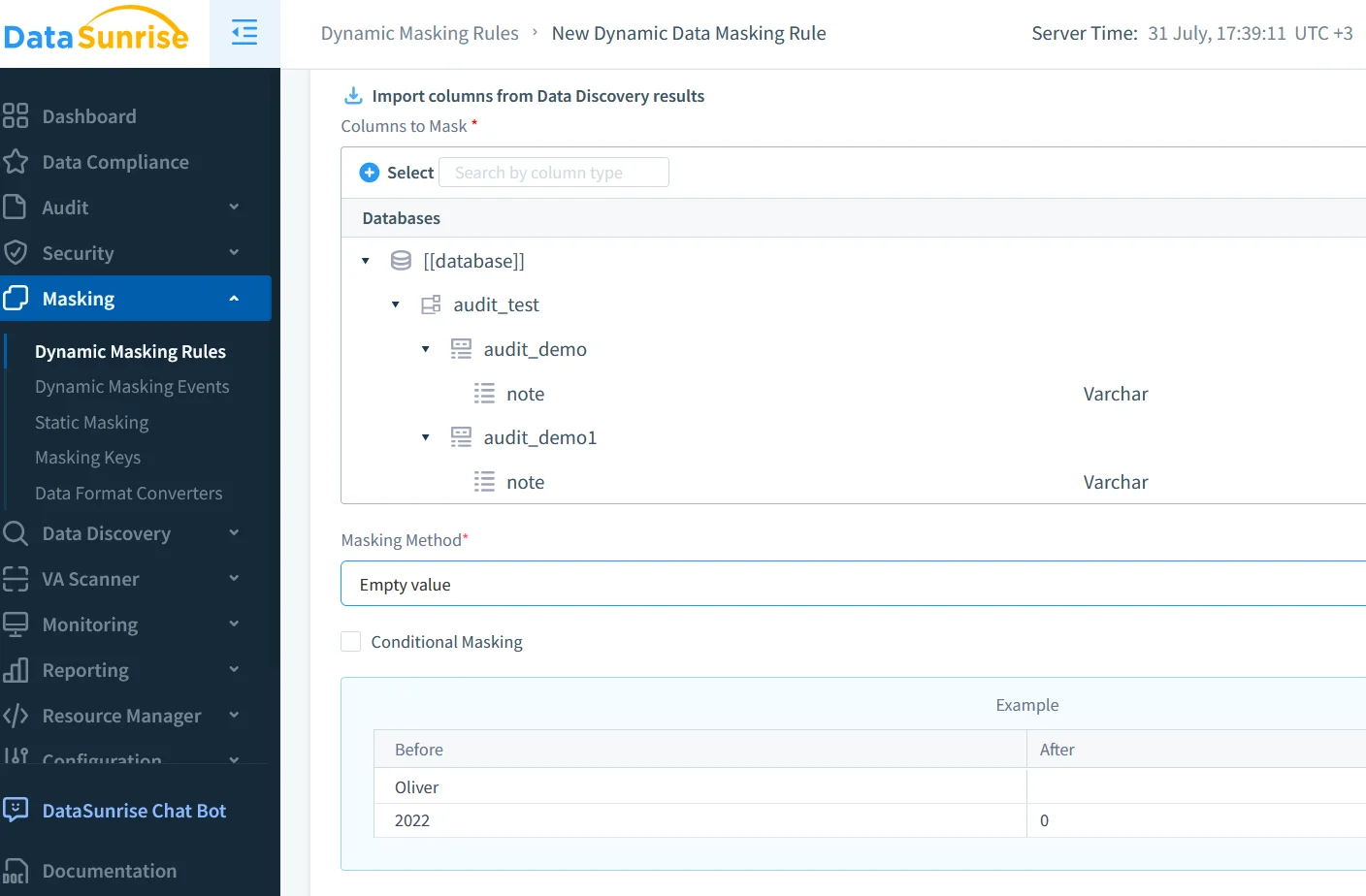
An audit trail is only as useful as the context around it. Integrating data discovery—automatically finding PII and business secrets—helps you understand the blast radius of a leaked query. Once sensitive columns are tagged, dynamic masking can hide their real values in query results while still logging the access. Tools such as DataSunrise support policy‑based masking that activates when an audit rule and a data classification rule match. See Data Discovery and Dynamic Data Masking for deeper dives.
A real‑time pipeline could look like this:
- Log event → 2. LLM label → 3. Mask response if needed → 4. Store & alert
Because masking is applied after the query is parsed but before results leave the server, legitimate analytics work continues uninterrupted while regulators stay happy.
Security and Compliance Convergence
Whether you answer to GDPR, PCI‑DSS, or HIPAA, an audit trail must prove that controls are effective. Frameworks such as NIST 800‑92 recommend:
- Immutable storage with retention equal to (or greater than) the statutory period;
- Cryptographic integrity checks;
- Role‑based access to audit data;
- Automated report generation.
Platforms such as DataSunrise ship pre‑built compliance dashboards inspired by GDPR and PCI DSS so auditors can self‑serve evidence without waiting for DBA support. On the MariaDB side, native logs can be shipped to Syslog or AWS CloudWatch and then archived to S3 Glacier with object‑lock to satisfy immutability requirements.
Configuring the Native MariaDB Audit Trail
MariaDB ships a GPL‑licensed Audit Plugin that captures connection, query, and table access events. The quickest way to enable it is through the plugin library that matches your server version.
-- 1. Load the plugin
INSTALL SONAME 'server_audit';
-- 2. Choose what to record
SET GLOBAL server_audit_events = 'CONNECT,QUERY,TABLE';
-- 3. Decide where logs go (FILE,SYSLOG,JSON)
SET GLOBAL server_audit_output_type = 'JSON';
-- 4. Protect the config
GRANT SELECT ON mysql.server_audit_log TO 'auditor'@'%';
-- 5. Persist across restarts
SET PERSIST server_audit = ON;
The plugin writes JSON lines like:
{ 'ts': '2025-07-30 12:41:07', 'id': 2, 'user': 'app', 'host': '10.0.0.12',
'query': 'SELECT card_no FROM payments WHERE id=42;' }
From here you can tail -F /var/lib/mysql/server_audit.log | jq or forward the file to your SIEM. Full documentation lives at the MariaDB Audit Plugin Reference. For a holistic overview of audit capabilities, consult the MariaDB Server Audit Overview. To fine‑tune behaviour, see the server_audit System Variables Reference and MariaDB's guidance on Forwarding Audit Events to Syslog for secure off‑host shipping.com/kb/en/audit-plugin/).
Tip: Separate administrative logs (CONNECT) from business logs (QUERY,TABLE) by sending them to different destinations—this avoids drowning incident responders in noise.
Augmenting Native Logs with DataSunrise
While the native plugin delivers raw events, DataSunrise Audit adds policy layers, self‑service dashboards, and machine‑learning‑driven baselines. A minimal setup involves:
- Deploying DataSunrise in proxy mode between applications and MariaDB.
- Adding a new Database Instance → MariaDB and importing credentials.
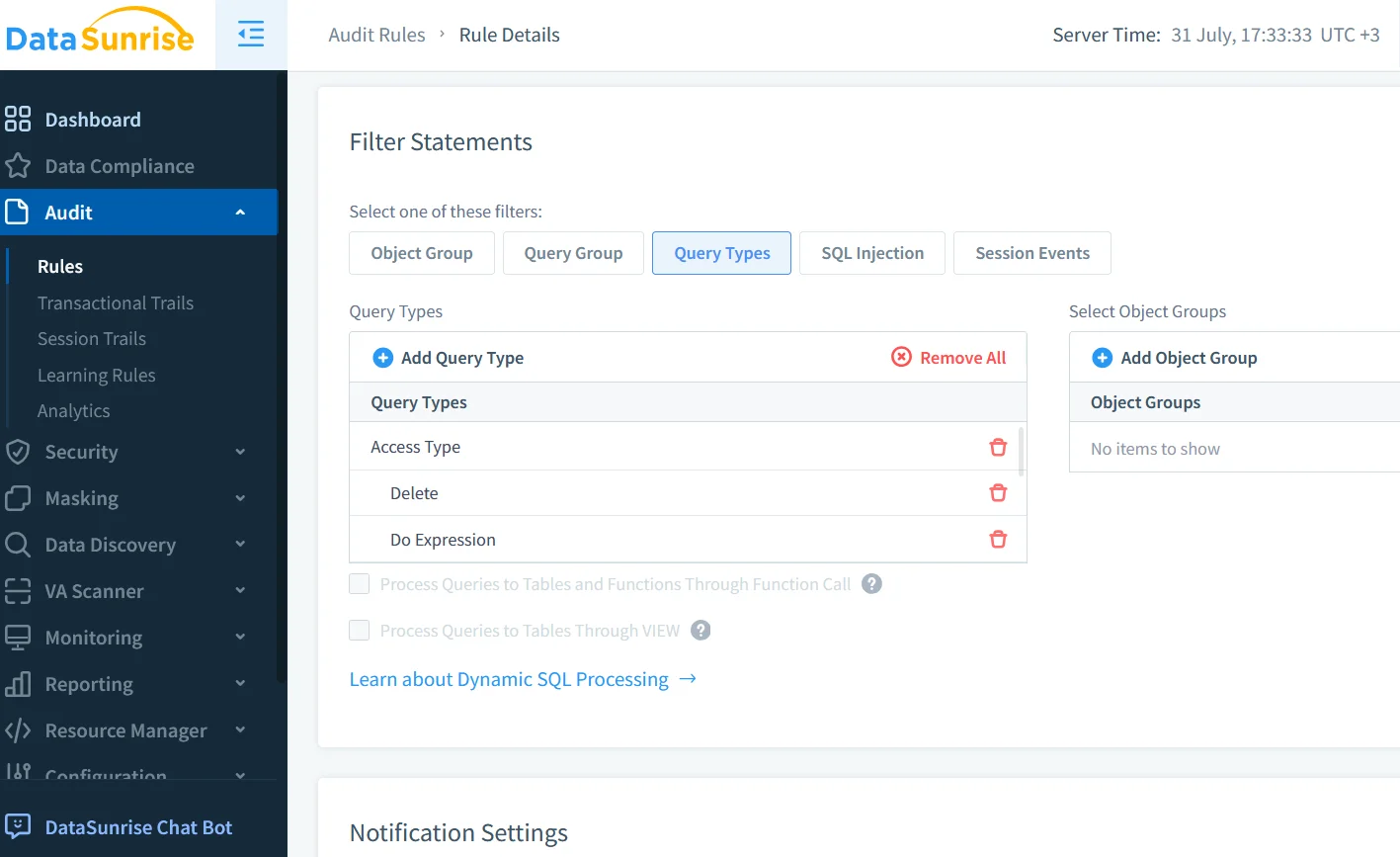
- Creating an Audit Rule that logs any
UPDATEorDELETEagainstfinance.*tables.
- Linking a Dynamic Masking policy that hides
card_nounless the user’s role isops_analyst. - Enabling Real‑Time Notifications with the built‑in Slack integration so critical events are delivered instantly.
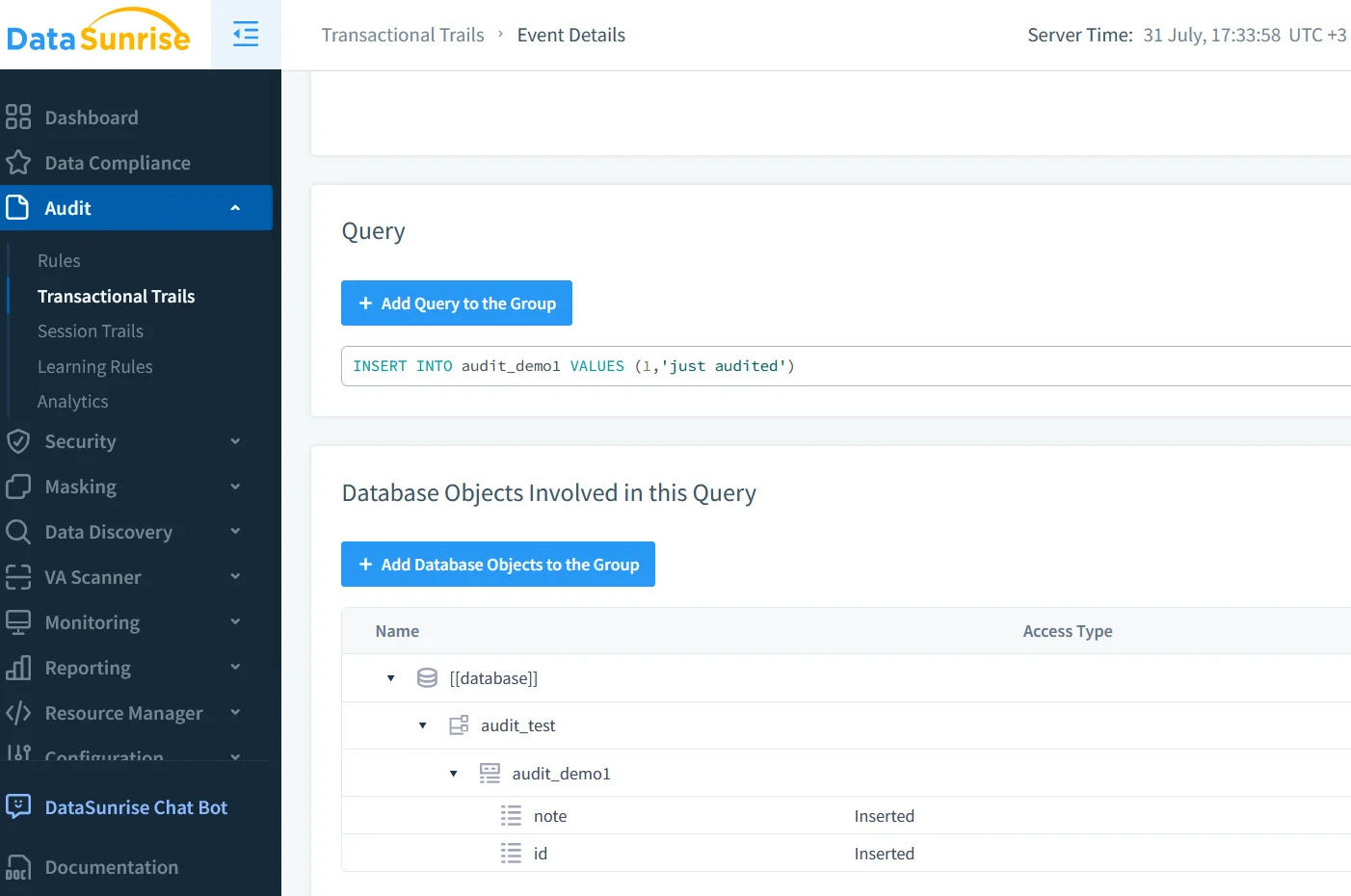
Detailed walkthroughs are in the Audit Guide and Audit Logs resources. DataSunrise writes its own structured log but can also consume the native MariaDB plugin via a built‑in collector, giving you a single pane of glass.
Capability Matrix at a Glance
| Capability | Native MariaDB Audit Plugin | DataSunrise Audit | GenAI-Augmented Pipeline |
|---|---|---|---|
| Real-time Streaming | File/Syslog; external forwarders | Built-in streaming proxy | Kafka → LLM classification in seconds |
| Dynamic Masking | — | Column-level, role-aware | Via DataSunrise policies or SQL wrappers |
| Sensitive Data Discovery | — | Automated discovery & regex libraries | LLM-based tag enrichment |
| Compliance Dashboards | Manual scripting | Pre-built PCI, GDPR, HIPAA | Custom LLM-generated reports |
| ML/Anomaly Detection | SIEM correlation rules | Behaviour-based baselining | Token-level LLM labelling & alerting |
Tiny Demo: Let GenAI Spot Suspicious Patterns
Imagine DataSunrise passes the JSON event below to your LLM pipeline:
{ 'user': 'app_readonly', 'ip': '192.168.3.77', 'object': 'payroll.employee_salary',
'statement': 'SELECT * FROM payroll.employee_salary', 'rows': 50000 }
The earlier classify_audit function may call this event critical because app_readonly should never query payroll data. A Slack message like “ Critical: payroll data exfiltration attempt by app_readonly (50 000 rows)” is posted within seconds, giving IR teams a head start.
Because events from both the native plugin and DataSunrise share a common JSON schema, your AI can learn once and protect many pipelines.
Takeaways
- What Is MariaDB Audit Trail today? It is a fusion of native plugin telemetry, DataSunrise intelligence, and generative AI that transforms raw logs into actionable insights.
- Real‑time streaming, sensitive‑data discovery, and dynamic masking shrink the window of exposure without slowing engineers down.
- Compliance reporting becomes a by‑product of well‑structured audit data—no midnight spreadsheet marathons.
- A few SQL commands enable the native plugin, while DataSunrise layers on advanced policy control and cloud‑ready dashboards.
- Generative AI closes the loop by contextualising events faster than human‑only teams could ever hope to.
By treating your audit trail as a living security service rather than a static archive, you not only answer “What Is MariaDB Audit Trail” but also demonstrate how it future‑proofs your data strategy against evolving threats and regulations.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now