Applying Data Governance for Amazon DynamoDB
Applying data governance to Amazon DynamoDB requires a different mindset than traditional relational databases. DynamoDB is schema-flexible, fully managed, and deeply integrated into AWS infrastructure. Because of this architecture, governance spans identity controls, infrastructure security, operational logging, and continuous monitoring instead of relying on a single database-level audit mechanism. As a result, teams shift their focus from classic database auditing toward broader data security and access controls enforced at the platform level.
For organizations that store sensitive, regulated, or business-critical data in DynamoDB, governance plays a central role in maintaining accountability, security, and regulatory alignment. Without a structured governance model, teams struggle to answer fundamental questions. For example, who accessed the data, which permissions allowed that access, which service initiated the request, and whether those actions complied with internal policies and external data compliance regulations.
Therefore, this article explains how organizations apply data governance to DynamoDB using native AWS controls, where those controls reach their limits, and how teams can operationalize governance at scale. In addition, it shows how concepts borrowed from centralized database activity monitoring and policy enforcement practices help create a consistent governance model for cloud-native environments.
What Data Governance Means for DynamoDB
In DynamoDB environments, data governance does not exist as a single feature or service. Instead, it functions as a coordinated set of controls that actively manage how teams access, protect, log, and review data throughout its lifecycle. In practice, this approach aligns governance with broader data management principles and platform-wide security controls rather than isolated database configurations.
As a result, effective DynamoDB governance focuses on several core objectives:
- Enforcing least-privilege access to tables and indexes through strict role-based access control
- Applying encryption and infrastructure-level protection consistently across all storage and replication layers
- Capturing reliable activity records to support accountability and traceability
- Supporting compliance audits and investigations with defensible, structured evidence
- Preventing governance drift as environments scale and architectures evolve
Because DynamoDB does not expose query-level auditing in the same way as SQL databases, governance depends heavily on AWS-level services instead of database internals. Consequently, operational visibility aligns more closely with data activity history than with traditional statement-level audit trails.
Governance Controls in Amazon DynamoDB
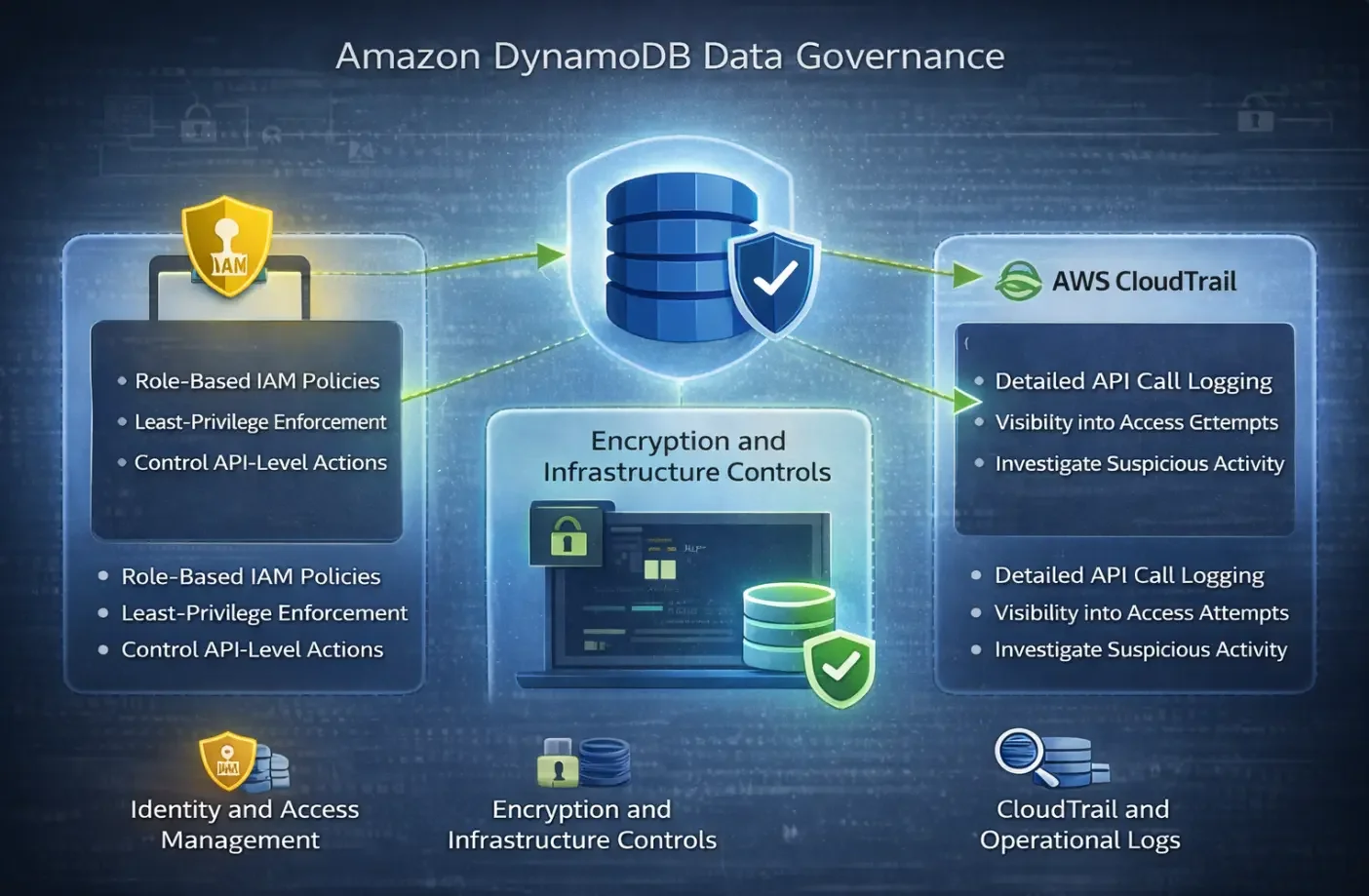
Identity and Access Governance
Amazon DynamoDB relies entirely on AWS Identity and Access Management (IAM) for authorization. Every request—whether originating from a Lambda function, containerized workload, API Gateway, or human operator—is evaluated against IAM policies before it reaches the DynamoDB service.
A sound governance model starts with strict least-privilege enforcement. IAM policies should be scoped to specific tables and indexes, with read and write permissions separated across roles. Wildcard actions such as dynamodb:* should be avoided in production environments, and administrative privileges must be isolated from application execution roles.
Example: least-privilege IAM policy scoped to a single table and read operations only:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"dynamodb:GetItem",
"dynamodb:Query"
],
"Resource": "arn:aws:dynamodb:us-east-1:123456789012:table/Orders"
}
]
}
IAM represents the first and strongest governance boundary in DynamoDB. Once a request is authorized at this level, DynamoDB assumes it is valid and does not apply additional contextual checks.
Governance must also account for execution context, not just user identity. Direct access to DynamoDB is rare; most interactions originate from AWS Lambda, ECS or EKS workloads, or backend services using SDKs. An over-privileged execution role is a governance failure even when no human has direct access to the data.
Example: separating application execution from administrative permissions:
{
"Effect": "Deny",
"Action": [
"dynamodb:DeleteTable",
"dynamodb:UpdateTable"
],
"Resource": "*"
}
Data Protection and Infrastructure Controls
DynamoDB encrypts data at rest by default using AWS-managed or customer-managed KMS keys. While encryption is essential, it does not provide visibility into data usage or prevent misuse on its own.
From a governance perspective, encryption controls focus on how keys are managed and applied. Customer-managed KMS keys with restrictive key policies are commonly used for sensitive datasets, combined with key usage monitoring and regular rotation. Regulated data domains are often separated using dedicated encryption keys to enforce clear protection boundaries.
Example: restrictive KMS key policy allowing use only by DynamoDB and a specific IAM role:
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::123456789012:role/dynamodb-app-role"
},
"Action": [
"kms:Encrypt",
"kms:Decrypt",
"kms:GenerateDataKey"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"kms:ViaService": "dynamodb.us-east-1.amazonaws.com"
}
}
}
Encryption secures data storage, but it does not govern how data is accessed or consumed.
Network controls add an additional governance layer. DynamoDB supports VPC endpoints, allowing traffic to remain entirely within AWS networks. In regulated environments, governance frameworks often mandate VPC endpoint usage, endpoint policies that restrict accessible tables, and the elimination of public internet access.
Example: VPC endpoint policy limiting access to approved tables only:
{
"Statement": [
{
"Effect": "Allow",
"Principal": "*",
"Action": "dynamodb:*",
"Resource": [
"arn:aws:dynamodb:us-east-1:123456789012:table/Orders",
"arn:aws:dynamodb:us-east-1:123456789012:table/Customers"
]
}
]
}
These controls enforce infrastructure-level containment that complements IAM-based access control.
Activity Traceability and Operational Evidence
DynamoDB does not generate query-level logs. Instead, governance relies on AWS CloudTrail to capture API-level activity.
CloudTrail records operations such as GetItem, PutItem, UpdateItem, Query, and Scan, along with table and index changes and IAM authorization outcomes. This provides a record of who performed an action, when it occurred, and which API was invoked.
Example: CloudTrail event for a DynamoDB read operation:
{
"eventSource": "dynamodb.amazonaws.com",
"eventName": "GetItem",
"userIdentity": {
"type": "AssumedRole",
"arn": "arn:aws:sts::123456789012:assumed-role/dynamodb-app-role/app"
},
"requestParameters": {
"tableName": "Orders"
},
"eventTime": "2026-01-23T14:42:11Z",
"awsRegion": "us-east-1"
}
However, CloudTrail does not expose item-level context, attribute-level visibility, or business logic interpretation. For this reason, CloudTrail logs should be treated as raw operational evidence, not as complete audit artifacts. Effective governance requires correlating and enriching this telemetry to produce meaningful compliance and security insights.
DataSunrise-Driven Governance for Amazon DynamoDB
Compliance Alignment Through Enforceable Controls
Regulatory frameworks do not adapt themselves to DynamoDB, and native AWS controls alone do not translate regulatory language into enforceable governance logic. Abstract requirements such as lawful access, segregation of duties, and audit evidence integrity must be operationalized across identities, execution contexts, and environments.
DataSunrise provides a governance layer above DynamoDB’s native services, translating regulatory requirements into policy-driven, enforceable controls aligned with real operational behavior. Instead of relying on isolated features, governance is implemented through coordinated access control, monitoring, and evidence collection supported by centralized data compliance workflows.
Typical compliance alignment patterns supported by DataSunrise include mapping IAM identities and execution roles to lawful processing purposes for GDPR compliance, restricting and monitoring write access to payment-related tables under PCI DSS compliance, isolating healthcare datasets with stricter access paths aligned with HIPAA compliance, and enforcing immutability and traceability of financial access records using structured audit logs for SOX-driven audits.
In DynamoDB environments, compliance is achieved through control composition, not individual mechanisms.
Centralized Governance Across Distributed DynamoDB Environments
DynamoDB architectures commonly span multiple AWS accounts, regions, and isolated environments such as development, testing, and production. Without centralized governance, these environments quickly diverge, leading to inconsistent access policies, fragmented visibility, and compliance gaps.
DataSunrise enables centralized governance enforcement across all DynamoDB environments. Governance logic is defined once and applied consistently, independent of AWS account boundaries or regional deployment models. DynamoDB activity sourced from CloudTrail is aggregated and analyzed through centralized database activity monitoring, allowing organizations to maintain consistent oversight across environments.
By unifying policy interpretation and reporting through the Compliance Manager, DataSunrise prevents configuration drift and maintains a predictable compliance posture as DynamoDB deployments scale and evolve.
Governance Beyond Native DynamoDB Capabilities
Native AWS services such as IAM, CloudTrail, KMS, and VPC endpoints provide essential building blocks, but they do not form a complete governance system. As DynamoDB usage grows, organizations require governance capabilities that go beyond raw infrastructure telemetry and static access rules.
DataSunrise extends DynamoDB governance by introducing policy-driven governance logic aligned with regulatory intent, centralized analysis of operational activity using structured data audit processes, context-aware enforcement based on identity and environment, and compliance-ready reporting designed for audits and regulatory reviews.
By adding semantic understanding and centralized control, DataSunrise transforms DynamoDB operational signals into actionable governance outcomes across cloud-native and hybrid architectures.
Business Impact of Proper DynamoDB Data Governance
| Governance Outcome | Business Impact |
|---|---|
| Reduced over-privileged access | Lowers the risk of unauthorized data exposure and limits blast radius in case of compromised roles |
| Structured activity evidence | Accelerates incident investigation by providing clear, correlated access records |
| Streamlined compliance audits | Reduces audit scope, preparation time, and manual evidence collection effort |
| Consistent controls across environments | Ensures a predictable security posture across accounts, regions, and deployment stages |
| Clear ownership and accountability | Establishes responsibility for data access decisions and governance enforcement |
Conclusion
Applying data governance to DynamoDB requires teams to abandon assumptions rooted in relational databases. Instead of relying on schema constraints or query logs, DynamoDB governance operates through identity management, infrastructure controls, and operational telemetry. As DynamoDB environments scale, effective governance depends on coordinated access control, consistent activity visibility, and explicit policy enforcement rather than database-level constructs.
Organizations that treat DynamoDB governance as a first-class architectural concern achieve stronger security through centralized data security controls. In addition, they gain clearer regulatory alignment through structured data compliance processes and higher operational confidence enabled by continuous database activity monitoring.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now