
Data Audit for AlloyDB for PostgreSQL

AlloyDB for PostgreSQL gives engineering teams the transactional power of PostgreSQL combined with Google Cloud elasticity. Yet the more critical workloads you migrate, the louder regulators and security architects ask a simple question: How can we prove that every data touch is legitimate? Data Audit for AlloyDB for PostgreSQL is the answer. It delivers continuous evidence for compliance, blocks insider misuse in real time, and transforms raw logs into executive‑level insight.
Why Modern Workloads Need Continuous Audit
Traditional nightly log rotation is too slow for today’s event‑driven applications. Micro‑services, data‑science notebooks, and external partners generate thousands of SQL statements per second. Without an always‑on audit pipeline you risk silent data leakage, unenforced least‑privilege policies, and costly post‑incident forensics. AlloyDB ships with the same pg_audit extension familiar to PostgreSQL admins, and the platform streams every entry into Cloud Logging, where it can be filtered, routed, and stored indefinitely. According to Google’s own Cloud Audit Logs guide, every AlloyDB event is retained for at least 400 days, ensuring a chain of custody.
From Logs to Live Telemetry: Real‑Time Audit Streams
AlloyDB audit events can be exported to Pub/Sub with a single sink rule, turning static files into live telemetry that analytics platforms such as Google Dataflow or Apache Flink can enrich in flight. When seconds matter, a DELETE without a WHERE clause is flagged and cancelled before it commits.
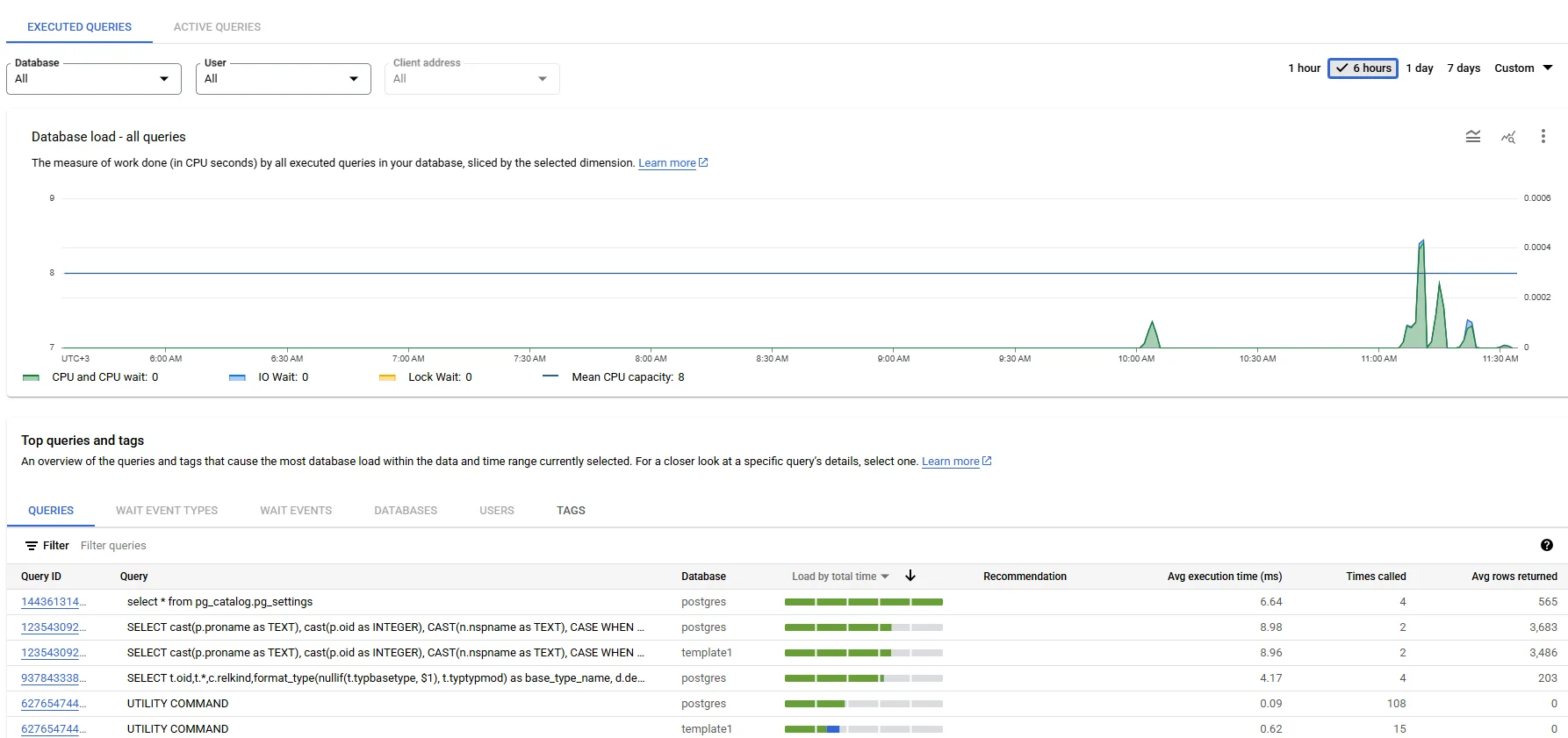
For deeper layer‑7 visibility, DataSunrise offers Database Activity Monitoring that sits as a reverse proxy. It intercepts each query, analyses it against adaptive baselines, and, if needed, blocks execution while sending an immediate Slack or Teams alert through Real‑Time Notifications. The result is sub‑second response to insider threats or compromised credentials.
Dynamic Data Masking: Protect Before You Log
Audit reduces risk further when attackers cannot see sensitive values in the first place. The DataSunrise Dynamic Data Masking engine rewrites result sets on the fly, exposing only the last four digits of a credit card or hashing personal e‑mail addresses. Unlike classic PostgreSQL view‑based masking, no schema changes are required and developers keep full SQL compatibility. Masking also satisfies “data minimisation” clauses found in both GDPR and PCI DSS.
Automated Data Discovery and Classification
Before you can mask or audit, you must know where sensitive information resides. AlloyDB metadata alone is insufficient when customer JSON columns bury nested PII. DataSunrise Data Discovery scans tables, views, and even semi‑structured fields, applying machine learning to flag PAN, NIN, PHI, and other regulated attributes. Each finding becomes a tag that downstream policies consume, ensuring every new column receives the same guards as core tables.
Security Analytics and Behavioural Detection
Volume and velocity turn audits into big data problems. DataSunrise augments raw events with Behavior Analytics. A profile is learned for each account—typical hours, tables, and command types. Deviations trigger policy‑driven counter‑measures defined in the graphical Audit Rules builder. Security teams no longer chase false positives; they focus on material anomalies such as a retired payroll account suddenly exporting millions of rows at 3 a.m.
Meeting the Letter of Compliance
Compliance managers need reproducible reports, not gigabytes of CSV. The DataSunrise Compliance Manager automatically cross‑references AlloyDB audit trails with control matrices for GDPR, PCI DSS, and HIPAA, generating auditor‑ready PDFs. Long‑term, cold audit storage can be off‑loaded to Cloud Storage or archived via the DataSunrise Audit Storage framework to control costs.
Configuring Native Audit in AlloyDB
Below is a minimal yet production‑ready configuration that captures both DDL and data‑modifying statements. Apply it once per instance:
-- Enable detailed parameter logging
ALTER SYSTEM SET log_parameter_max_length = 2048;
-- Turn on the pg_audit extension
CREATE EXTENSION IF NOT EXISTS pg_audit;
-- Record DDL plus INSERT/UPDATE/DELETE
ALTER SYSTEM SET pgaudit.log = 'ddl, write';
SELECT pg_reload_conf();
A Cloud Logging sink such as:
gcloud logging sinks create alloydb-audit \
pubsub.googleapis.com/projects/<PROJECT>/topics/alloydb-audit \
--log-filter='resource.type=cloudsql_database AND logName:"cloudaudit.googleapis.com%2Fdata_access"'
forwards every event into a Pub/Sub topic where SIEM or Flink jobs subscribe.
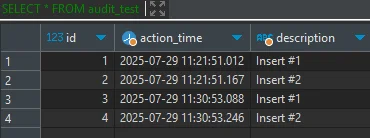
Deep Audit with DataSunrise
Native audit is powerful but has limits: it cannot correlate across sessions or inspect packet payloads. Deploy DataSunrise as a transparent proxy and gain:
- Centralised Audit Storage with compression and retention rules.
- Content‑aware blocking driven by Security Threats feeds.
- Fine‑grained obfuscation for ad‑hoc analytics users.
- On‑demand HTML and PDF reports via Report Generation.
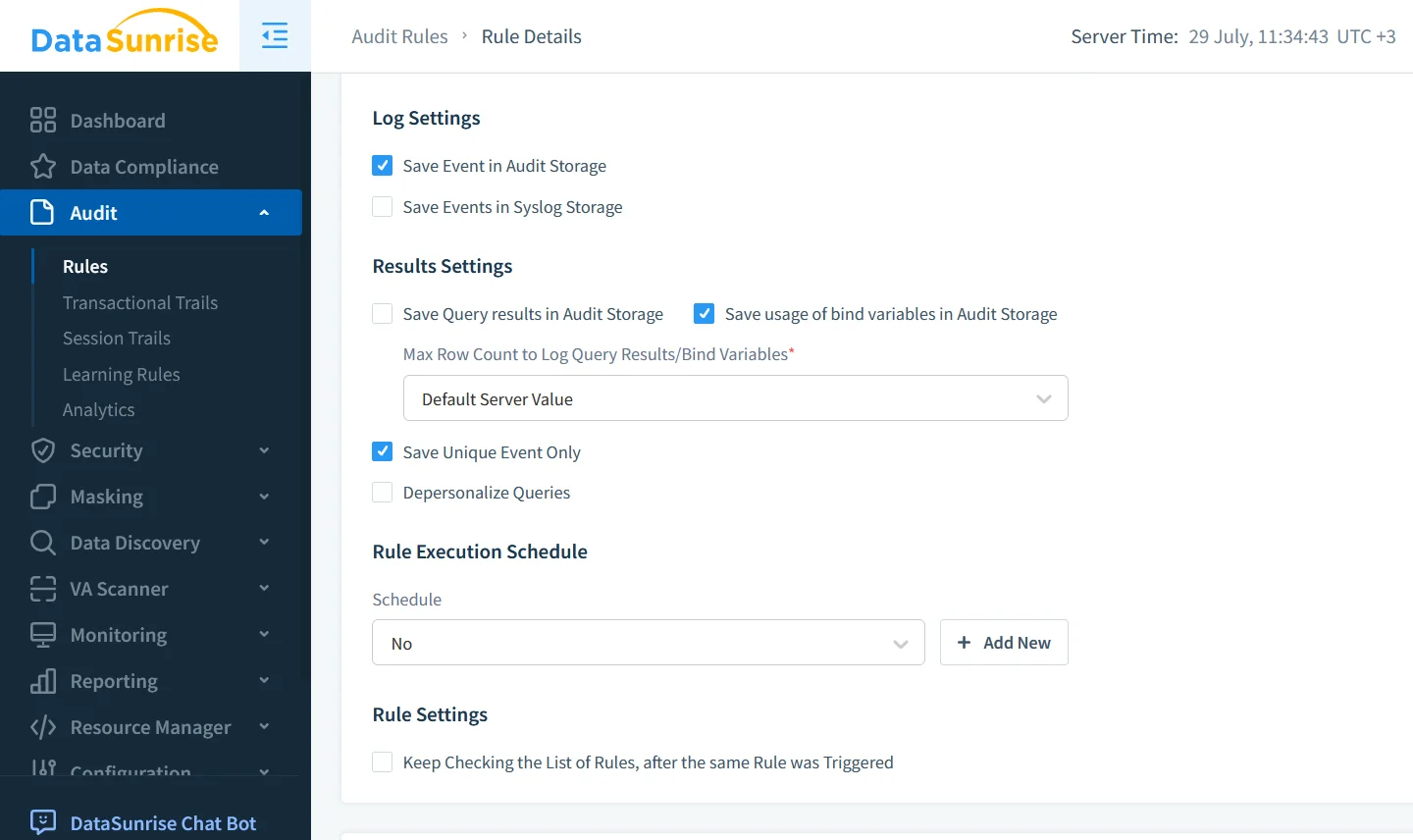
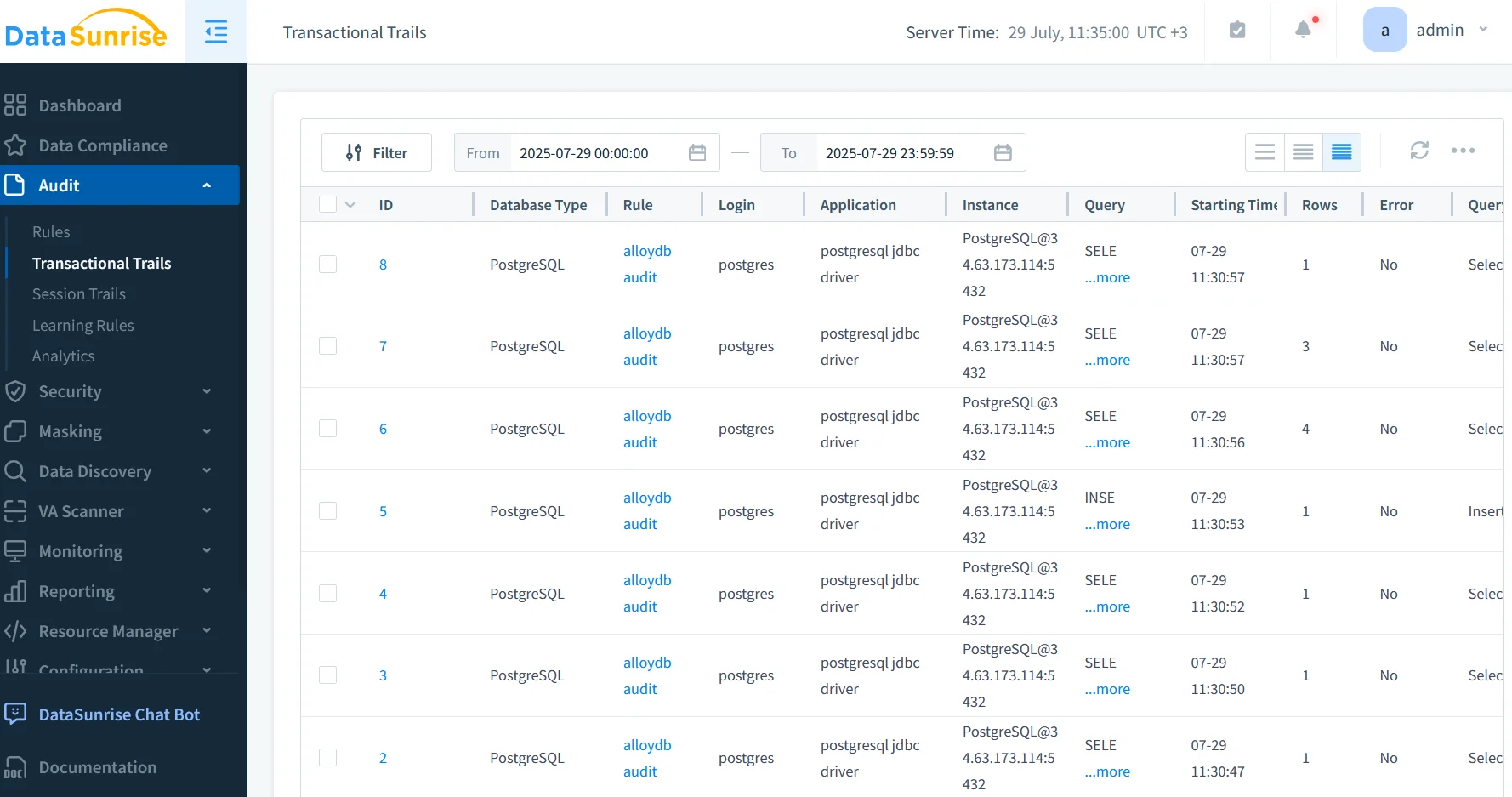
Implementation is straightforward: run the DataSunrise container in the same VPC, register AlloyDB as a backend, and point application connection strings to the proxy endpoint. No code changes, yet a full audit firewall appears overnight.
GenAI‑Powered Audit Intelligence
Raw audit lines still require expert interpretation. By pairing Data Audit for AlloyDB for PostgreSQL with modern large language models you translate logs into plain‑English summaries and root‑cause analysis.
The query below selects potentially dangerous write commands for the past hour and prepares them as JSON for Vertex AI Gemini 1.5:
WITH flagged AS (
SELECT event_time,
user_name,
command_tag,
statement
FROM audit_events
WHERE event_time > NOW() - INTERVAL '1 hour'
AND command_tag IN ('DELETE','UPDATE')
)
SELECT json_build_object('events', json_agg(flagged)) AS payload
FROM flagged;
A Python Cloud Function then sends payload with the prompt “Summarise and rank these events by risk” to the model endpoint in Vertex AI Generative AI. The response—concise narrative, recommended action, and priority score—is pushed back to security chat via webhook. Because the LLM runs in a privacy‑shielded Vertex AI container and DataSunrise can scrub personal identifiers using its LLM and ML Tools gateway, no confidential information ever leaves the trust boundary.
Conclusion
Auditing used to be an afterthought bolted onto databases. Today it is an always‑on, intelligence‑amplified service that combines native AlloyDB telemetry, DataSunrise’s proxy‑level controls, and the summarisation power of GenAI. By adopting Data Audit for AlloyDB for PostgreSQL early, organisations satisfy regulators, empower developers, and react to threats in real time—without drowning in logs or sacrificing performance.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now