
Database Activity Monitoring
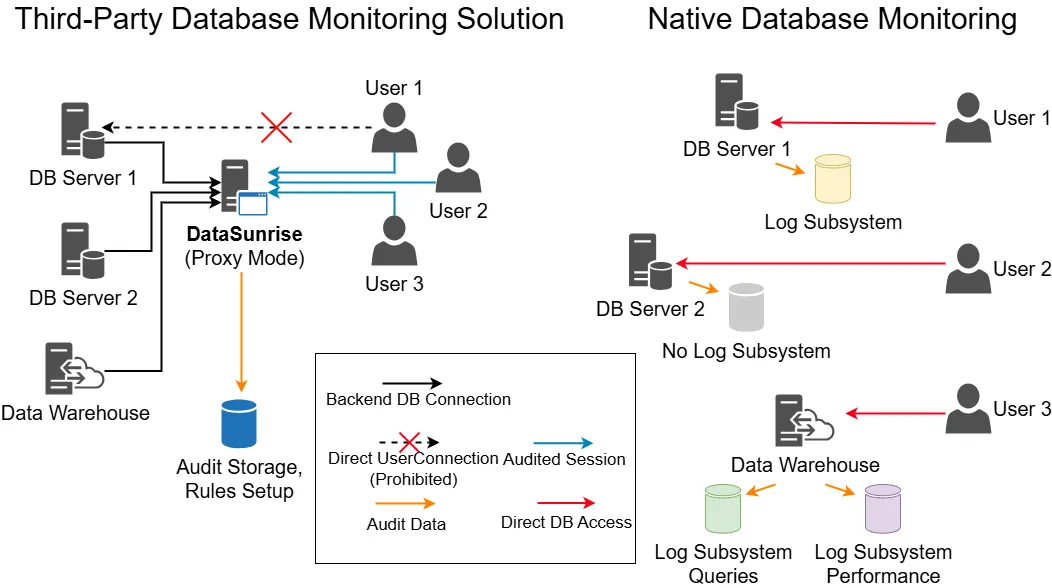
As organizations increasingly operate across multi-cloud and hybrid environments, overlooking database activity is no longer an option. Database Activity Monitoring (DAM) delivers continuous, real-time insight into user logins, executed queries, schema modifications, and data access patterns. This visibility empowers security and compliance teams to detect abnormal behavior early, enforce access control policies, prevent insider threats, and maintain adherence to regulatory standards—all without disrupting normal database operations.
DataSunrise extends the power of DAM by providing centralized monitoring across on-premises, cloud, and hybrid infrastructures. Through customizable rules, advanced behavioral analytics, and integration with SIEM and SOAR platforms, it unifies fragmented native tools into a single, coherent security layer. This ensures organizations can correlate events across multiple environments, respond faster to incidents, and sustain optimal database performance while maintaining strong governance and audit readiness.
What Is Database Activity Monitoring?
Database Activity Monitoring (DAM) provides ongoing oversight of all operations within a database. Similar to a security camera, it logs every query and change, identifies unusual or potentially harmful actions, and maintains a thorough audit record. DAM plays a critical role in both preventing and mitigating incidents as they occur, as well as enabling comprehensive and reliable forensic analysis afterward.
Why Monitoring Matters
A modern DAM platform enables organizations to:
- Identify unauthorized access or data exfiltration attempts
- Meet regulatory requirements for GDPR, HIPAA, PCI DSS, and SOX
- Resolve performance issues with better visibility into queries
- Understand user behavior through access patterns
Key Features of DAM Solutions
1. Real-Time Query Logging
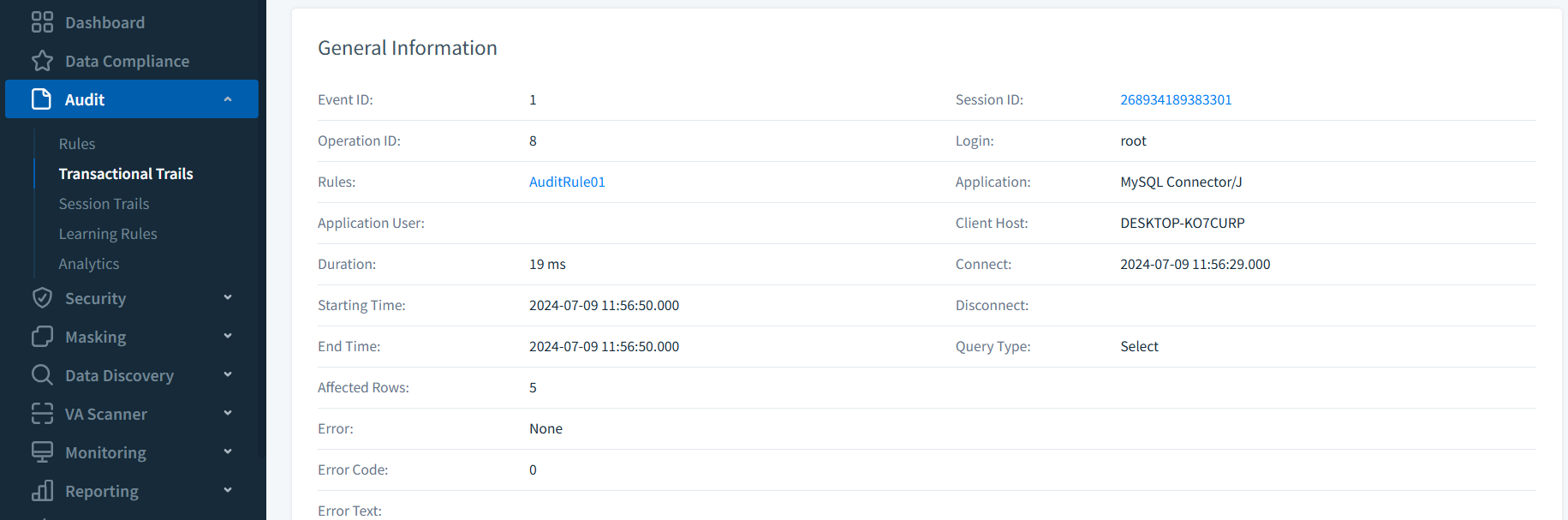
Top-tier tools capture SQL statements, DML operations, schema changes, and authentication events. DataSunrise’s Transactional Trails records SELECT statements with timestamp, session metadata, and response size.
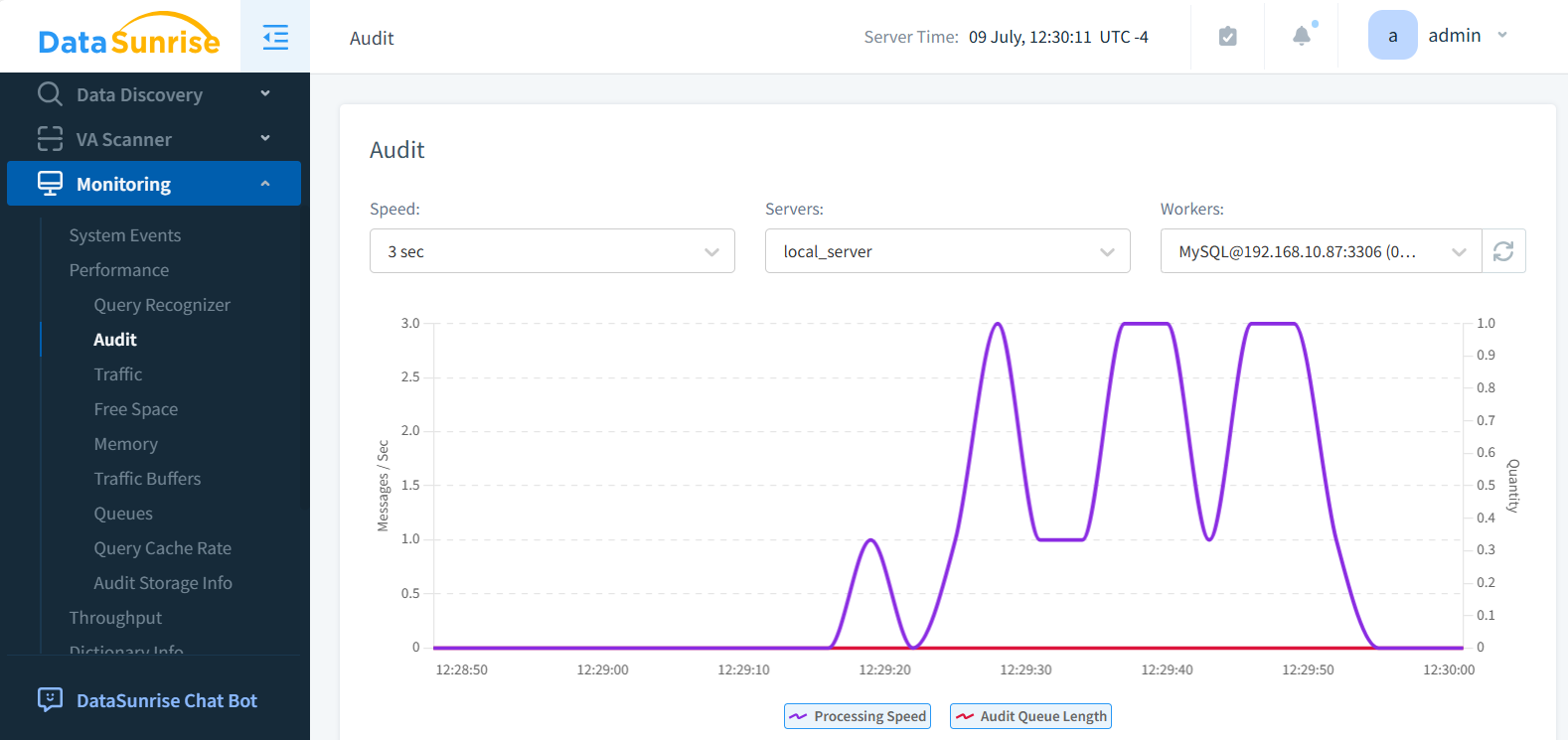
2. Custom Alerting and Notifications
When policies are violated or anomalies appear, alerting mechanisms take over. DataSunrise supports Slack, email, and SIEM integrations for incident response.
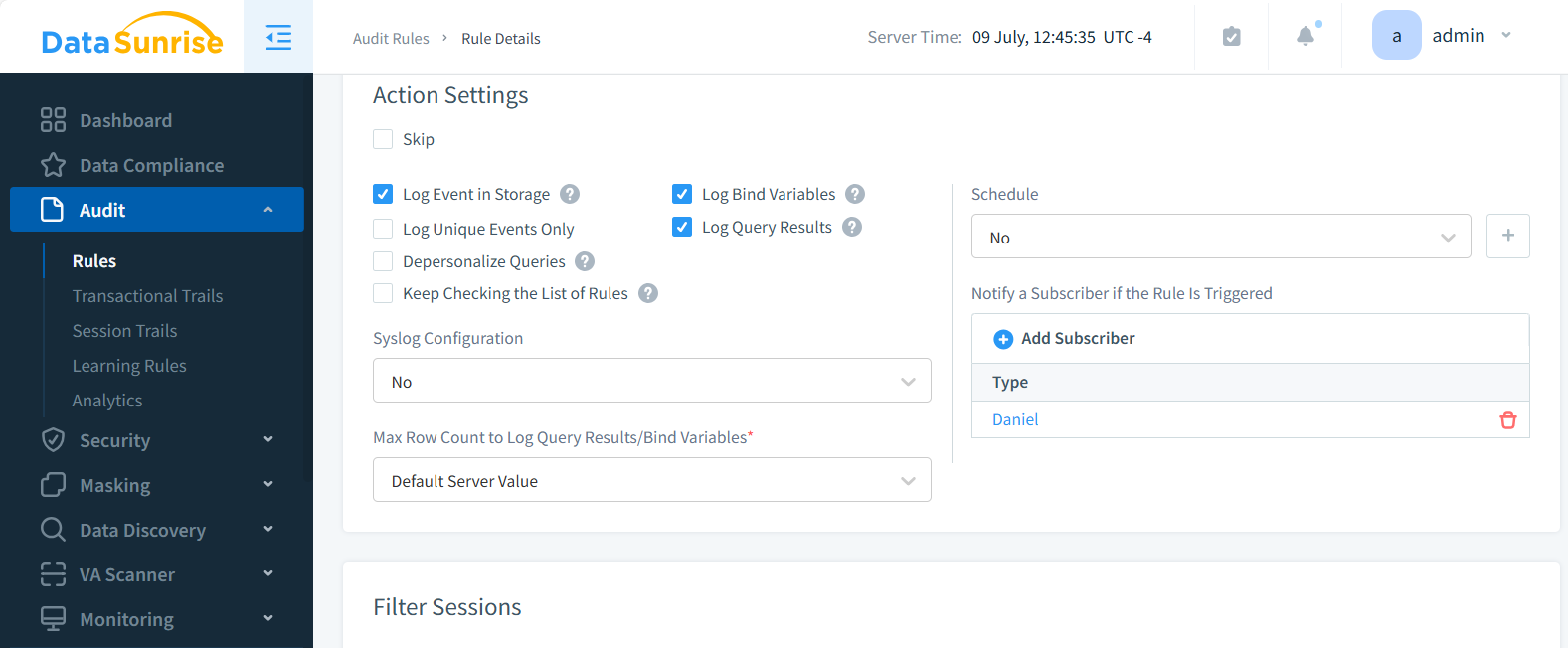
Example: Real-Time Alert via PostgreSQL + Webhook (Basic DIY)
For teams operating without a dedicated DAM platform, it’s possible to create basic real-time alerts using PostgreSQL triggers and external webhooks. Here’s a simplified example:
-- Create a function to notify via an external webhook
CREATE OR REPLACE FUNCTION notify_via_webhook()
RETURNS TRIGGER AS $$
DECLARE
payload JSON;
url TEXT := 'https://your-alert-endpoint.example.com/webhook';
BEGIN
payload := json_build_object(
'event_time', current_timestamp,
'user', current_user,
'action', TG_OP,
'table', TG_TABLE_NAME,
'data', row_to_json(NEW)
);
-- Post the payload using pg_notify or external script (pseudo)
PERFORM pg_notify('webhook_channel', payload::TEXT);
RETURN NEW;
END;
$$ LANGUAGE plpgsql;
-- Attach to sensitive operations
CREATE TRIGGER alert_on_change
AFTER INSERT OR UPDATE OR DELETE ON sensitive_data
FOR EACH ROW EXECUTE FUNCTION notify_via_webhook();
This manual approach requires additional scripting outside the database to consume the pg_notify event and forward it to a webhook or alert system. While functional in small setups, platforms like DataSunrise simplify this by supporting native alert routing to Slack, SIEM tools, and email—without custom scripts or polling overhead.
3. Persistent Audit Trails
Audit logs must be retained to meet compliance frameworks and investigative demands. Here’s a PostgreSQL trigger example that records user activity:
-- PostgreSQL: Sample trigger-based audit log
CREATE TABLE user_activity_log (
id SERIAL PRIMARY KEY,
event_time TIMESTAMP DEFAULT current_timestamp,
username TEXT,
action TEXT,
table_accessed TEXT,
old_data JSONB,
new_data JSONB
);
CREATE OR REPLACE FUNCTION log_user_activity()
RETURNS TRIGGER AS $$
BEGIN
INSERT INTO user_activity_log(username, action, table_accessed, old_data, new_data)
VALUES (
current_user,
TG_OP,
TG_TABLE_NAME,
row_to_json(OLD),
row_to_json(NEW)
);
RETURN NEW;
END;
$$ LANGUAGE plpgsql;
CREATE TRIGGER audit_sensitive_table
AFTER INSERT OR UPDATE OR DELETE ON customer_data
FOR EACH ROW EXECUTE FUNCTION log_user_activity();
Although useful in small-scale environments, this method lacks scalability and central management. DataSunrise improves on this by aggregating logs across platforms with structured filtering and role-based access.
4. Performance Monitoring
Beyond access control, DAM helps teams identify inefficient SQL queries and resource-heavy processes. In proxy mode, DataSunrise analyzes performance without introducing major latency.
- Identification of long-running transactions and locking issues – the system detects slow operations, competing transactions, and blocking queries that may reduce database throughput.
- Load distribution analysis across users and applications – DataSunrise highlights which services or accounts generate the heaviest workload, helping teams optimize resource usage.
- Detection of resource consumption anomalies – the monitoring engine identifies sudden spikes in CPU, memory, or I/O usage, allowing teams to prevent performance degradation before it impacts operations.
5. SIEM and Compliance Integration
Enterprise environments need visibility across the stack. DAM tools like DataSunrise support log forwarding to SIEM systems and provide APIs for compliance automation.
Built-In vs Third-Party Monitoring: Feature Comparison
To illustrate the difference, let’s compare native tools—using PostgreSQL and MongoDB as examples—against a consolidated third-party platform like DataSunrise. While built-in logging provides a starting point, it falls short on centralized visibility, user attribution, and compliance automation.
| Feature | Built-In (PostgreSQL/MongoDB) | Third-Party (DataSunrise) |
|---|---|---|
| Real-Time Alerts | Manual scripting (triggers + NOTIFY) | Native Slack, SIEM, Email integration |
| Centralized Logs | Scattered, per-node logging | Unified, queryable audit trail |
| User Behavior Analytics | Limited session context | Behavioral tracking with context |
| Rule Management | Custom scripts only | GUI-driven policy engine |
| Compliance Support | Basic logs, manual exports | Regulation-ready reporting & export |
PostgreSQL, for example, supports extended audit logging through the pgAudit extension, though it requires manual setup and lacks built-in alerting. Meanwhile, MongoDB’s built-in Database Profiler provides detailed operation tracking, but it doesn’t correlate actions to users or trigger alerts automatically. These native tools offer a good start, but they lack the centralized control, scalability, and integration depth needed for enterprise-grade monitoring—capabilities you get with DataSunrise.
Risks of Operating Without Database Activity Monitoring
Without a structured DAM solution, security and compliance gaps are inevitable. Native logging or ad-hoc scripts rarely provide the breadth, correlation, and retention needed for modern audits. Common issues include:
- Undetected Data Breaches – Without centralized alerts, suspicious activity can go unnoticed for weeks or months.
- Compliance Failures – Regulations like GDPR and HIPAA require detailed activity logs; missing or incomplete records can lead to fines.
- Fragmented Logs – Per-node logs scatter the audit trail, making investigations slow and incomplete.
- High Forensic Costs – Without event correlation, forensic investigations require combing through raw logs manually.
- Performance Blind Spots – Without query-level monitoring, resource bottlenecks and inefficient SQL remain hidden.
Platforms like DataSunrise eliminate these risks by consolidating activity into a single, queryable source, automating alerts, and ensuring compliance reports are always export-ready.
Best Practices for Monitoring Success
- Establish baselines for normal behavior — define what typical user, application, and database activity looks like. Accurate baselines help distinguish legitimate operations from true anomalies and reduce false positives.
- Review alerts and audit logs routinely — implement a structured review schedule (daily, weekly, monthly) and ensure all critical events are escalated to SIEM/SOAR systems. Regular log review improves incident response readiness and helps identify slow-moving or low-noise attacks.
- Apply least-privilege access and enforce role separation — ensure that administrators, developers, analysts, and support engineers have clearly separated duties. Minimizing access reduces attack surface and strengthens accountability in audit trails.
- Use masking or encryption where possible (dynamic masking helps reduce alert noise on non-privileged users) — protect sensitive fields in real time and ensure that only authorized roles can see raw data. This not only improves security but also simplifies compliance with GDPR, HIPAA, PCI DSS, and other frameworks.
- Adjust detection thresholds as new risks emerge — continuously refine your alerting rules and sensitivity levels as your environment changes. Incorporate threat intelligence, new application workflows, or unusual user behavior to keep detection effective and relevant.
- Integrate monitoring with incident response workflows — ensure alerts automatically create tickets, send notifications, or trigger SOAR playbooks. This closes the loop between detection and response and reduces time to containment.
- Periodically validate monitoring accuracy — perform tests such as simulated attacks, credential misuse, or abnormal query execution to verify that alerts trigger as expected. This ensures controls are functioning and reduces blind spots.
- Correlate events across multiple systems — combine DataSunrise logs with SIEM, IAM, firewall, and CloudTrail data to achieve full visibility. Correlation helps identify multi-stage attacks that would appear harmless in isolation.
Practical Use Cases of Database Activity Monitoring
In financial services, DAM helps detect unusual transfers or unauthorized queries in payment systems, directly supporting PCI DSS and SOX compliance. Healthcare organizations use it to track every access to patient records, ensuring HIPAA audit requirements are met without slowing down clinical workflows.
Government agencies rely on DAM to keep privileged user activity under control, preventing insider threats around classified datasets. For SaaS and cloud providers, monitoring plays a key role in enforcing least-privilege access across multi-tenant environments, while quickly spotting any cross-tenant data exposure attempts.
E-commerce platforms also benefit, using DAM to recognize spikes in login failures or abnormal order queries that could signal account takeovers or credential-stuffing attacks. In each case, database activity monitoring provides both real-time protection and forensic visibility.
Conclusion
Database Activity Monitoring (DAM) is a core element of modern data protection strategies, providing organizations with continuous insight into every action occurring within their database environments. By tracking and analyzing user activities, access patterns, and system events in real time, DAM tools protect sensitive assets against unauthorized access, manipulation, and insider threats. Contemporary DAM solutions extend beyond passive monitoring—leveraging behavioral analytics, automated alerting, and machine learning models to detect irregularities before they evolve into serious security breaches.
In addition to enhancing visibility and accountability, DAM simplifies incident response and supports forensic analysis through the maintenance of immutable audit trails for all database operations. This allows organizations to respond promptly to suspicious activity while ensuring compliance with major data protection regulations such as GDPR, HIPAA, SOX, PCI DSS, and the EU AI Act. Designed for hybrid and cloud environments, modern DAM systems deliver scalable, high-performance protection through automated policies, fine-grained role-based controls, and adaptive risk evaluation. Ultimately, DAM strengthens data governance, mitigates threats, and promotes lasting operational resilience across the enterprise.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now