
Machine Learning for Cybersecurity Defense

As digital threats evolve at unprecedented scale, organizations worldwide are implementing machine learning systems to defend against sophisticated cyber attacks. While ML delivers transformative defense capabilities, it introduces complex security implementation challenges that traditional cybersecurity frameworks cannot adequately address.
This guide examines machine learning for cybersecurity defense, exploring implementation strategies that enable organizations to deploy intelligent, adaptive security systems while maintaining operational excellence.
DataSunrise's cutting-edge ML-powered cybersecurity platform delivers Zero-Touch Defense Orchestration with Autonomous Threat Detection across all major security infrastructures. Our Context-Aware Protection seamlessly integrates machine learning capabilities with technical controls, providing Surgical Precision security management for comprehensive cyber defense.
Understanding Machine Learning in Cybersecurity Defense
Machine learning transforms cybersecurity from reactive signature-based detection to proactive, intelligent threat prevention. Unlike traditional security systems that rely on predefined rules, ML algorithms continuously learn from network behavior, user patterns, and attack vectors to identify emerging threats in real-time.
Modern ML-powered defense systems encompass behavioral analytics, anomaly detection, predictive threat modeling, and automated incident response. These systems provide continuous data protection while adapting to evolving attack strategies through comprehensive audit capabilities and data value optimization.
Critical Machine Learning Defense Applications
Behavioral Analytics and Anomaly Detection
ML algorithms establish baseline patterns of normal network activity, user behavior, and system operations. Advanced behavioral detection analytics leverage machine learning to dynamically adapt and learn from new data, enhancing accuracy in recognizing evolving threats that traditional rule-based methods would miss. Organizations must implement data accessibility controls and learning rules and audit procedures for effective threat identification.
Intelligent Malware Detection
ML models analyze file behavior, system interactions, and code patterns to identify previously unknown malware variants. AI-based malware detection uses machine learning algorithms to identify malicious software by analyzing file behavior and system changes, helping prevent malware that frequently changes its code. This requires database encryption and comprehensive security threats mitigation strategies.
Predictive Threat Intelligence
ML systems analyze historical attack patterns and vulnerability data to predict future attack vectors. This shifts cybersecurity from reactive to proactive, enabling organizations to strengthen defenses before attacks occur. Organizations need data-driven testing capabilities and reverse proxy protection for comprehensive threat intelligence.
Implementation Examples
Network Anomaly Detection
This example demonstrates real-time network threat detection using machine learning. The Isolation Forest algorithm works by isolating anomalies in network traffic data without requiring pre-labeled examples of attacks. It builds decision trees that separate normal traffic patterns from suspicious activities by analyzing features like packet sizes, connection durations, and failed login attempts. The algorithm assigns anomaly scores where lower scores indicate higher threat levels.
import numpy as np
from sklearn.ensemble import IsolationForest
class MLAnomalyDetector:
def __init__(self):
self.model = IsolationForest(contamination=0.1, random_state=42)
def detect_threat(self, network_activity):
"""Detect network threats using ML anomaly detection"""
features = np.array([[
network_activity.get('packet_size', 0),
network_activity.get('connection_duration', 0),
network_activity.get('failed_logins', 0)
]])
anomaly_score = self.model.decision_function(features)[0]
is_threat = self.model.predict(features)[0] == -1
return {
"threat_detected": bool(is_threat),
"risk_level": "HIGH" if anomaly_score < -0.5 else "LOW"
}
Behavioral Analysis System
This implementation showcases insider threat detection through user behavior analysis. The system creates behavioral baselines by tracking user login patterns, data access volumes, and system usage. It calculates deviation scores by comparing current behavior against established patterns. Higher deviations indicate potential security risks such as compromised accounts or malicious insider activities.
class BehaviorAnalyzer:
def __init__(self):
self.user_baselines = {}
def analyze_user_risk(self, user_id, current_activity):
"""Analyze user behavior for insider threat detection"""
if user_id not in self.user_baselines:
self.user_baselines[user_id] = current_activity
return {"risk_score": 0.0, "status": "baseline_created"}
baseline = self.user_baselines[user_id]
deviation = abs(current_activity['data_accessed'] - baseline['data_accessed'])
risk_score = min(deviation / baseline['data_accessed'], 1.0)
return {
"risk_score": risk_score,
"alert_level": "HIGH" if risk_score > 0.7 else "LOW"
}
Implementation Best Practices
For Organizations:
- Layered ML Defense: Implement multiple ML models addressing different threat vectors with test data management protocols
- Continuous Learning: Deploy systems that adapt to evolving threats through ongoing training and least privilege principles
- Human-AI Collaboration: Combine ML automation with human expertise for optimal threat response
- Performance Monitoring: Maintain model accuracy through regular evaluation and compliance regulations adherence
For Technical Teams:
- Data Quality Management: Ensure high-quality training data with data discovery capabilities and audit storage optimization
- Model Explainability: Implement interpretable ML models for regulatory compliance and report generation
- Adversarial Robustness: Protect ML models against adversarial attacks and data breach prevention
- Integration Architecture: Seamlessly integrate ML capabilities with existing security infrastructure using advanced table relations management
DataSunrise: Comprehensive ML-Powered Cybersecurity Solution
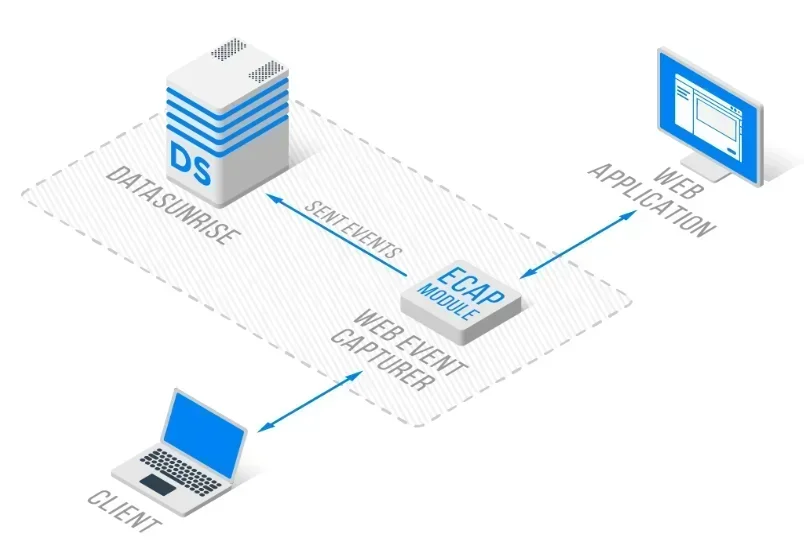
DataSunrise provides enterprise-grade machine learning cybersecurity solutions designed specifically for modern threat landscapes. Our platform delivers AI Compliance by Default with Maximum Security, Minimum Risk across all major security infrastructures.
Key Features:
- Advanced ML Threat Detection: Real-Time AI Activity Monitoring with Suspicious Behavior Detection using machine learning algorithms
- Behavioral Analytics Engine: Context-Aware Protection with comprehensive user behavior analysis
- Automated Response Systems: Surgical Precision incident response with real-time notifications
- Cross-Platform Coverage: Unified security across 50+ supported platforms
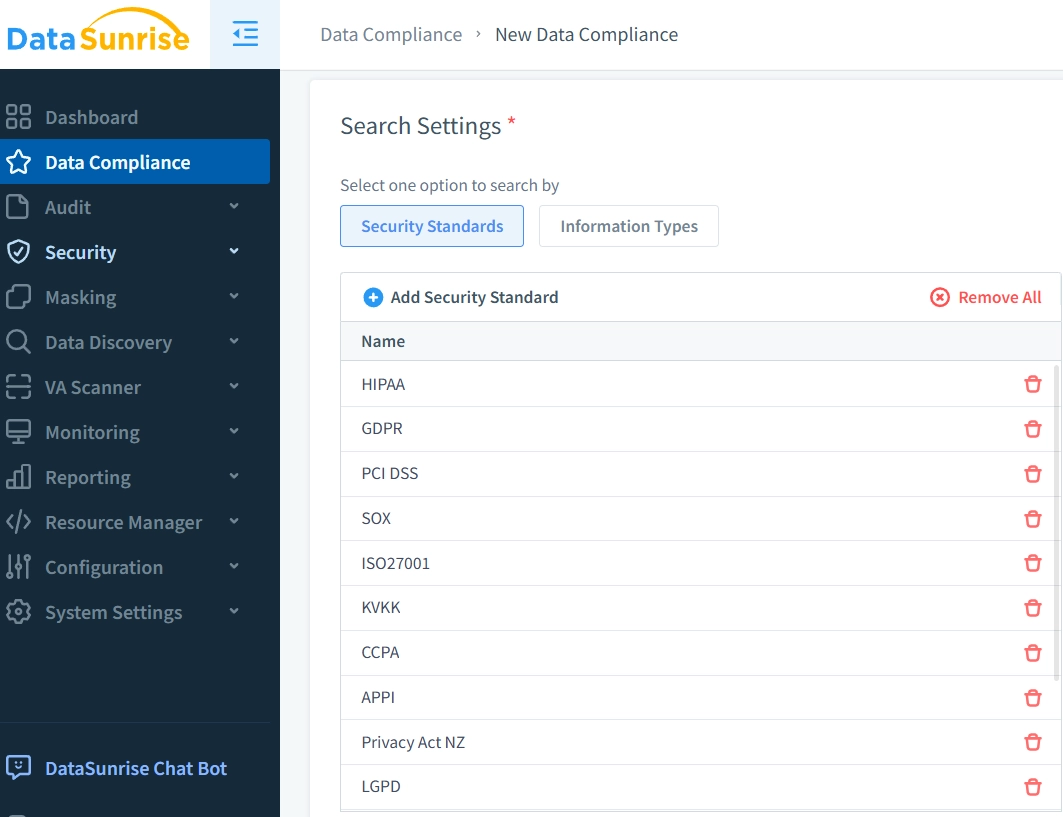
DataSunrise's Flexible Deployment Modes support on-premise, cloud, and hybrid environments with Zero-Touch Implementation. Organizations achieve significant reduction in threat detection time through automated ML-powered monitoring.
Challenges and Future Trends
Machine learning cybersecurity faces several challenges including data quality requirements, adversarial attacks, and model interpretability needs. However, emerging trends show promise:
- Federated Learning: Collaborative threat intelligence without sharing sensitive data
- Explainable AI: Transparent ML models for regulatory compliance
- Edge ML Security: Distributed intelligence for IoT device protection
Conclusion: Transforming Cybersecurity Through Machine Learning
Machine learning represents a fundamental shift in cybersecurity defense, enabling organizations to move from reactive protection to proactive threat prevention. By implementing comprehensive ML-powered security frameworks, organizations can significantly enhance their defense capabilities while maintaining operational efficiency.
As cyber threats continue to evolve, machine learning becomes not just an enhancement but an essential component of modern cybersecurity defense. Organizations that master machine learning for cybersecurity will be best positioned to protect their assets in an increasingly dangerous digital landscape.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now