
Amazon S3 Audit trail

Introduction
As organizations scale their cloud footprint, Amazon S3 becomes the central repository for logs, machine learning datasets, archives, and high-risk business documents. Yet, while storage is easy, oversight isn't. A formal audit trail for Amazon S3 ensures that every access, write, deletion, and permission change is traceable—automatically.
Unlike traditional databases, S3 lacks transactional state. There’s no “session”—just stateless API calls. That makes audit trails critical for detecting misuse, proving compliance, and enforcing governance in distributed, multi-role environments.
The Architecture of Amazon S3 Audit Trail
An audit trail for Amazon S3 must answer three core questions:
- Who accessed the object?
- What was the operation?
- Where did it originate from?
AWS provides raw telemetry via CloudTrail, but this alone isn’t an audit trail. Logs exist, but insight does not.
A complete audit trail includes:
- Unified capture of read/write/delete actions
- Interpretation of access control changes (ACLs, bucket policies, IAM roles)
- Cross-account activity correlation
- Context-aware tagging of sensitive object access
Challenges with S3 Logging Alone
Even with CloudTrail and S3 Server Access Logs enabled, major gaps remain:
| Audit Requirement | Native Capability |
|---|---|
| Change history of bucket permissions | Partial (IAM only) |
| Object-level masking during audits | ❌ Not supported |
| File content inspection for sensitivity | ❌ External tooling required |
| Unified view across accounts/regions | ❌ Manual setup |
| Alerting on access anomalies | ❌ Requires Lambda/SIEM |
| Compliance export with object lineage | ❌ Not available |
These limitations lead to fragmented visibility—especially for security teams managing multiple buckets across environments or linked AWS Organizations.
Going Beyond Logging: DataSunrise-Powered Amazon S3 Audit Trails
DataSunrise transforms S3 telemetry into a contextual audit trail, adding structure, tagging, and real-time enrichment. Instead of just recording access events, DataSunrise performs deep inspection, policy validation, and behavioral correlation.
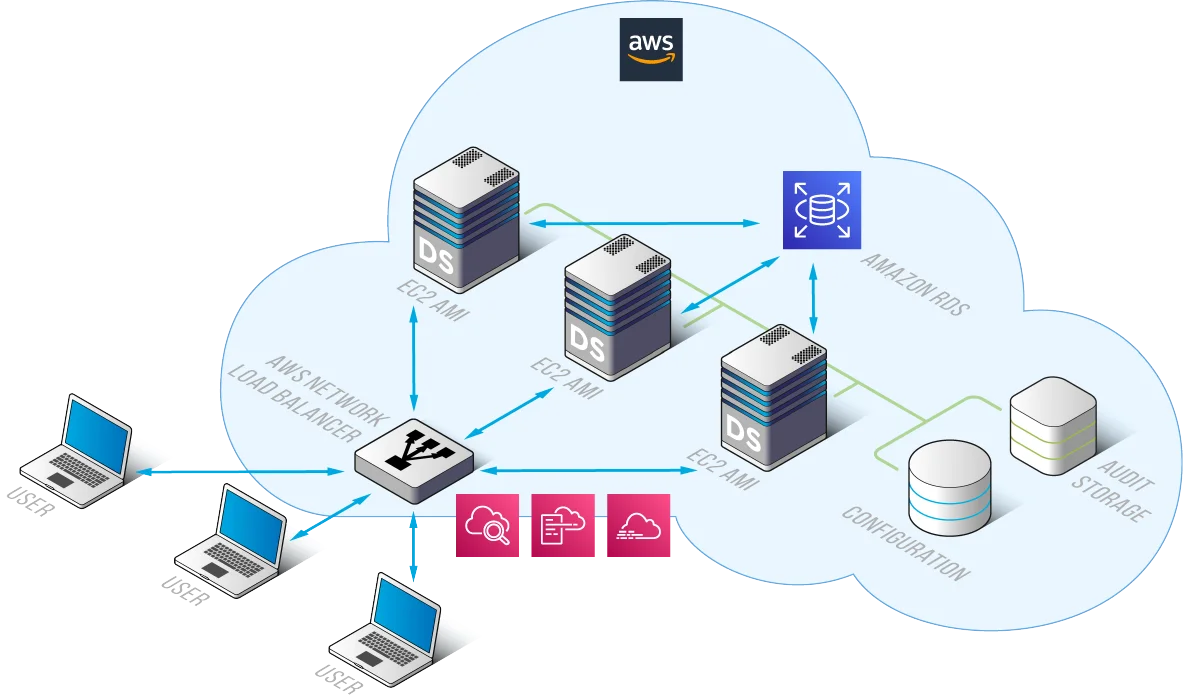
Key Capabilities
- Sensitive Data Discovery: Automatically scan buckets to classify PII, PHI, and PCI content using pattern recognition and OCR-driven inspection.
- Behavioral Correlation: Identify anomalies by correlating IP origin, access volume, user type, and time-of-day patterns.
- Policy-Enforced Trails: Generate audit logs only when accesses intersect with defined security policies, reducing noise.
- Tag-Aware Audit Events: Label and track objects based on custom or auto-discovered sensitive data tags.
Cross-Platform Integration: S3, RDS, Redshift, and More
DataSunrise supports hybrid environments. While auditing S3 access, it can also correlate activity from:
- Amazon RDS
- Redshift
- DynamoDB
- MongoDB and file systems
This unified security framework helps trace data flows across platforms, ensuring compliance mapping for frameworks like GDPR, HIPAA, and PCI DSS.
Enabling Smart Amazon S3 Audit Trails with DataSunrise
DataSunrise transforms Amazon S3 activity into a structured audit trail, not just logs. It inspects content, contextualizes access, and generates audit events aligned to your policies.
With a non-intrusive proxy mode or event stream integration, DataSunrise adds policy enforcement without requiring changes to S3 configurations.
Audit Trail Sample (With Context)
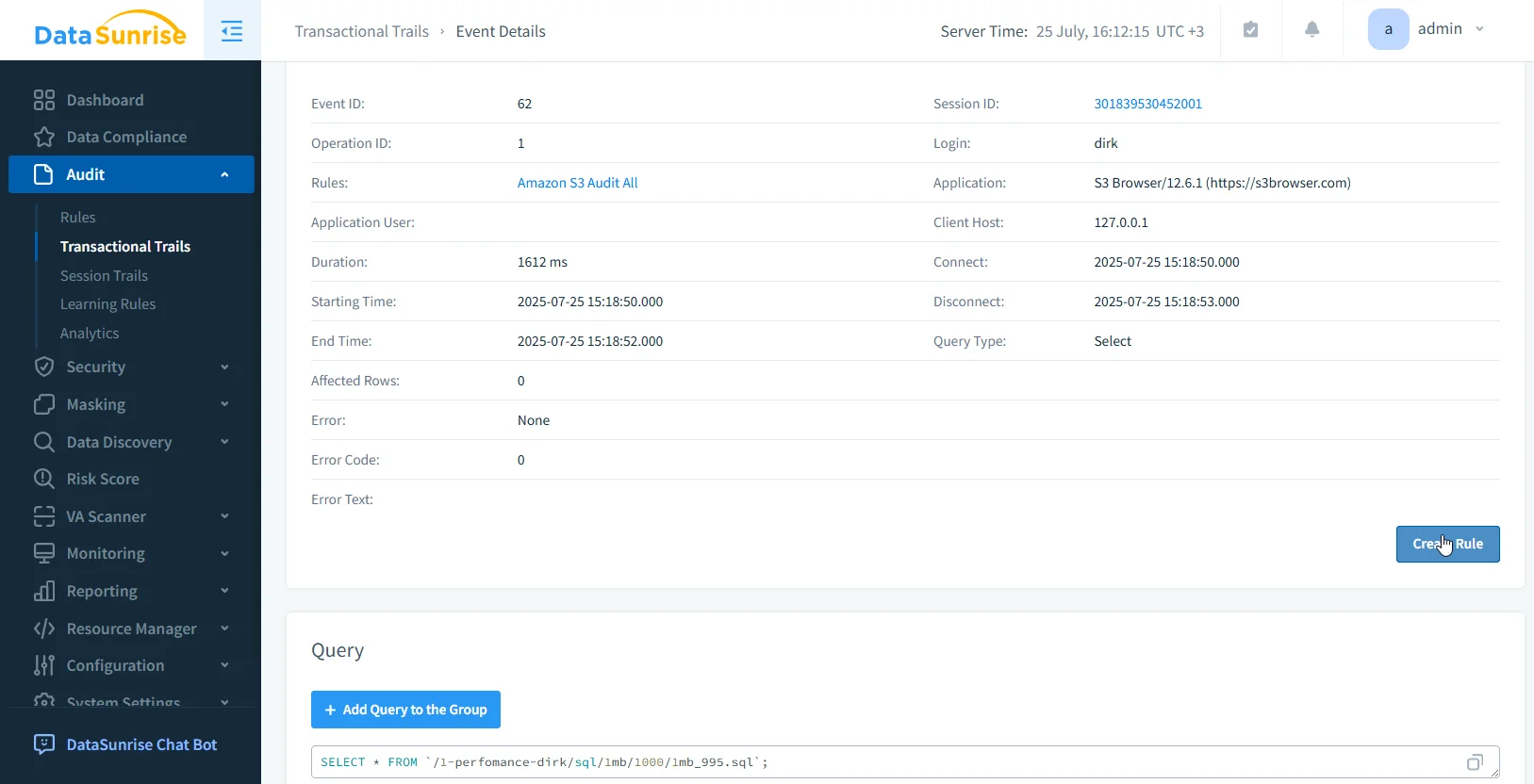
This level of detail is not available in native logs. It comes from combining access metadata with data classification and custom audit rules.
Highlights
- Behavior-based tracking: Audit not just the event, but the user profile, IP origin, time pattern, and volume trends
- Policy-aware trails: See not only what was accessed, but whether it was allowed under internal compliance controls
- Multi-bucket intelligence: Connect audit activity across teams, buckets, and VPCs—whether public, private, or cross-account
- Data tagging trails: Automatically track which files match sensitive data patterns (PII, PCI, PHI) and who accessed them
Integration & Deployment
DataSunrise supports multiple S3 auditing models:
- Proxy-based deployment: Intercepts traffic via reverse proxy
- CloudTrail parsing connector: Parses existing CloudTrail logs and enriches them with data context
- Hybrid visibility: Correlate S3 access with RDS, Redshift, MongoDB, and file storage in one place
You can start in audit-only mode, then enable data masking or threat prevention as needed—all without interrupting operations.
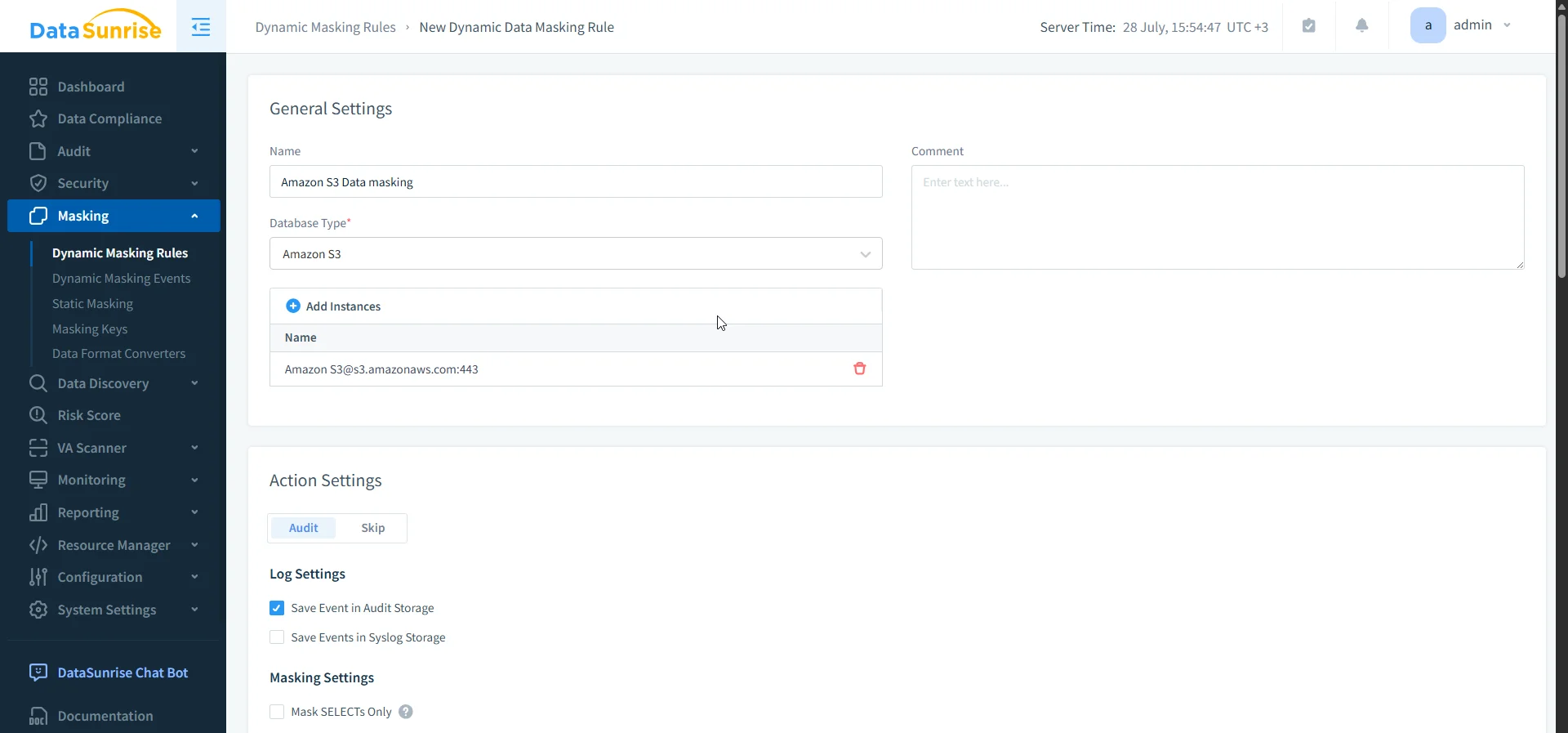
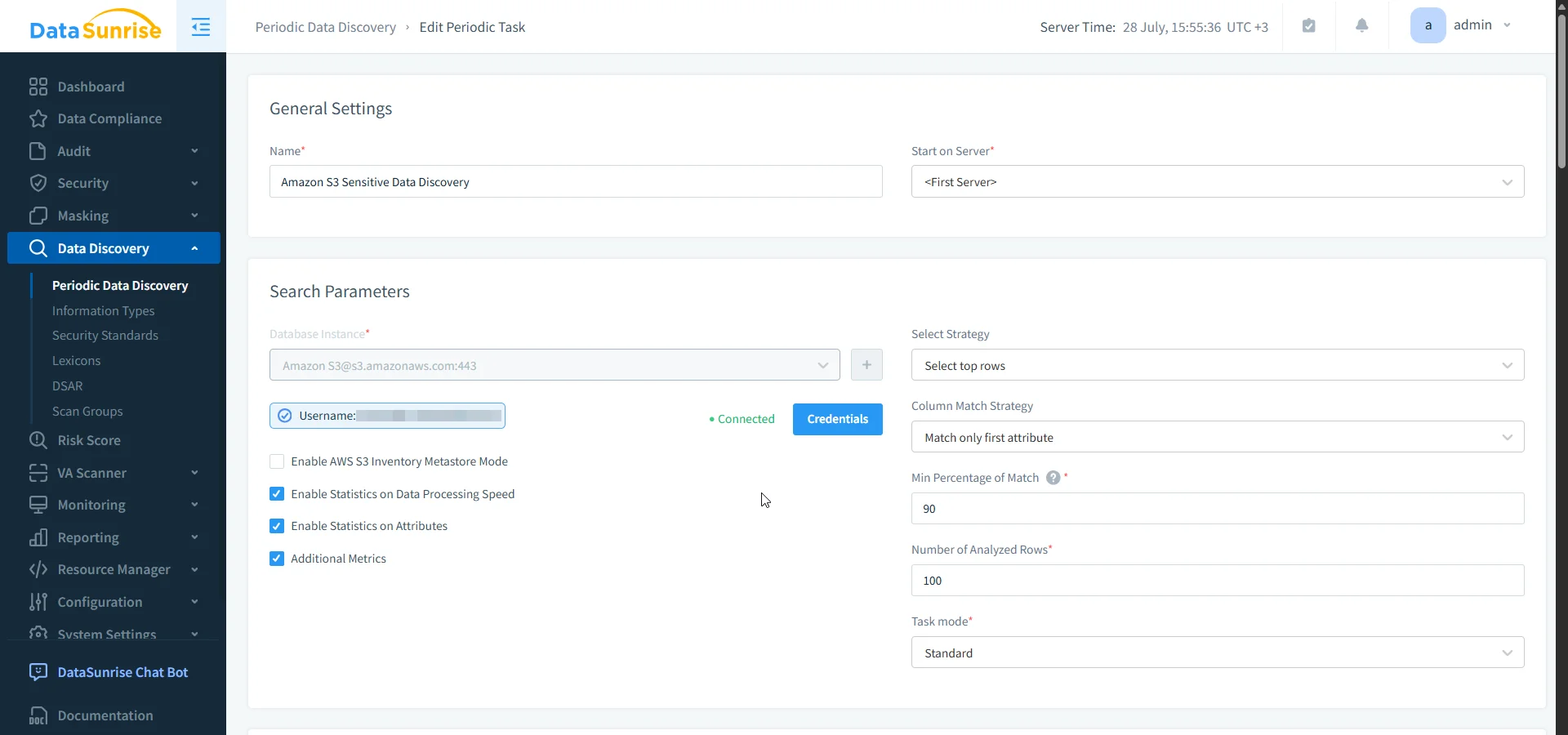
In addition, DataSunrise includes a robust sensitive data discovery engine that automatically classifies S3 objects containing regulated content like PII, PHI, and PCI data. It applies OCR and NLP-driven detection methods to unstructured and semi-structured content, helping security teams label, audit, and protect high-risk files at scale.
With support for over 50 platforms, DataSunrise integrates easily into existing pipelines.
Business Impact of S3 Audit Trails with DataSunrise
| Benefit | With Native AWS Tools | With DataSunrise |
|---|---|---|
| Object Access Tracking | CloudTrail only | Policy-enforced event trails |
| Real-Time Alerts | SIEM integration needed | Out-of-the-box alerts |
| Cross-Platform Visibility | Manual correlation | Unified audit platform |
| Sensitive Data Discovery | ❌ Not available | Built-in PII/PHI/PCI detection |
| Dynamic Data Masking | ❌ Not supported | Dynamic masking rules with multiple filters |
Final Thoughts
An audit trail for Amazon S3 isn’t just a security requirement—it’s a visibility framework. CloudTrail shows you what happened, but doesn’t answer why, should it have, or what’s at risk. That’s where platforms like DataSunrise step in.
They provide full-stack, policy-enforced, real-time audit trails that make S3 governance not only possible—but automated.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now